Gemini CLI – Github.com
Published on: 2025-06-25
Intelligence Report: Gemini CLI – Github.com
1. BLUF (Bottom Line Up Front)
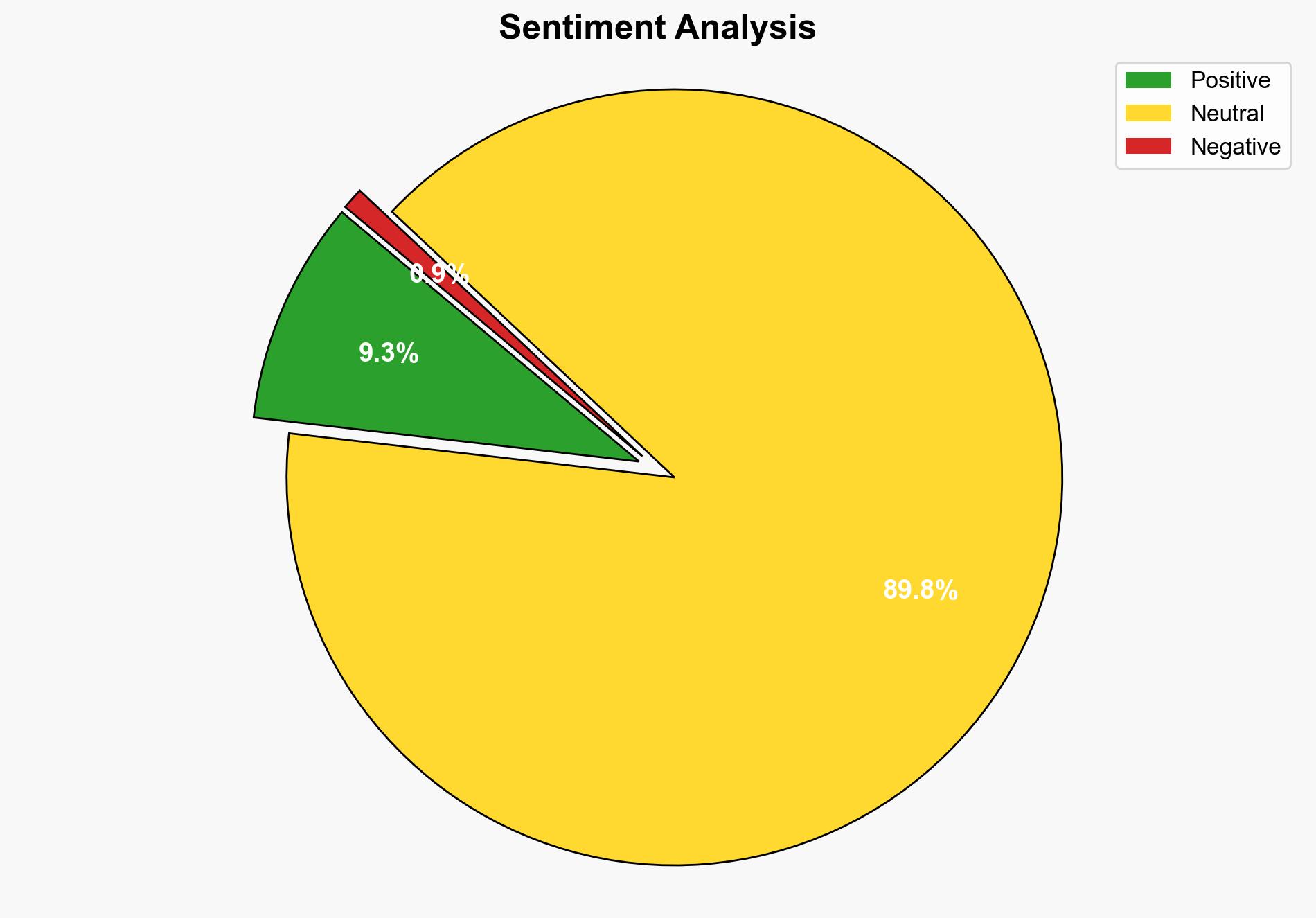
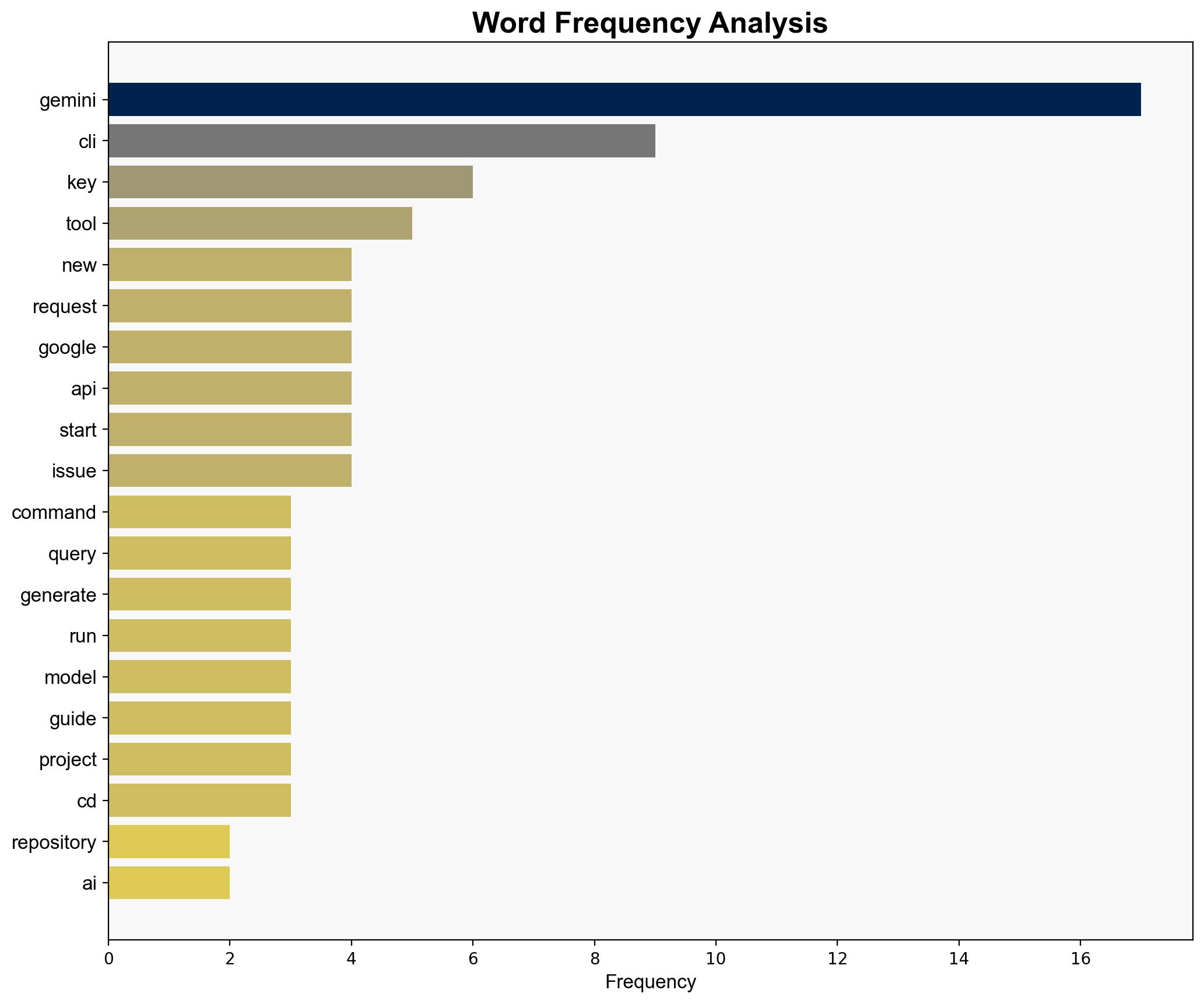
The Gemini CLI is a command-line AI workflow tool designed to enhance code understanding and accelerate development processes. It offers multimodal capabilities for automating tasks such as code queries and pull requests. The tool requires specific setup steps, including authentication via Google accounts and API key generation. Its integration with various systems poses potential cybersecurity risks that need to be addressed to ensure secure deployment and operation.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The Gemini CLI’s integration with external systems like Google accounts and API keys could be targeted by cyber adversaries. Simulating potential attack vectors can help identify vulnerabilities in authentication and data handling processes.
Indicators Development
Monitoring for anomalies in API key usage and authentication attempts can provide early warning signs of unauthorized access or misuse, allowing for timely intervention.
Bayesian Scenario Modeling
Using probabilistic models to predict potential cyberattack pathways can help prioritize security measures and allocate resources effectively to mitigate risks.
3. Implications and Strategic Risks
The integration of Gemini CLI with cloud-based services and local systems introduces potential vulnerabilities that could be exploited by cyber threats. These risks could have cascading effects on enterprise operations, especially if sensitive data is compromised. Ensuring robust security mechanisms is crucial to prevent unauthorized access and data breaches.
4. Recommendations and Outlook
- Implement multi-factor authentication and regular security audits to enhance the security of the Gemini CLI.
- Develop a comprehensive incident response plan to address potential breaches swiftly.
- Scenario-based projections suggest that, in a best-case scenario, robust security measures will prevent breaches, while a worst-case scenario could involve significant data loss and operational disruption.
5. Key Individuals and Entities
No specific individuals are mentioned in the source data. Future reports should identify key developers and contributors to the Gemini CLI project for targeted security assessments.
6. Thematic Tags
cybersecurity, software development, AI tools, system integration, risk management