Government Employee Arrested for Unlawful Retention of National Defense Information – Globalsecurity.org
Published on: 2025-10-22
Intelligence Report: Government Employee Arrested for Unlawful Retention of National Defense Information – Globalsecurity.org
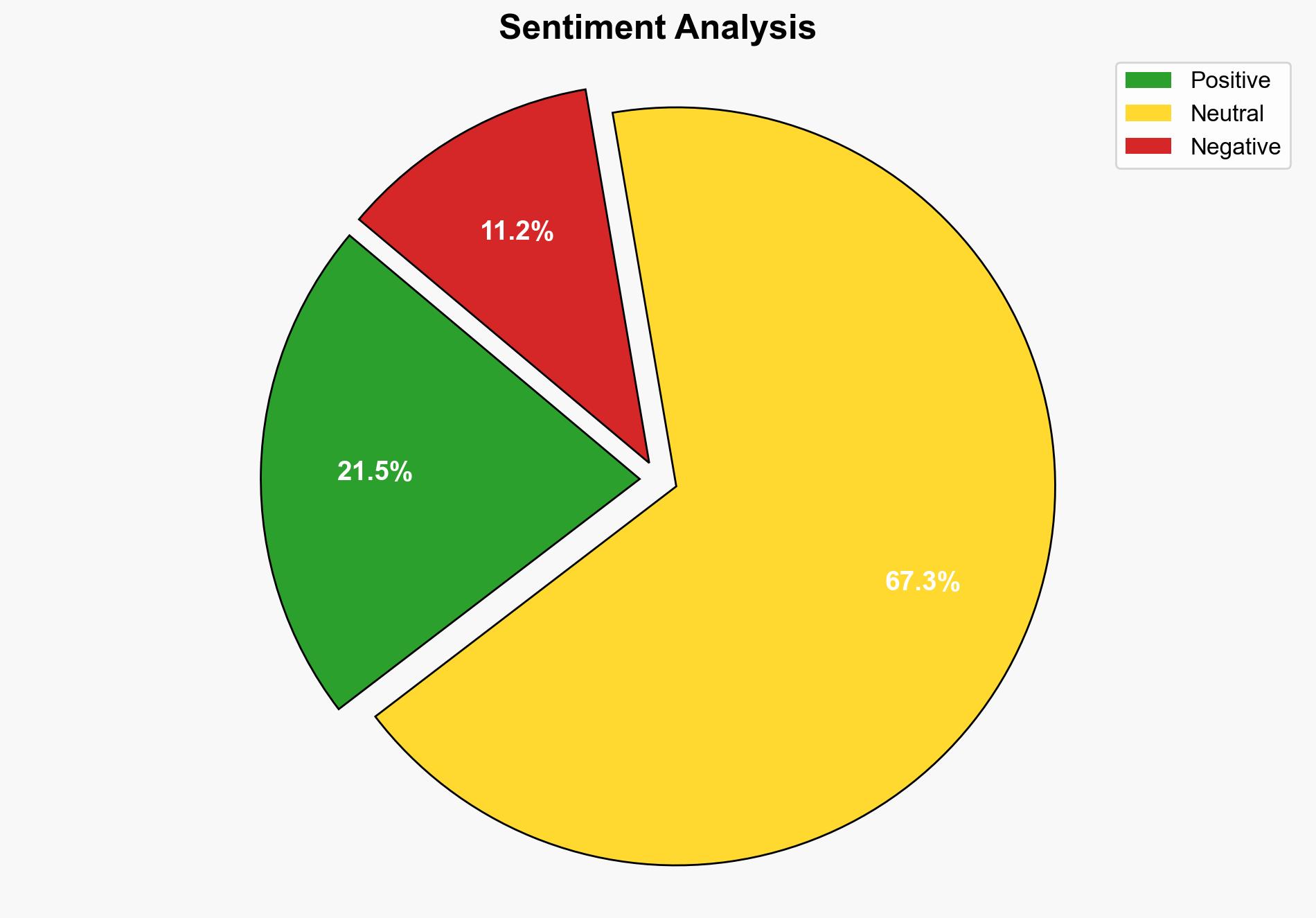
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that Ashley Tellis acted independently in unlawfully retaining classified national defense information for personal use or gain. This conclusion is drawn with moderate confidence due to the lack of evidence indicating external influence or espionage motives. Recommended action includes enhancing security protocols and conducting a thorough investigation to rule out any potential espionage links.
2. Competing Hypotheses
1. **Independent Action Hypothesis**: Ashley Tellis acted alone in retaining classified documents for personal use, possibly for future leverage or career advancement.
