Global Condemnation Follows Deadly Shooting at Jewish Festival in Sydney’s Bondi Beach
Published on: 2025-12-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: World reacts to Jewish festival shooting attack at Sydneys Bondi Beach
1. BLUF (Bottom Line Up Front)
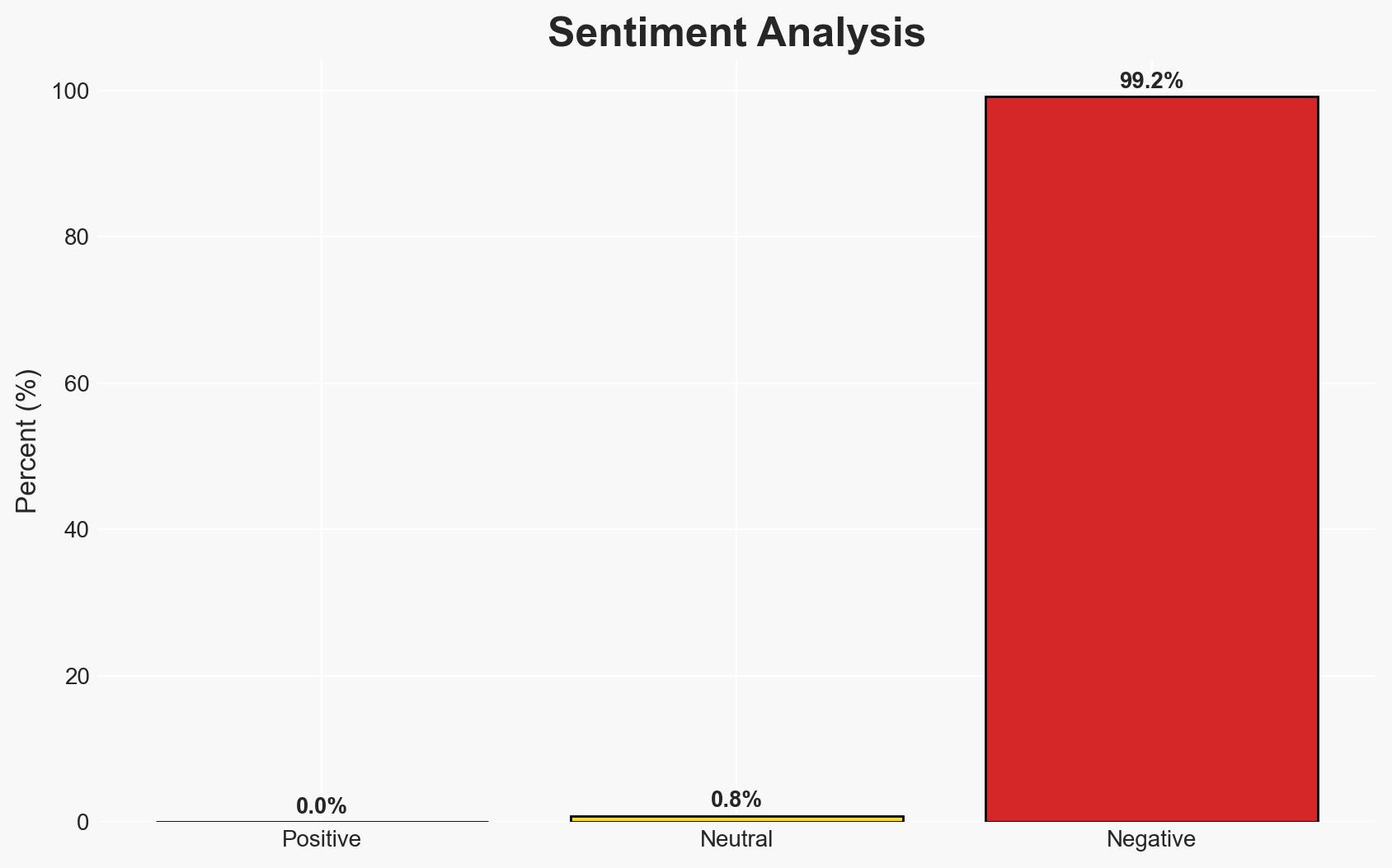
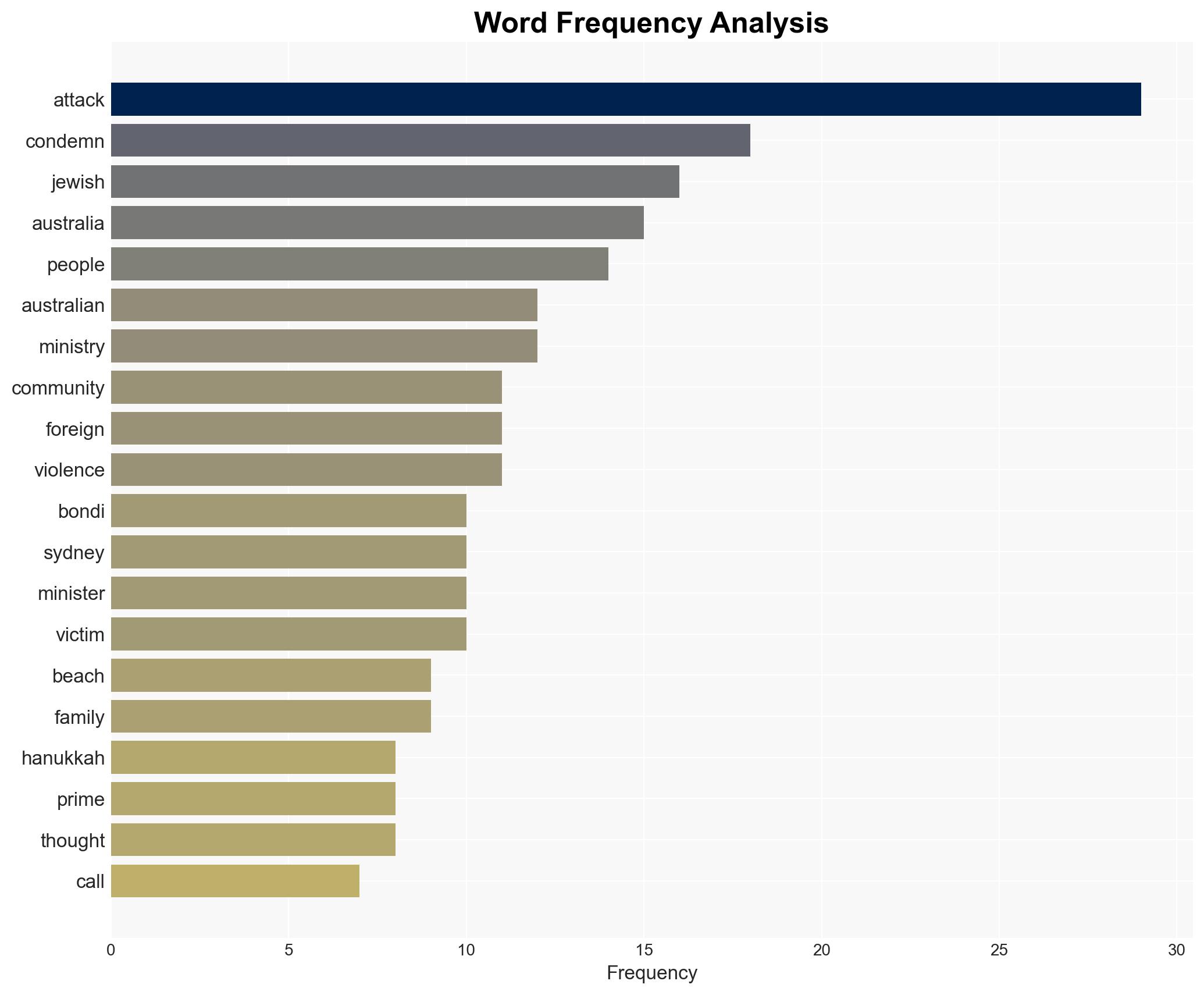
The mass shooting at a Jewish festival in Sydney, Australia, represents a significant terrorist incident targeting the Jewish community, resulting in at least 15 fatalities. This attack has drawn international condemnation and highlights vulnerabilities in community security. The most likely hypothesis is that this was an antisemitic attack with potential links to broader extremist networks. Overall confidence in this judgment is moderate due to limited information on the perpetrators.
2. Competing Hypotheses
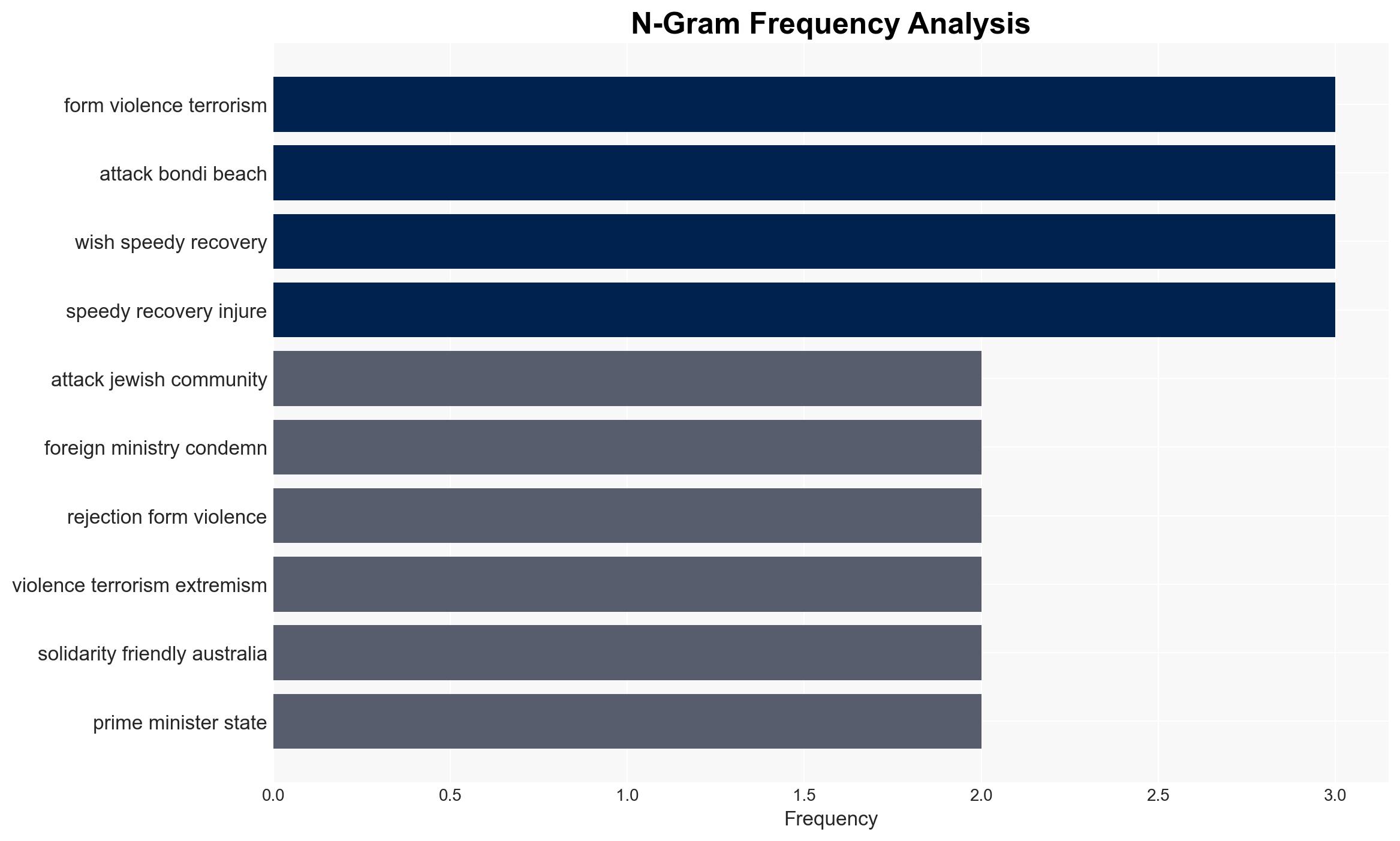
- Hypothesis A: The attack was a premeditated antisemitic act by a local extremist group. This is supported by the timing (first day of Hanukkah) and location (Jewish festival). However, there is uncertainty about the group’s identity and whether it has external support.
- Hypothesis B: The attack was carried out by a lone actor with personal grievances against the Jewish community. This is less supported due to the scale and coordination required, which suggests organizational involvement.
- Assessment: Hypothesis A is currently better supported due to the targeted nature and timing of the attack. Key indicators that could shift this judgment include evidence of external coordination or a manifesto from the perpetrator(s).
3. Key Assumptions and Red Flags
- Assumptions: The attack was ideologically motivated; the perpetrators had prior knowledge of the event; security measures were insufficient to prevent the attack.
- Information Gaps: Identity and motivations of the attackers; any prior intelligence warnings; details on security measures in place.
- Bias & Deception Risks: Potential bias in attributing the attack to a specific group without concrete evidence; risk of overestimating the threat level based on international reactions.
4. Implications and Strategic Risks
This attack could exacerbate tensions within Australia and increase security concerns for minority communities. It may also influence international counter-terrorism cooperation and domestic policy changes.
- Political / Geopolitical: Potential strain on Australia’s domestic policies regarding minority protection and international relations with countries condemning the attack.
- Security / Counter-Terrorism: Heightened alert for similar attacks; possible increase in security measures at public events.
- Cyber / Information Space: Potential for increased online extremist propaganda and misinformation targeting Jewish communities.
- Economic / Social: Possible impact on tourism and local businesses due to perceived insecurity; increased social division and community fear.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance security at Jewish and other vulnerable community events; increase intelligence sharing with international partners; monitor extremist online activity.
- Medium-Term Posture (1–12 months): Develop community resilience programs; strengthen counter-terrorism capabilities; foster interfaith dialogue to reduce tensions.
- Scenario Outlook:
- Best: Rapid identification and neutralization of the threat, leading to increased community trust and security.
- Worst: Further attacks or copycat incidents, leading to widespread fear and societal division.
- Most-Likely: Increased security measures and community vigilance, with gradual return to normalcy but heightened awareness.
6. Key Individuals and Entities
- Prime Minister Anthony Albanese
- New Zealand Prime Minister Chris Luxon
- US President Donald Trump
- US Secretary of State Marco Rubio
- UN Secretary-General Antonio Guterres
- Israeli President Isaac Herzog
- Not clearly identifiable from open sources in this snippet
7. Thematic Tags
Counter-Terrorism, antisemitism, community security, international relations, extremist networks, public safety, intelligence sharing
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us