Global Exploitation of MongoDB Vulnerability CVE-2025-14847 Threatens Sensitive Data Security
Published on: 2025-12-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: MongoDB Vulnerability CVE-2025-14847 Under Active Exploitation Worldwide
1. BLUF (Bottom Line Up Front)
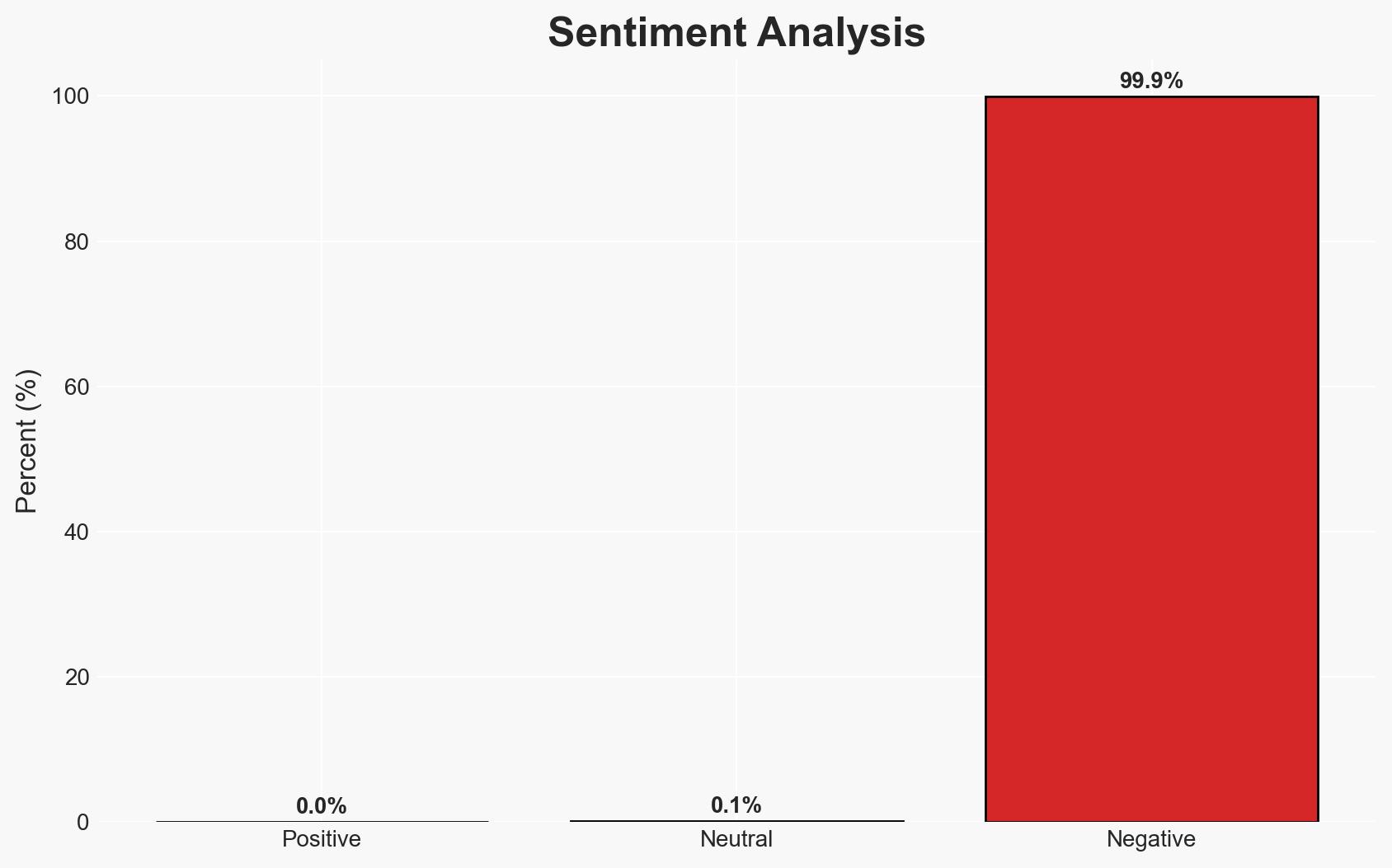
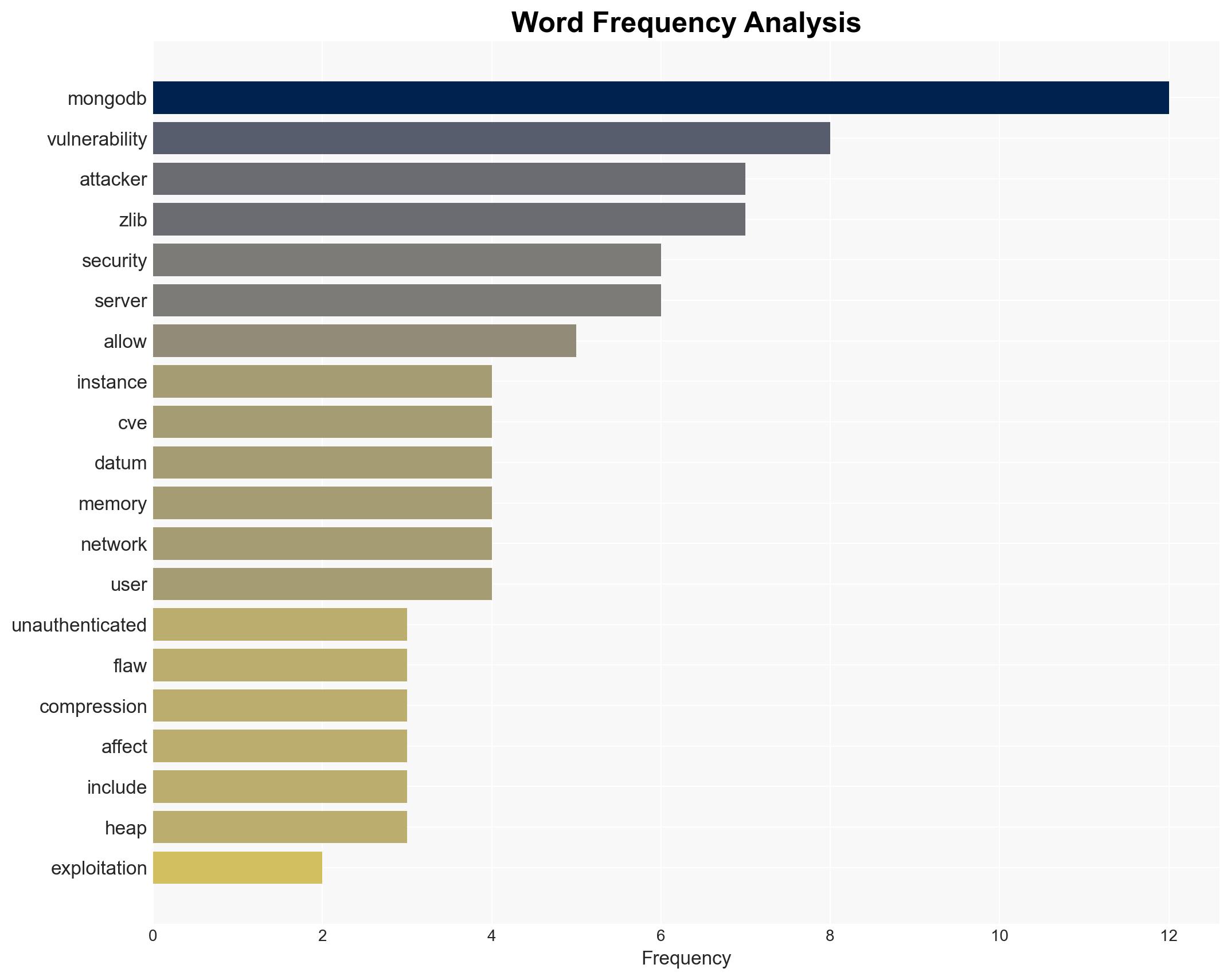
The MongoDB vulnerability CVE-2025-14847, known as MongoBleed, is actively being exploited, affecting over 87,000 instances globally. This vulnerability allows unauthenticated attackers to leak sensitive data from MongoDB server memory. The most likely hypothesis is that cybercriminals are leveraging this vulnerability for data theft. The overall confidence level in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Cybercriminals are exploiting CVE-2025-14847 primarily for data theft. Supporting evidence includes the vulnerability’s ability to leak sensitive data and the large number of exposed instances. Contradicting evidence is the lack of specific attack details.
- Hypothesis B: State-sponsored actors are exploiting the vulnerability for espionage purposes. Supporting evidence could be inferred from the global distribution of affected instances, but there is no direct evidence linking state actors to these activities.
- Assessment: Hypothesis A is currently better supported due to the nature of the vulnerability and the typical motivations of cybercriminals. Indicators that could shift this judgment include evidence of targeted attacks against specific geopolitical interests.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is primarily being exploited by cybercriminals; the majority of affected instances are not yet patched; MongoDB instances are widely used in critical sectors.
- Information Gaps: Specific details on the nature and scope of the attacks exploiting this vulnerability; identification of actors involved.
