Former Western Sydney University student faces new charges for ongoing cyber crimes while on bail
Published on: 2025-12-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Alleged Sydney uni hacker charged with additional cyber crimes
1. BLUF (Bottom Line Up Front)
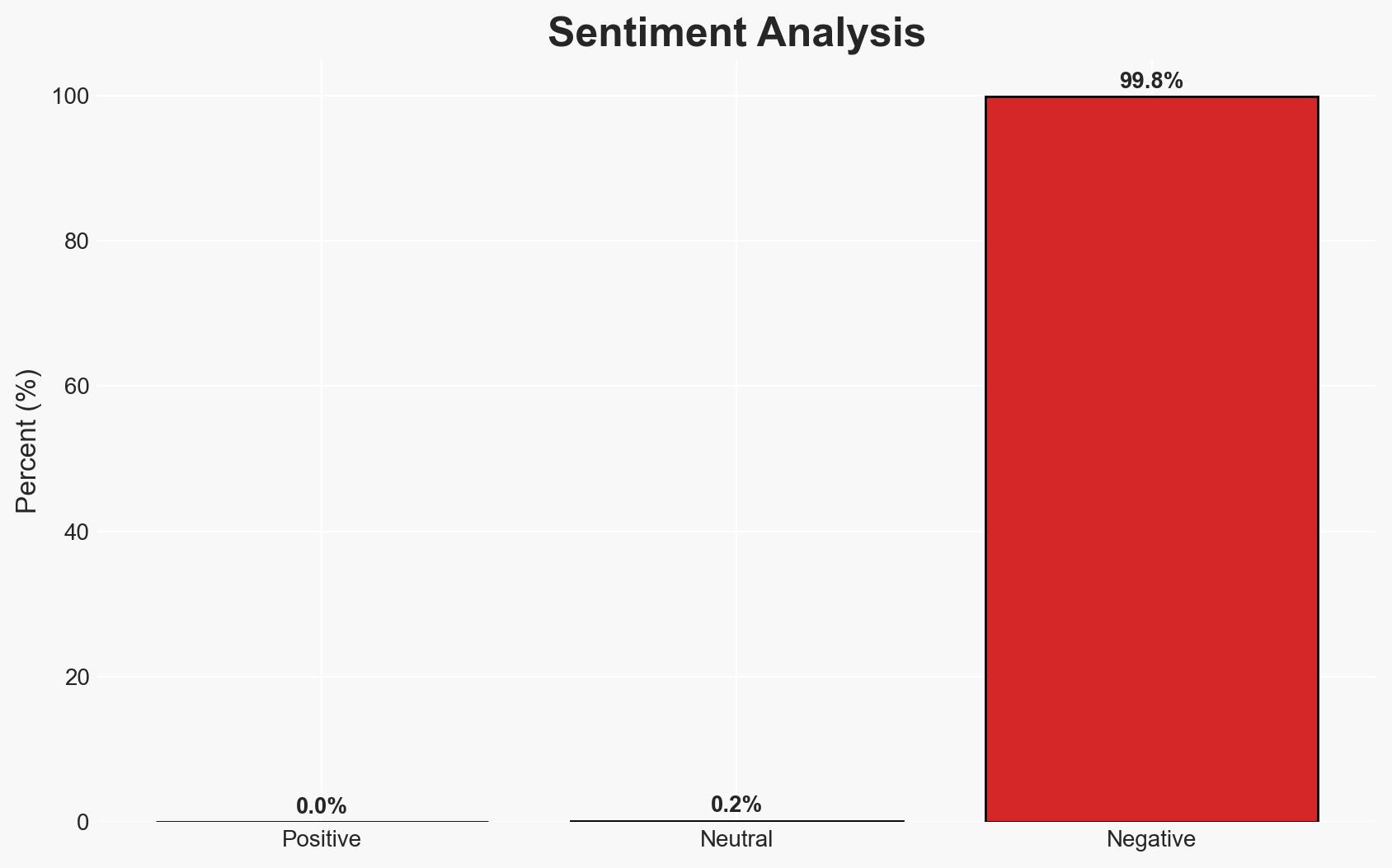
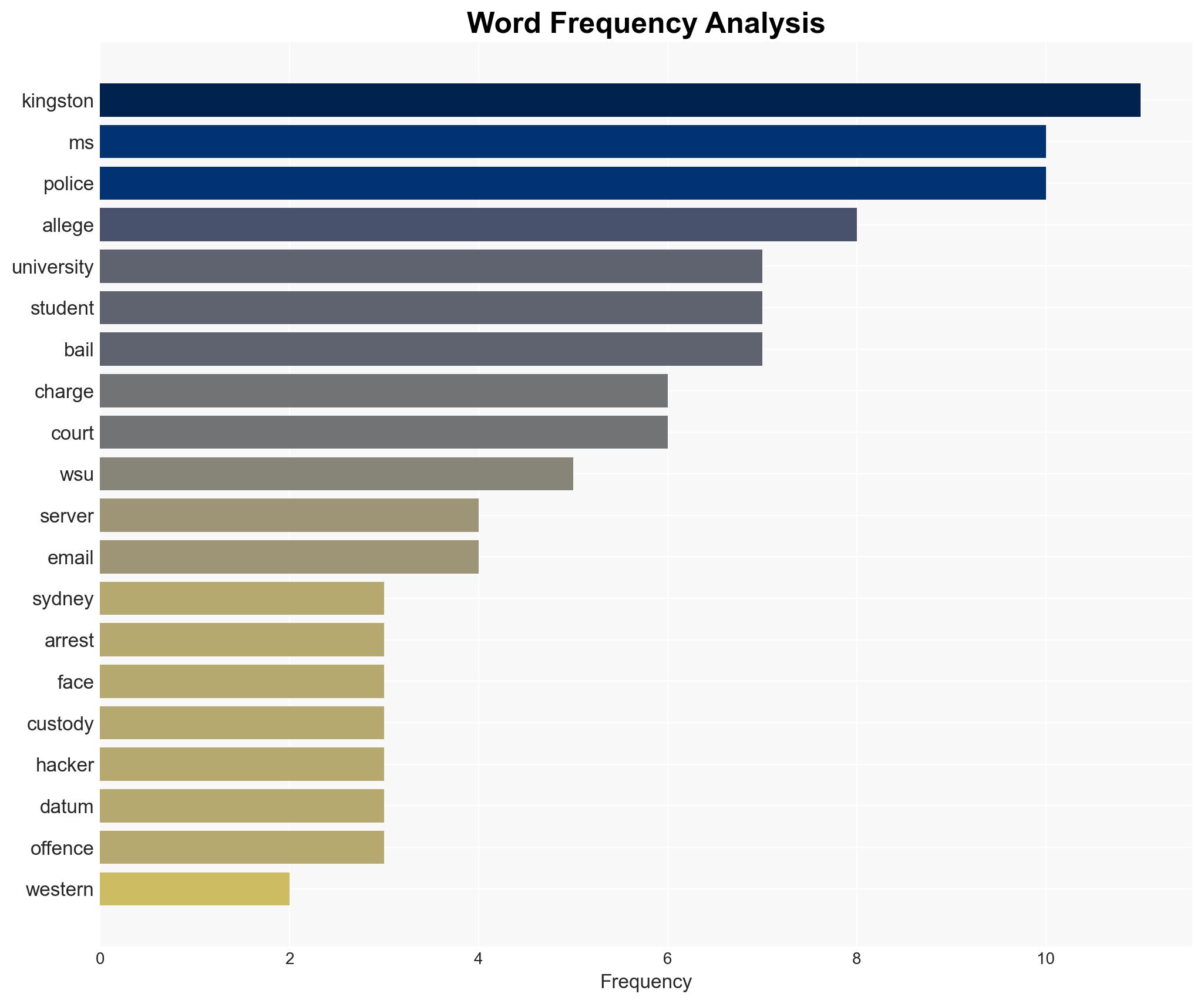
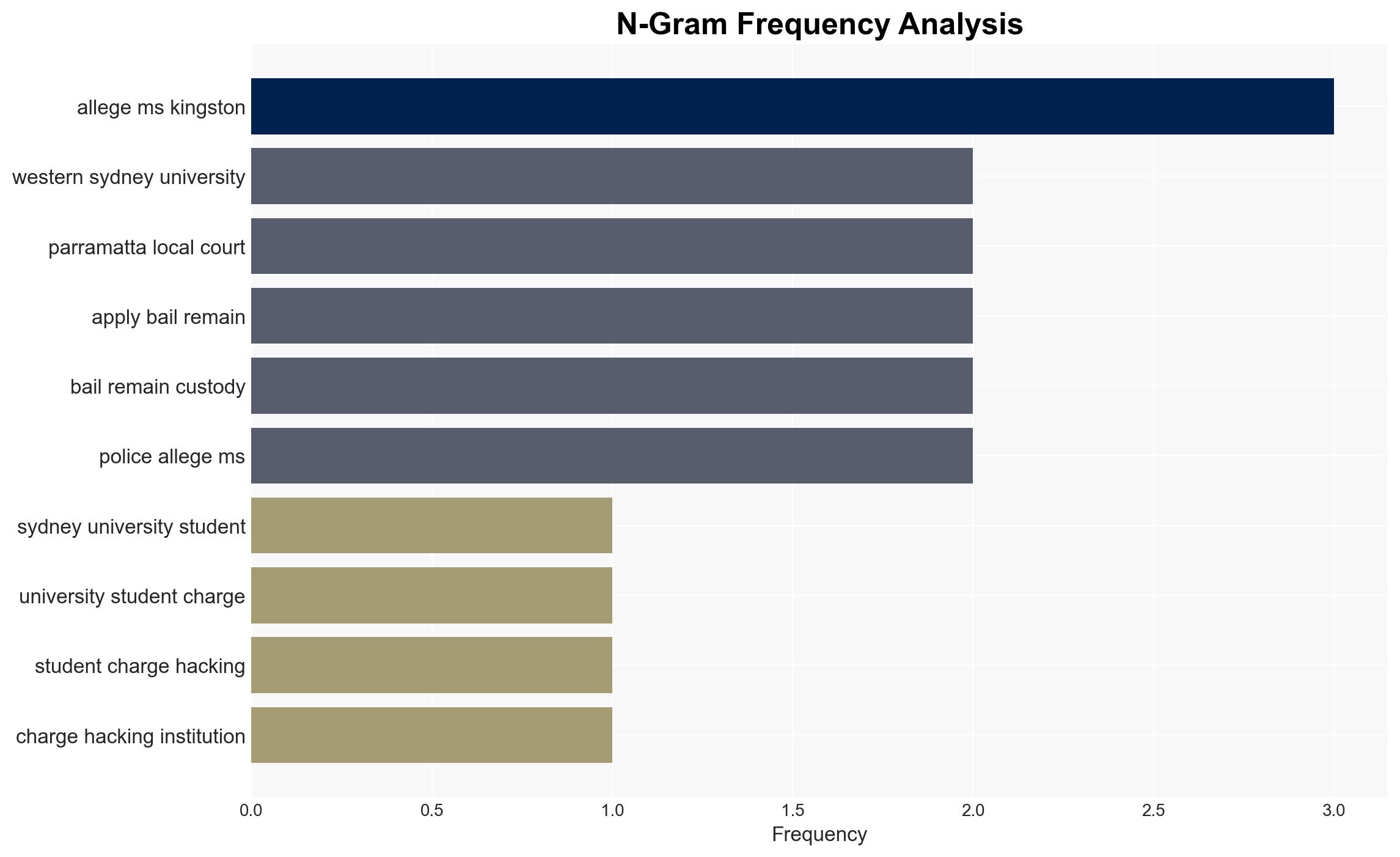
The arrest of Birdie Kingston, a former Western Sydney University student, for alleged repeated cyber intrusions into university systems highlights ongoing vulnerabilities in institutional cybersecurity. The most likely hypothesis is that Kingston acted independently, motivated by personal grievances. This situation affects university stakeholders and law enforcement, with moderate confidence in this assessment due to limited information on potential accomplices or external influences.
2. Competing Hypotheses
- Hypothesis A: Birdie Kingston acted independently in conducting cyber attacks against Western Sydney University, driven by personal motives such as altering grades and financial gain. Supporting evidence includes her previous actions to change grades and use free parking, and her continued activities while on bail. Key uncertainties include whether she had any external support or influence.
- Hypothesis B: Kingston was part of a larger group or influenced by external actors to target the university, possibly for broader objectives such as data theft for financial gain or reputational damage. Contradicting evidence includes the lack of identified accomplices and the personal nature of her initial motives.
- Assessment: Hypothesis A is currently better supported due to the personal nature of the initial motives and lack of evidence suggesting external involvement. Indicators that could shift this judgment include discovery of communications with other actors or evidence of broader strategic objectives.
3. Key Assumptions and Red Flags
- Assumptions: Kingston had the technical capability to conduct these attacks independently; her actions were primarily motivated by personal grievances; the university’s cybersecurity measures were insufficient to prevent repeated breaches.
- Information Gaps: Details on Kingston’s potential communications with other individuals or groups; comprehensive forensic analysis of the university’s systems to identify all breach vectors.
- Bias & Deception Risks: Potential bias in focusing solely on Kingston without exploring other possible actors; risk of deception if Kingston attempts to mislead investigators about her motives or actions.
4. Implications and Strategic Risks
This development underscores vulnerabilities in institutional cybersecurity and the potential for insider threats. It may lead to increased scrutiny of university cybersecurity practices and policies.
- Political / Geopolitical: Limited direct implications, though could influence policy discussions on cybersecurity in educational institutions.
- Security / Counter-Terrorism: Highlights the need for improved monitoring of insider threats and potential for similar incidents in other institutions.
- Cyber / Information Space: Demonstrates the ease with which individuals can exploit institutional vulnerabilities, potentially encouraging similar attacks.
- Economic / Social: Potential financial impact on the university due to data breaches and reputational damage, affecting student and staff trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic investigation of the university’s systems; enhance monitoring and access controls; engage with cybersecurity experts to assess and mitigate vulnerabilities.
- Medium-Term Posture (1–12 months): Develop and implement comprehensive cybersecurity training for staff and students; establish partnerships with law enforcement and cybersecurity agencies for ongoing threat intelligence sharing.
- Scenario Outlook:
- Best: Improved cybersecurity measures prevent future breaches, restoring confidence (trigger: successful implementation of new protocols).
- Worst: Continued breaches lead to significant data loss and reputational damage (trigger: additional successful attacks).
- Most-Likely: Incremental improvements in security with occasional minor breaches (trigger: partial implementation of recommendations).
6. Key Individuals and Entities
- Birdie Kingston, former Western Sydney University student
- Western Sydney University
- NSW Police
- Australian Federal Police
- Joint Policing Cybercrime Coordination Centre
7. Thematic Tags
Cybersecurity, insider threat, data breach, law enforcement, university security, cybercrime, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us