Hacker using backdoor to exploit SonicWall Secure Mobile Access to steal credentials – TechRadar
Published on: 2025-07-17
Intelligence Report: Hacker using backdoor to exploit SonicWall Secure Mobile Access to steal credentials – TechRadar
1. BLUF (Bottom Line Up Front)
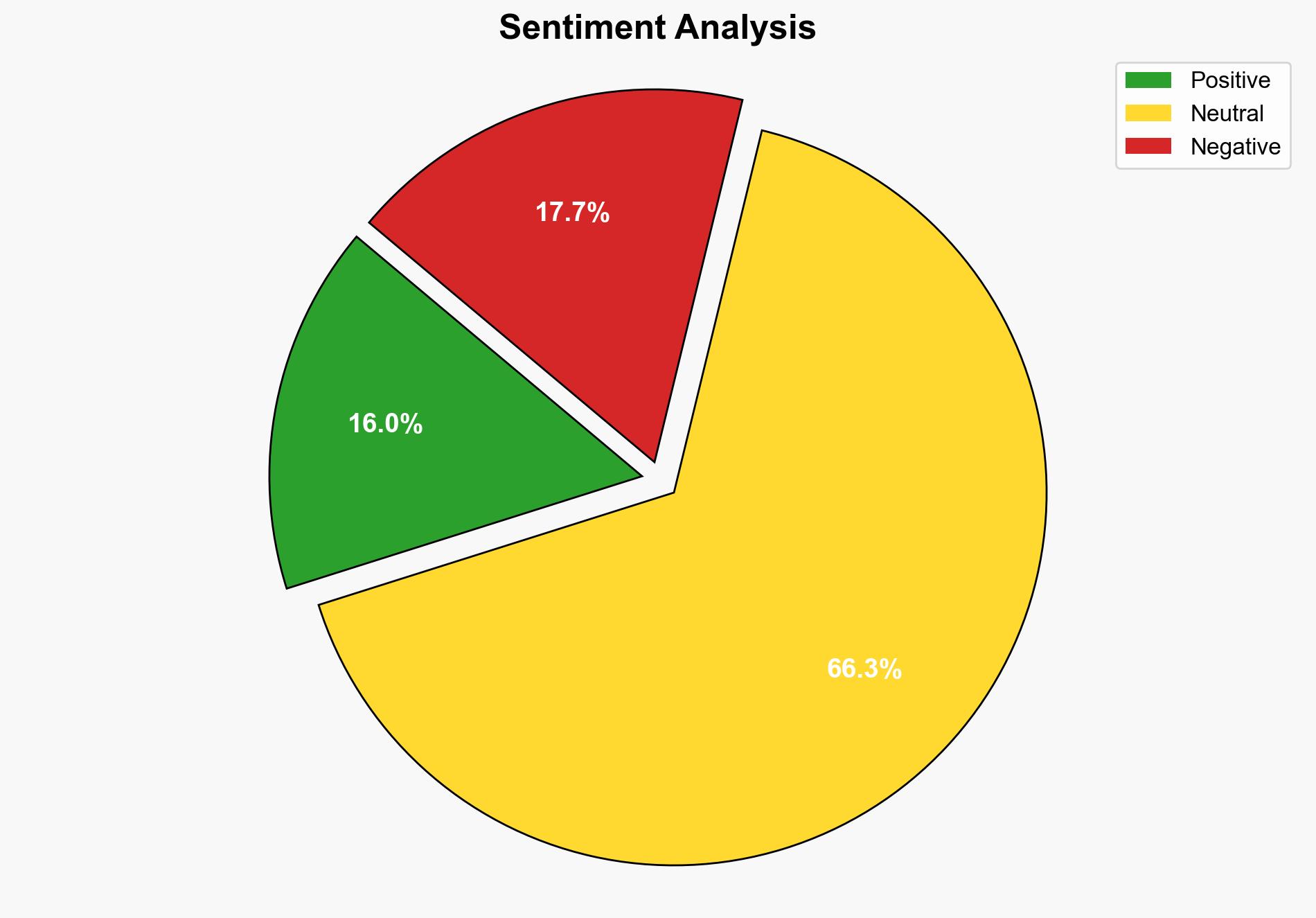
A cyber threat actor, tracked as UNC, has exploited a vulnerability in SonicWall Secure Mobile Access (SMA) appliances to steal credentials, potentially leading to ransomware deployment. Despite the vulnerability being patched, the threat actor has found a way to bypass security measures. Immediate action is required to update systems and enhance security protocols to prevent further exploitation.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that the threat actor uses a persistent backdoor, possibly a rootkit, to maintain access and steal sensitive information. This highlights the need for enhanced monitoring of network anomalies.
Indicators Development
Key indicators include unauthorized access attempts, unusual network traffic, and modifications to the appliance boot process. Monitoring these can aid in early detection of similar threats.
Bayesian Scenario Modeling
Probabilistic models suggest a moderate likelihood of continued attacks on unpatched systems, with a high probability of credential theft leading to ransomware deployment.
3. Implications and Strategic Risks
The exploitation of SonicWall SMA appliances poses significant risks to organizations relying on these systems for secure remote access. Potential cascading effects include data breaches, financial loss, and operational disruptions. The persistent nature of the threat actor suggests a sophisticated operation with possible links to broader cybercriminal networks.
4. Recommendations and Outlook
- Immediately apply all available patches to SonicWall SMA appliances and conduct thorough security audits.
- Implement advanced monitoring solutions to detect and respond to anomalies in real-time.
- Consider scenario-based planning:
- Best Case: Rapid patching and monitoring prevent further breaches.
- Worst Case: Continued exploitation leads to widespread ransomware attacks.
- Most Likely: Ongoing attempts to exploit unpatched systems with sporadic success.
5. Key Individuals and Entities
Google’s Threat Intelligence Group is actively monitoring the situation and providing insights into the threat actor’s activities.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus