Former Google Engineer Found Guilty of Economic Espionage for Stealing AI Trade Secrets for Chinese Startup
Published on: 2026-01-30
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ex-Google Engineer Convicted for Stealing 2000 AI Trade Secrets for China Startup
1. BLUF (Bottom Line Up Front)
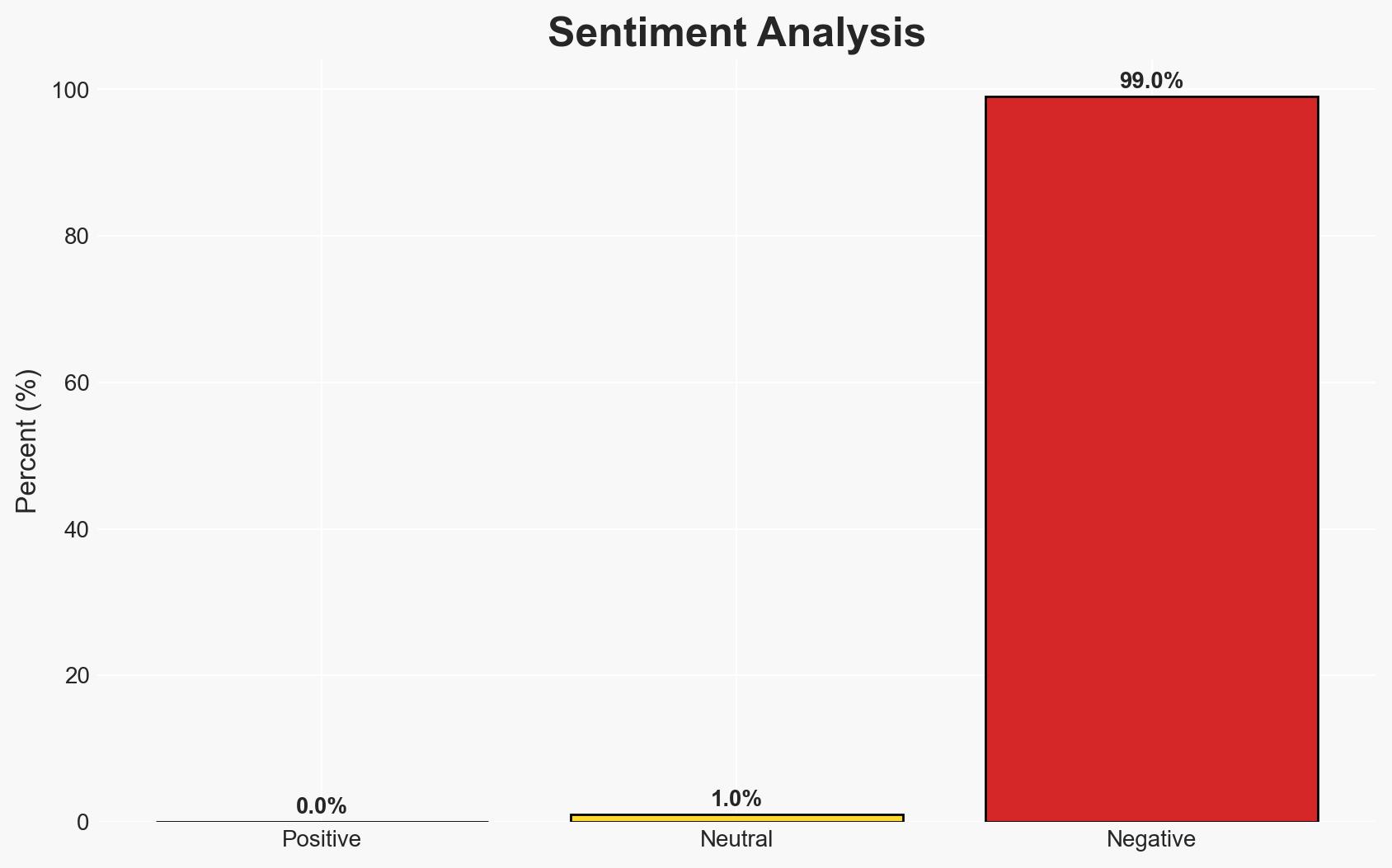
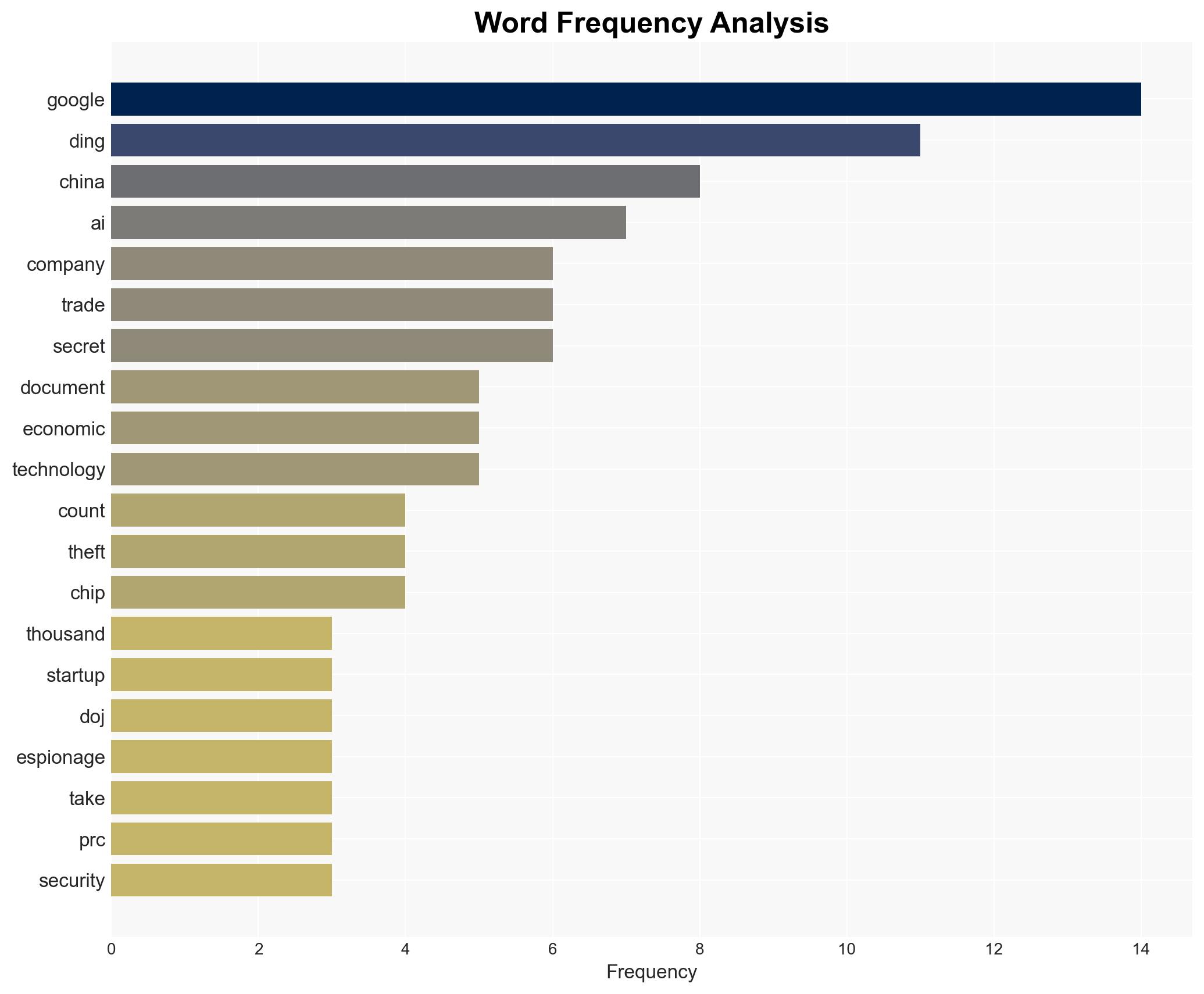
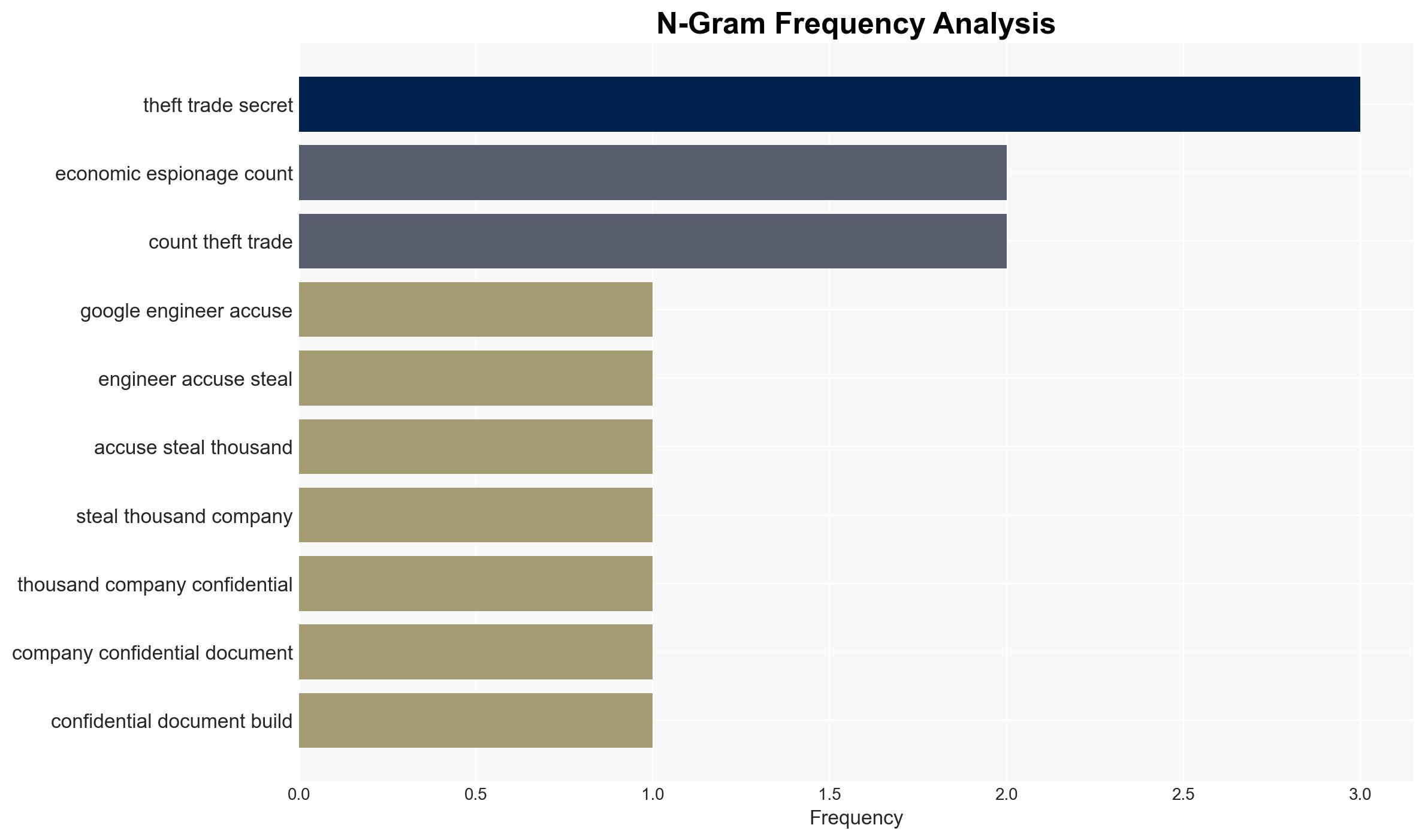
A former Google engineer, Linwei Ding, has been convicted of economic espionage and theft of trade secrets, transferring over 2,000 confidential AI-related documents to a Chinese startup. This incident highlights significant vulnerabilities in corporate security and the potential for foreign entities to exploit U.S. technological advancements. The most likely hypothesis is that this was a deliberate act of economic espionage aimed at strengthening China’s AI capabilities. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Linwei Ding engaged in economic espionage to benefit Chinese technological advancements, as evidenced by his actions to transfer sensitive AI-related documents to a Chinese startup. The conviction and detailed evidence of document transfers support this hypothesis, though the extent of direct state involvement remains uncertain.
