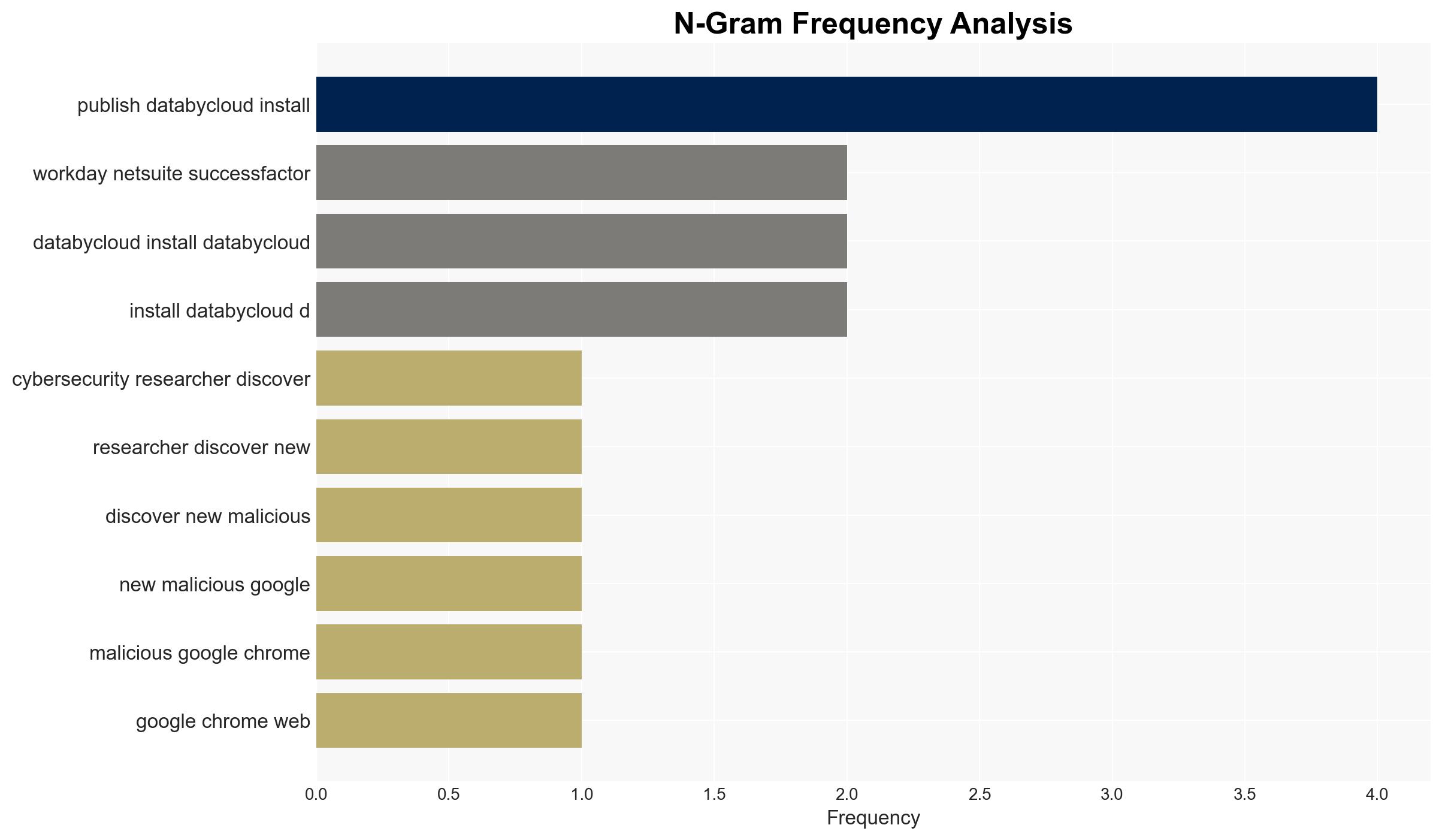
Five Rogue Chrome Extensions Imitate Workday and NetSuite to Compromise User Accounts
Published on: 2026-01-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Five Malicious Chrome Extensions Impersonate Workday and NetSuite to Hijack Accounts
1. BLUF (Bottom Line Up Front)
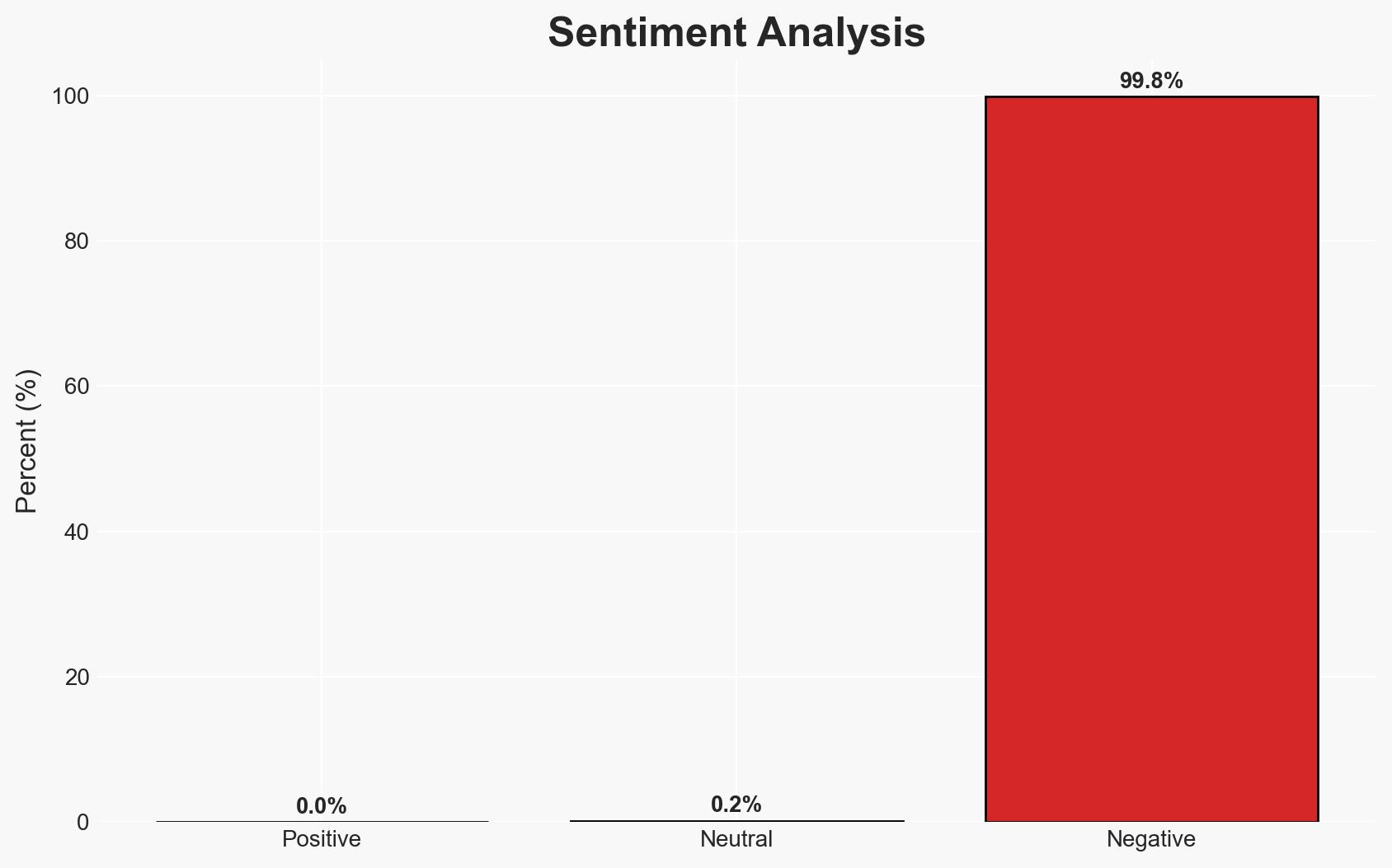
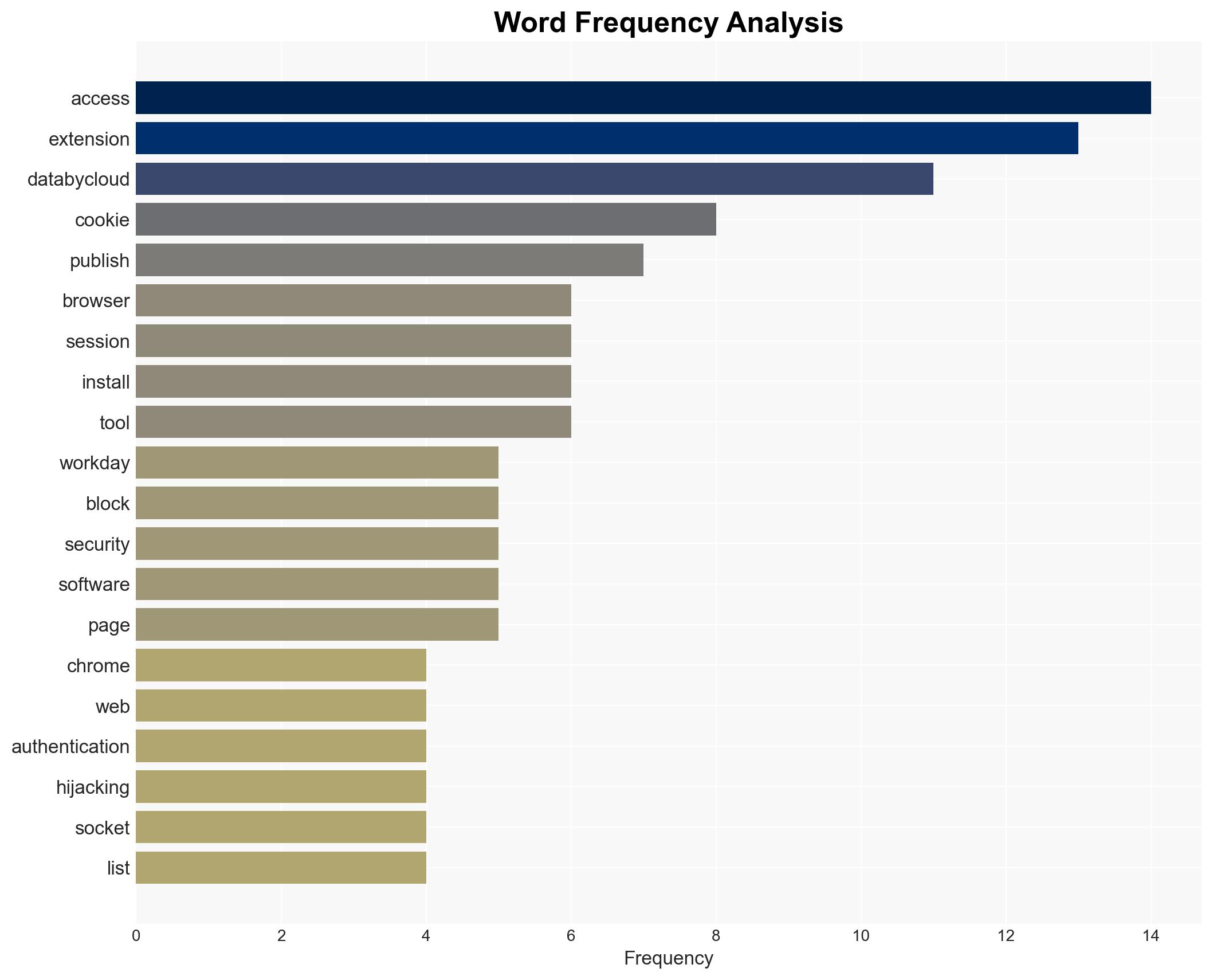
Five malicious Chrome extensions have been identified, targeting HR and ERP platforms to hijack user accounts. The campaign appears coordinated, leveraging session hijacking and DOM manipulation to exfiltrate data and block security responses. This poses a significant threat to organizations using these platforms, with moderate confidence in the assessment due to limited visibility into the attackers’ ultimate objectives.
2. Competing Hypotheses
- Hypothesis A: The extensions are part of a coordinated cyber-espionage campaign targeting specific organizations for strategic data theft. This is supported by the coordinated nature of the extensions and their sophisticated functionality. However, the ultimate intent remains unclear, and no direct links to state actors have been identified.
- Hypothesis B: The extensions are part of a financially motivated cybercrime operation aimed at selling access to compromised accounts. The presence of these extensions on third-party sites supports this hypothesis, but the complexity of the operation suggests a higher level of organization than typical financially motivated attacks.
- Assessment: Hypothesis A is currently better supported due to the coordinated and sophisticated nature of the attack, which is more indicative of strategic data theft. Future indicators such as the identification of specific targets or state actor involvement could further support this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: The extensions are primarily targeting enterprises using Workday and NetSuite; the attackers have the capability to maintain and update the malicious infrastructure; the removal from the Chrome Web Store limits but does not eliminate the threat.
- Information Gaps: The identity and ultimate objectives of the attackers; the full scope of affected organizations; potential links to broader cyber campaigns.
- Bias & Deception Risks: Potential confirmation bias towards attributing the attack to state actors; reliance on open-source data that may be incomplete or manipulated by the attackers.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of browser extensions and heightened security measures for enterprise platforms. The campaign’s evolution may reveal broader cyber-espionage or cybercrime networks.
- Political / Geopolitical: Potential diplomatic tensions if state actor involvement is confirmed.
- Security / Counter-Terrorism: Increased threat to enterprise security environments, necessitating enhanced monitoring and response capabilities.
- Cyber / Information Space: Potential for similar tactics to be used against other platforms, increasing the overall cyber threat landscape.
- Economic / Social: Financial losses for affected organizations and potential reputational damage, impacting stakeholder trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Organizations should audit installed browser extensions, enhance monitoring of authentication activities, and educate employees on the risks of third-party extensions.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing, and invest in advanced threat detection and response capabilities.
- Scenario Outlook: Best: Rapid identification and mitigation of the threat with minimal impact. Worst: Widespread data breaches and significant financial losses. Most-Likely: Continued targeted attacks with gradual improvements in organizational defenses.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, enterprise platforms, session hijacking, cyber-espionage, cybercrime, browser extensions, data exfiltration
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us