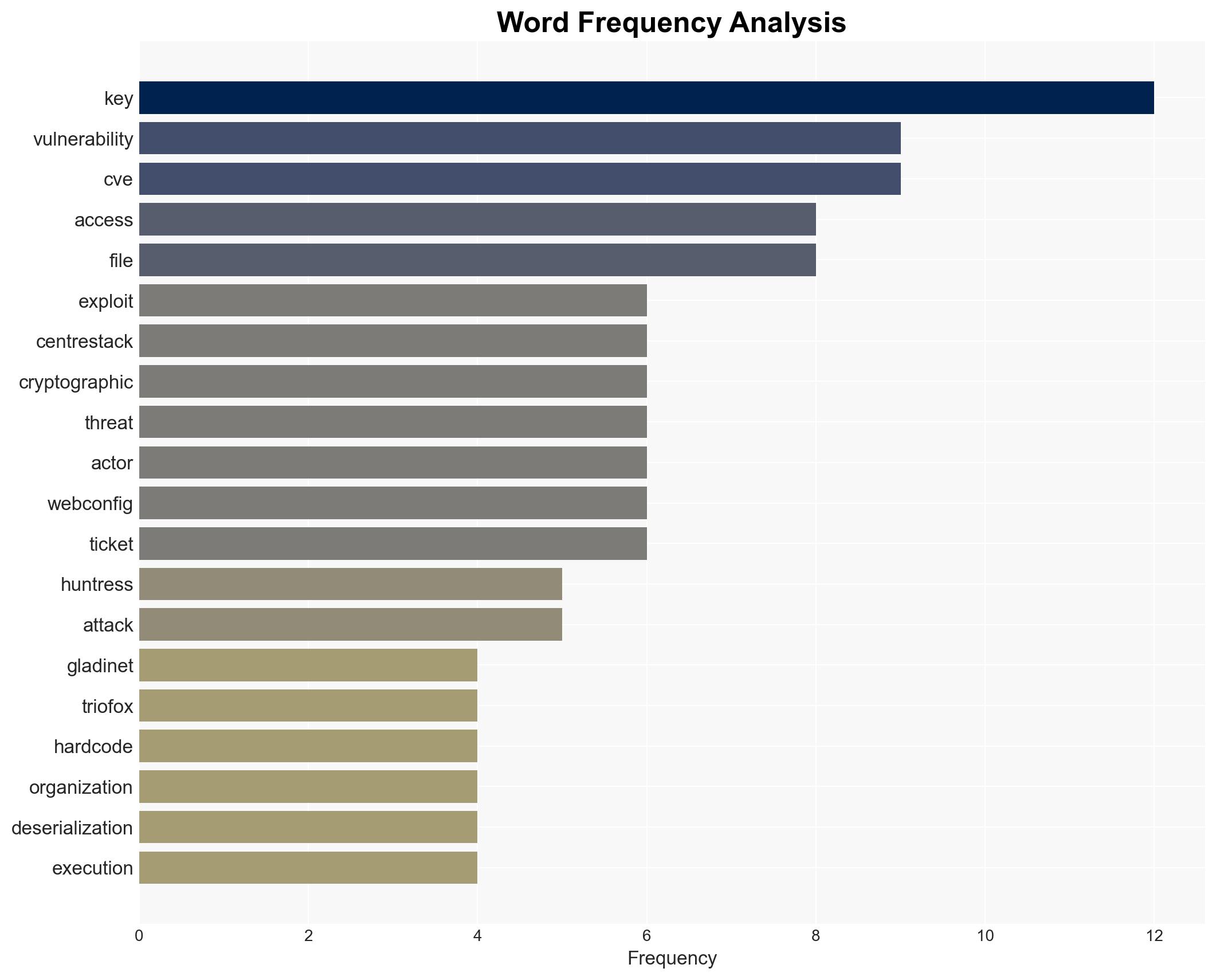
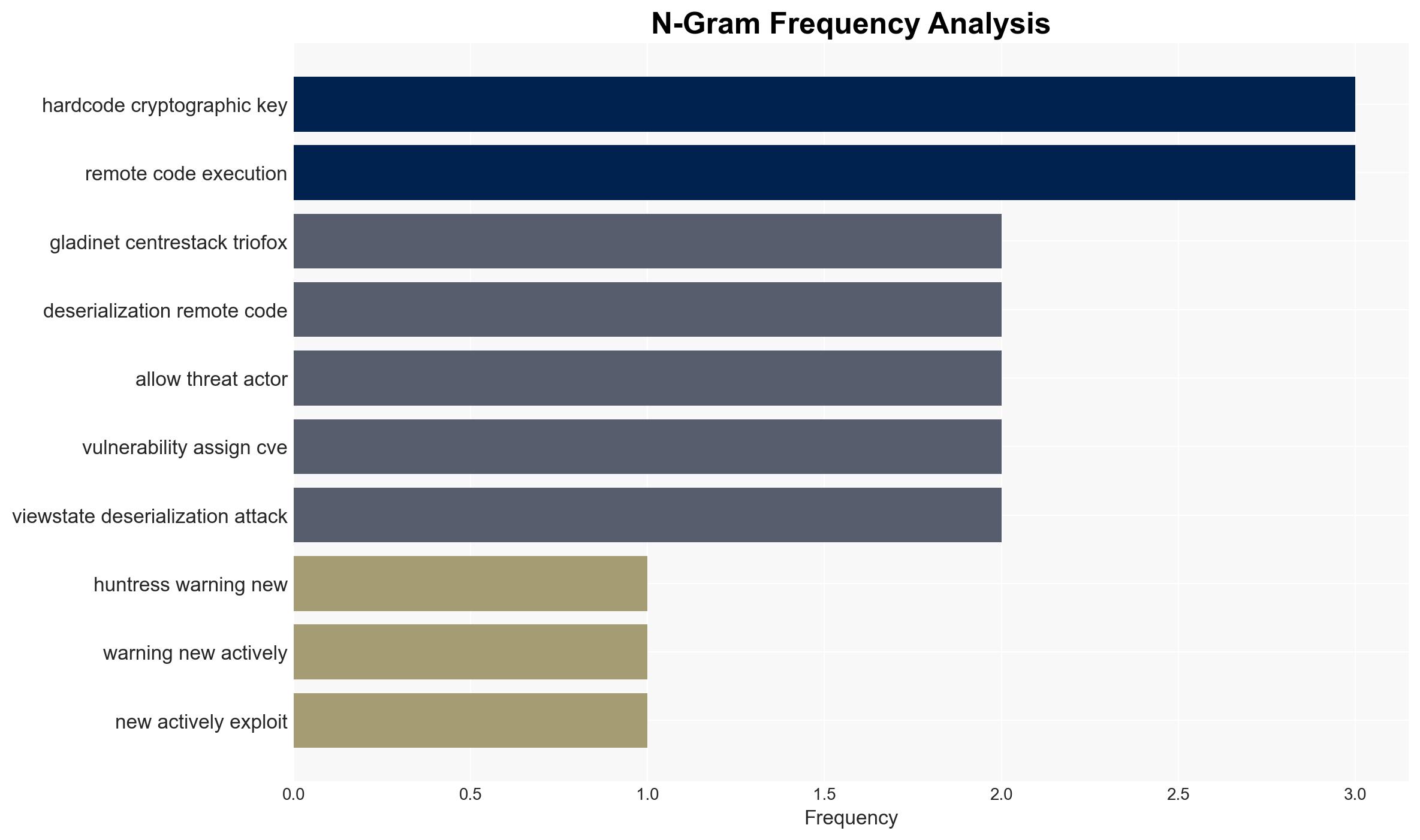
Gladinet Vulnerability Allows Unauthorized Access and Code Execution via Hard-Coded Cryptographic Keys
Published on: 2025-12-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Active Attacks Exploit Gladinet’s Hard-Coded Keys for Unauthorized Access and Code Execution
1. BLUF (Bottom Line Up Front)
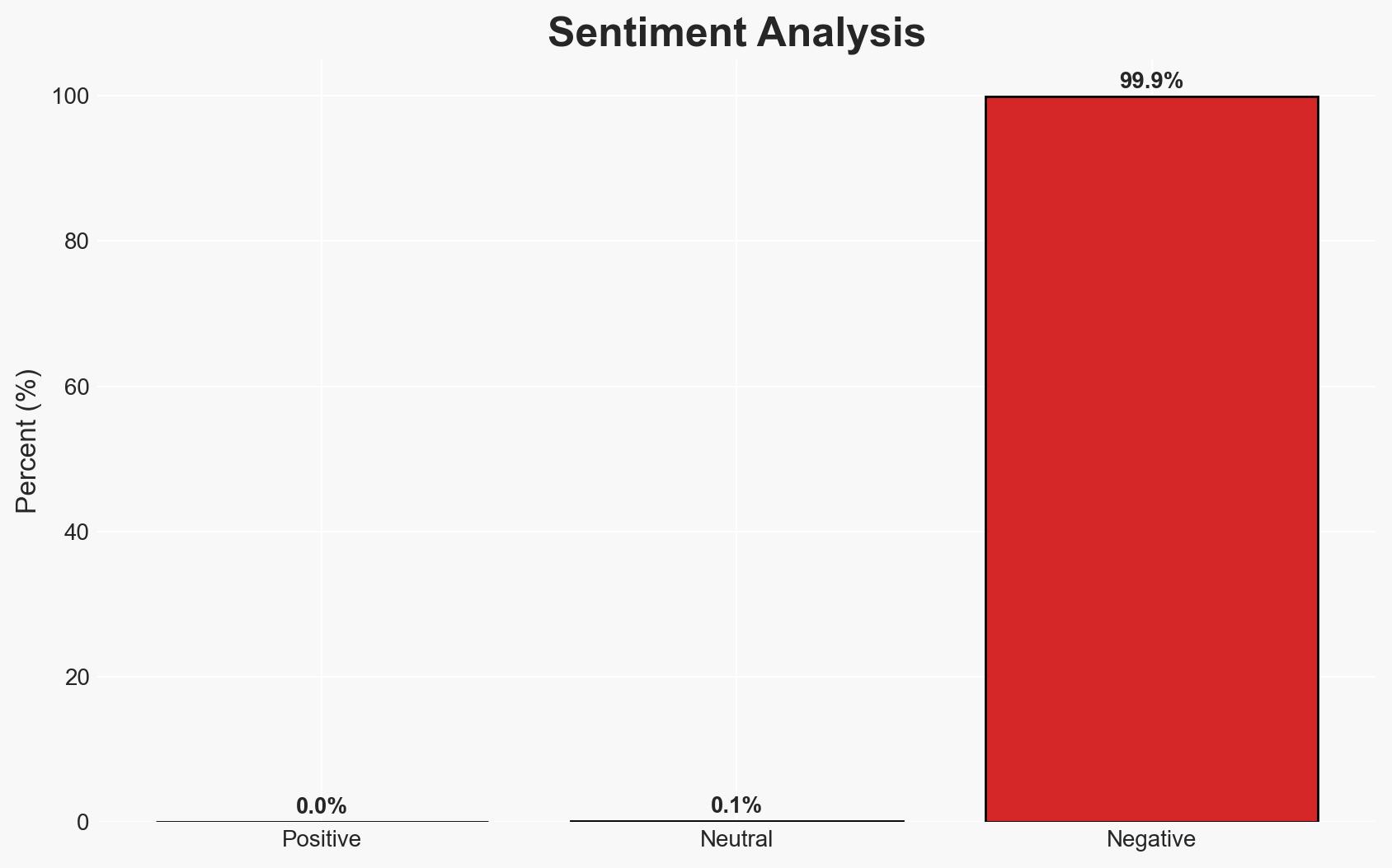
Active exploitation of a vulnerability in Gladinet’s products, due to hard-coded cryptographic keys, poses a significant security risk to affected organizations, primarily in healthcare and technology sectors. The most likely hypothesis is that threat actors are leveraging this flaw for unauthorized access and potential code execution. Overall confidence in this assessment is moderate, considering the limited scope of affected entities and the absence of a CVE identifier.
2. Competing Hypotheses
- Hypothesis A: Threat actors are exploiting the hard-coded keys in Gladinet’s products to gain unauthorized access and execute code. This is supported by the reported active exploitation and the technical details provided by Huntress. However, the lack of a CVE identifier and broader reporting introduces uncertainty.
- Hypothesis B: The reported attacks may be isolated incidents or misconfigurations rather than a widespread exploitation campaign. This hypothesis is contradicted by the specific technical exploitation details and multiple affected organizations, but the limited number of reported cases supports it.
- Assessment: Hypothesis A is currently better supported due to the detailed technical analysis and evidence of active exploitation. Indicators such as increased reporting or a CVE assignment could further strengthen this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is actively exploited by external threat actors; affected organizations have not yet fully mitigated the vulnerability; the exploitation is primarily for unauthorized access and code execution.
- Information Gaps: Lack of a CVE identifier; limited information on the full scope of affected organizations; unclear attribution of threat actors.
- Bias & Deception Risks: Potential bias from relying on a single source (Huntress); risk of underestimating the scale of exploitation due to limited reporting.
4. Implications and Strategic Risks
The exploitation of Gladinet’s vulnerability could lead to broader security challenges if not addressed, potentially affecting more sectors and increasing the sophistication of attacks.
- Political / Geopolitical: Escalation could occur if state actors exploit the vulnerability for espionage or sabotage.
- Security / Counter-Terrorism: Increased risk of data breaches and operational disruptions in critical sectors like healthcare.
- Cyber / Information Space: Potential for further exploitation by cybercriminals or state-sponsored actors, increasing the complexity of cyber defense.
- Economic / Social: Potential financial losses and reputational damage to affected organizations, impacting stakeholder trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgent patching of affected systems, increased monitoring for indicators of compromise, and sharing threat intelligence with relevant stakeholders.
- Medium-Term Posture (1–12 months): Develop resilience measures, enhance partnerships for information sharing, and invest in cybersecurity capabilities to prevent similar vulnerabilities.
- Scenario Outlook: Best case: Vulnerability is patched and exploitation ceases. Worst case: Broader exploitation leads to significant data breaches. Most likely: Continued targeted exploitation with gradual mitigation efforts.
6. Key Individuals and Entities
- Gladinet (software vendor)
- Huntress (cybersecurity company)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, vulnerability exploitation, unauthorized access, remote code execution, healthcare sector, technology sector, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us