Google Alerts on Ongoing Exploitation of Patched WinRAR Vulnerability CVE-2025-8088 by Multiple Threat Actors
Published on: 2026-01-28
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Google Warns of Active Exploitation of WinRAR Vulnerability CVE-2025-8088
1. BLUF (Bottom Line Up Front)
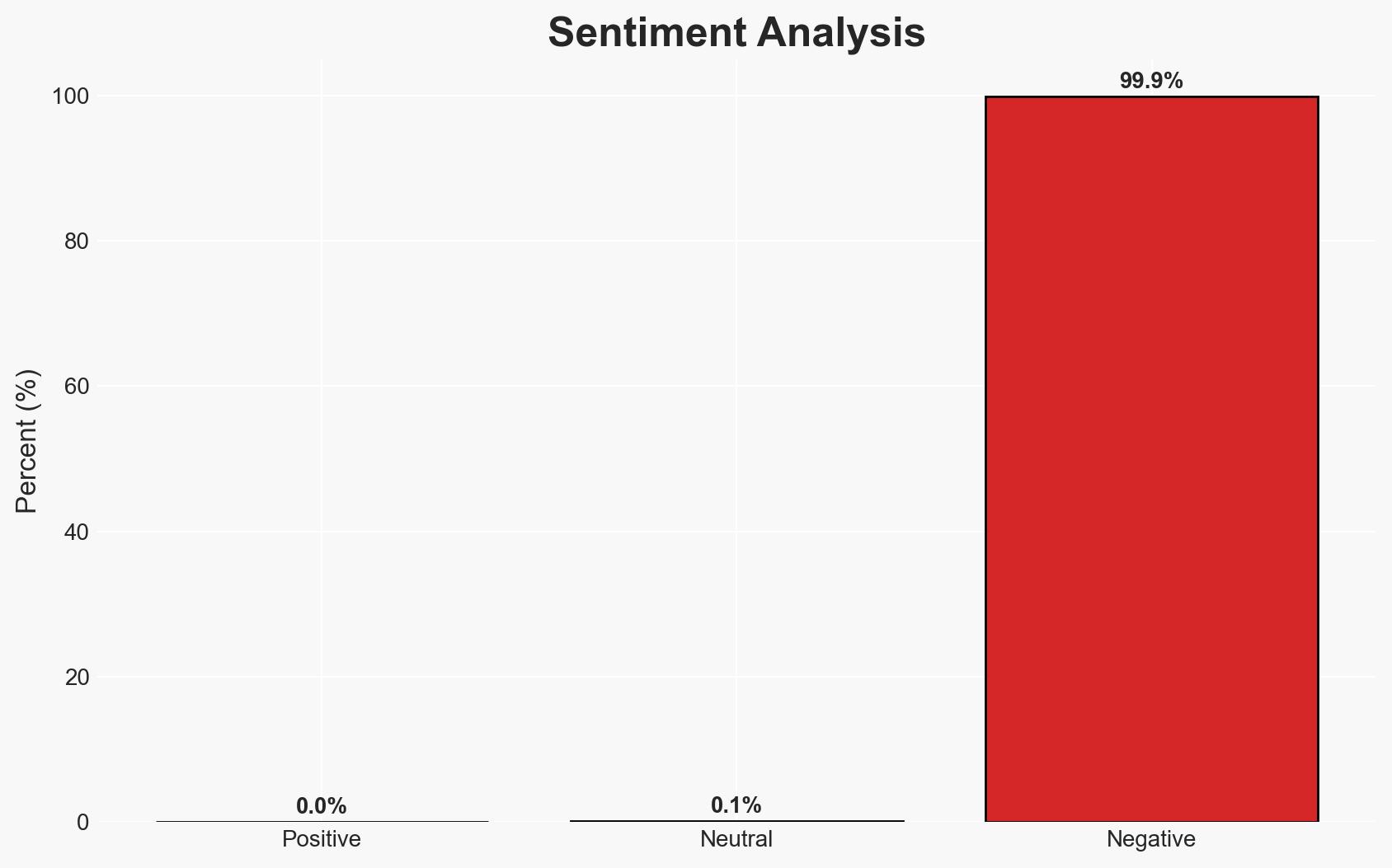
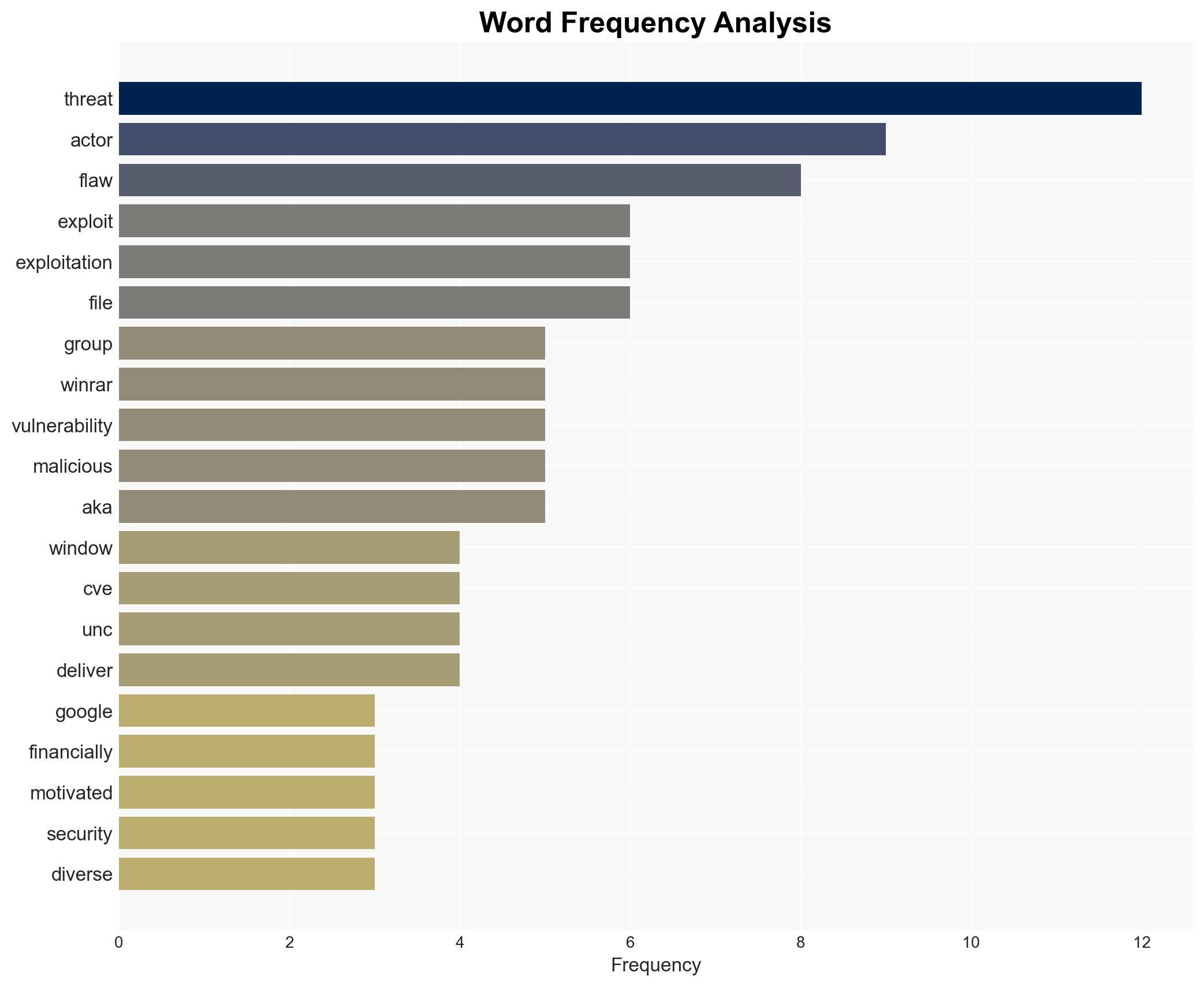
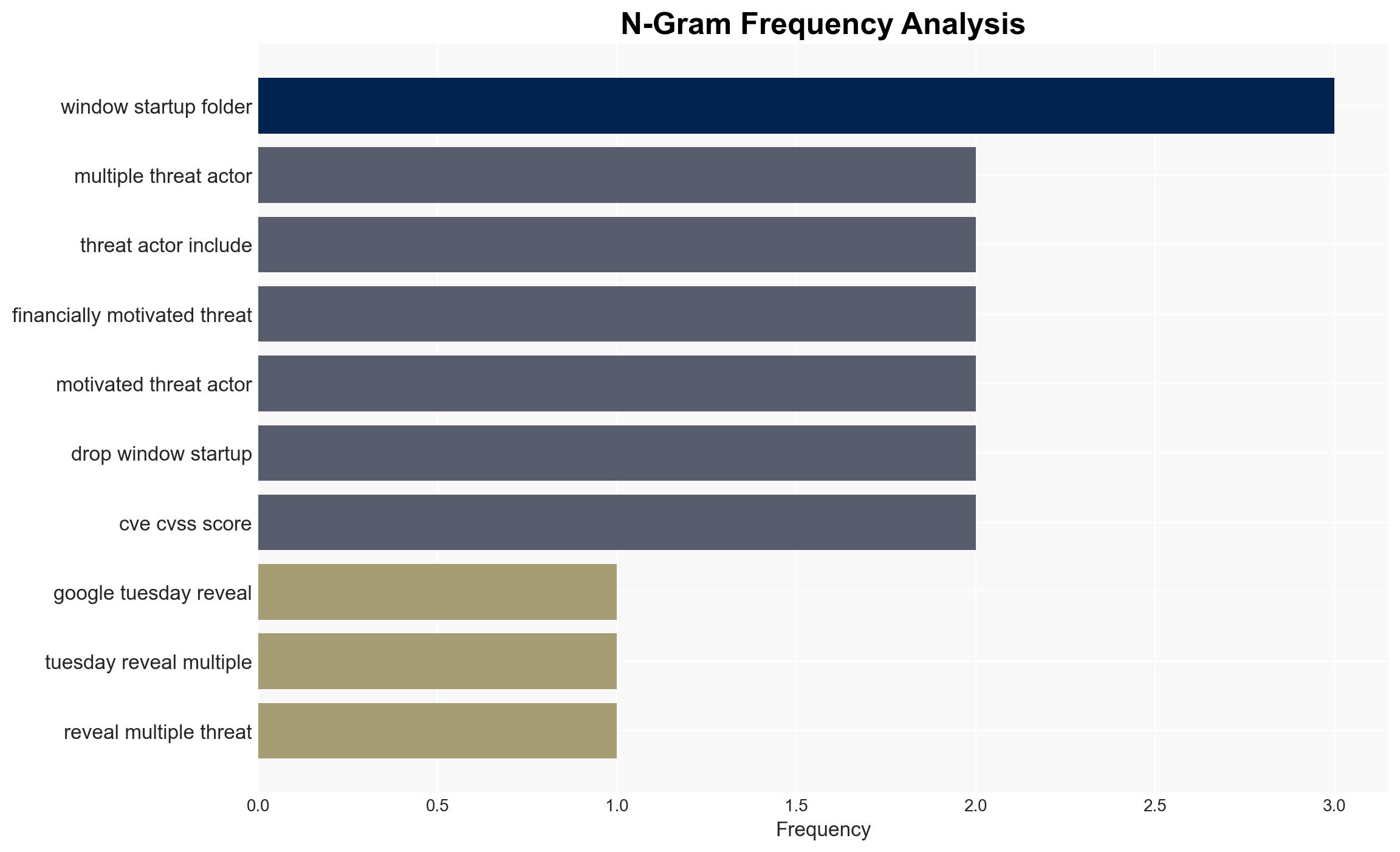
The CVE-2025-8088 vulnerability in WinRAR is actively exploited by multiple threat actors, including nation-state and financially motivated groups, to gain initial access and deploy malware. The primary targets appear to be entities in Ukraine and potentially other geopolitical adversaries. The exploitation underscores significant gaps in application security and user awareness. Overall confidence in this assessment is moderate, given the complexity of the threat landscape and the potential for undisclosed operations.
