Father-Son Terror Suspects Linked to ISIS Prior to Deadly Bondi Beach Hanukkah Attack
Published on: 2025-12-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Father-Son Duo Terror Suspects Reportedly Pledged Allegiance to ISIS Before Bondi Beach Attack
1. BLUF (Bottom Line Up Front)
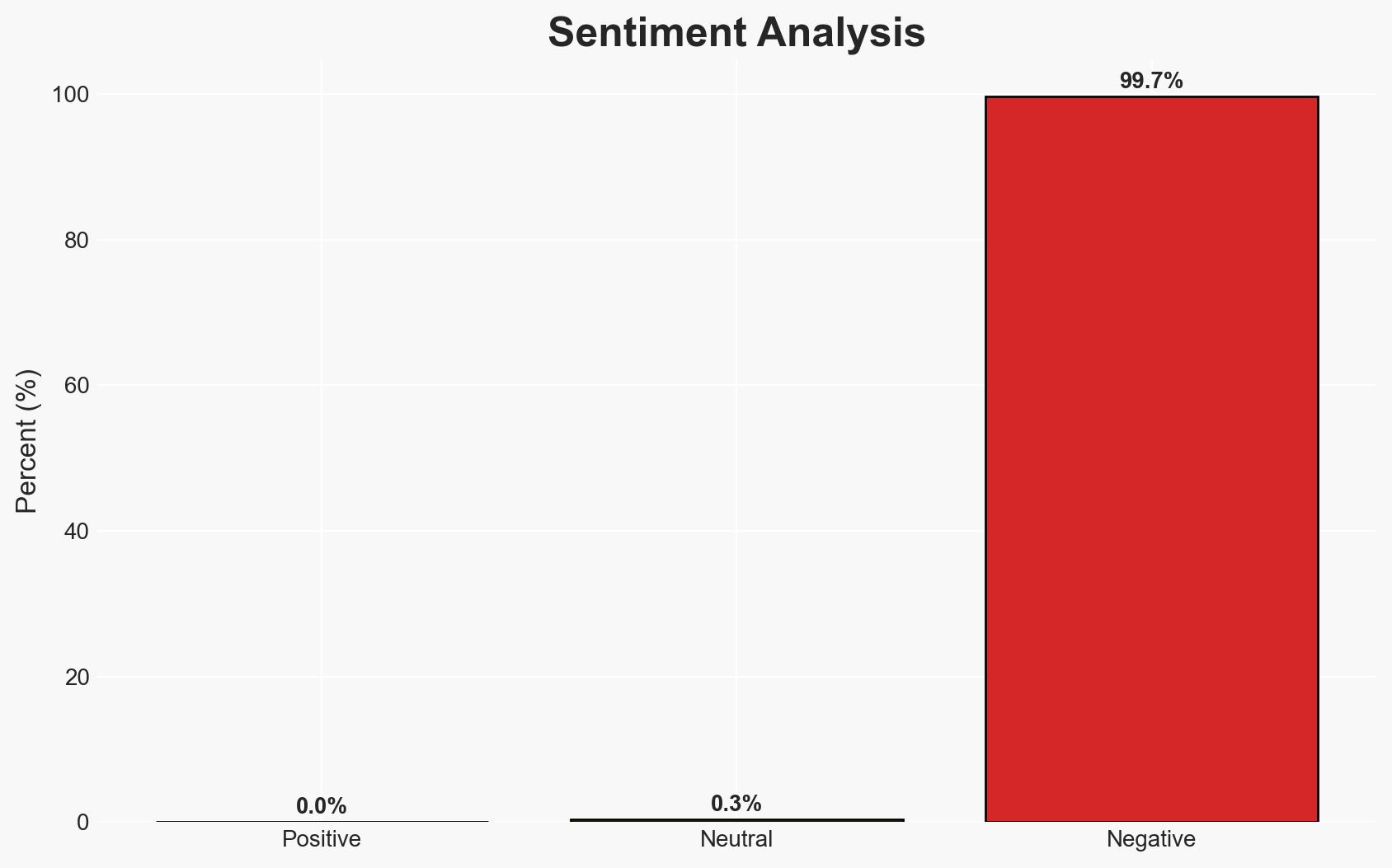
The Bondi Beach attack, allegedly perpetrated by a father-son duo with reported ties to ISIS, highlights potential intelligence gaps in monitoring radicalized individuals. The attack, which targeted a Jewish celebration, suggests a possible antisemitic motive. The most likely hypothesis is that the attack was ideologically driven by radical Islamist beliefs. Overall confidence in this assessment is moderate, pending further intelligence disclosures.