2. **Espionage Hypothesis**: Tellis was influenced or coerced by a foreign entity to retain and potentially transfer classified information.
Using ACH 2.0, the Independent Action Hypothesis is better supported due to the lack of direct evidence linking Tellis to foreign entities and the nature of the document storage, which suggests personal rather than organized espionage motives.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the documents were retained without external coercion. The hypothesis relies on the absence of evidence of foreign contact.
– **Red Flags**: The volume of documents and the method of concealment suggest potential premeditation. The absence of clear motive or end-use for the documents is concerning.
– **Blind Spots**: Limited information on Tellis’s communications and interactions with foreign entities or individuals.
4. Implications and Strategic Risks
– **National Security**: Potential exposure of sensitive military capabilities.
– **Geopolitical**: If espionage is involved, it could strain diplomatic relations and increase tensions.
– **Cybersecurity**: Risk of digital breach if documents were shared electronically.
5. Recommendations and Outlook
- Conduct a comprehensive review of security clearance protocols and access controls.
- Enhance monitoring of personnel with access to classified information.
- Scenario Projections:
- Best Case: Independent action confirmed, leading to improved security measures.
- Worst Case: Discovery of espionage links, necessitating diplomatic and security responses.
- Most Likely: Independent action with no foreign involvement, leading to procedural reforms.
6. Key Individuals and Entities
– Ashley Tellis
– Roman Rozhavsky
– Sue Bai
– Darren Cox
– Seth Schlessinger
– Leslie Esbrook
7. Thematic Tags
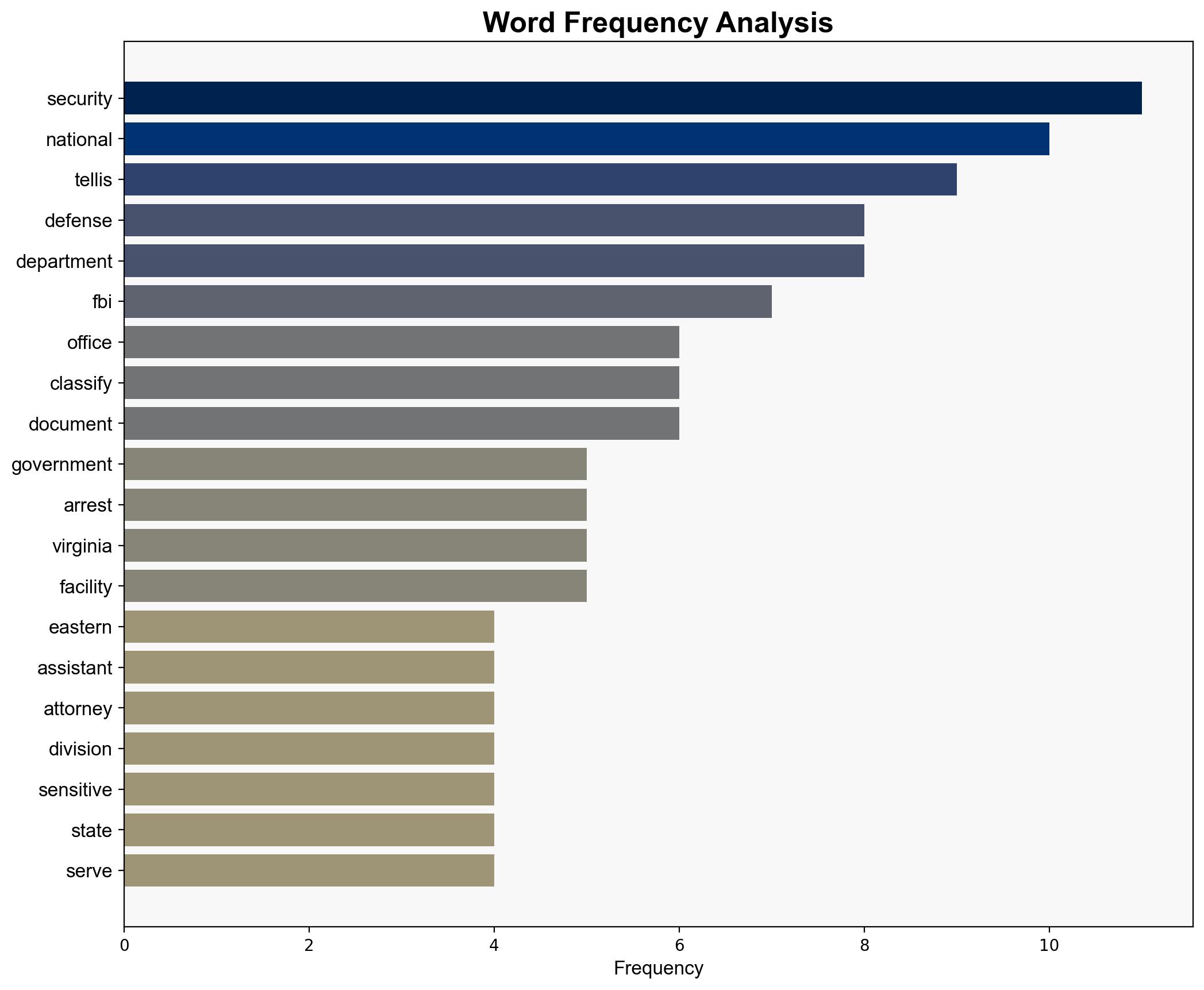
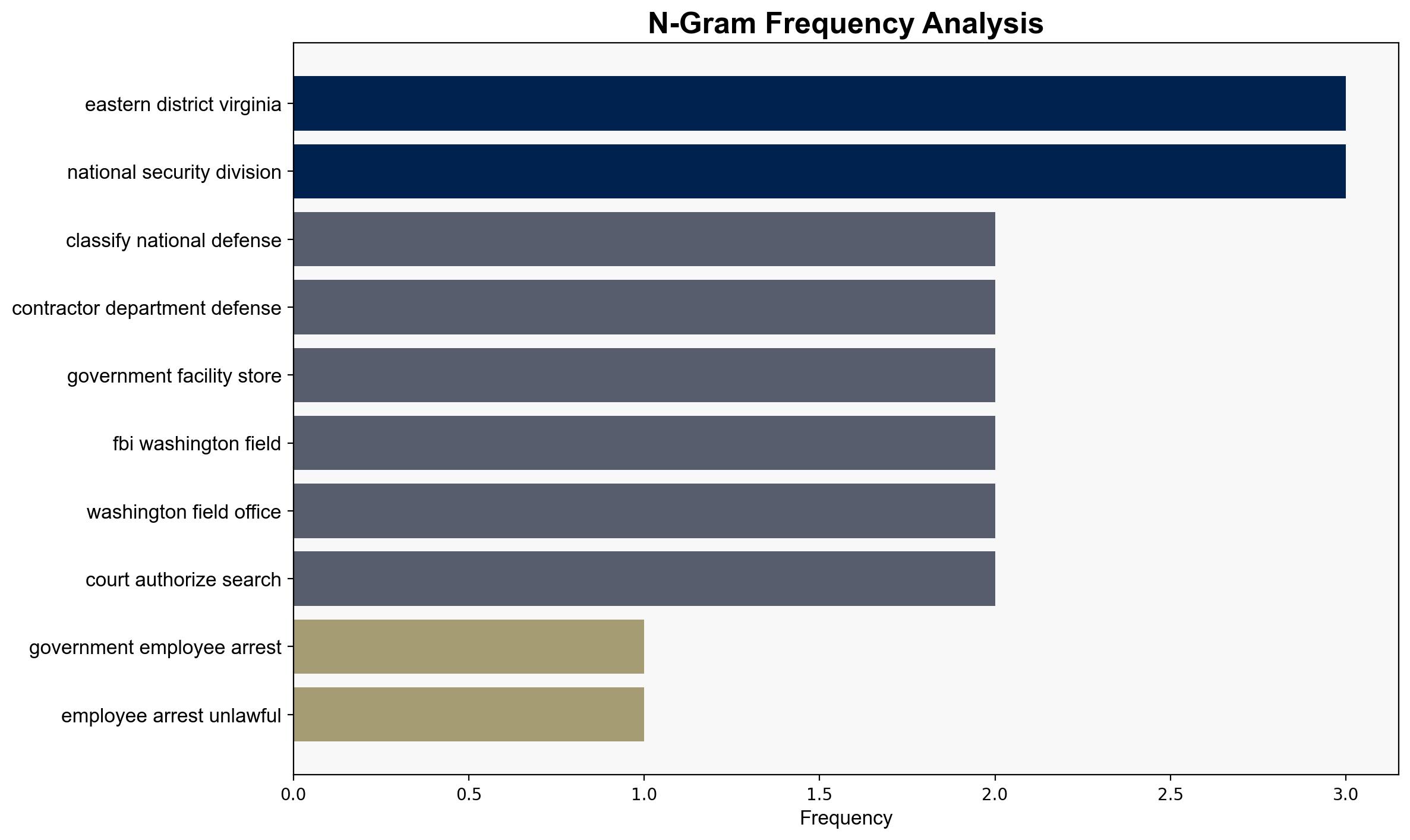
national security threats, cybersecurity, counter-terrorism, regional focus