Fortinet FortiGate Devices Targeted in Active Exploits of Critical SAML SSO Authentication Bypass Vulnerabili…
Published on: 2025-12-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Fortinet FortiGate Under Active Attack Through SAML SSO Authentication Bypass
1. BLUF (Bottom Line Up Front)
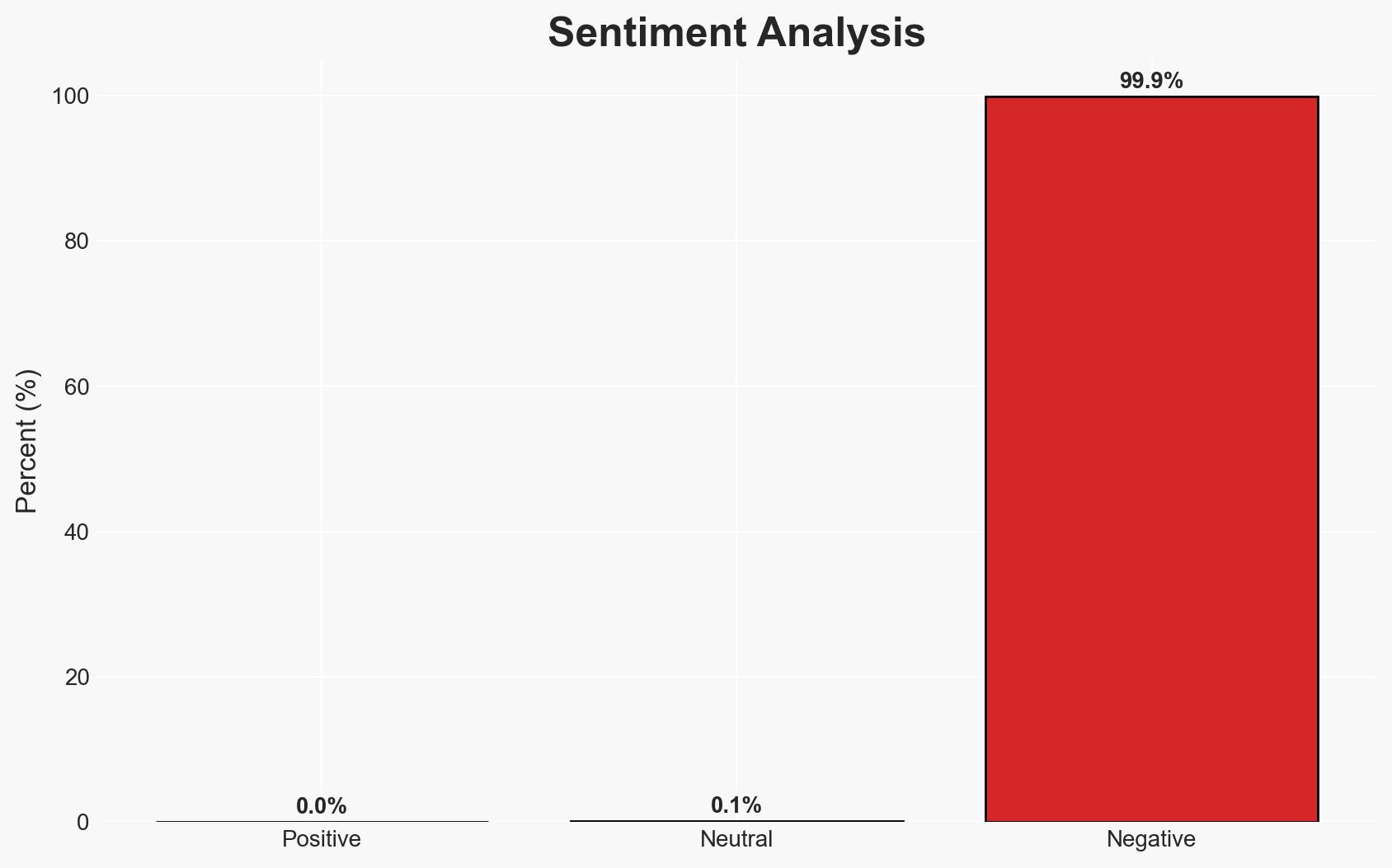
Threat actors are actively exploiting two critical vulnerabilities in Fortinet FortiGate devices, leveraging SAML SSO authentication bypasses. The attacks are opportunistic, targeting a small number of networks, with potential for wider impact if not mitigated. The overall confidence in this assessment is moderate, given the early stage of the campaign and limited attribution data.
2. Competing Hypotheses
- Hypothesis A: The attacks are opportunistic, conducted by unsophisticated threat actors exploiting publicly disclosed vulnerabilities for financial gain. This is supported by the use of common hosting providers and the lack of specific attribution. However, the early stage of the campaign and limited affected networks introduce uncertainty.
- Hypothesis B: The attacks are a precursor to a larger, coordinated campaign by a sophisticated actor aiming to establish persistent access for strategic objectives. The rapid exploitation post-disclosure and targeting of administrative accounts could support this, but the lack of complex tactics and broader impact contradicts it.
- Assessment: Hypothesis A is currently better supported due to the opportunistic nature of the attacks and the use of common infrastructure. Indicators such as increased sophistication or broader targeting could shift this assessment towards Hypothesis B.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities are being exploited primarily due to their high severity and recent disclosure. The threat actors lack sophisticated capabilities. FortiCloud SSO is enabled in a significant number of vulnerable systems.
- Information Gaps: Specific attribution of the threat actors involved. Detailed understanding of the attackers’ end goals. Comprehensive data on the number of affected networks.
- Bias & Deception Risks: Potential bias towards assuming unsophisticated actors due to early-stage observations. Risk of underestimating the threat if the actors are masking their true capabilities.
4. Implications and Strategic Risks
This development could lead to increased cyber threats against organizations using Fortinet devices, potentially impacting national security and economic stability if not addressed. The situation may evolve into a more sophisticated campaign if left unchecked.
- Political / Geopolitical: Escalation could occur if state-sponsored actors are involved, leading to geopolitical tensions.
- Security / Counter-Terrorism: Increased risk of unauthorized access to critical infrastructure and sensitive data.
- Cyber / Information Space: Potential for widespread data breaches and information manipulation if vulnerabilities are not patched.
- Economic / Social: Disruption to businesses reliant on Fortinet devices, leading to economic losses and reduced trust in cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Apply patches immediately, disable FortiCloud SSO, and restrict management interface access. Monitor for indicators of compromise and reset compromised credentials.
- Medium-Term Posture (1–12 months): Enhance network security protocols, conduct regular vulnerability assessments, and foster partnerships for threat intelligence sharing.
- Scenario Outlook:
- Best: Rapid patching and mitigation efforts prevent further exploitation, maintaining network security.
- Worst: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Continued opportunistic attacks with limited impact if mitigations are promptly applied.
6. Key Individuals and Entities
- Arctic Wolf Labs
- Fortinet
- The Constant Company LLC
- Bl Networks
- Kaopu Cloud HK Limited
- U.S. Cybersecurity and Infrastructure Security Agency (CISA)
7. Thematic Tags
cybersecurity, vulnerability exploitation, Fortinet, SAML SSO, authentication bypass, network security, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us