- Bias & Deception Risks: Potential bias in assuming cybercriminal activity without evidence of state involvement; risk of underestimating the vulnerability’s impact due to incomplete data.
4. Implications and Strategic Risks
This vulnerability could lead to significant data breaches, affecting both private and public sectors. Over time, unpatched instances may become targets for more sophisticated attacks.
- Political / Geopolitical: Potential for increased tensions if state actors are implicated in exploiting the vulnerability.
- Security / Counter-Terrorism: Increased risk of data theft could compromise sensitive information, impacting national security.
- Cyber / Information Space: The vulnerability highlights the need for improved cybersecurity measures and could lead to increased scrutiny of cloud services.
- Economic / Social: Data breaches could result in financial losses and damage to organizational reputations, affecting economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch vulnerable MongoDB instances; disable zlib compression as a temporary measure; increase monitoring of network traffic for signs of exploitation.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing on vulnerabilities; enhance capabilities for rapid response to cyber threats.
- Scenario Outlook:
- Best: Rapid patching mitigates the threat with minimal data loss.
- Worst: Widespread exploitation leads to significant data breaches and geopolitical tensions.
- Most-Likely: Continued exploitation by cybercriminals with gradual improvement in patching and security measures.
6. Key Individuals and Entities
- OX Security
- Wiz
- Censys
- Merav Bar
- Amitai Cohen
- MongoDB Inc.
7. Thematic Tags
cybersecurity, data breach, vulnerability management, cloud security, cybercrime, information leakage, MongoDB
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us