- Hypothesis B: Ding acted independently for personal gain, without direct state sponsorship, motivated by career advancement opportunities in China. While his founding of a startup supports this, the alignment with Chinese interests and the scale of the theft suggest more organized intent.
- Assessment: Hypothesis A is currently better supported due to the scale of the theft and the strategic nature of the information involved. Indicators such as direct communications with Chinese entities or state actors could further solidify this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Ding had access to and knowledge of the value of the stolen documents; Chinese entities would benefit from the stolen information; Google’s security measures were insufficient to prevent the theft.
- Information Gaps: The level of direct involvement or support from the Chinese government; the full extent of damage to Google’s competitive position.
- Bias & Deception Risks: Potential bias in interpreting actions as state-sponsored without clear evidence; risk of overestimating the strategic value of the stolen documents.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of U.S.-China technology exchanges and heightened tensions in the tech sector. It may prompt stronger regulatory measures and corporate security practices.
- Political / Geopolitical: Potential for diplomatic tensions between the U.S. and China, influencing bilateral tech agreements.
- Security / Counter-Terrorism: Increased focus on protecting critical technology sectors from espionage.
- Cyber / Information Space: Heightened awareness and potential for retaliatory cyber operations or increased cyber defense measures.
- Economic / Social: Potential impact on investor confidence in tech firms’ ability to protect intellectual property.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of tech sector employees with access to sensitive information; engage in diplomatic channels to address potential state involvement.
- Medium-Term Posture (1–12 months): Develop partnerships with allies to strengthen collective cybersecurity measures; invest in advanced security technologies and employee training.
- Scenario Outlook: Best: Strengthened international cooperation on IP protection; Worst: Escalation of tech-based economic conflicts; Most-Likely: Incremental improvements in corporate security with ongoing geopolitical tensions.
6. Key Individuals and Entities
- Linwei Ding (aka Leon Ding) – Former Google engineer, convicted individual
- Shanghai Zhisuan Technologies Co. – Startup founded by Ding
- Google – Affected company
- Department of Justice (DoJ) – Prosecuting authority
7. Thematic Tags
cybersecurity, economic espionage, intellectual property theft, U.S.-China relations, AI technology, corporate security, technology transfer
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us