Free Ebooks on Cybersecurity: Explore Generative AI, RAG, and More Bestsellers for a Limited Time
Published on: 2025-11-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: FREE EBOOKS The Art of Cyber Security Unlocking Data with Generative AI and RAG Four More Best Selling Titles
1. BLUF (Bottom Line Up Front)
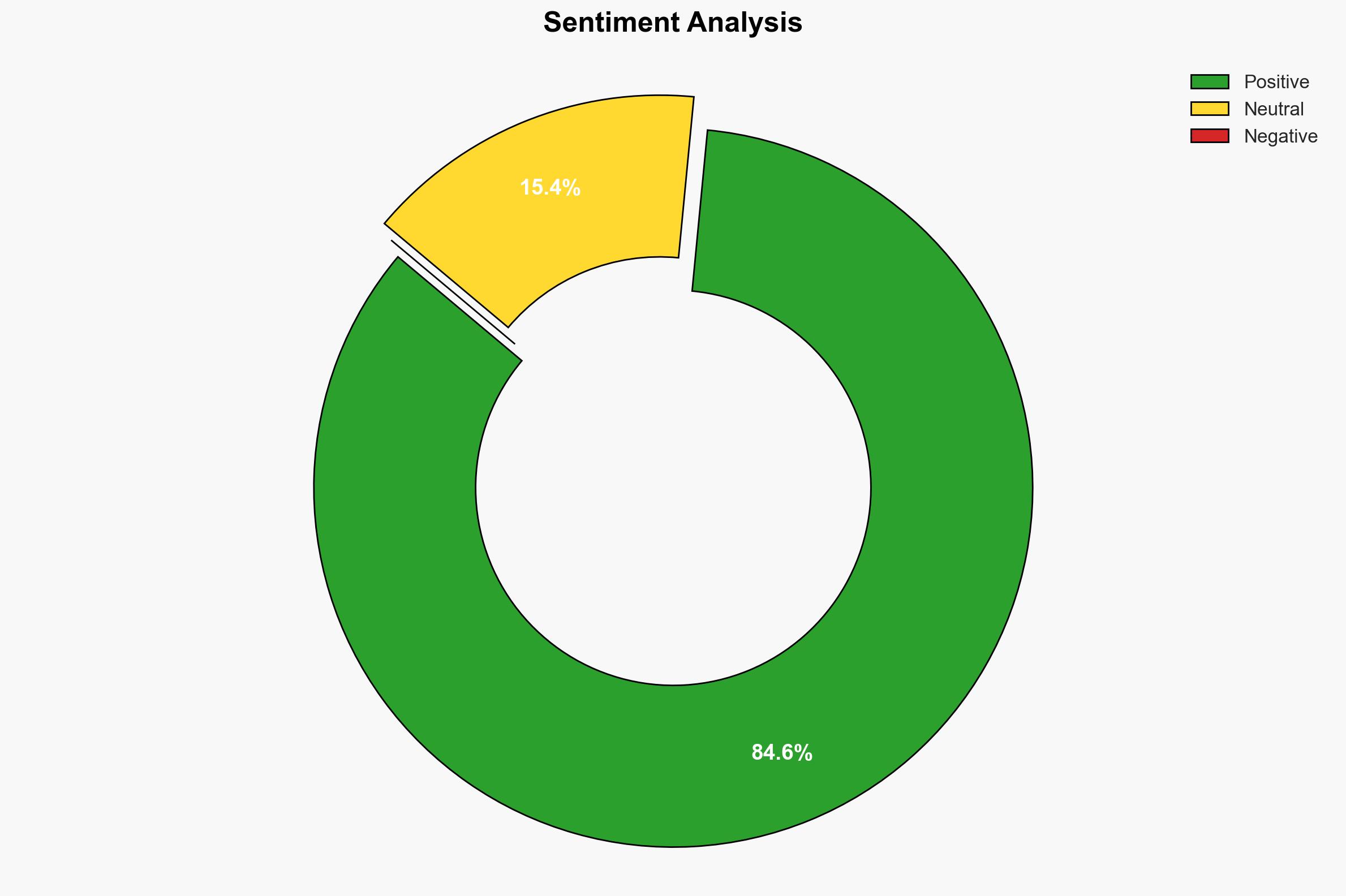
The release of free eBooks on cybersecurity and generative AI aims to redefine security strategies by integrating creativity and classical strategies with modern technology. This initiative could influence cybersecurity professionals and organizations by promoting innovative approaches to digital defense. Overall, there is moderate confidence that this development will enhance cybersecurity practices but with potential risks of misapplication or misunderstanding of complex concepts.
2. Competing Hypotheses
- Hypothesis A: The eBooks will significantly improve cybersecurity practices by providing new insights and techniques that integrate generative AI and classical strategies. This is supported by the emphasis on creativity and practical examples. However, the complexity of the content may limit its accessibility to only advanced practitioners.
- Hypothesis B: The eBooks may have limited impact due to potential misinterpretation of advanced concepts by less experienced users, leading to ineffective implementation. The lack of structured educational frameworks could hinder broader adoption.
- Assessment: Hypothesis A is currently better supported due to the detailed practical examples and case studies provided, which can facilitate understanding and application. However, monitoring user feedback and adoption rates will be crucial to validate this hypothesis further.
3. Key Assumptions and Red Flags
- Assumptions: The target audience has a foundational understanding of cybersecurity and AI; the eBooks are distributed widely and accessed by relevant professionals; the integration of AI and classical strategies is feasible and beneficial.
- Information Gaps: The actual reach and readership demographics of the eBooks; empirical evidence of improved cybersecurity outcomes following the adoption of these strategies.
- Bias & Deception Risks: Potential bias in the presentation of AI capabilities; risk of over-reliance on AI without adequate understanding of its limitations; possibility of deceptive practices in marketing the eBooks.
4. Implications and Strategic Risks
This development could catalyze a shift towards more innovative cybersecurity practices, but it also poses risks if misapplied. The integration of AI in cybersecurity strategies could redefine threat landscapes and defensive measures.
- Political / Geopolitical: Potential influence on national cybersecurity policies and international cooperation frameworks.
- Security / Counter-Terrorism: Enhanced defensive capabilities may deter cybercrime but could also lead to adversaries adopting similar strategies.
- Cyber / Information Space: Increased use of AI in cybersecurity could lead to new vulnerabilities and attack vectors if not properly managed.
- Economic / Social: Improved cybersecurity could enhance economic stability, but disparities in access to advanced knowledge may widen the gap between organizations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor the distribution and reception of the eBooks; engage with cybersecurity communities to gauge initial reactions and feedback.
- Medium-Term Posture (1–12 months): Develop training programs to facilitate the understanding and application of the concepts presented; foster partnerships with educational institutions to integrate these strategies into curricula.
- Scenario Outlook:
- Best: Widespread adoption leads to significant improvements in cybersecurity practices.
- Worst: Misapplication of concepts results in increased vulnerabilities.
- Most-Likely: Gradual adoption with mixed results, contingent on user expertise and support structures.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, generative AI, digital defense, strategic innovation, educational outreach, AI integration, cybersecurity strategy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us