Grubhub acknowledges data theft in security breach, faces potential extortion threats
Published on: 2026-01-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Grubhub confirms hackers stole data in recent security breach
1. BLUF (Bottom Line Up Front)
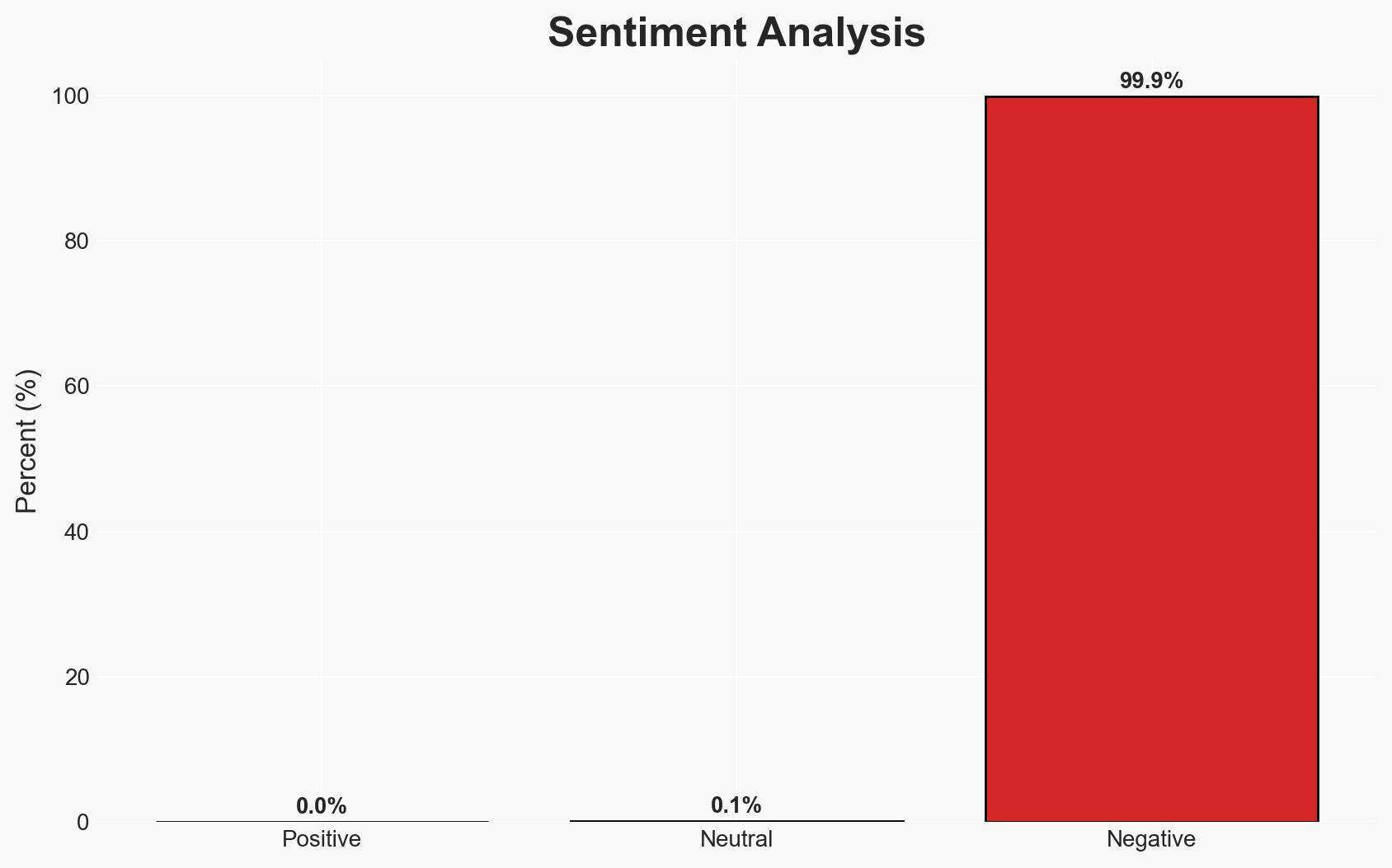
Grubhub has experienced a data breach attributed to the ShinyHunters cybercrime group, resulting in extortion demands. The breach involved unauthorized access to Grubhub’s systems, but reportedly did not compromise sensitive financial or order history data. The incident follows a related wave of scam emails. The overall confidence level in this assessment is moderate due to limited disclosure from Grubhub and unverified claims regarding the cyber actors involved.
2. Competing Hypotheses
- Hypothesis A: The breach is a targeted attack by ShinyHunters, leveraging previously stolen Salesforce data to extort Grubhub. This is supported by multiple sources attributing the attack to ShinyHunters and the demand for Bitcoin payments. However, the lack of direct confirmation from the threat actors introduces uncertainty.
- Hypothesis B: The breach is an opportunistic attack by an unknown group exploiting vulnerabilities in Grubhub’s system, unrelated to ShinyHunters. This hypothesis considers the possibility of misattribution or multiple groups exploiting similar vulnerabilities, but lacks direct supporting evidence.
- Assessment: Hypothesis A is currently better supported due to consistent reporting from multiple sources about ShinyHunters’ involvement and the extortion demands. Confirmation from the threat actors or further evidence could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Grubhub’s internal systems were sufficiently secured prior to the breach; ShinyHunters is the sole group involved; the breach and scam emails are connected.
