Fortinet initiates fixes for critical zero-day CVE-2026-24858 exploited in FortiCloud SSO attacks
Published on: 2026-01-28
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Fortinet starts patching exploited FortiCloud SSO zero-day CVE-2026-24858
1. BLUF (Bottom Line Up Front)
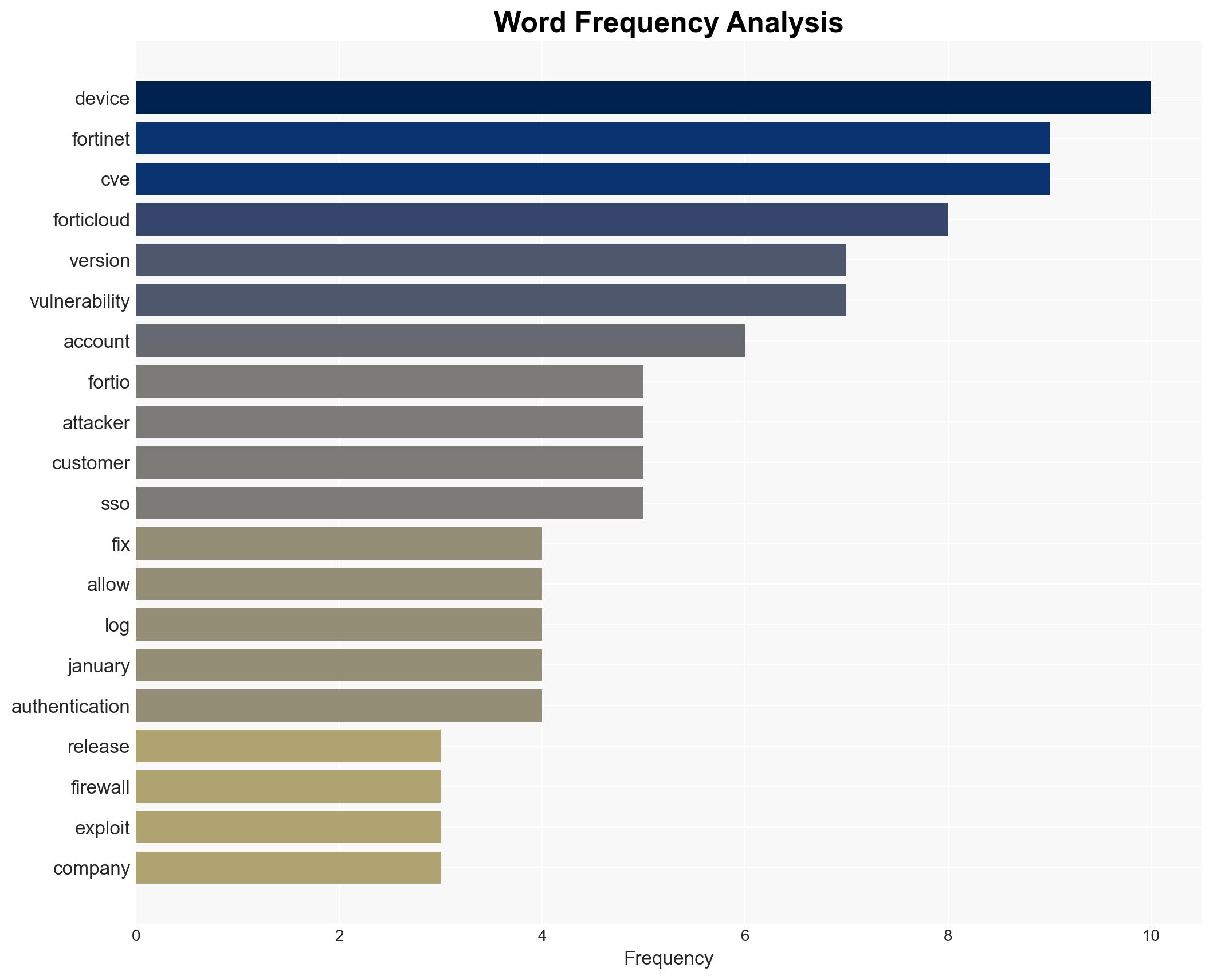
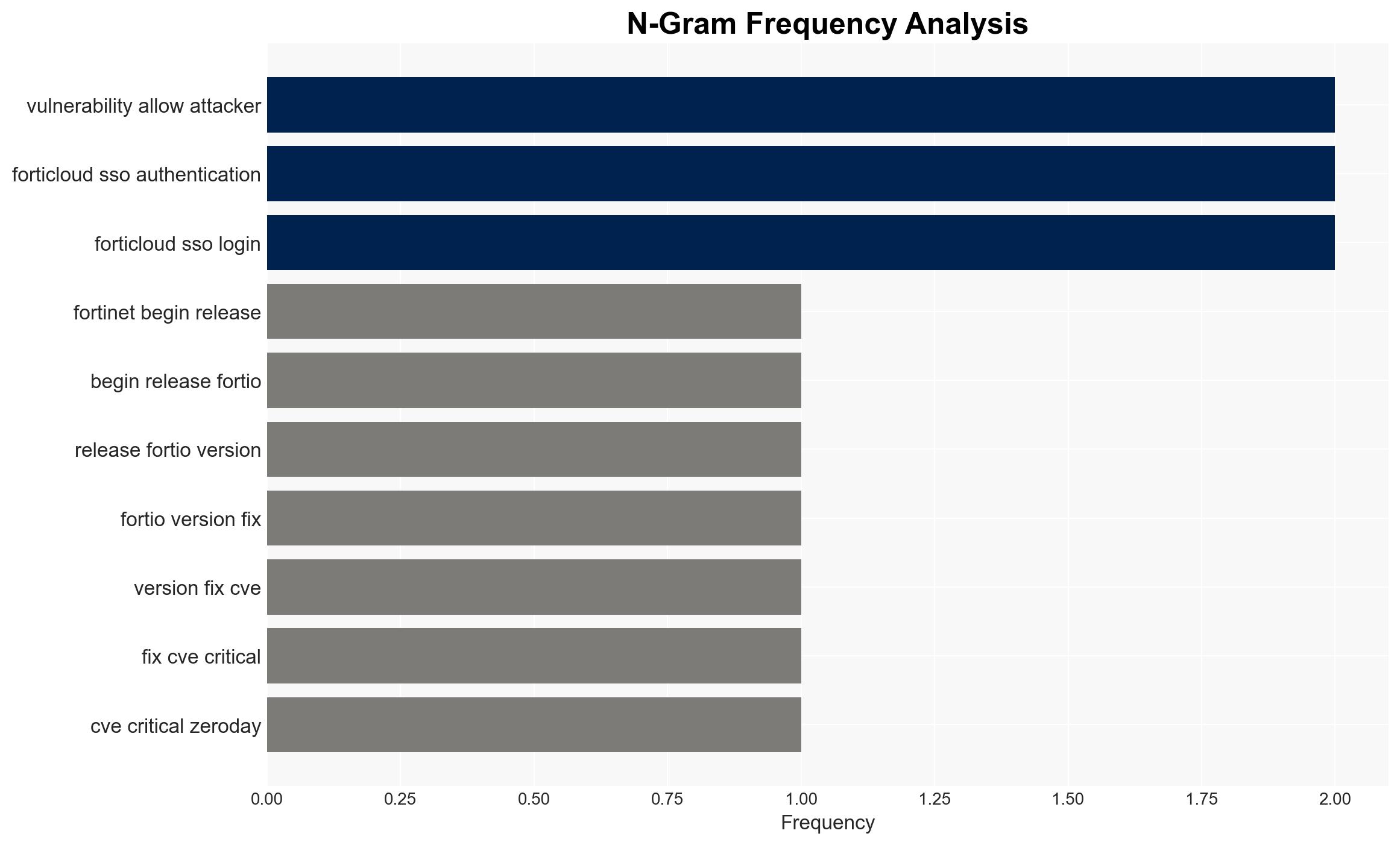
Fortinet has released patches for a critical zero-day vulnerability, CVE-2026-24858, affecting FortiCloud SSO, which was actively exploited to access FortiGate firewalls. This vulnerability poses significant risks to organizations using Fortinet products with FortiCloud SSO enabled. The most likely hypothesis is that the vulnerability was exploited by actors with specific knowledge of Fortinet systems. Overall, there is moderate confidence in this assessment due to limited information on the attackers’ identity and motives.
2. Competing Hypotheses
- Hypothesis A: The exploitation of CVE-2026-24858 was conducted by sophisticated threat actors with insider knowledge or access to Fortinet’s systems. This is supported by the targeted nature of the attacks and the use of FortiCloud accounts. However, the identity and exact methods of the attackers remain unclear.
- Hypothesis B: The exploitation was opportunistic, carried out by cybercriminals who discovered the vulnerability independently. This hypothesis is less supported due to the complexity of the attack and the need for specific FortiCloud accounts.
- Assessment: Hypothesis A is currently better supported due to the targeted exploitation and the use of specific FortiCloud accounts, suggesting a level of sophistication and insider knowledge. Key indicators that could shift this judgment include the identification of the attackers or further details on how the vulnerability was discovered.
3. Key Assumptions and Red Flags
- Assumptions: Fortinet’s patches are effective; the attackers had prior knowledge of Fortinet systems; the vulnerability was not widely known before exploitation.
- Information Gaps: The identity and motives of the attackers; the full scope of the vulnerability’s exploitation; potential other vulnerabilities in Fortinet products.
