Hackers are hitting firewalls and VPNs to breach businesses – TechRadar
Published on: 2025-04-22
Intelligence Report: Hackers are hitting firewalls and VPNs to breach businesses – TechRadar
1. BLUF (Bottom Line Up Front)
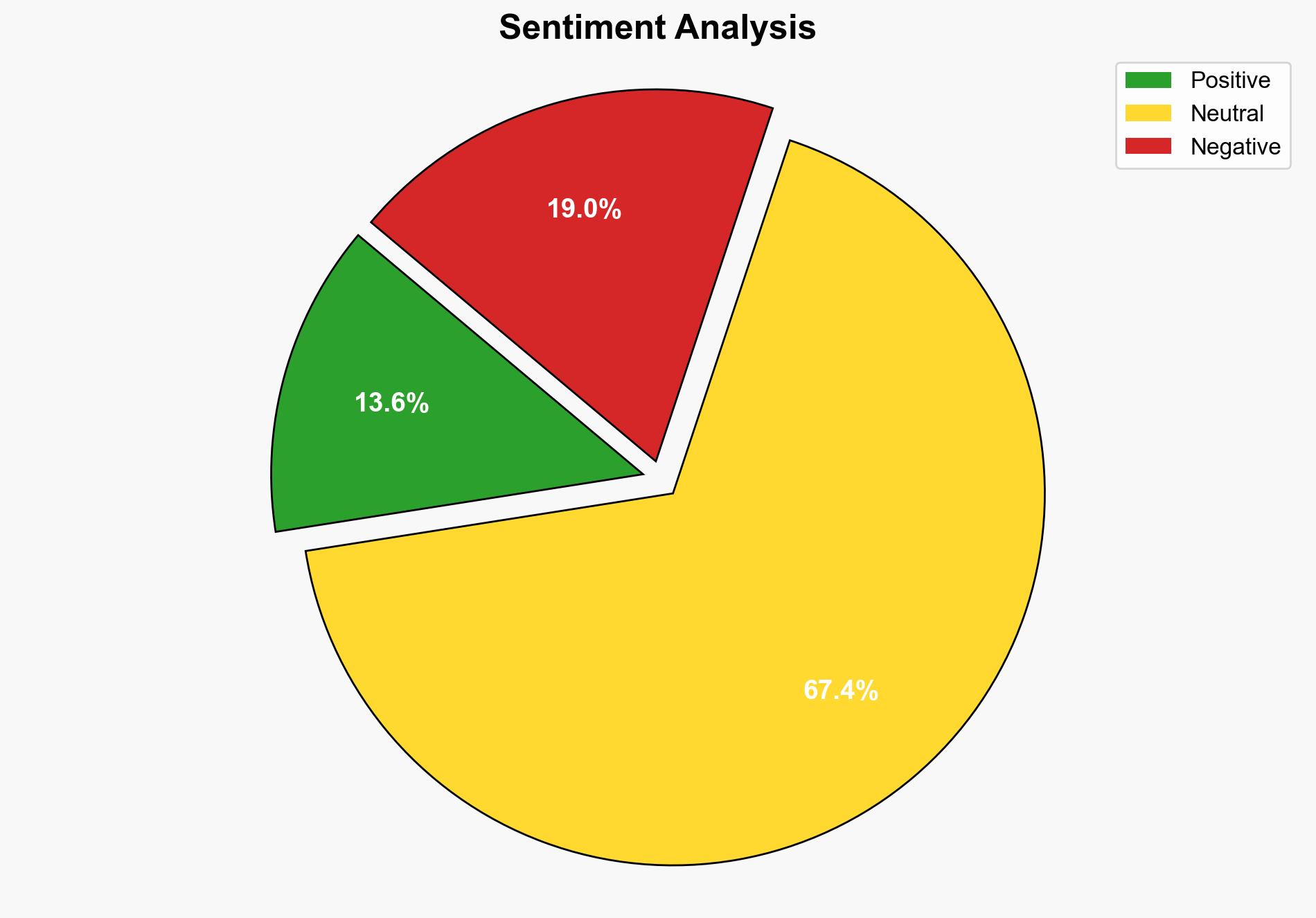
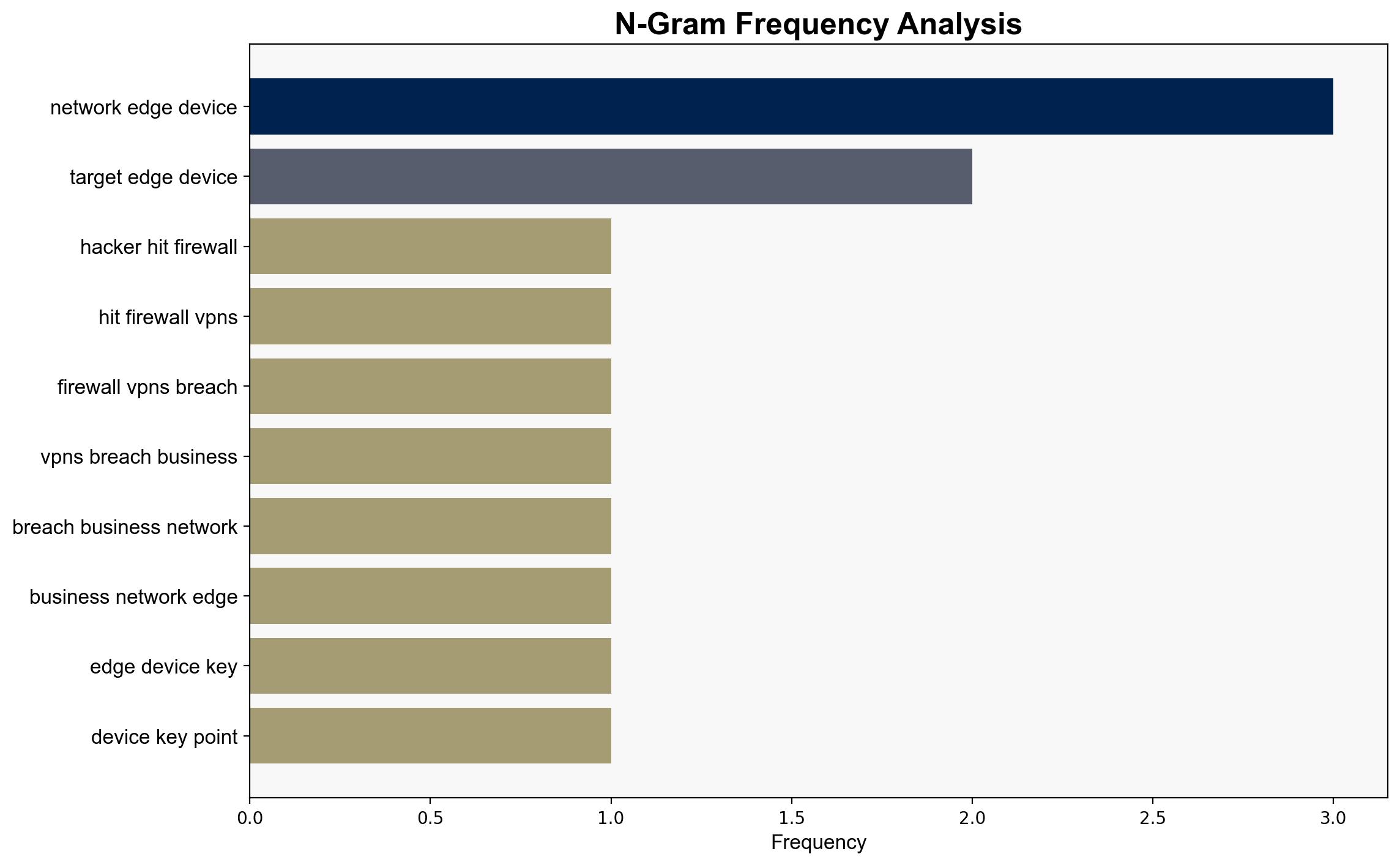
Recent findings indicate a significant increase in cyberattacks targeting network edge devices such as firewalls and VPNs. These devices are becoming primary points of entry for attackers, leading to a rise in ransomware incidents and data exfiltration. Organizations must prioritize updating and securing these devices to mitigate risks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The primary hypothesis is that attackers are increasingly targeting network edge devices due to their vulnerabilities and the high impact of successful breaches. Alternative hypotheses, such as internal threats or other entry points, were considered but found less supported by current evidence.
SWOT Analysis
Strengths: Organizations with robust patch management and updated security protocols.
Weaknesses: High prevalence of end-of-life devices and inadequate patching.
Opportunities: Implementing advanced threat detection and response systems.
Threats: Increasing sophistication of AI-enabled phishing attacks.
Indicators Development
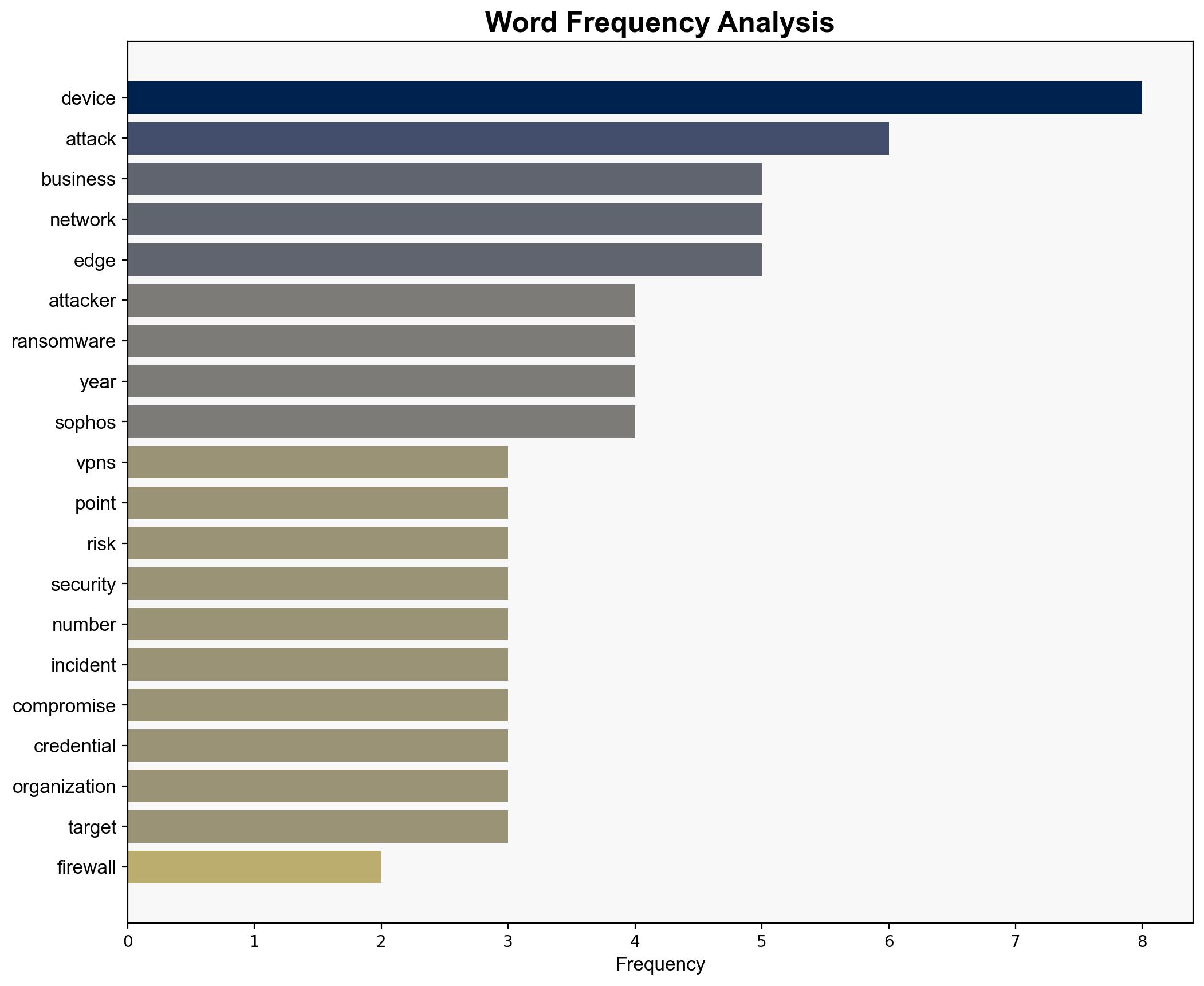
Key indicators include unusual network traffic patterns, increased phishing attempts, and unauthorized access attempts on edge devices. Monitoring these signs can help in early threat detection.
3. Implications and Strategic Risks
The growing trend of targeting network edge devices poses significant risks to organizational cybersecurity. This could lead to increased operational costs, data breaches, and potential economic impacts. The reliance on outdated devices exacerbates these vulnerabilities, necessitating immediate attention to lifecycle management.
4. Recommendations and Outlook
- Conduct comprehensive audits of network edge devices and prioritize updates and patches.
- Invest in AI-driven threat detection systems to identify and respond to phishing and other sophisticated attacks.
- Scenario-based projections:
- Best Case: Enhanced security measures lead to a significant reduction in successful breaches.
- Worst Case: Continued neglect of device updates results in widespread data breaches and financial losses.
- Most Likely: Gradual improvement in security posture as awareness and technology adoption increase.
5. Key Individuals and Entities
Sean Gallagher, a principal threat researcher at Sophos, has highlighted the critical need for improved lifecycle management of network edge devices.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)