February 2026 Microsoft Patch Tuesday Addresses Six Exploited Zero-Day Vulnerabilities
Published on: 2026-02-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Patch Tuesday 6 exploited zero-days fixed in February 2026
1. BLUF (Bottom Line Up Front)
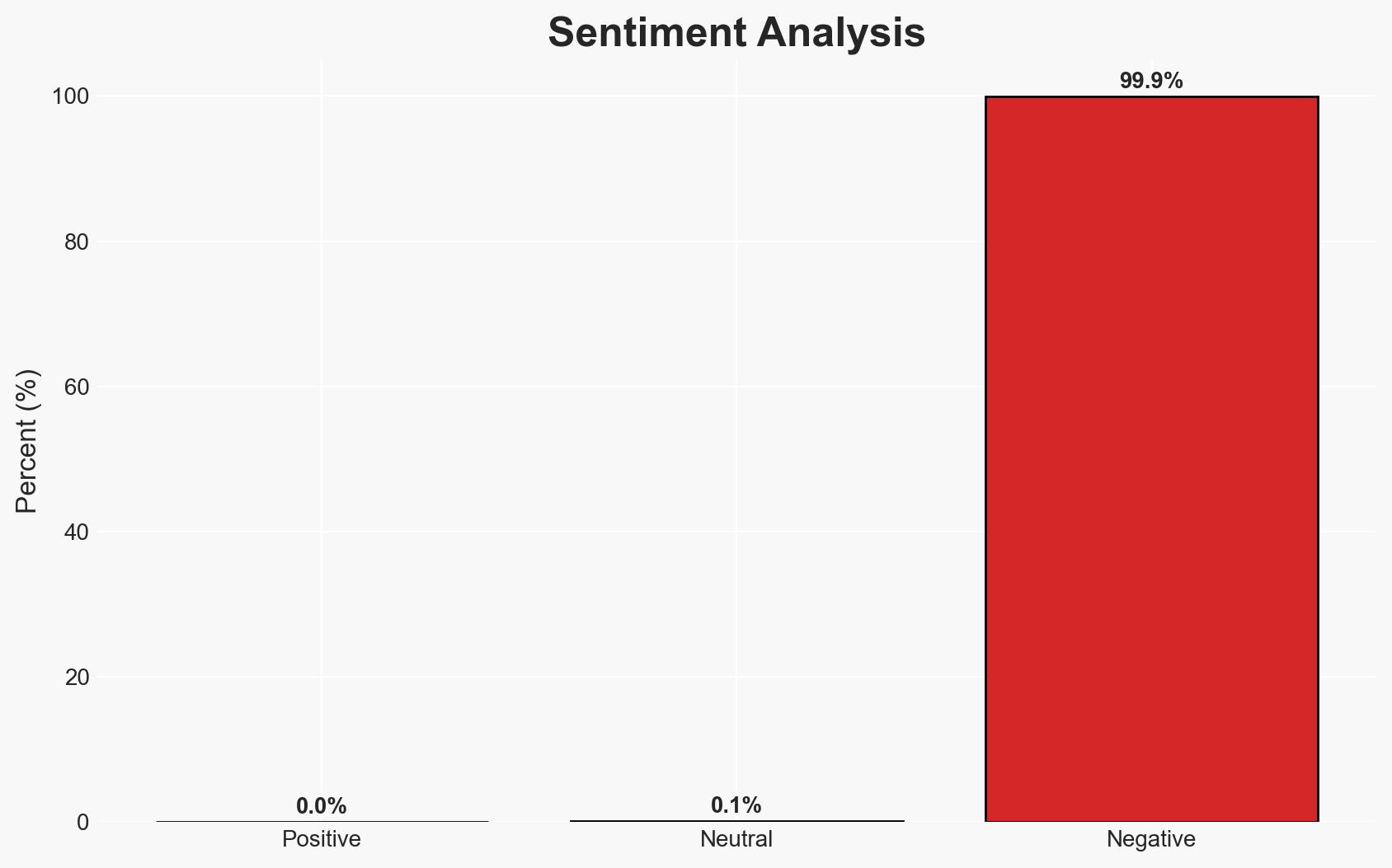
Microsoft’s February 2026 Patch Tuesday addressed over 50 vulnerabilities, including six zero-day exploits actively used in the wild. The most likely hypothesis is that these vulnerabilities, particularly those affecting Windows and Office products, pose significant risks to U.S. and Canadian entities, with moderate confidence in this assessment. Immediate patching is critical to mitigate potential exploitation. The overall confidence level in this judgment is moderate due to existing information gaps and potential for ongoing exploitation.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities were primarily exploited by financially motivated cybercriminals aiming to monetize access to compromised systems. Supporting evidence includes the nature of the vulnerabilities allowing privilege escalation and bypassing security features, which are attractive for ransomware and other financially driven attacks. However, the specific targeting of U.S. and Canadian entities suggests possible geopolitical motives, which remains uncertain.
- Hypothesis B: State-sponsored actors are exploiting these vulnerabilities to conduct espionage or disruptive operations against strategic targets. This hypothesis is supported by the targeting of critical infrastructure sectors in the U.S. and Canada. The involvement of sophisticated exploitation techniques and the timing of the attacks could indicate strategic intent beyond financial gain.
- Assessment: Hypothesis A is currently better supported due to the broader applicability of the vulnerabilities for financial exploitation and the lack of specific evidence pointing to state-sponsored actors. Indicators that could shift this judgment include attribution to known state actors or evidence of strategic targeting beyond financial sectors.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities are actively exploited by multiple threat actors; patching will significantly reduce exploitation risk; the disclosed vulnerabilities are the full extent of the current threat landscape.
- Information Gaps: Specific attribution to threat actors; detailed impact assessment on affected entities; full scope of exploitation tactics and techniques.