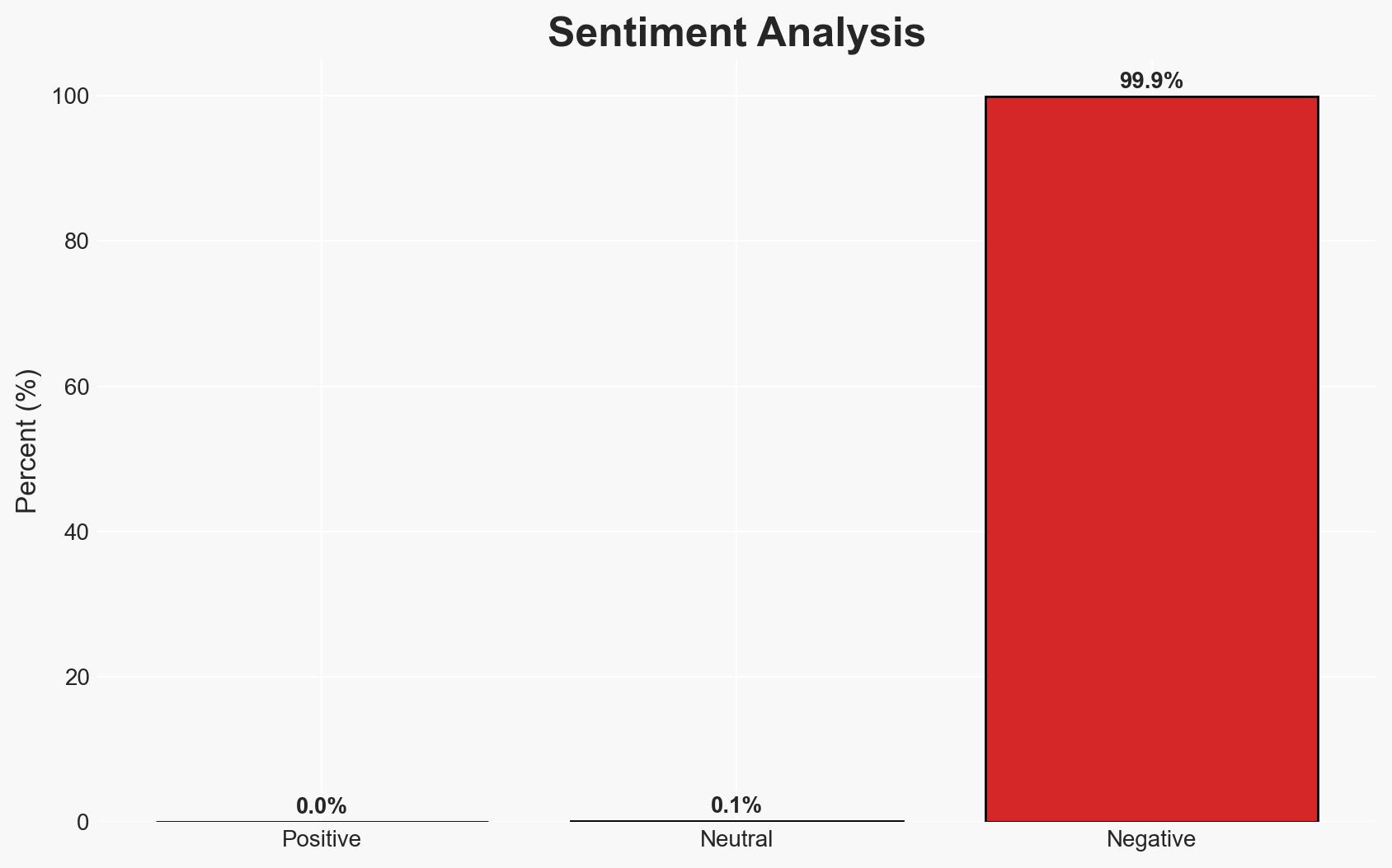
- Bias & Deception Risks: Potential bias in Fortinet’s reporting to minimize perceived impact; lack of independent verification of the vulnerability’s exploitation scope.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on Fortinet’s security practices and impact customer trust. If the vulnerability is not fully mitigated, it may lead to further exploitation attempts.
- Political / Geopolitical: Potential for increased regulatory pressure on cybersecurity standards and practices.
- Security / Counter-Terrorism: Heightened threat environment for organizations using Fortinet products, necessitating increased vigilance and security measures.
- Cyber / Information Space: Potential for further cyber operations targeting similar vulnerabilities in other systems.
- Economic / Social: Possible financial losses for affected organizations and reputational damage to Fortinet.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Organizations should immediately apply available patches, review security configurations, and monitor for indicators of compromise.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, enhance internal cybersecurity training, and conduct regular security audits.
- Scenario Outlook: Best: Vulnerability fully mitigated with no further incidents. Worst: Continued exploitation leading to significant breaches. Most-Likely: Partial mitigation with sporadic exploitation attempts.
6. Key Individuals and Entities
- Fortinet (vendor of affected products)
- Not clearly identifiable from open sources in this snippet (attackers)
7. Thematic Tags
cybersecurity, zero-day vulnerability, Fortinet, network security, threat actors, cyber defense, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us