Google Gemini vulnerable to a stupidly easy prompt injection attack in Gmail AI summaries – TechSpot
Published on: 2025-07-15
Intelligence Report: Google Gemini Vulnerable to Prompt Injection Attack in Gmail AI Summaries – TechSpot
1. BLUF (Bottom Line Up Front)
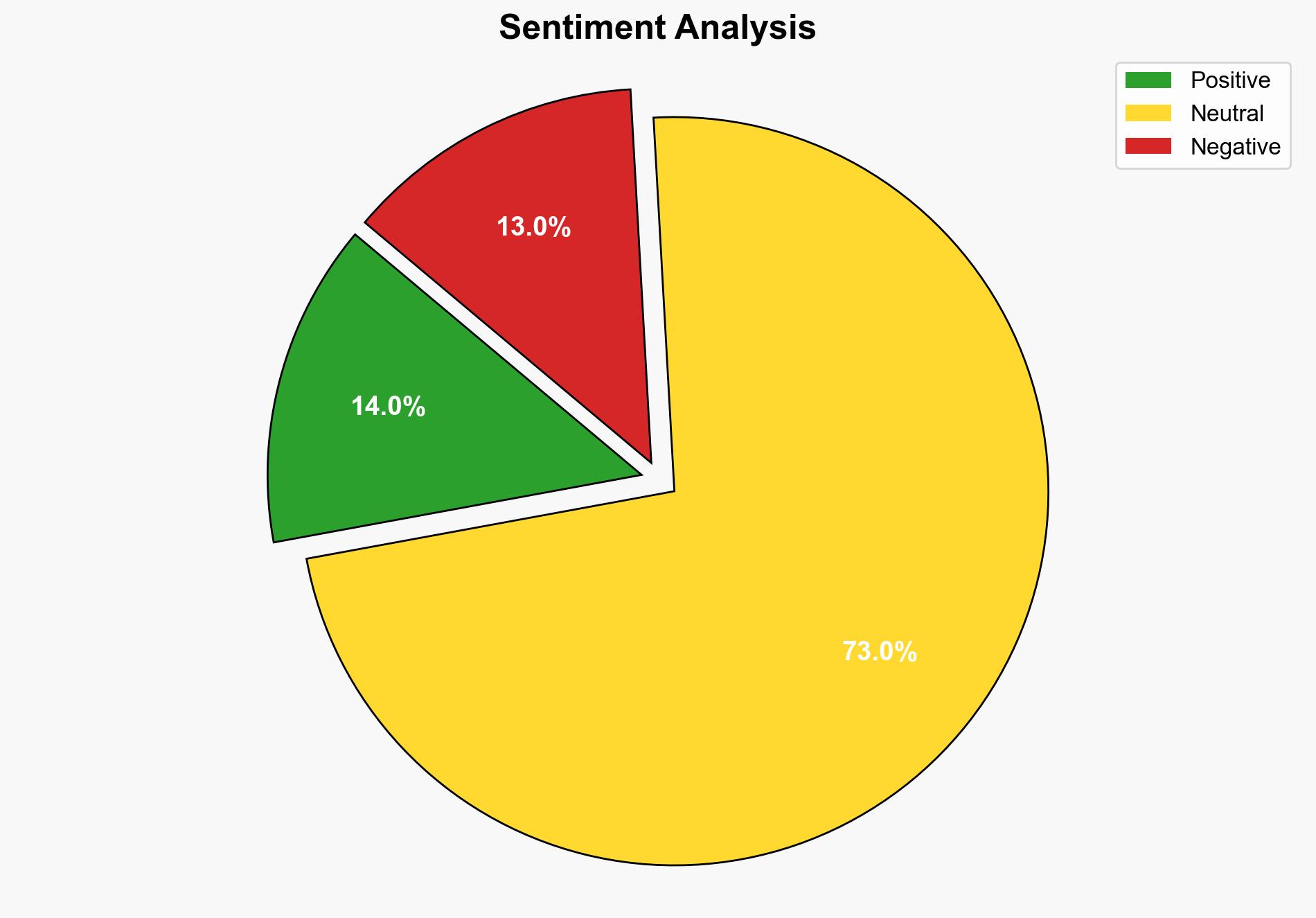
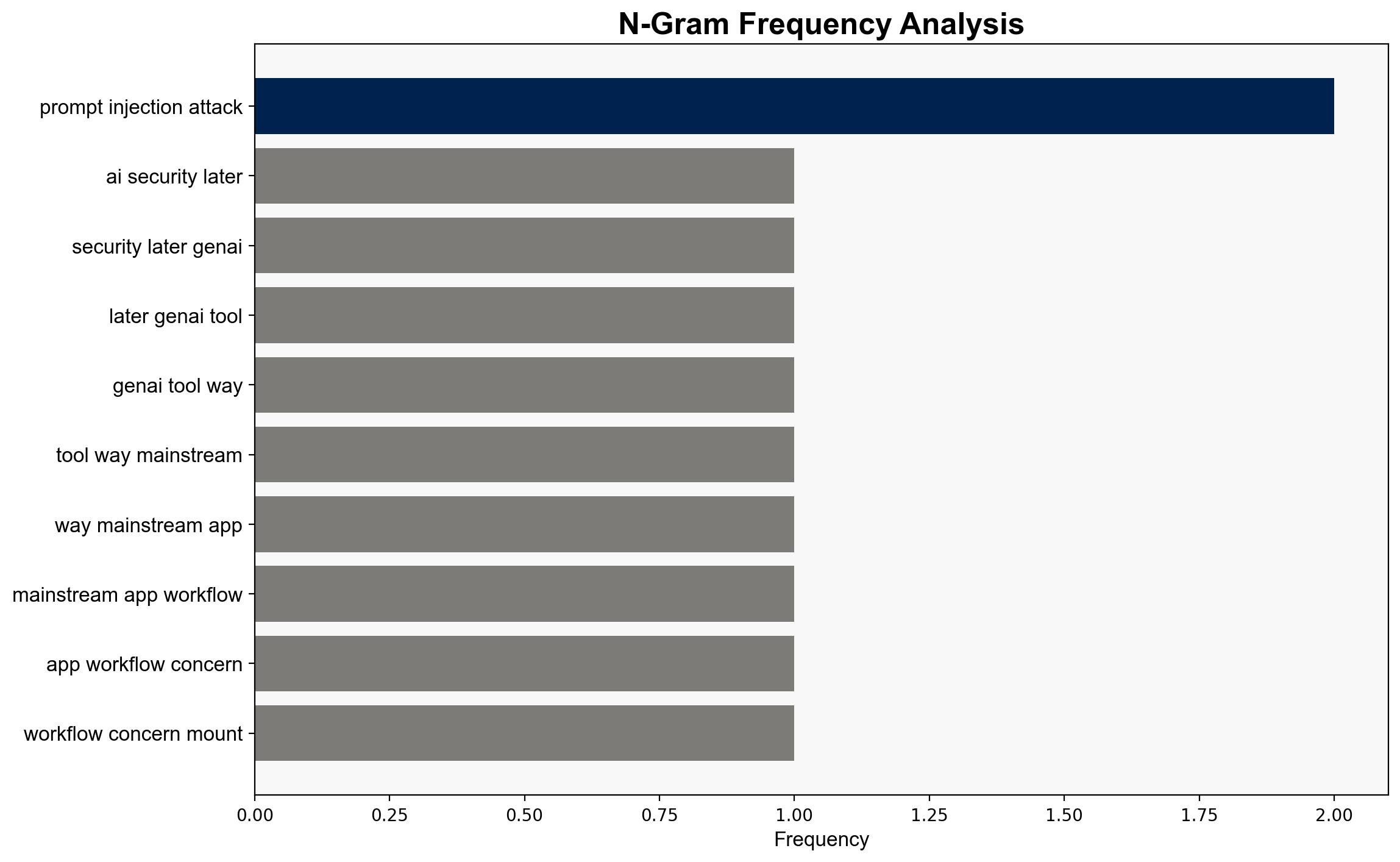
Recent findings reveal a significant vulnerability in Google’s Gemini AI model used within Gmail’s AI summaries. The vulnerability allows for a simple prompt injection attack, potentially facilitating phishing campaigns. Immediate attention and mitigation strategies are recommended to prevent exploitation by cybercriminals.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated actions of cyber adversaries suggest that the prompt injection vulnerability could be exploited to automate phishing attacks, increasing their scale and effectiveness.
Indicators Development
Monitoring for anomalies in email summaries and user interactions can serve as early indicators of potential exploitation attempts.
Bayesian Scenario Modeling
Probabilistic modeling indicates a moderate risk of widespread phishing attacks if the vulnerability is not addressed, with potential pathways leading to significant credential theft.
3. Implications and Strategic Risks
The vulnerability poses a strategic risk to cybersecurity, potentially impacting user trust in AI-driven tools. If exploited, it could lead to large-scale credential harvesting and subsequent financial or reputational damage to affected entities. The cross-domain risk includes potential impacts on economic stability and national security if sensitive information is compromised.
