From age verification to weakening encryption 2025 saw a decline in online anonymity everywhere – TechRadar
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: From age verification to weakening encryption 2025 saw a decline in online anonymity everywhere – TechRadar
1. BLUF (Bottom Line Up Front)
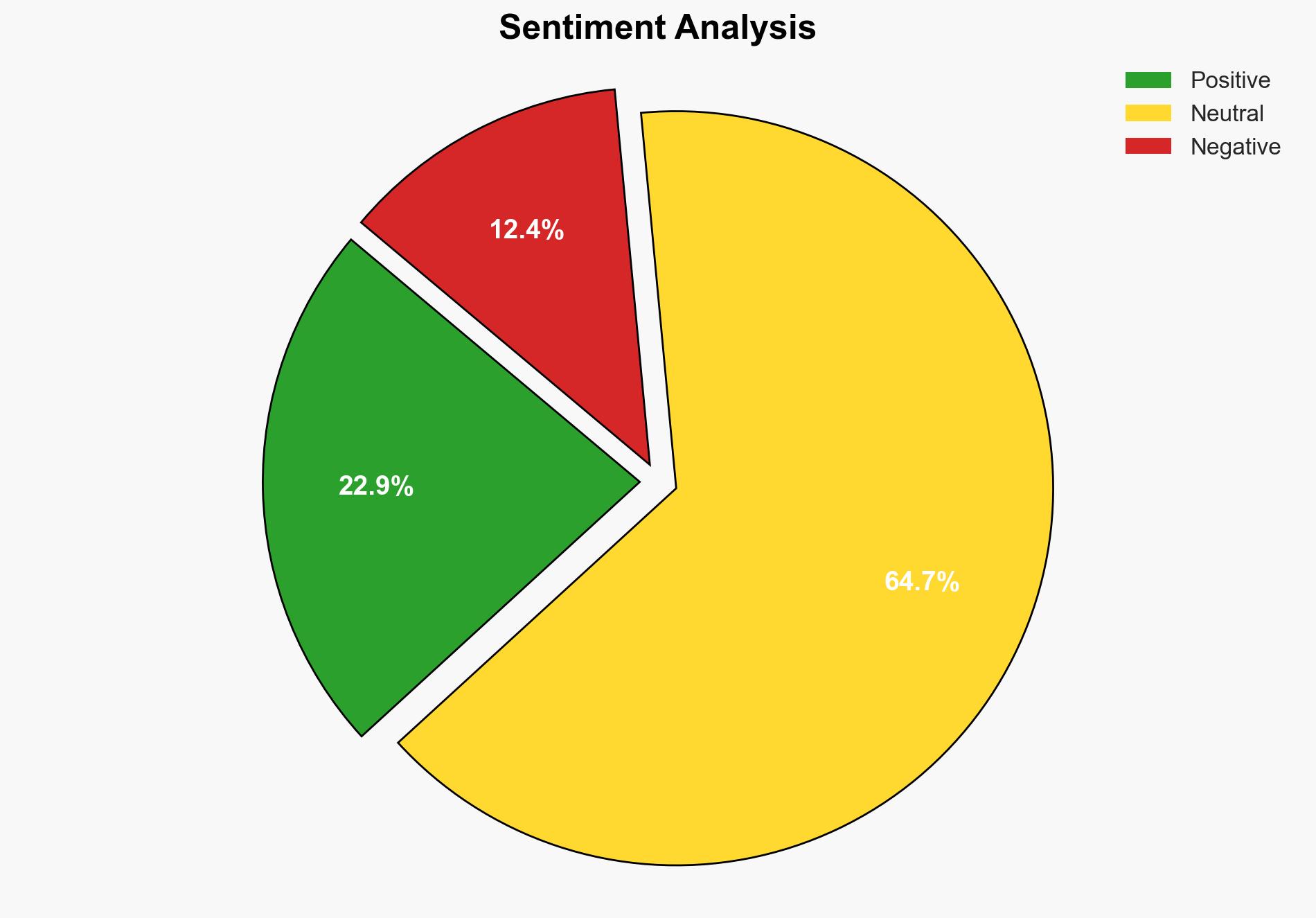
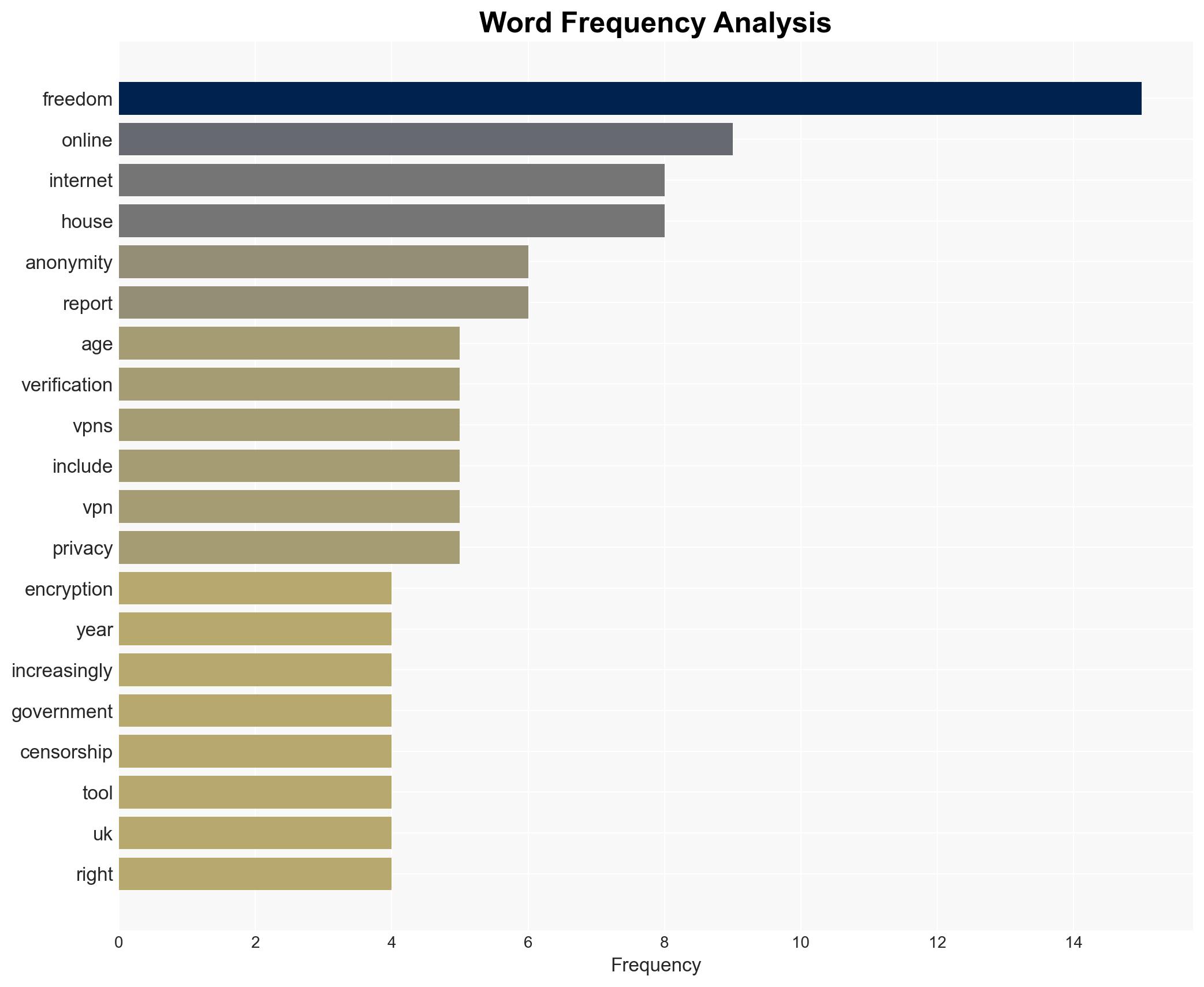
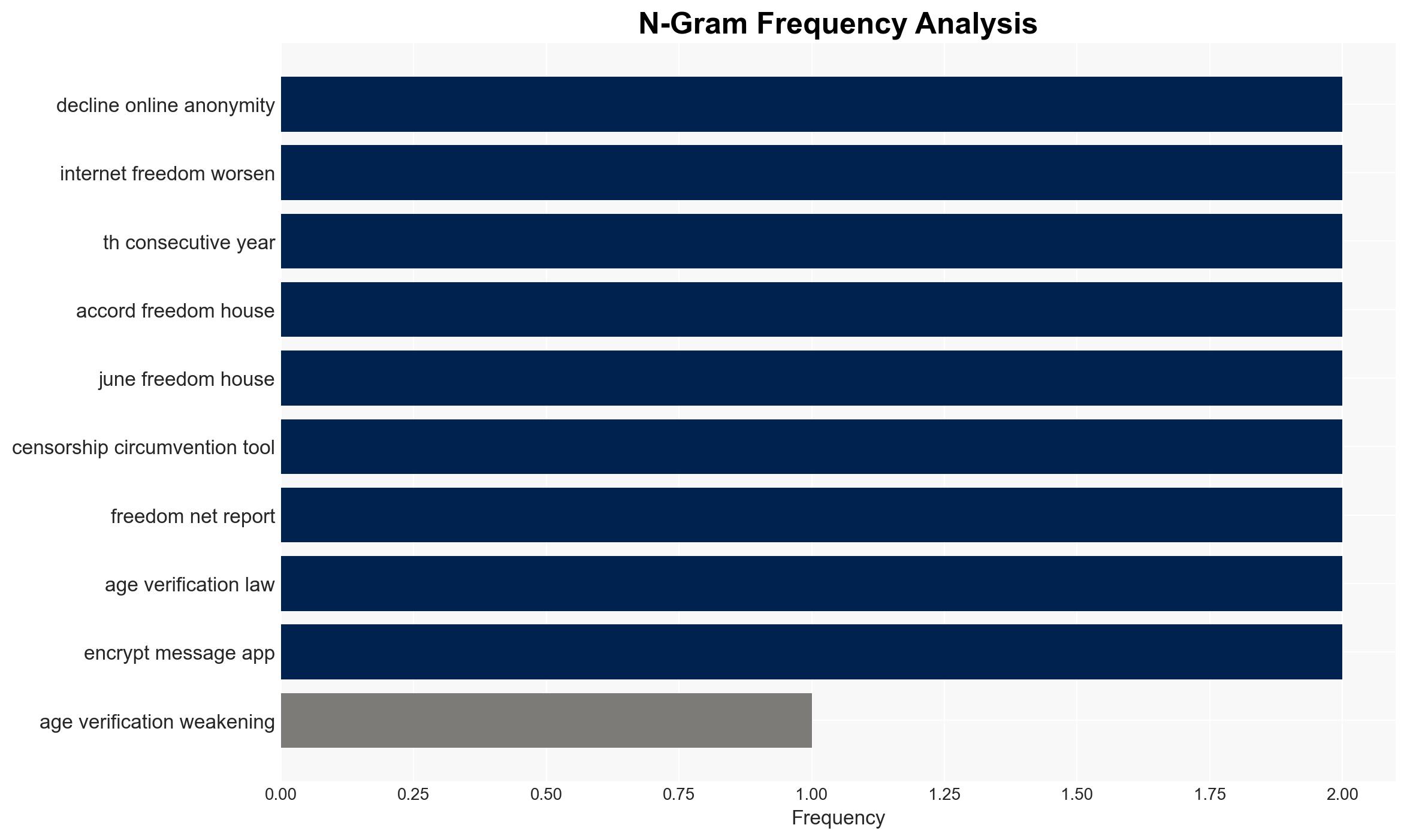
The decline in online anonymity, driven by increased age verification and weakened encryption, poses significant threats to internet freedom and privacy. The most supported hypothesis is that these measures are primarily motivated by government interests in control and surveillance, rather than solely child protection. Confidence Level: Moderate. Recommended action includes advocating for balanced policy measures that protect children while preserving privacy and digital rights.
2. Competing Hypotheses
Hypothesis 1: Governments are implementing age verification and weakening encryption primarily to enhance child protection and prevent online harm.
Hypothesis 2: The primary motivation behind these measures is increased governmental control and surveillance, under the guise of child protection.