- Information Gaps: Exact timeline of the breach, specific data accessed, and the full scope of the extortion demands.
- Bias & Deception Risks: Potential bias from sources with vested interests in cybersecurity narratives; possible deception by threat actors to mislead attribution.
4. Implications and Strategic Risks
This breach could lead to increased scrutiny on Grubhub’s cybersecurity measures and affect customer trust. If unresolved, it may encourage further cyber extortion attempts against similar platforms.
- Political / Geopolitical: Limited direct implications, but could influence regulatory discussions on data protection.
- Security / Counter-Terrorism: Heightened alert for similar cyber extortion tactics targeting critical service providers.
- Cyber / Information Space: Potential for increased cyber threat activity exploiting similar vulnerabilities across platforms.
- Economic / Social: Possible financial impact on Grubhub and erosion of consumer confidence in digital service providers.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Grubhub should enhance monitoring of its systems, engage with cybersecurity experts for a comprehensive security audit, and communicate transparently with stakeholders.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms, invest in employee training, and implement advanced threat detection technologies.
- Scenario Outlook: Best: Breach contained with minimal impact; Worst: Data released, leading to significant financial and reputational damage; Most-Likely: Continued negotiation with threat actors, with partial data exposure.
6. Key Individuals and Entities
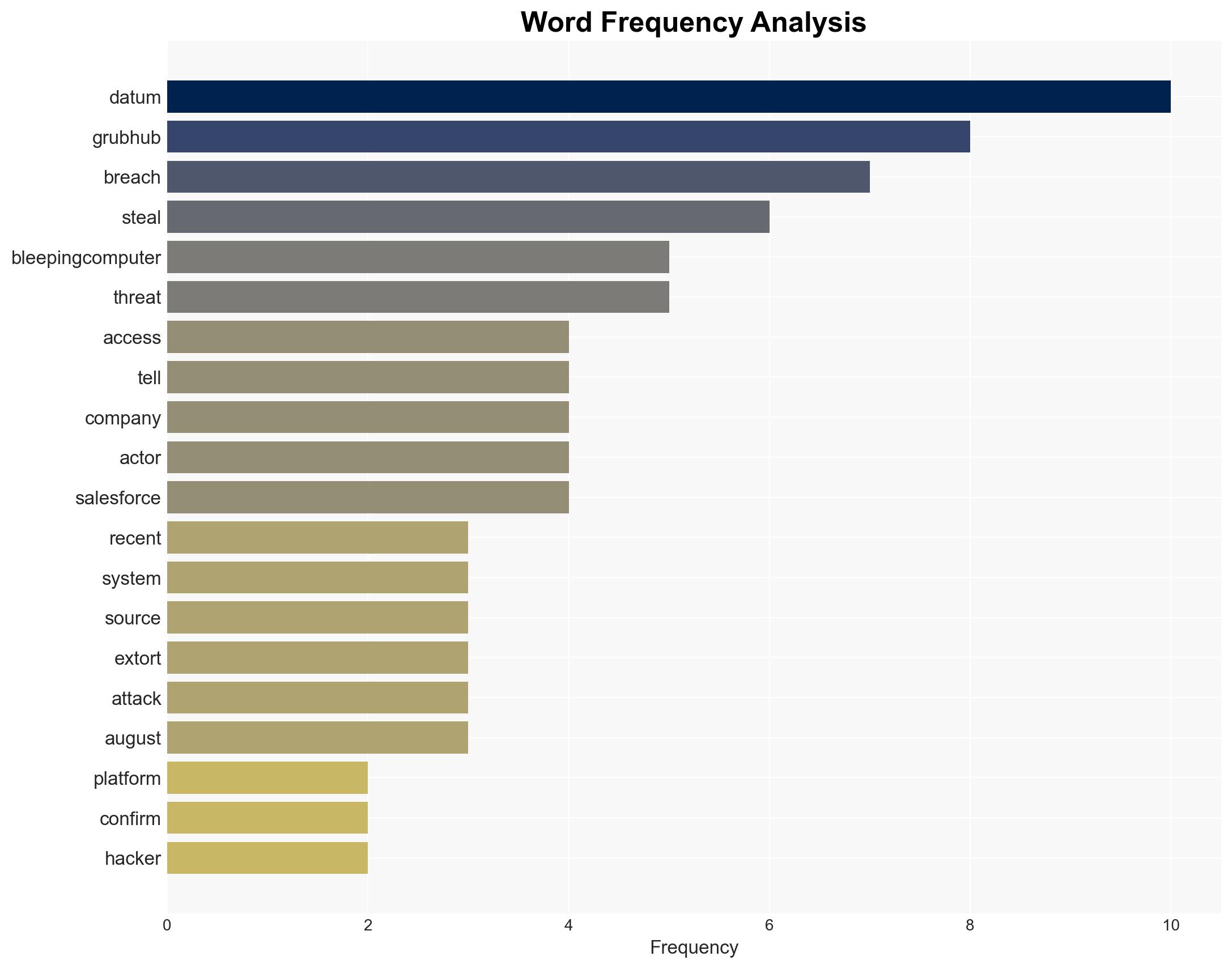
- Grubhub
- ShinyHunters
- BleepingComputer
- Google’s Threat Intelligence team (Mandiant)
- Salesloft
7. Thematic Tags
cybersecurity, data breach, extortion, cybercrime, information security, digital platforms
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us