FBI warns Play ransomware hackers have hit nearly a thousand US firms – TechRadar
Published on: 2025-06-05
Intelligence Report: FBI warns Play ransomware hackers have hit nearly a thousand US firms – TechRadar
1. BLUF (Bottom Line Up Front)
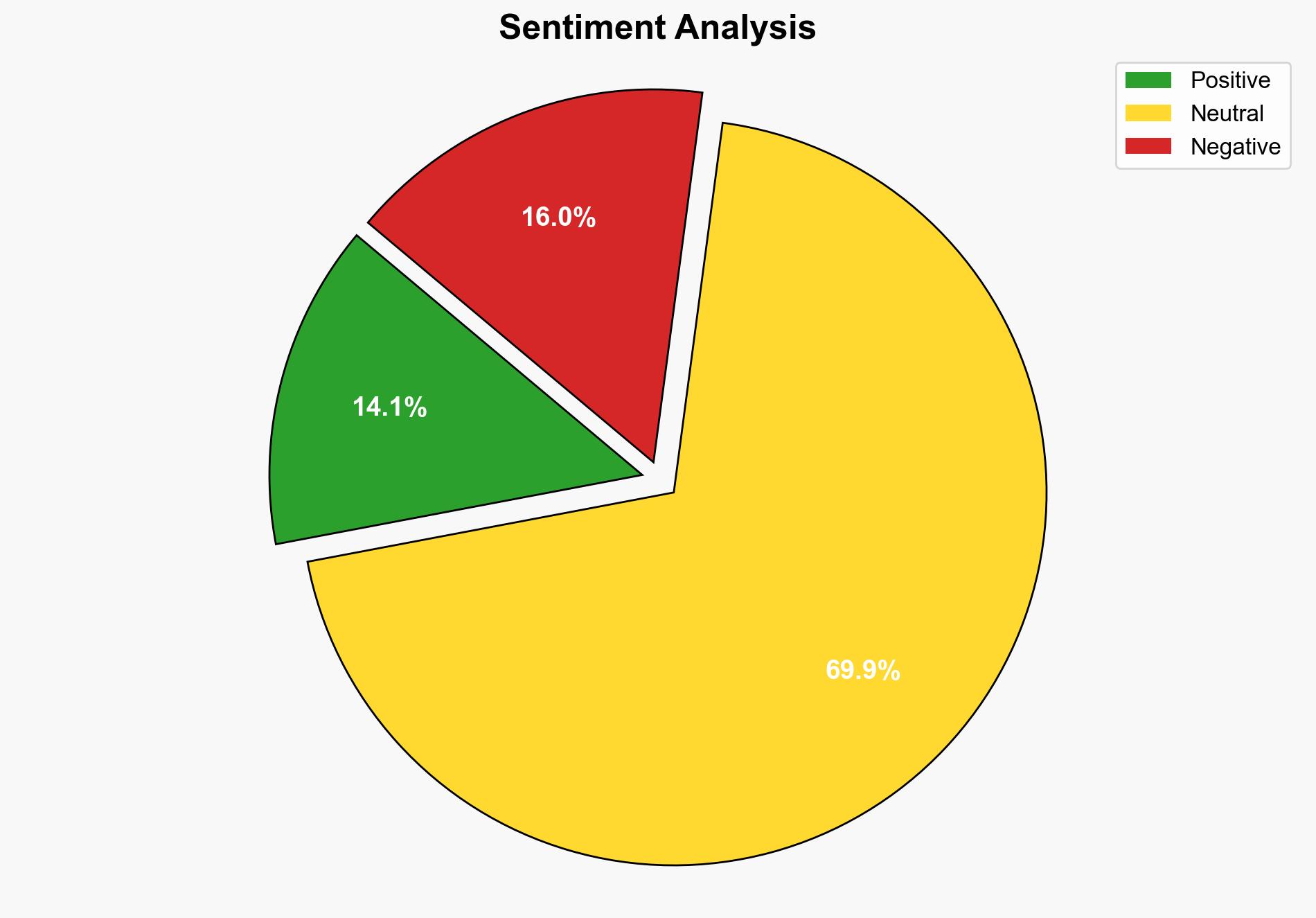
The Play ransomware group has targeted nearly a thousand US firms, employing advanced tactics such as phone call extortion and exploiting new vulnerabilities. The FBI, in collaboration with other agencies, has issued advisories urging businesses to enhance their cybersecurity measures. Immediate action is recommended to mitigate potential disruptions and financial losses.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The Play ransomware group is known for its atypical triple extortion methods, including encryption, data exfiltration, and direct victim contact via phone calls. Simulation of these tactics can help anticipate potential vulnerabilities and improve organizational resilience.
Indicators Development
Key indicators include the exploitation of vulnerabilities such as FortiOS CVE and Microsoft Exchange ProxyNotShell CVE. Monitoring these technical anomalies can facilitate early detection and response to threats.
Bayesian Scenario Modeling
Probabilistic modeling suggests a high likelihood of continued attacks targeting both Windows and Linux platforms, including VMware ESXi environments. This modeling aids in predicting future attack vectors and preparing defensive measures.
3. Implications and Strategic Risks
The widespread impact of the Play ransomware group poses significant risks to economic stability and national security. The use of sophisticated extortion techniques and exploitation of critical vulnerabilities could lead to cascading effects across various sectors, potentially disrupting supply chains and critical infrastructure.
4. Recommendations and Outlook
- Enhance cybersecurity protocols by patching known vulnerabilities and implementing robust monitoring systems.
- Conduct regular security audits and employee training to recognize and respond to phishing and extortion attempts.
- Scenario-based projections suggest that in the best case, proactive measures will mitigate most threats; in the worst case, failure to act could result in widespread operational disruptions.
5. Key Individuals and Entities
Sead, a freelance journalist based in Sarajevo, Bosnia and Herzegovina, has reported extensively on cybersecurity and ransomware issues.
6. Thematic Tags
national security threats, cybersecurity, ransomware, critical infrastructure