Hypothesis 2 is more likely due to the global trend of increasing governmental control over digital spaces, as evidenced by similar measures in non-democratic states like Vietnam and China, and the broad application of these measures beyond child protection contexts.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that governments have the technical capacity to enforce these measures effectively. It is also assumed that the public will accept these measures as necessary for child protection.
Red Flags: The rapid implementation of these measures without comprehensive public debate or transparency. The involvement of democratic states in these practices raises concerns about potential overreach and erosion of civil liberties.
Deception Indicators: Framing these measures strictly as child protection initiatives without acknowledging broader surveillance implications.
4. Implications and Strategic Risks
The decline in online anonymity could lead to increased censorship, suppression of free speech, and a chilling effect on online discourse. Politically, this may result in heightened tensions between governments and civil society, as well as between states with differing views on internet freedom. Economically, tech companies may face increased compliance costs and potential loss of consumer trust. Cyber risks include potential vulnerabilities introduced by weakened encryption.
5. Recommendations and Outlook
- Advocate for international standards that balance child protection with privacy rights.
- Encourage transparency and public debate on the implications of these measures.
- Develop technologies and policies that enhance privacy without compromising safety.
- Best-case scenario: Governments adopt balanced policies that protect children while preserving privacy.
- Worst-case scenario: Widespread erosion of digital rights and increased state surveillance.
- Most-likely scenario: Continued tension between privacy advocates and governments, with incremental policy adjustments.
6. Key Individuals and Entities
Kian Vesteinsson, Senior Research Analyst at Freedom House; Annie Boyajian, President of Freedom House; European University Institute.
7. Thematic Tags
Cybersecurity, Internet Freedom, Digital Rights, Government Surveillance, Privacy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·