Hackers abuse TOR network and misconfigured Docker APIs to steal crypto – so keep an eye on your wallet – TechRadar
Published on: 2025-09-10
Intelligence Report: Hackers abuse TOR network and misconfigured Docker APIs to steal crypto – so keep an eye on your wallet – TechRadar
1. BLUF (Bottom Line Up Front)
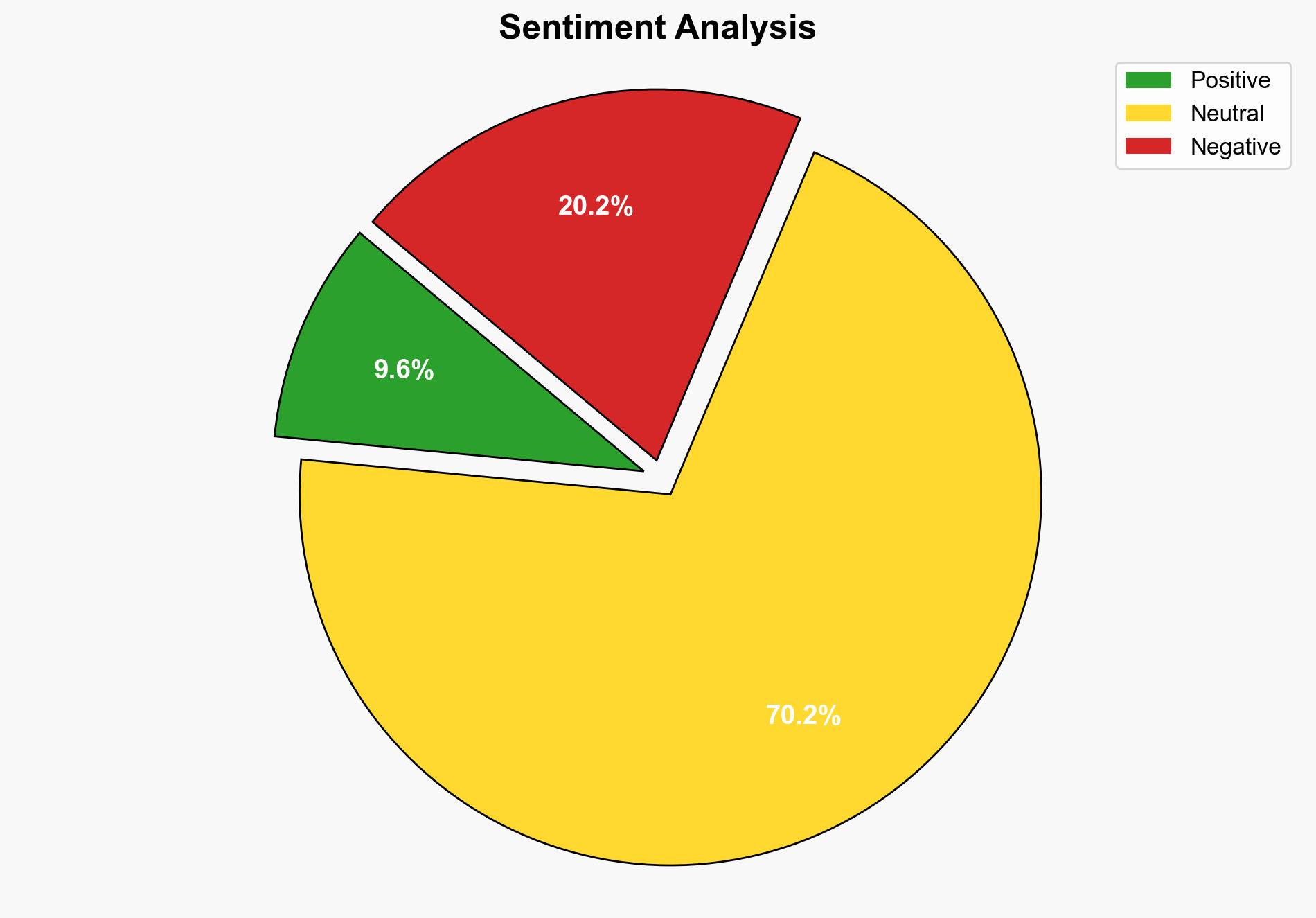
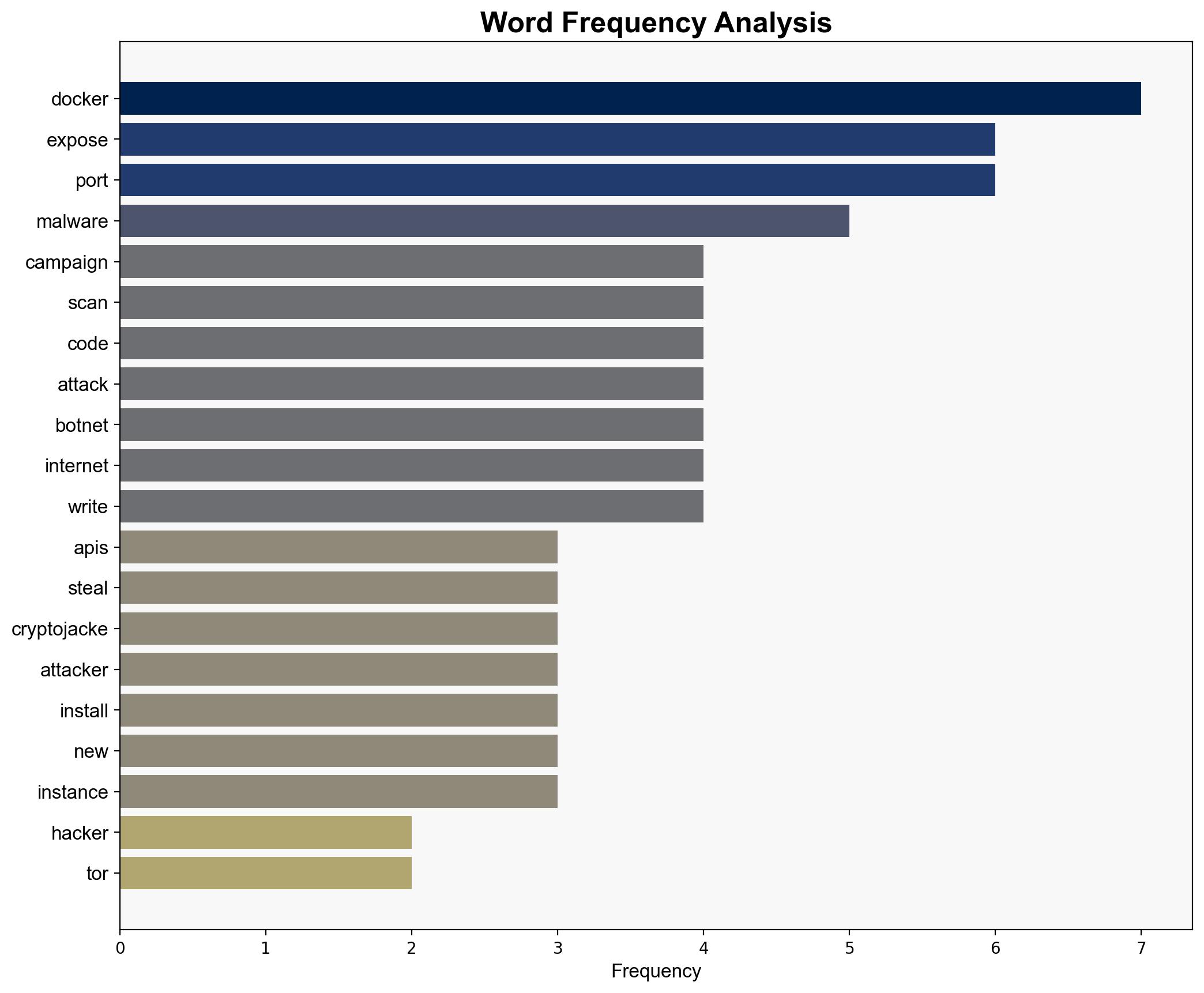
The most supported hypothesis is that cybercriminals are leveraging misconfigured Docker APIs and the TOR network to conduct a sophisticated cryptojacking campaign, potentially expanding into a botnet for broader cyber-attacks. Confidence level: Moderate. Recommended action: Strengthen Docker security configurations and monitor network traffic for anomalies.
2. Competing Hypotheses
1. **Hypothesis A**: The primary goal of the attackers is to exploit misconfigured Docker APIs to mine cryptocurrency using cryptojacking techniques, with the TOR network providing anonymity.
2. **Hypothesis B**: The attackers are using the cryptojacking as a cover for building a botnet, which could be used for more extensive cyber-attacks such as DDoS or data theft.
Using ACH 2.0, Hypothesis A is better supported due to the detailed description of cryptojacking activities and the use of persistence tools. However, the presence of inactive code suggests potential for Hypothesis B, indicating a broader strategic intent.
3. Key Assumptions and Red Flags
– Assumptions for Hypothesis A: The primary motivation is financial gain through cryptojacking.
– Assumptions for Hypothesis B: The cryptojacking is a secondary objective, with the main goal being the expansion of a botnet.
– Red Flags: The presence of inactive code and potential for further exploitation indicates a possible underestimation of the attackers’ capabilities.
– Blind Spots: Lack of detailed information on the attackers’ identity and ultimate objectives.
4. Implications and Strategic Risks
The campaign could lead to significant financial losses for individuals and businesses through cryptojacking. If the botnet hypothesis is correct, there is a risk of large-scale cyber-attacks, including DDoS attacks, which could disrupt critical infrastructure. The use of TOR complicates attribution and response efforts, increasing the challenge for cybersecurity defenses.
5. Recommendations and Outlook
- Strengthen Docker security by isolating environments and limiting exposed services.
- Implement network monitoring to detect unusual traffic patterns indicative of cryptojacking or botnet activity.
- Scenario Projections:
- Best Case: Attackers are quickly identified and neutralized, minimizing damage.
- Worst Case: Botnet expands, leading to widespread cyber-attacks and significant economic impact.
- Most Likely: Continued cryptojacking activities with gradual expansion of botnet capabilities.
6. Key Individuals and Entities
– No specific individuals identified in the report. The entities involved include the TOR network and Docker API users.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus