FBI shuts down RAMP ransomware forum, marking a significant blow to cybercrime operations.
Published on: 2026-01-31
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: FBI takes notorious RAMP ransomware forum offline
1. BLUF (Bottom Line Up Front)
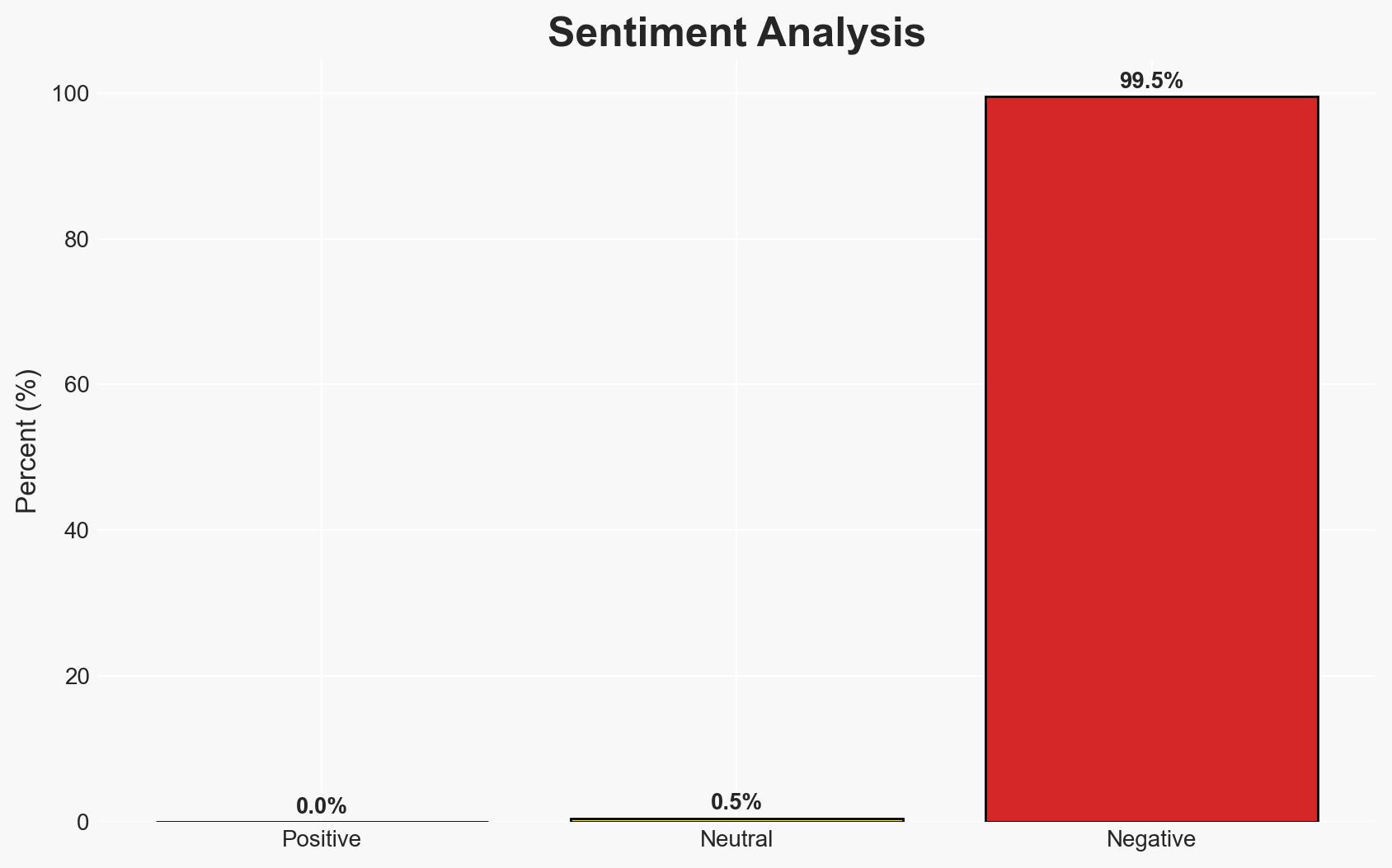
The FBI’s seizure of the RAMP ransomware forum represents a significant disruption to cybercriminal infrastructure, particularly affecting ransomware operators and their affiliates. This action underscores U.S. law enforcement’s capability to target and dismantle cybercriminal networks, even those operating on the dark web. However, the persistence of ransomware activities through other channels suggests only a temporary setback for cybercriminals. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The seizure of RAMP will significantly disrupt ransomware operations by dismantling a key platform for coordination and recruitment. Supporting evidence includes the forum’s role as a marketplace for ransomware operators and its popularity among cybercriminals. Contradicting evidence includes statements from cybercriminals indicating operations will continue through other channels.
- Hypothesis B: The seizure of RAMP will have limited long-term impact on ransomware activities, as cybercriminals will quickly adapt and migrate to alternative platforms. Supporting evidence includes the historical resilience of cybercriminal networks and the existence of other forums. Contradicting evidence is the immediate disruption and operational challenges faced by cybercriminals.
- Assessment: Hypothesis B is currently better supported due to the adaptability of cybercriminals and the existence of alternative platforms. Key indicators that could shift this judgment include evidence of significant delays or failures in ransomware operations and the emergence of new, similarly effective platforms.
3. Key Assumptions and Red Flags
- Assumptions: The seizure will disrupt cybercriminal operations temporarily; cybercriminals will seek alternative platforms; law enforcement will continue targeting similar forums.
- Information Gaps: Details on the extent of data seized by the FBI and the potential for further arrests or disruptions remain unclear.
- Bias & Deception Risks: Potential bias in underestimating the resilience of cybercriminal networks; possible deception in cybercriminals’ public statements about continuing operations.
4. Implications and Strategic Risks
The seizure of RAMP could lead to a temporary decrease in ransomware activities, but long-term impacts are uncertain. Cybercriminals may adapt by enhancing operational security and migrating to new platforms, potentially leading to more sophisticated and resilient networks.
- Political / Geopolitical: Increased tensions between the U.S. and countries perceived as safe havens for cybercriminals, particularly Russia.
- Security / Counter-Terrorism: Short-term reduction in ransomware threats, but potential for increased sophistication in future attacks.
- Cyber / Information Space: Shift in cybercriminal tactics and potential emergence of new platforms or methods for coordination.
- Economic / Social: Temporary relief for businesses targeted by ransomware, but ongoing threat to economic stability if cybercriminals adapt successfully.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Intensify monitoring of alternative cybercriminal forums; enhance international cooperation for cybercrime enforcement.
- Medium-Term Posture (1–12 months): Develop resilience measures for potential ransomware attacks; invest in cybersecurity partnerships and intelligence sharing.
- Scenario Outlook:
- Best: Significant disruption leads to a sustained decrease in ransomware activities.
- Worst: Cybercriminals quickly adapt, leading to more sophisticated and widespread ransomware attacks.
- Most-Likely: Temporary disruption with gradual adaptation by cybercriminals to new platforms.
6. Key Individuals and Entities
- Mikhail Matveev (“Orange”, “Wazawaka”, “BorisElcin”)
- “Stallman” (alleged RAMP operator)
- FBI
- US Attorney’s Office for the Southern District of Florida
- US Justice Department’s Computer Crime and Intellectual Property Section (CCIPS)
7. Thematic Tags
cybersecurity, cybercrime, ransomware, law enforcement, dark web, cyber resilience, international cooperation, cyber operations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us