Hack of US Surveillance Provider RemoteCOM Exposes Court Data – HackRead
Published on: 2025-09-30
Intelligence Report: Hack of US Surveillance Provider RemoteCOM Exposes Court Data – HackRead
1. BLUF (Bottom Line Up Front)
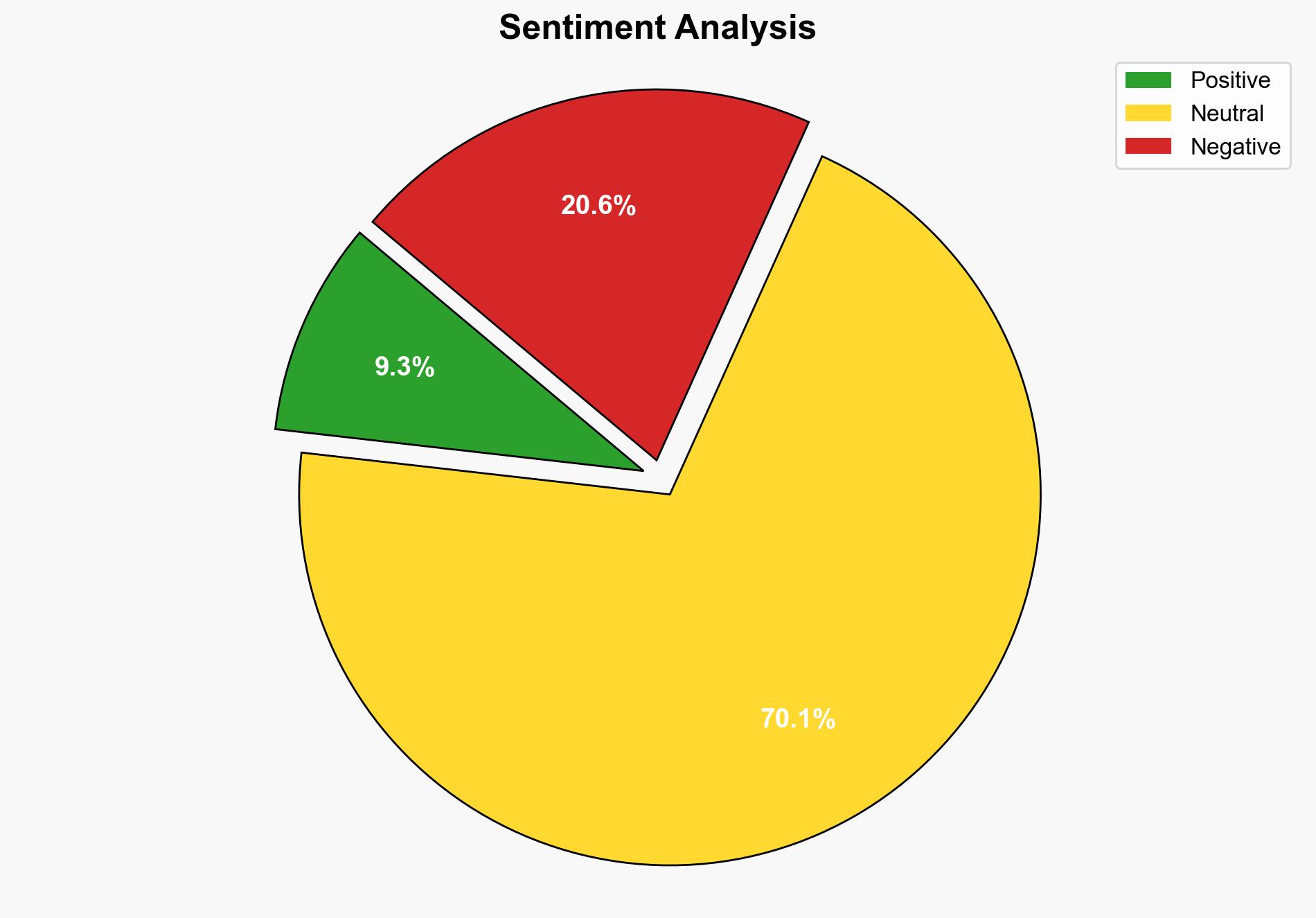
The breach of RemoteCOM, a surveillance provider, has exposed sensitive court data, posing significant risks to individuals under monitoring and law enforcement personnel. The most supported hypothesis suggests a targeted attack aimed at exploiting surveillance data for malicious purposes. Confidence level: Moderate. Recommended action: Enhance cybersecurity measures for surveillance systems and initiate a comprehensive risk assessment of exposed individuals and entities.
2. Competing Hypotheses
1. **Targeted Exploitation Hypothesis**: The breach was a deliberate attack by a sophisticated actor aiming to exploit sensitive surveillance data for malicious purposes, such as blackmail or identity theft.
2. **Opportunistic Breach Hypothesis**: The breach was an opportunistic attack by hackers with no specific target, aiming to sell or leak data for financial gain or notoriety.
Using Analysis of Competing Hypotheses (ACH 2.0), the Targeted Exploitation Hypothesis is better supported due to the selective nature of the data exposed, including sensitive personal and law enforcement information, suggesting a motive beyond financial gain.
3. Key Assumptions and Red Flags
– **Assumptions**: The attackers had prior knowledge of the value of the data. RemoteCOM’s security measures were insufficient to prevent such a breach.
– **Red Flags**: Lack of immediate response from RemoteCOM raises concerns about internal security protocols. The hacker’s claim of ease in breaching the system suggests potential insider knowledge or severe security lapses.
4. Implications and Strategic Risks
The breach could lead to increased targeting of individuals under surveillance, potentially compromising ongoing investigations and endangering law enforcement personnel. There is a risk of cascading effects, including loss of public trust in surveillance systems and potential geopolitical tensions if foreign actors are involved.
5. Recommendations and Outlook
- Conduct a thorough cybersecurity audit of RemoteCOM and similar providers to identify vulnerabilities.
- Implement enhanced encryption and access controls for sensitive data.
- Develop a rapid response protocol for data breaches involving sensitive surveillance information.
- Best-case scenario: Breach is contained, and vulnerabilities are addressed, restoring trust in surveillance systems.
- Worst-case scenario: Data is used for widespread malicious activities, leading to severe consequences for individuals and law enforcement.
- Most likely scenario: Increased scrutiny and regulatory pressure on surveillance providers to enhance data protection measures.
6. Key Individuals and Entities
– RemoteCOM (surveillance provider)
– Hacker known as “wikkid” (claimed responsibility for the breach)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus