Flock Safety Exposed ArcGIS API Key in 53 Public Bundles, Compromising National Surveillance Data Access
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Flock Hardcoded the Password for America’s Surveillance Infrastructure 53 Times
1. BLUF (Bottom Line Up Front)
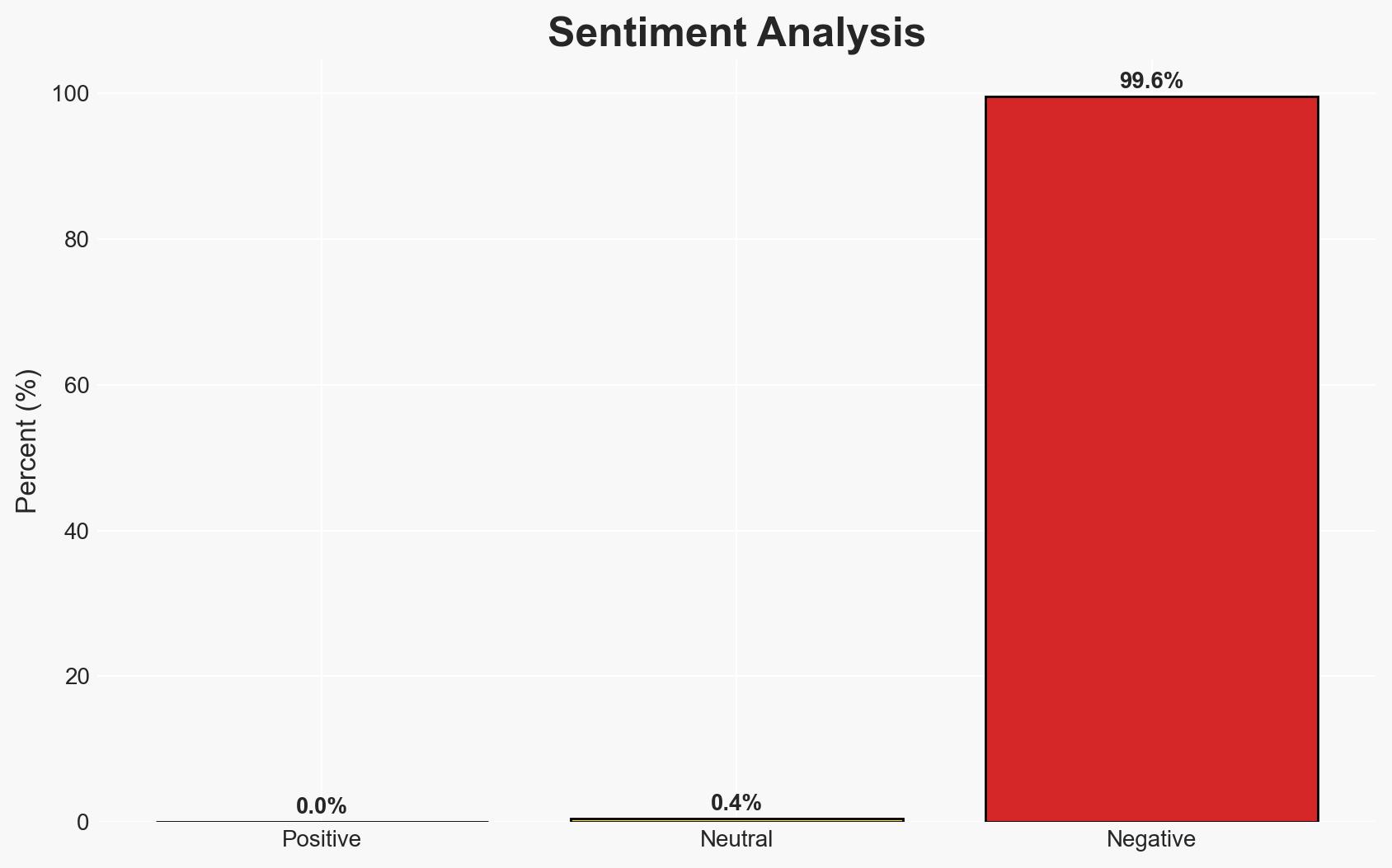
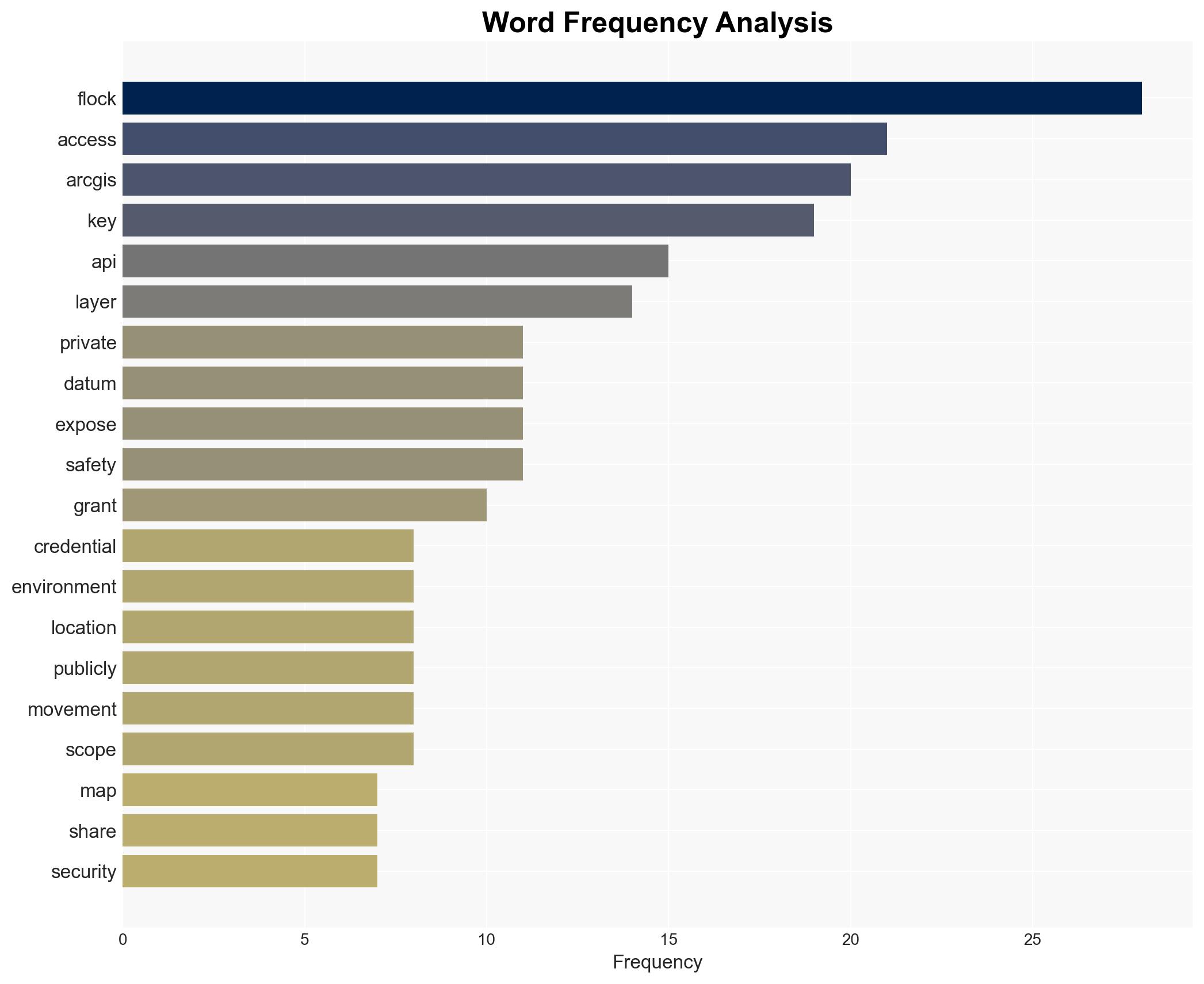
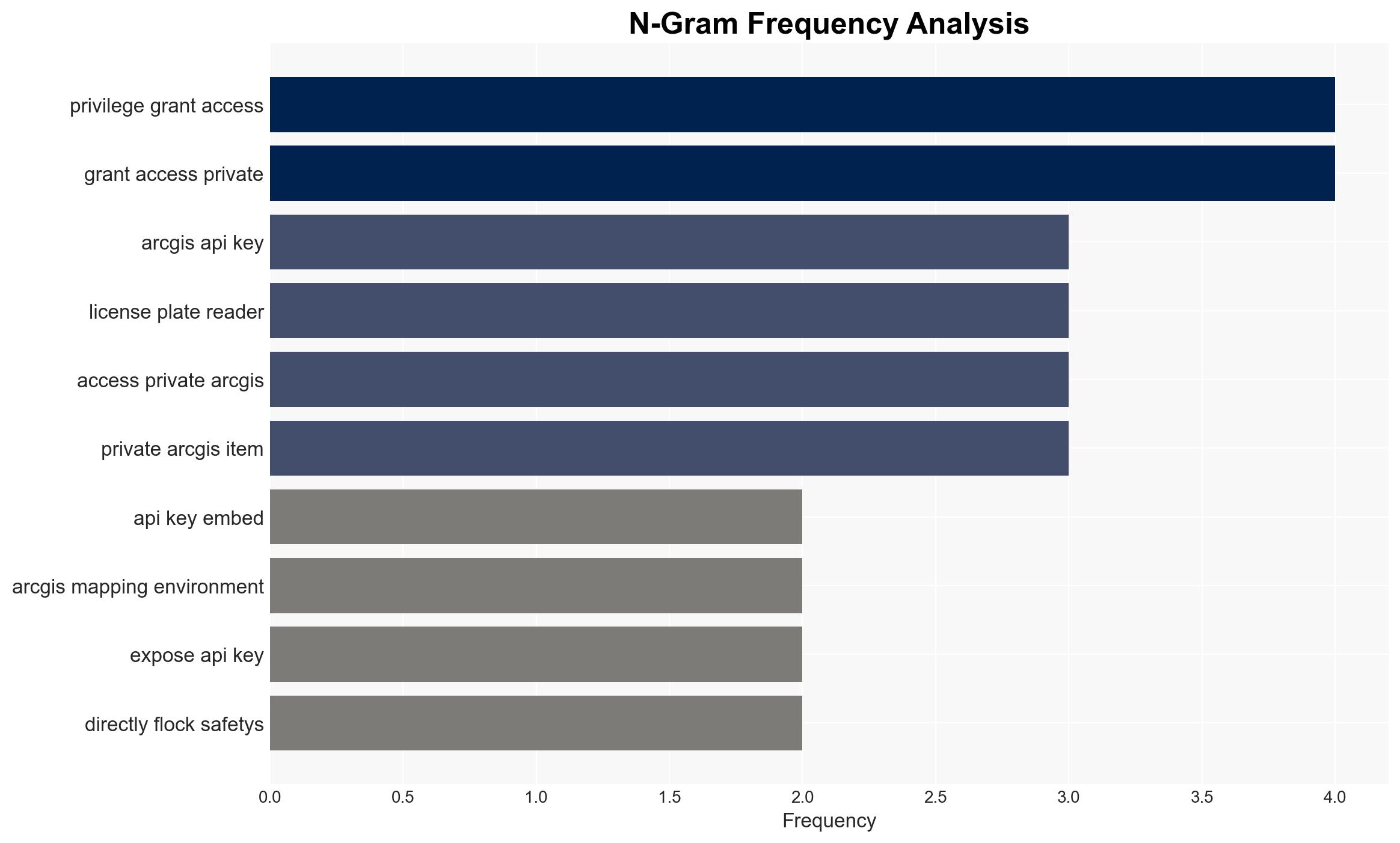
The exposure of a default ArcGIS API key in Flock Safety’s public-facing JavaScript bundles poses a significant security risk, potentially compromising sensitive surveillance data from approximately 12,000 deployments across the United States. This incident highlights vulnerabilities in Flock Safety’s data management practices, affecting law enforcement and private sector entities relying on this infrastructure. Overall confidence in this assessment is moderate due to the lack of detailed information on the extent of data accessed using the exposed key.
2. Competing Hypotheses
- Hypothesis A: The exposure of the API key was an oversight in Flock Safety’s software development process. Supporting evidence includes the presence of the key in development subdomains and its auto-generated nature. Key uncertainties involve whether any unauthorized access occurred and the duration of exposure.
- Hypothesis B: The exposure was a deliberate act to facilitate unauthorized access or surveillance. This hypothesis is less supported due to the lack of evidence indicating malicious intent or exploitation. However, the unrestricted nature of the key raises concerns about potential misuse.
- Assessment: Hypothesis A is currently better supported, given the technical nature of the oversight and the absence of clear indicators of deliberate exposure. Indicators such as evidence of unauthorized data access or internal communications suggesting intent could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Flock Safety did not intend for the API key to be publicly accessible; the exposure was not exploited for unauthorized access; the key was exposed due to a lack of robust security protocols.
- Information Gaps: Specifics on whether the key was used for unauthorized access, the duration of exposure, and any internal security audits conducted by Flock Safety.
- Bias & Deception Risks: Potential bias in assuming benign intent without evidence; risk of underestimating the threat due to lack of exploitation evidence; possible manipulation of public perception by Flock Safety to downplay the incident.
4. Implications and Strategic Risks
The exposure of the API key could lead to significant security vulnerabilities if exploited, affecting the integrity and confidentiality of surveillance data. This incident may prompt increased scrutiny of Flock Safety’s security practices and broader discussions on data privacy and surveillance.
- Political / Geopolitical: Potential for increased regulatory oversight and policy changes regarding surveillance infrastructure security.
- Security / Counter-Terrorism: Risk of compromised law enforcement operations and intelligence if data was accessed by malicious actors.
- Cyber / Information Space: Highlighting vulnerabilities in digital infrastructure, prompting a reevaluation of cybersecurity measures in similar systems.
- Economic / Social: Possible erosion of public trust in surveillance systems and increased demand for transparency and accountability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough security audit of Flock Safety’s systems, revoke and replace the exposed API key, and monitor for any unauthorized access attempts.
- Medium-Term Posture (1–12 months): Develop and implement enhanced security protocols, establish partnerships for cybersecurity support, and engage stakeholders to rebuild trust.
- Scenario Outlook:
- Best: No unauthorized access occurred, leading to improved security practices without significant fallout.
- Worst: Data was accessed and exploited, resulting in compromised operations and regulatory penalties.
- Most-Likely: Exposure prompts security enhancements and increased scrutiny, but no major breaches are confirmed.
6. Key Individuals and Entities
- Flock Safety
- Esri (ArcGIS provider)
- Law enforcement agencies using Flock Safety’s infrastructure
- Private sector entities relying on Flock Safety’s services
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, surveillance infrastructure, data privacy, law enforcement, public safety, information security, regulatory oversight
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us