Google Disrupts Major Proxy Network IPIDEA, Targeting Cybercrime Operations and Seizing Control Domains
Published on: 2026-01-29
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: ‘We believe our actions have seriously impacted one of the largest residential proxy providers’ Google takes the fight to IPIDEA and removes millions of devices from criminal network
1. BLUF (Bottom Line Up Front)
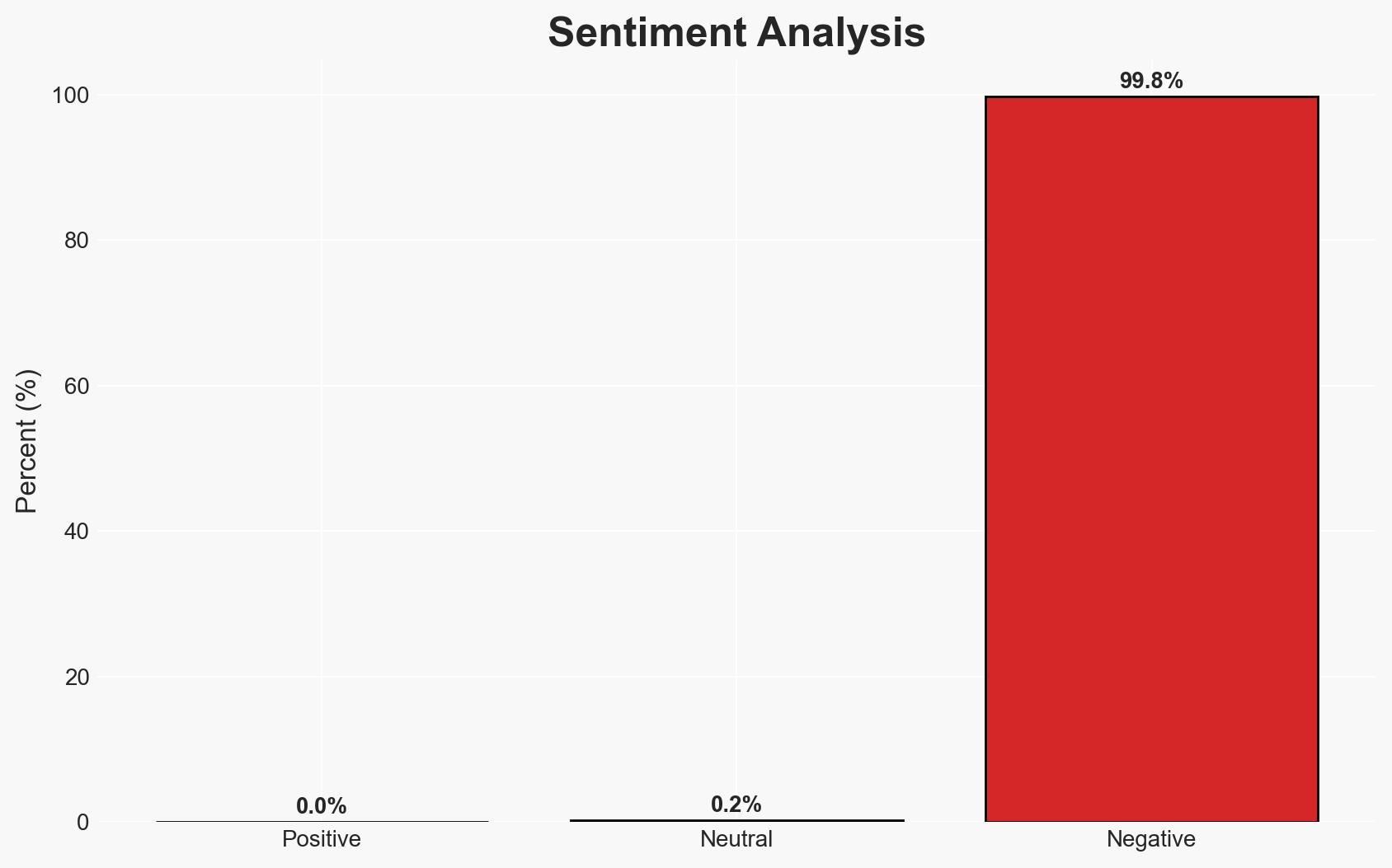
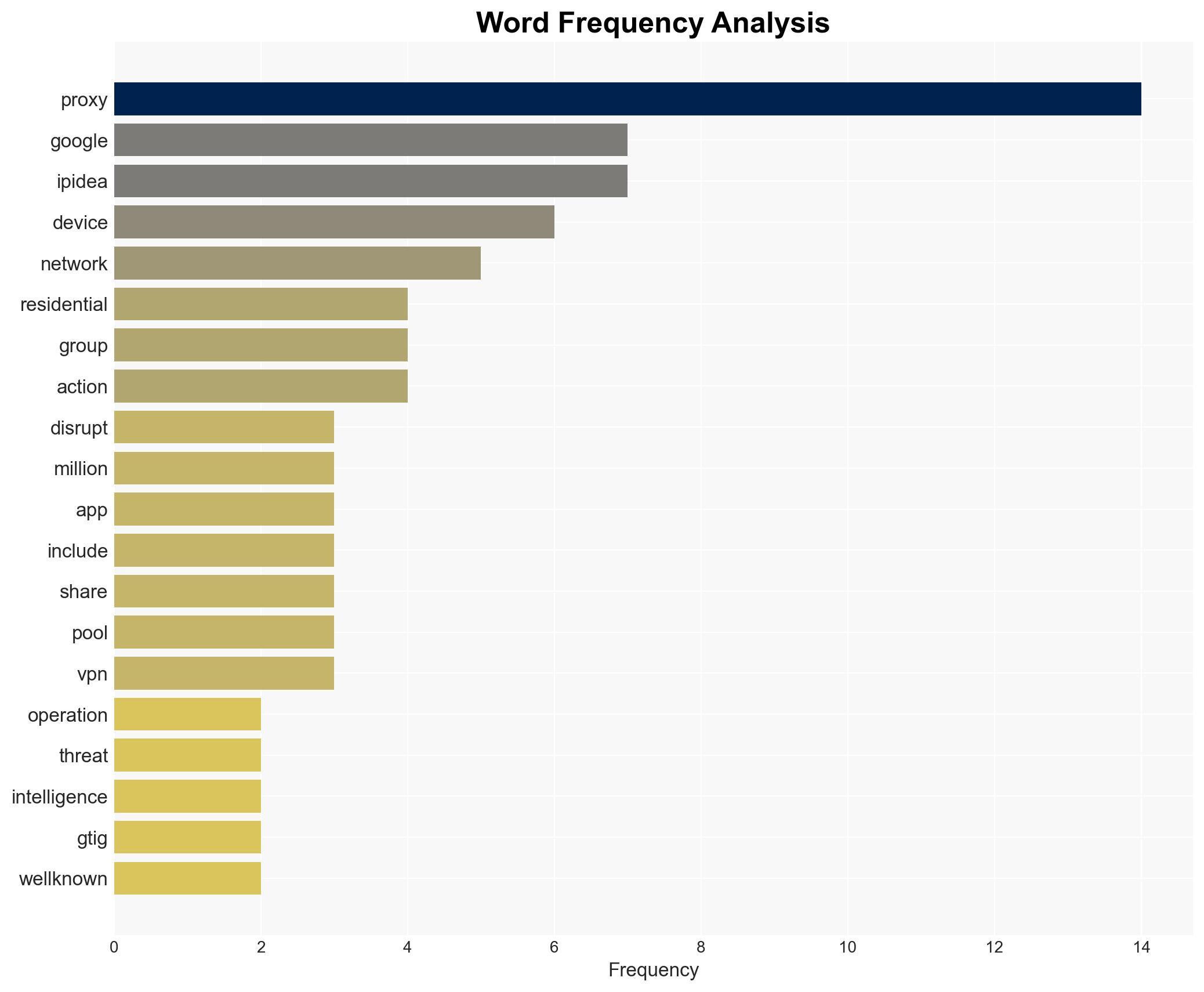
Google’s disruption of the IPIDEA network has significantly degraded one of the largest residential proxy services, impacting hundreds of cybercriminal groups and thousands of hacking operations. This action has reduced the proxy device pool by millions, affecting entities linked to China, Russia, Iran, and North Korea. The overall confidence level in this assessment is moderate, given the potential for rapid adaptation by threat actors.
2. Competing Hypotheses
- Hypothesis A: Google’s actions have effectively crippled IPIDEA’s operations, leading to a long-term reduction in cybercriminal activities. Supporting evidence includes the seizure of domains and the removal of SDKs, while uncertainties remain about the network’s ability to reconstitute itself.
- Hypothesis B: IPIDEA and associated networks will quickly adapt and restore operations, minimizing the long-term impact of Google’s actions. This is supported by the resilience and adaptability of cybercriminal networks, though currently lacking direct evidence of immediate recovery.
- Assessment: Hypothesis A is currently better supported due to the immediate and significant reduction in proxy devices and the legal and technical measures taken by Google. However, indicators such as rapid re-emergence of similar networks or continued high levels of cybercrime could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The legal and technical measures will have a sustained impact; threat actors will not quickly find alternative proxy networks; industry partners will continue to cooperate effectively.
- Information Gaps: Detailed intelligence on the adaptability of IPIDEA and its affiliates; the full scope of devices still under control; the extent of law enforcement engagement globally.