- Bias & Deception Risks: Potential bias in reporting due to reliance on vendor disclosures; risk of underestimating state-sponsored involvement due to lack of direct evidence.
4. Implications and Strategic Risks
The resolution of these vulnerabilities could temporarily reduce the threat landscape, but ongoing exploitation attempts may continue. The situation could evolve with new vulnerabilities or exploitation techniques emerging.
- Political / Geopolitical: Increased tensions if state-sponsored involvement is confirmed, potentially leading to diplomatic disputes or sanctions.
- Security / Counter-Terrorism: Heightened alert for critical infrastructure sectors; potential for increased cyber defense measures.
- Cyber / Information Space: Potential for increased cyber espionage or disruptive activities; emphasis on cybersecurity resilience and threat intelligence sharing.
- Economic / Social: Possible economic impact due to disruption of services; increased demand for cybersecurity solutions and expertise.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgent patching of affected systems; enhanced monitoring for exploitation attempts; dissemination of threat intelligence to relevant sectors.
- Medium-Term Posture (1–12 months): Strengthening cybersecurity partnerships; investment in threat detection and response capabilities; regular vulnerability assessments.
- Scenario Outlook:
- Best: Successful mitigation with no further exploitation, leading to improved cybersecurity posture.
- Worst: Continued exploitation with significant impact on critical infrastructure and economic sectors.
- Most-Likely: Intermittent exploitation attempts with gradual improvement in defensive measures.
6. Key Individuals and Entities
- Microsoft Threat Intelligence Center (MSTIC)
- Microsoft Security Response Center (MSRC)
- Google Threat Intelligence Group
- Office Product Group Security Team
- CrowdStrike
- 0patch research team
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
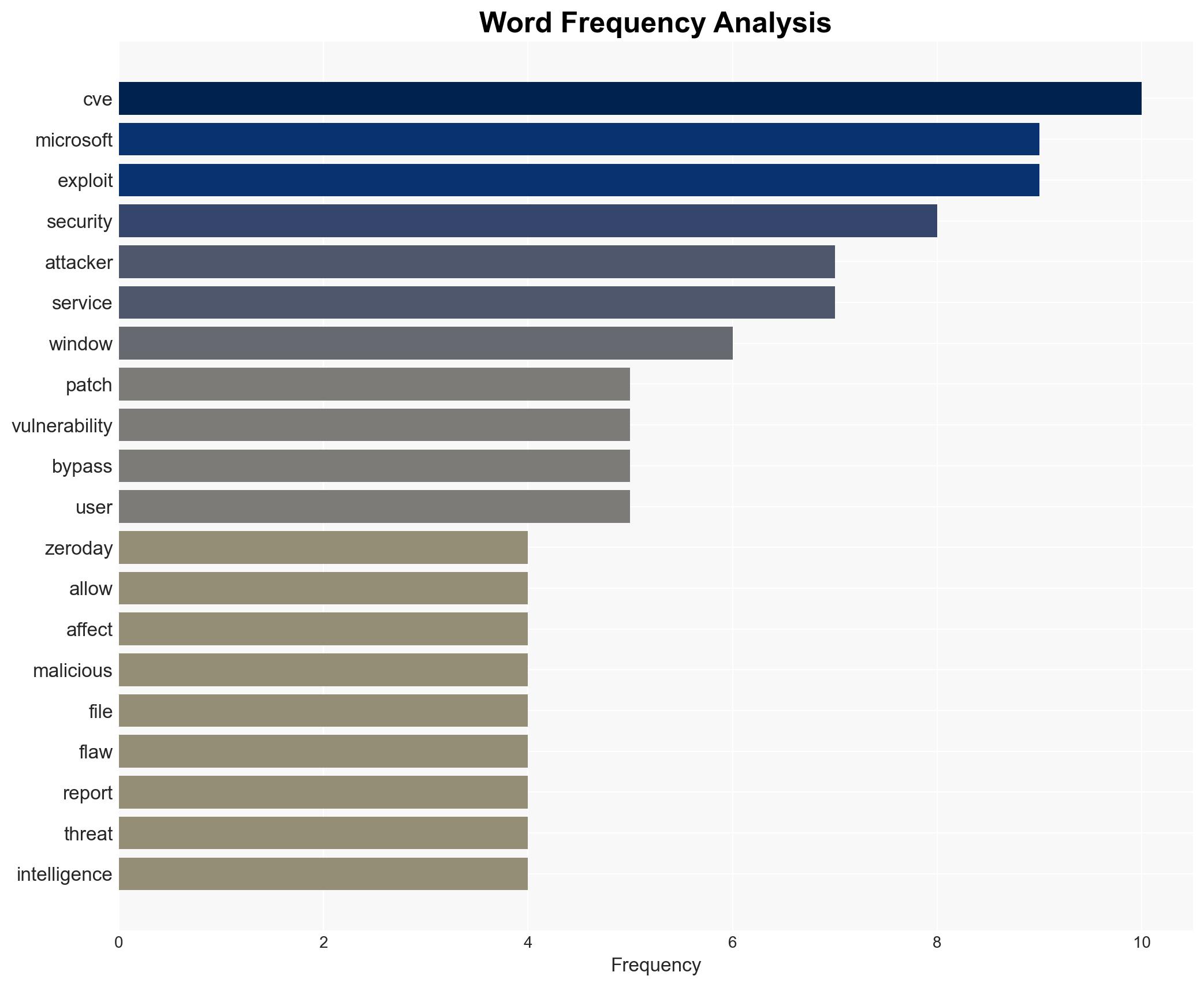
cybersecurity, zero-day vulnerabilities, patch management, cyber-espionage, threat intelligence, critical infrastructure, Microsoft
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us