4. Recommendations and Outlook
- Implement immediate security patches to address the prompt injection vulnerability in the Gemini AI model.
- Enhance user awareness and training on recognizing phishing attempts, especially those leveraging AI-generated content.
- Scenario-based projections suggest that without intervention, the worst-case scenario could involve widespread data breaches. The best-case scenario involves rapid mitigation and increased resilience against similar threats.
5. Key Individuals and Entities
Marco Figueroa
6. Thematic Tags
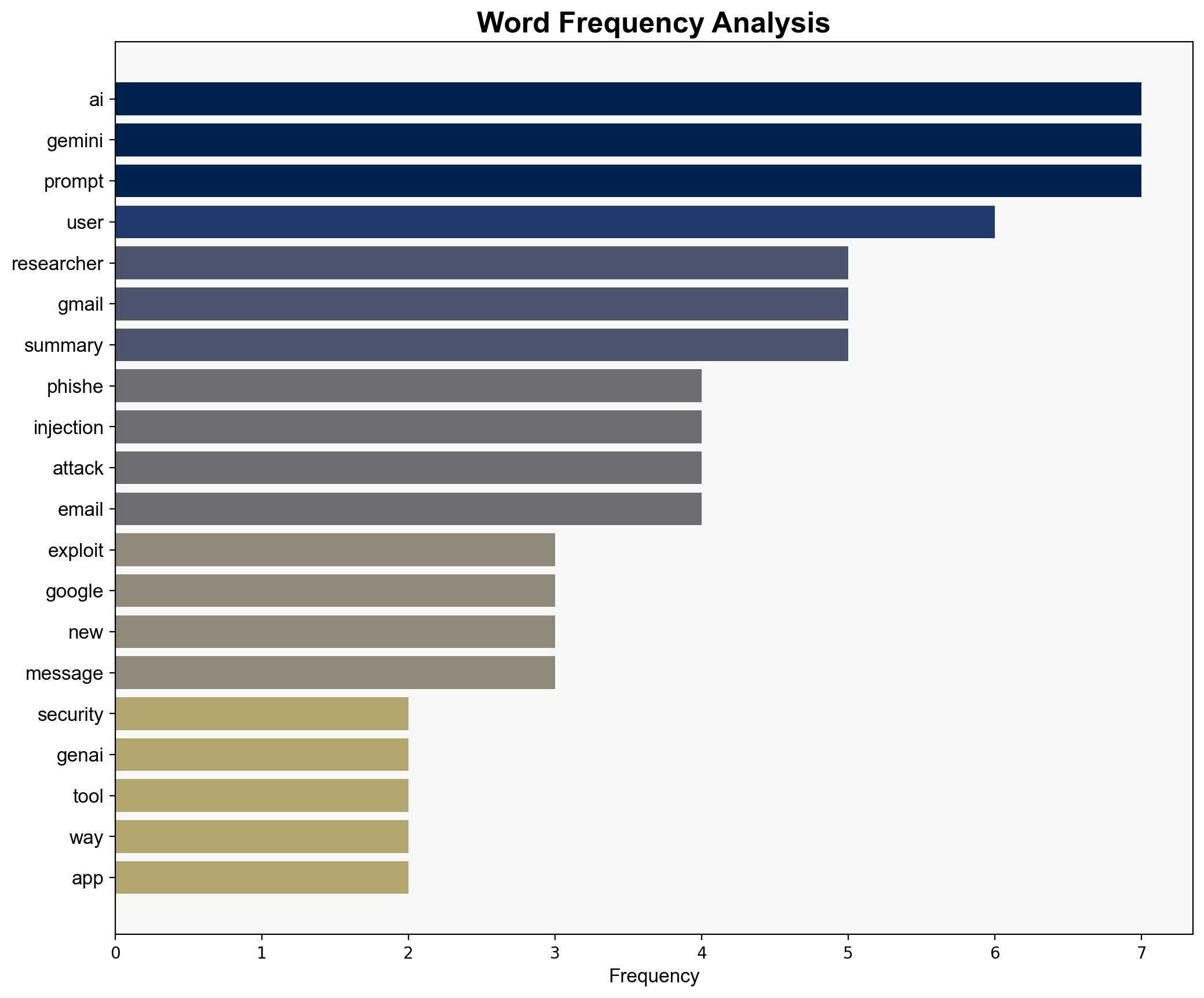
cybersecurity, phishing attacks, AI vulnerabilities, risk mitigation