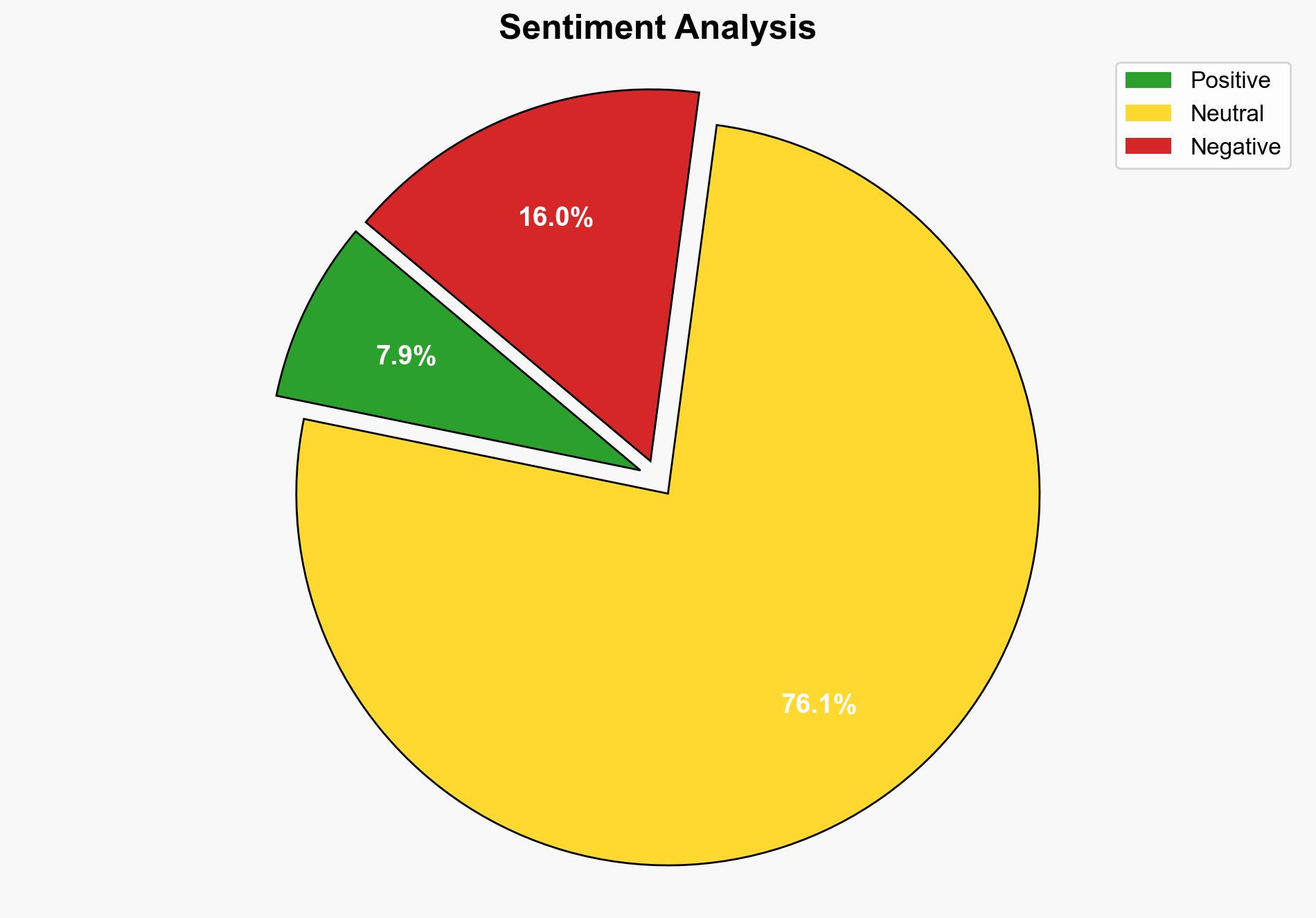
Global Hack Hits US Agencies via Microsoft SharePoint Flaw – Sputnikglobe.com
Published on: 2025-07-21
Intelligence Report: Global Hack Hits US Agencies via Microsoft SharePoint Flaw – Sputnikglobe.com
1. BLUF (Bottom Line Up Front)
A significant cyberattack has exploited a vulnerability in Microsoft SharePoint, impacting government agencies and companies globally, including in the US, Canada, and Australia. Immediate actions are required to mitigate the breach and prevent further exploitation. Key recommendations include urgent patching of affected systems and enhanced monitoring for unusual activities.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Cyber adversaries are exploiting a known vulnerability in Microsoft SharePoint. Simulations suggest potential for further breaches if not addressed promptly, emphasizing the need for proactive defense strategies.
Indicators Development
Anomalies such as unauthorized access attempts and data exfiltration activities have been identified. Continuous monitoring is essential to detect and respond to these indicators swiftly.
Bayesian Scenario Modeling
Probabilistic models indicate a high likelihood of similar attacks occurring if the vulnerability remains unpatched. The model also suggests potential pathways for attackers to escalate privileges within affected networks.
3. Implications and Strategic Risks
The breach highlights systemic vulnerabilities in widely used software platforms, posing risks to national security and economic stability. The attack could lead to data theft, operational disruptions, and loss of public trust. Cross-domain risks include potential impacts on critical infrastructure and international relations.
4. Recommendations and Outlook
- Immediate deployment of Microsoft’s security update to patch the SharePoint vulnerability.
- Enhance cybersecurity protocols and conduct regular vulnerability assessments.
- Develop contingency plans for potential escalation scenarios, including data breaches and service disruptions.
- Best case: Rapid containment and patching prevent further incidents. Worst case: Prolonged exposure leads to significant data loss and operational impacts. Most likely: Partial containment with isolated incidents continuing until full patch deployment.
5. Key Individuals and Entities
No specific individuals are named in the report. The focus remains on the affected entities, including government agencies and companies in the US, Canada, and Australia.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus