Ground zero 5 things to do after discovering a cyberattack – We Live Security
Published on: 2025-11-03
Intelligence Report: Ground zero 5 things to do after discovering a cyberattack – We Live Security
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that rapid and structured incident response is crucial to minimizing the impact of a cyberattack. This is based on the evidence that timely actions can significantly reduce the breach lifecycle and associated costs. Confidence level: High. Recommended action: Organizations should prioritize developing and rehearsing comprehensive incident response plans to ensure swift action in the event of a breach.
2. Competing Hypotheses
1. **Hypothesis A**: A well-prepared incident response team can effectively mitigate the impact of a cyberattack if they act swiftly and decisively.
2. **Hypothesis B**: Despite preparation, the complexity and speed of modern cyberattacks may still overwhelm incident response efforts, leading to significant damage.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the emphasis on preparation and rapid response reducing breach costs and lifecycle, as indicated by the source.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that organizations have the resources and capability to develop and implement effective incident response plans. Another assumption is that all stakeholders will be promptly informed and coordinated.
– **Red Flags**: The source does not address potential resource constraints or organizational inertia that could hinder rapid response. There is also a lack of data on how often incident response plans are successfully executed in real-world scenarios.
4. Implications and Strategic Risks
The primary implication is that organizations with robust incident response plans can significantly reduce the financial and reputational damage from cyberattacks. However, the risk remains that sophisticated attacks could bypass even the best-prepared defenses, leading to potential economic losses and data breaches. There is also a risk of cascading effects if sensitive data is compromised, affecting customer trust and regulatory compliance.
5. Recommendations and Outlook
- Organizations should conduct regular incident response drills and update their plans based on evolving threats.
- Invest in advanced threat detection and response technologies to enhance speed and accuracy.
- Scenario Projections:
- Best Case: Rapid response limits breach impact, preserving organizational integrity and customer trust.
- Worst Case: Delayed response leads to significant data loss and financial penalties.
- Most Likely: Prepared organizations will manage breaches effectively, but unprepared ones will face severe consequences.
6. Key Individuals and Entities
No specific individuals are mentioned in the source. The focus is on organizational roles such as incident response teams and stakeholders.
7. Thematic Tags
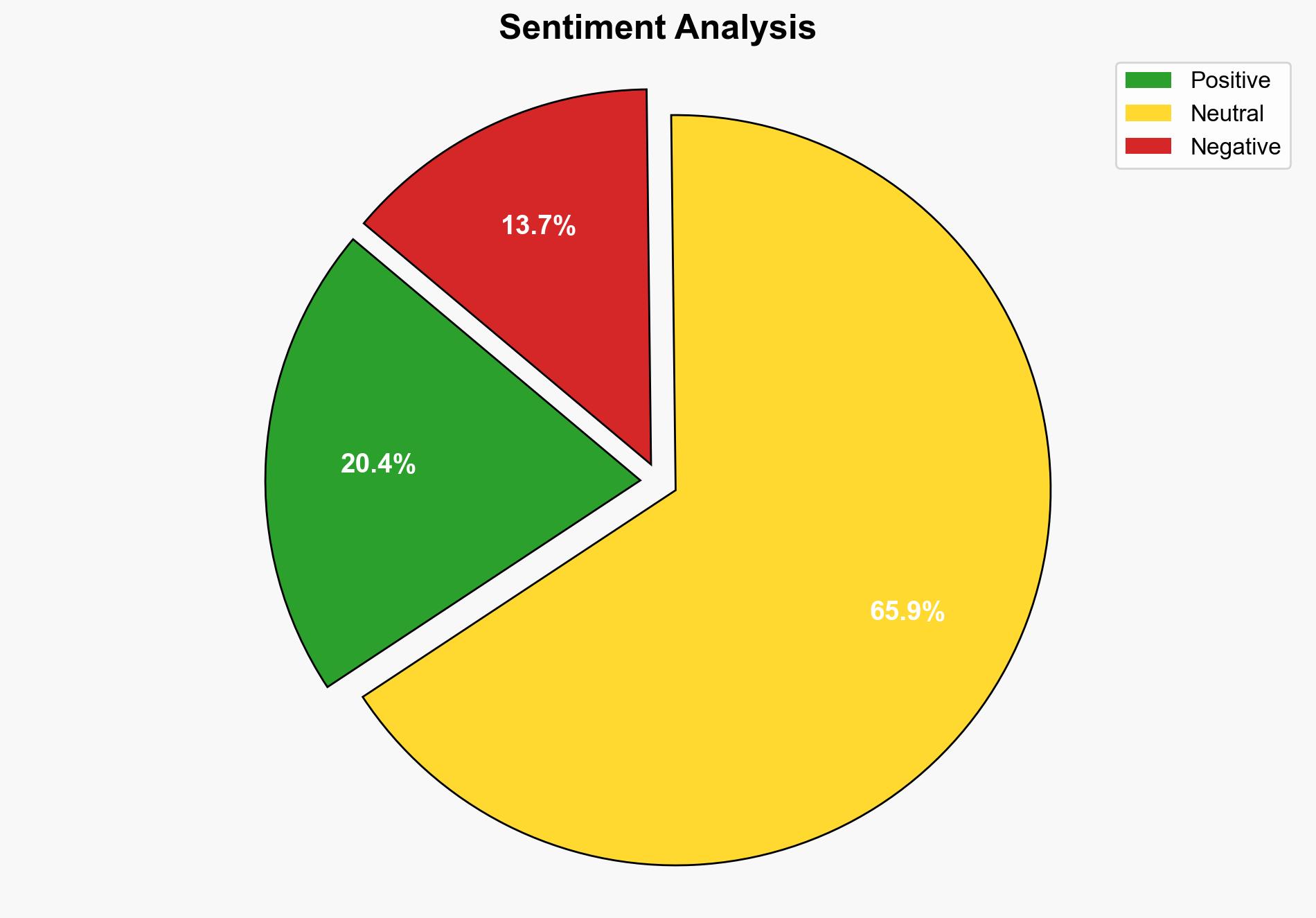
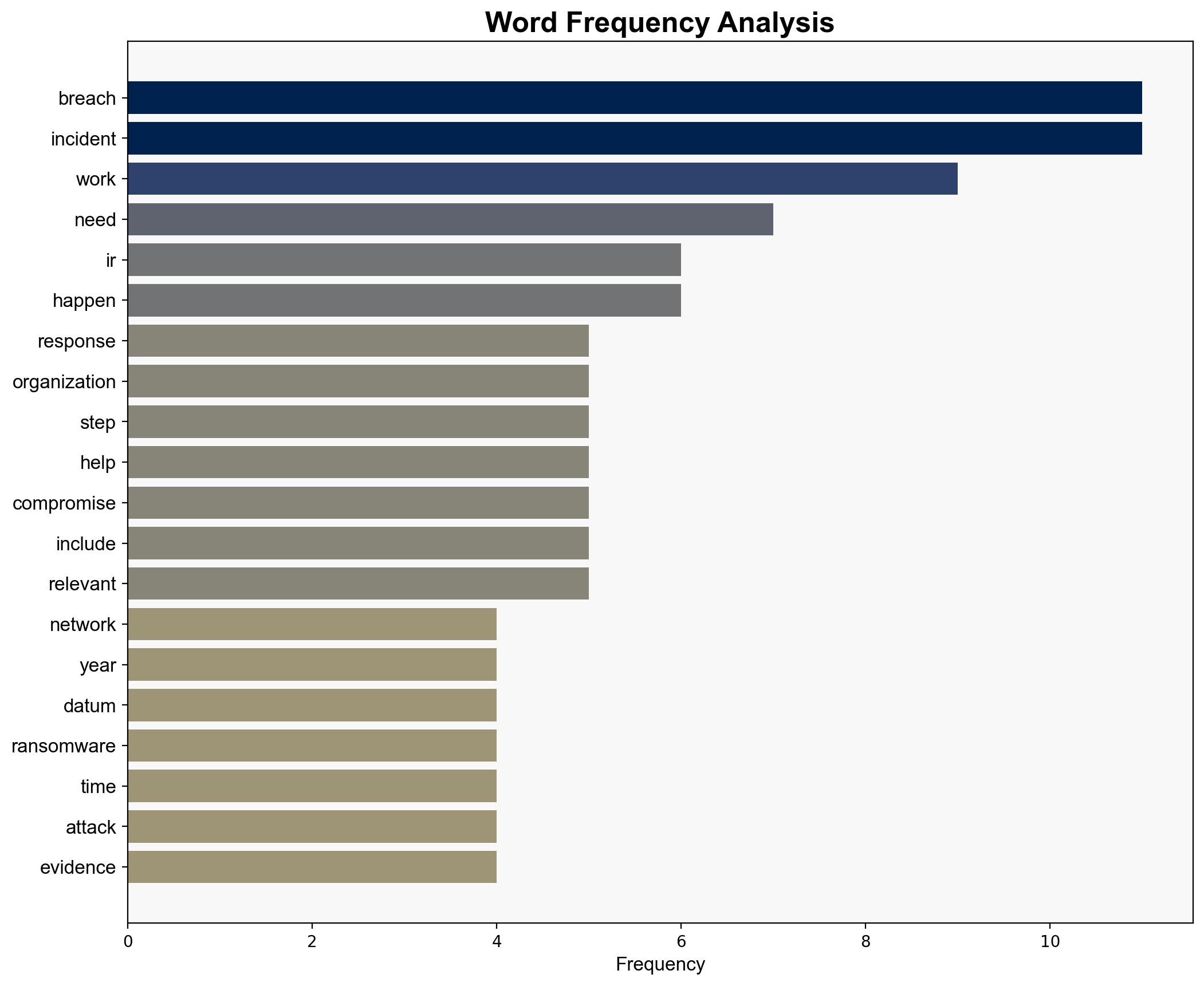
national security threats, cybersecurity, incident response, data breach, organizational resilience