2. Competing Hypotheses
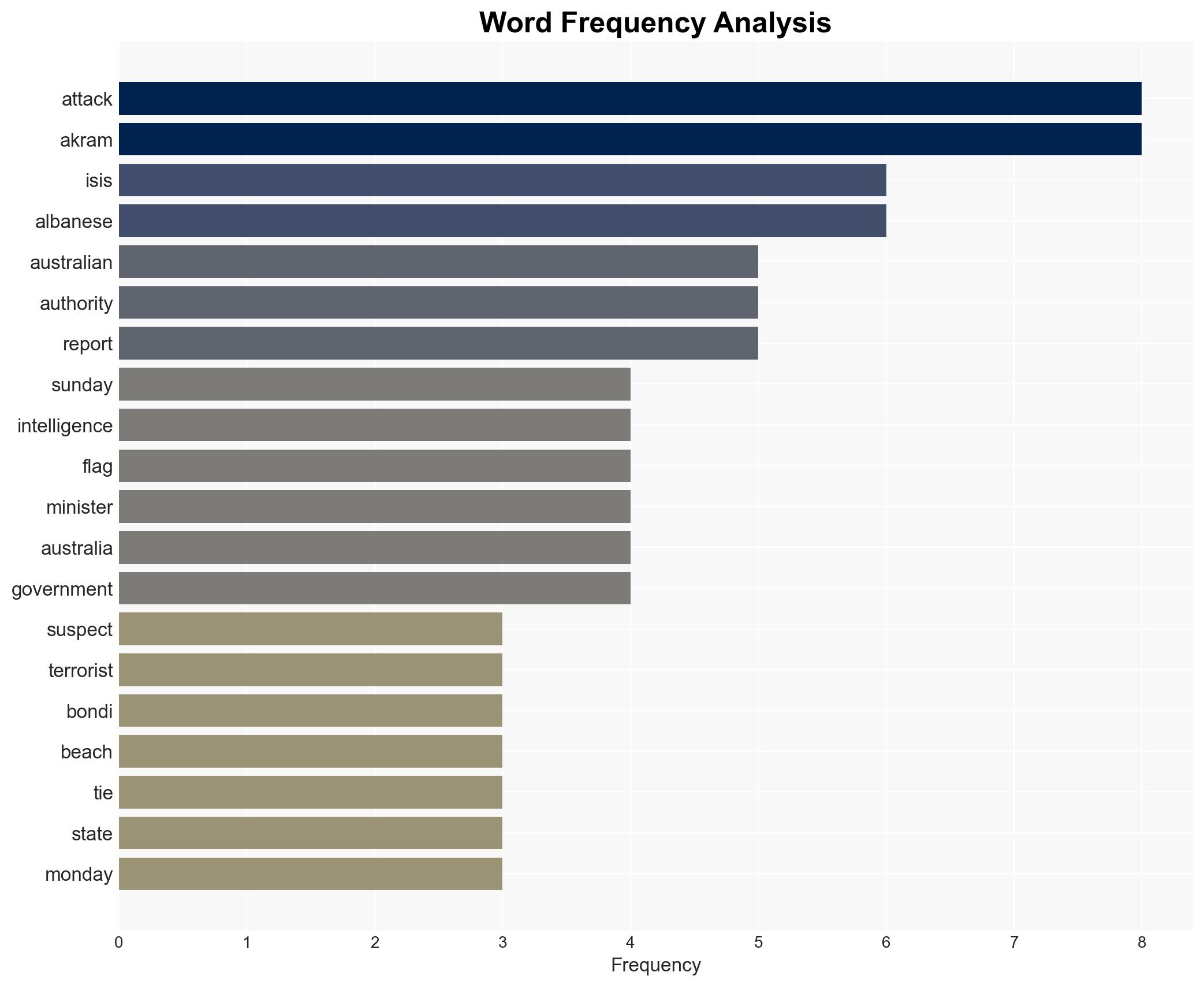
- Hypothesis A: The attack was ideologically motivated by radical Islamist beliefs, supported by the discovery of ISIS flags and previous investigations into Naveed Akram’s ties to ISIS. Contradicting evidence includes the lack of a current watchlist status and the authorities’ reluctance to cite radical Islam as a motive.
- Hypothesis B: The attack was primarily driven by personal grievances or mental instability, with the ISIS affiliation being incidental or overstated. This is supported by the lack of recent intelligence indicating an imminent threat and the attackers not being on a watchlist.
- Assessment: Hypothesis A is currently better supported due to the presence of ISIS flags and prior investigations into Naveed Akram’s radical associations. Indicators that could shift this judgment include new evidence of personal motives or mental health issues.
3. Key Assumptions and Red Flags
- Assumptions: The presence of ISIS flags indicates ideological motivation; prior investigations were thorough; the attack was premeditated.
- Information Gaps: Details on the attackers’ recent activities, communications, and the extent of their connections to ISIS affiliates.
- Bias & Deception Risks: Potential underestimation of the threat due to cognitive biases; media or political narratives may skew perception of motives.
4. Implications and Strategic Risks
This development could exacerbate tensions within Australia’s multicultural society and strain community relations. It may also prompt a reevaluation of counter-terrorism strategies and intelligence oversight.
- Political / Geopolitical: Increased scrutiny on immigration policies and potential diplomatic tensions with countries linked to radicalization.
- Security / Counter-Terrorism: Possible tightening of surveillance and monitoring of suspected radicals; increased security measures at public events.
- Cyber / Information Space: Potential for increased online radicalization efforts and propaganda dissemination by extremist groups.
- Economic / Social: Heightened fear and division within communities, potentially impacting social cohesion and economic activities in affected areas.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of radicalized individuals, review intelligence-sharing protocols, and increase security at vulnerable events.
- Medium-Term Posture (1–12 months): Strengthen community engagement initiatives, develop counter-radicalization programs, and invest in intelligence capabilities.
- Scenario Outlook: Best: Improved intelligence leads to prevention of future attacks. Worst: Failure to address gaps results in further incidents. Most-Likely: Incremental improvements in counter-terrorism measures with occasional lapses.
6. Key Individuals and Entities
- Naveed Akram – Suspected attacker
- Sajid Akram – Deceased attacker
- Anthony Albanese – Australian Prime Minister
- Mal Lanyon – NSW Police Commissioner
- Greg Barton – Counter-terrorism expert
- Tony Burke – Home Affairs Minister
- Isaac El Matari – Imprisoned ISIS terrorist
7. Thematic Tags
Counter-Terrorism, radicalization, intelligence oversight, ISIS, antisemitism, Australia, community relations
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us