- Bias & Deception Risks: Potential overreliance on Google’s reporting; underestimation of threat actors’ capabilities to adapt; possible deception in reported affiliations of threat actor groups.
4. Implications and Strategic Risks
This development could lead to a temporary reduction in cybercriminal activities but may also drive innovation in proxy network technologies. The geopolitical landscape may see increased tension as affected states react to disruptions in their cyber capabilities.
- Political / Geopolitical: Potential diplomatic friction with states linked to the disrupted networks; increased scrutiny on tech companies’ roles in cybersecurity.
- Security / Counter-Terrorism: Short-term reduction in cyber threats; potential for increased sophistication in future attacks.
- Cyber / Information Space: Possible shift in cybercriminal tactics; increased focus on alternative methods of anonymization and network exploitation.
- Economic / Social: Potential economic impact on companies reliant on proxy services; increased public awareness of cybersecurity issues.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of proxy network activities; increase collaboration with international law enforcement; deploy public awareness campaigns on device security.
- Medium-Term Posture (1–12 months): Develop resilience measures against proxy network reconstitution; strengthen partnerships with tech companies for intelligence sharing; invest in capability development for rapid response.
- Scenario Outlook:
- Best: Sustained reduction in cybercrime activities, with no significant resurgence of proxy networks.
- Worst: Rapid reconstitution of proxy networks, leading to increased cyber threats.
- Most-Likely: Temporary reduction in activities with gradual adaptation by threat actors.
6. Key Individuals and Entities
- Google Threat Intelligence Group (GTIG)
- IPIDEA
- ABC Proxy
- Galleon VPN
- PIA S5 Proxy
- Radish VPN
- Tab Proxy
- Threat actor groups linked to China, Russia, Iran, North Korea
7. Thematic Tags
cybersecurity, proxy networks, cybercrime, threat intelligence, international cooperation, cyber-espionage, digital resilience
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us