2. Competing Hypotheses
- Hypothesis A: The primary motivation behind exploiting CVE-2025-8088 is geopolitical, with state-sponsored actors from Russia and China targeting Ukrainian and other adversarial entities. This is supported by the involvement of known APT groups like Sandworm and Turla, which have historical ties to state objectives. However, the presence of financially motivated actors complicates the attribution.
- Hypothesis B: The exploitation is primarily financially motivated, with actors using geopolitical tensions as a cover to conduct ransomware and data extortion operations. The involvement of groups like RomCom and the use of ransomware supports this hypothesis, though the geopolitical targeting pattern suggests a dual-purpose strategy.
- Assessment: Hypothesis A is currently better supported due to the strategic targeting of Ukrainian entities and the involvement of state-linked APT groups. Indicators such as the use of decoy files with Ukrainian themes and the historical context of Russian cyber operations in Ukraine reinforce this judgment. However, further evidence of financial transactions or ransom demands could shift the assessment towards Hypothesis B.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is not fully patched across all potential targets; state-sponsored actors have strategic objectives aligned with their national interests; financially motivated actors are opportunistic in exploiting geopolitical tensions.
- Information Gaps: Specific details on the full scope of affected entities, confirmation of financial transactions or ransom payments, and comprehensive attribution of all involved actors.
- Bias & Deception Risks: Potential bias in attributing state sponsorship due to historical patterns; possible deception by actors using false flags to mislead attribution efforts.
4. Implications and Strategic Risks
The exploitation of CVE-2025-8088 could exacerbate geopolitical tensions, particularly in Eastern Europe, and increase the cyber threat landscape’s complexity. The continued exploitation may lead to more sophisticated attack vectors and broader targeting.
- Political / Geopolitical: Escalation of cyber operations against Ukraine could lead to retaliatory measures and increased tensions between involved states.
- Security / Counter-Terrorism: Heightened risk of cyber incidents affecting critical infrastructure and government entities, potentially impacting national security.
- Cyber / Information Space: Increased need for cybersecurity measures and awareness, with potential impacts on information integrity and trust.
- Economic / Social: Potential economic disruptions from ransomware attacks and data breaches, affecting public and private sector operations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch vulnerable systems, enhance monitoring for known indicators of compromise, and increase user awareness training.
- Medium-Term Posture (1–12 months): Develop international partnerships for threat intelligence sharing, invest in advanced cybersecurity tools, and conduct regular security audits.
- Scenario Outlook:
- Best: Rapid patching and international cooperation mitigate the threat, reducing exploitation incidents.
- Worst: Escalation of cyber attacks leads to significant geopolitical conflict and economic damage.
- Most-Likely: Continued exploitation with periodic spikes in activity, driven by both geopolitical and financial motivations.
6. Key Individuals and Entities
- Sandworm (APT44, FROZENBARENTS)
- Gamaredon (CARPATHIAN)
- Turla (SUMMIT)
- RomCom (CIGAR, UNC4895)
- UNC2596
- Industrial Spy
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, ransomware, geopolitical tensions, application security, nation-state actors, financial cybercrime, Ukraine
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us