Formerly convicted twins charged with deleting government databases after termination from federal contractor…
Published on: 2025-12-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Twins who hacked State Dept hired to work for gov again now charged with deleting databases
1. BLUF (Bottom Line Up Front)
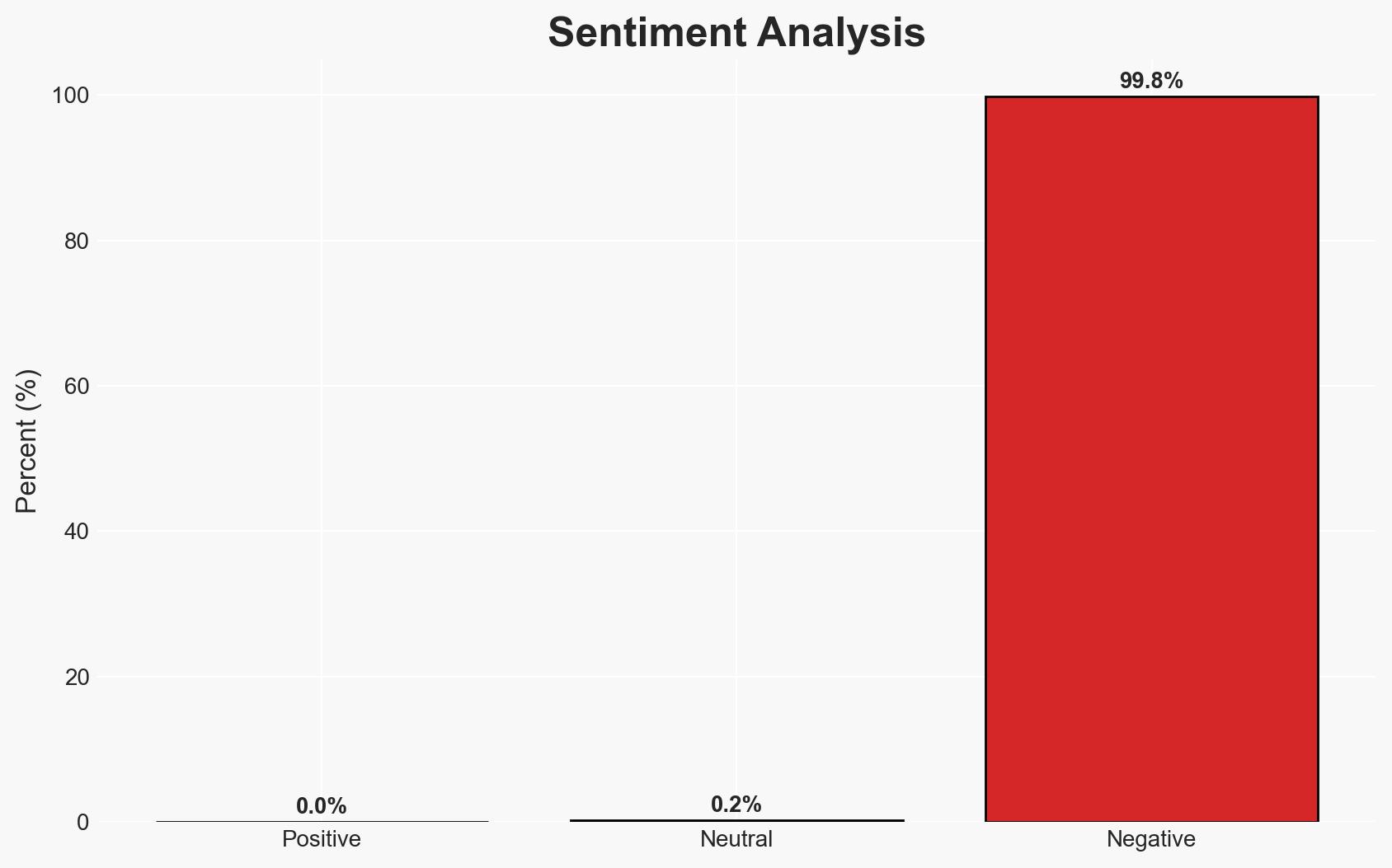
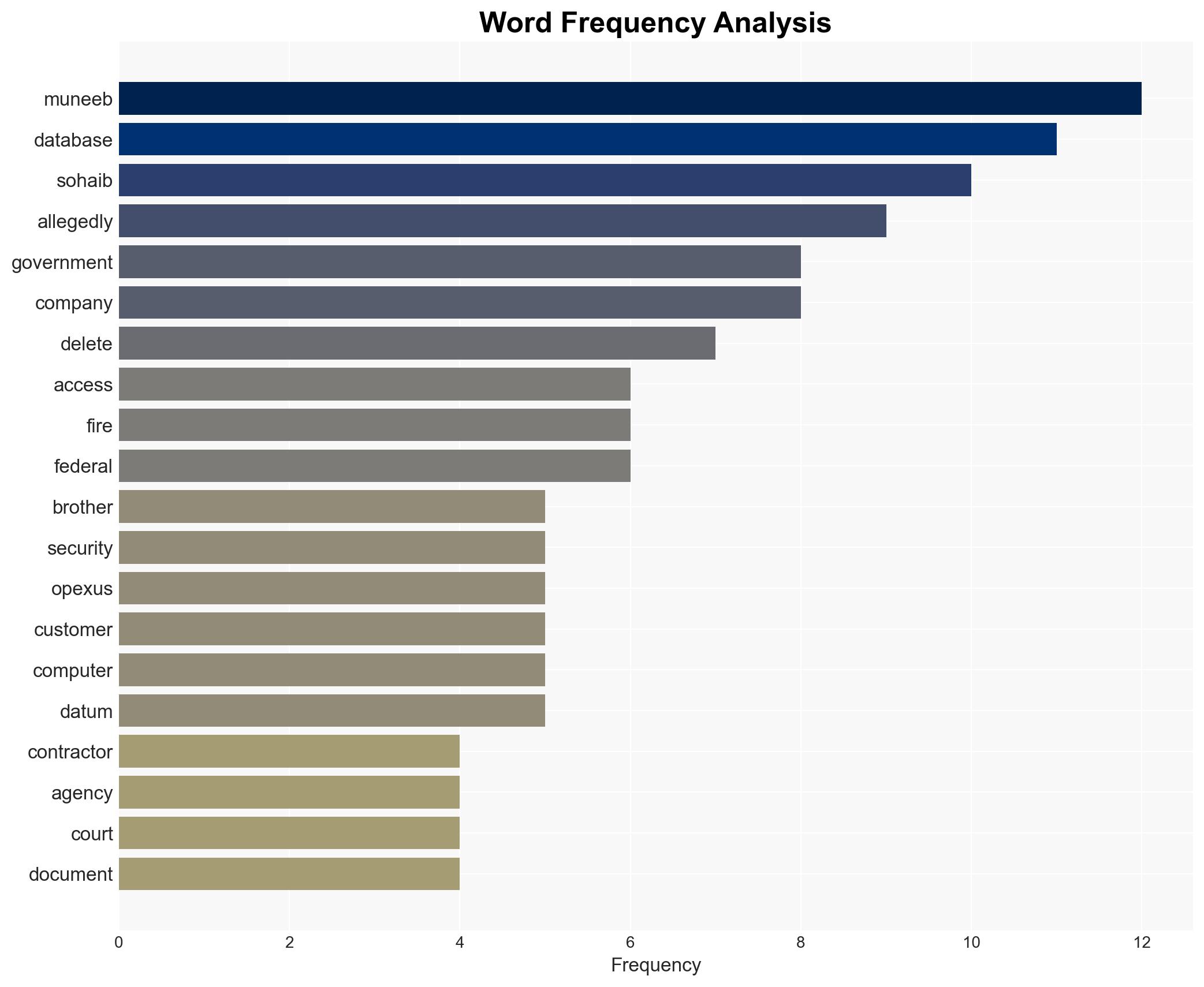
The indictment of Muneeb and Sohaib Akhter for deleting nearly 100 government databases highlights significant vulnerabilities in contractor vetting and access management protocols. The incident underscores the need for enhanced cybersecurity measures within federal contracting entities. The most likely hypothesis is that the brothers exploited residual access post-termination, facilitated by inadequate deactivation procedures. This assessment is made with moderate confidence due to incomplete information on internal security protocols and the extent of the breach’s impact.
2. Competing Hypotheses
- Hypothesis A: The Akhter brothers exploited residual access due to inadequate deactivation protocols, allowing them to delete databases post-termination. Supporting evidence includes the rapid timeline of database deletions following their firing and the use of AI tools to facilitate their actions. Key uncertainties include the specific internal security measures in place at Opexus.
- Hypothesis B: The breach was facilitated by an insider within Opexus who provided the Akhter brothers with unauthorized access post-termination. While this could explain the rapid access post-firing, there is currently no direct evidence supporting insider collusion.
- Assessment: Hypothesis A is currently better supported due to the immediate timeline of events and the brothers’ known technical capabilities. Indicators that could shift this judgment include evidence of insider assistance or more detailed information on Opexus’s access management failures.
3. Key Assumptions and Red Flags
- Assumptions: The Akhter brothers acted independently without insider assistance; Opexus’s access management protocols were insufficient; the use of AI tools was pivotal in executing the breach.
- Information Gaps: Detailed internal security protocols of Opexus; extent of data loss impact on government operations; potential prior warnings or red flags about the brothers’ activities.
- Bias & Deception Risks: Potential bias in source reporting from Opexus; risk of underestimating insider threat potential; deception indicators in the brothers’ use of AI tools to obscure their actions.
4. Implications and Strategic Risks
This incident could lead to increased scrutiny and regulatory pressure on federal contractors to enhance cybersecurity protocols, potentially influencing broader federal cybersecurity policies.
- Political / Geopolitical: Potential for increased legislative oversight on contractor cybersecurity practices.
- Security / Counter-Terrorism: Heightened awareness of insider threats and residual access risks within federal agencies.
- Cyber / Information Space: Increased focus on AI’s role in facilitating cybercrimes and the need for robust access management systems.
- Economic / Social: Potential reputational damage to Opexus and similar contractors, impacting future government contracts and trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of access management protocols across federal contractors; enhance monitoring of terminated employees’ access.
- Medium-Term Posture (1–12 months): Develop partnerships for sharing best practices in cybersecurity among federal contractors; invest in AI-driven security solutions to detect and prevent unauthorized access.
- Scenario Outlook:
- Best: Strengthened cybersecurity measures prevent future breaches, restoring trust in federal contractors.
- Worst: Continued vulnerabilities lead to further breaches, prompting severe regulatory actions.
- Most-Likely: Incremental improvements in security protocols with ongoing challenges in insider threat management.
6. Key Individuals and Entities
- Muneeb Akhter
- Sohaib Akhter
- Opexus (Washington-based firm)
- US Federal Government Agencies (affected by database deletions)
7. Thematic Tags
Cybersecurity, insider threat, federal contractors, AI in cybercrime, access management, government data breach, regulatory oversight
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us