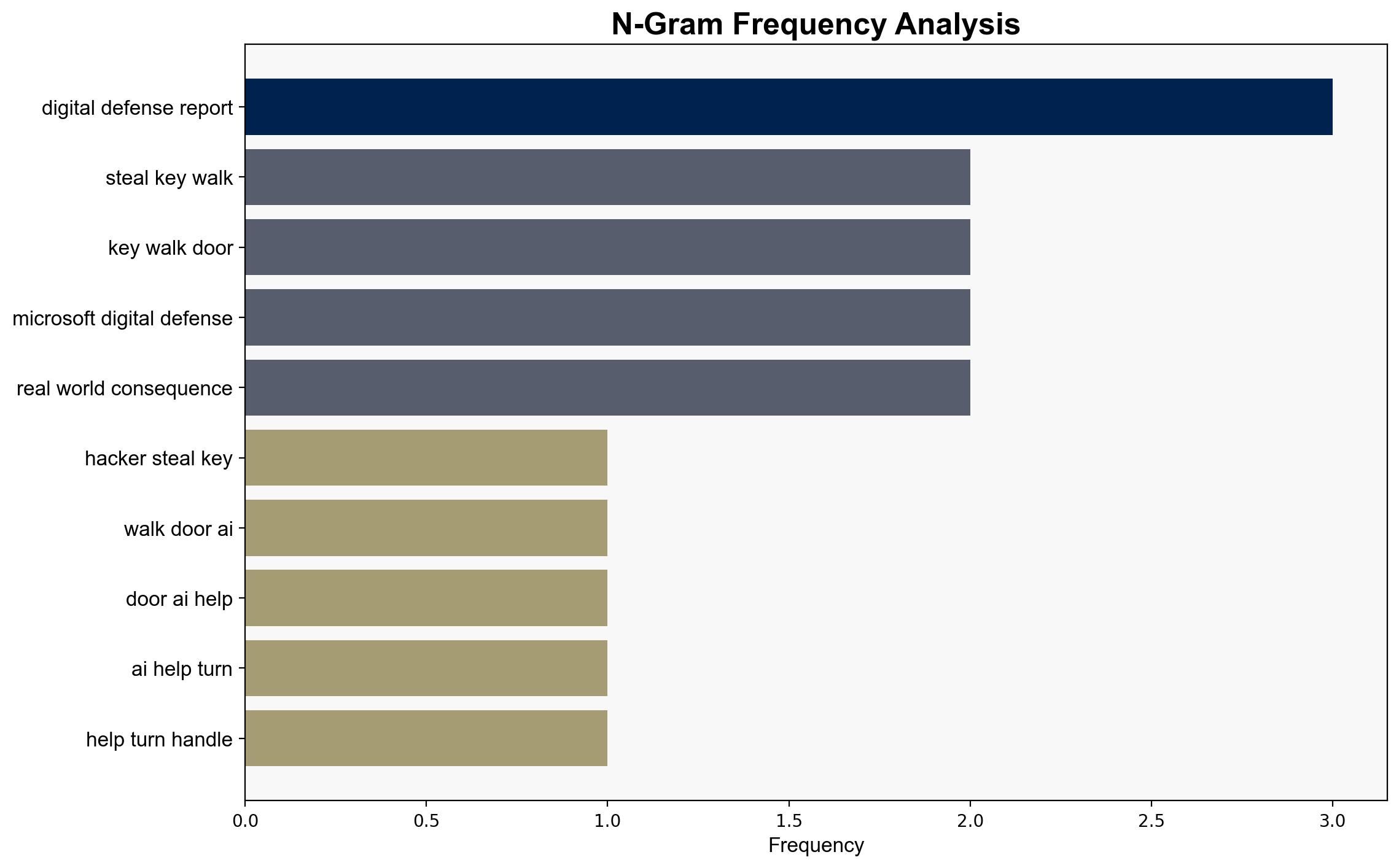
Hackers are stealing the keys and walking through the front door and AI is helping them turn the handle – TechRadar
Published on: 2025-10-16
Intelligence Report: Hackers are stealing the keys and walking through the front door and AI is helping them turn the handle – TechRadar
1. BLUF (Bottom Line Up Front)
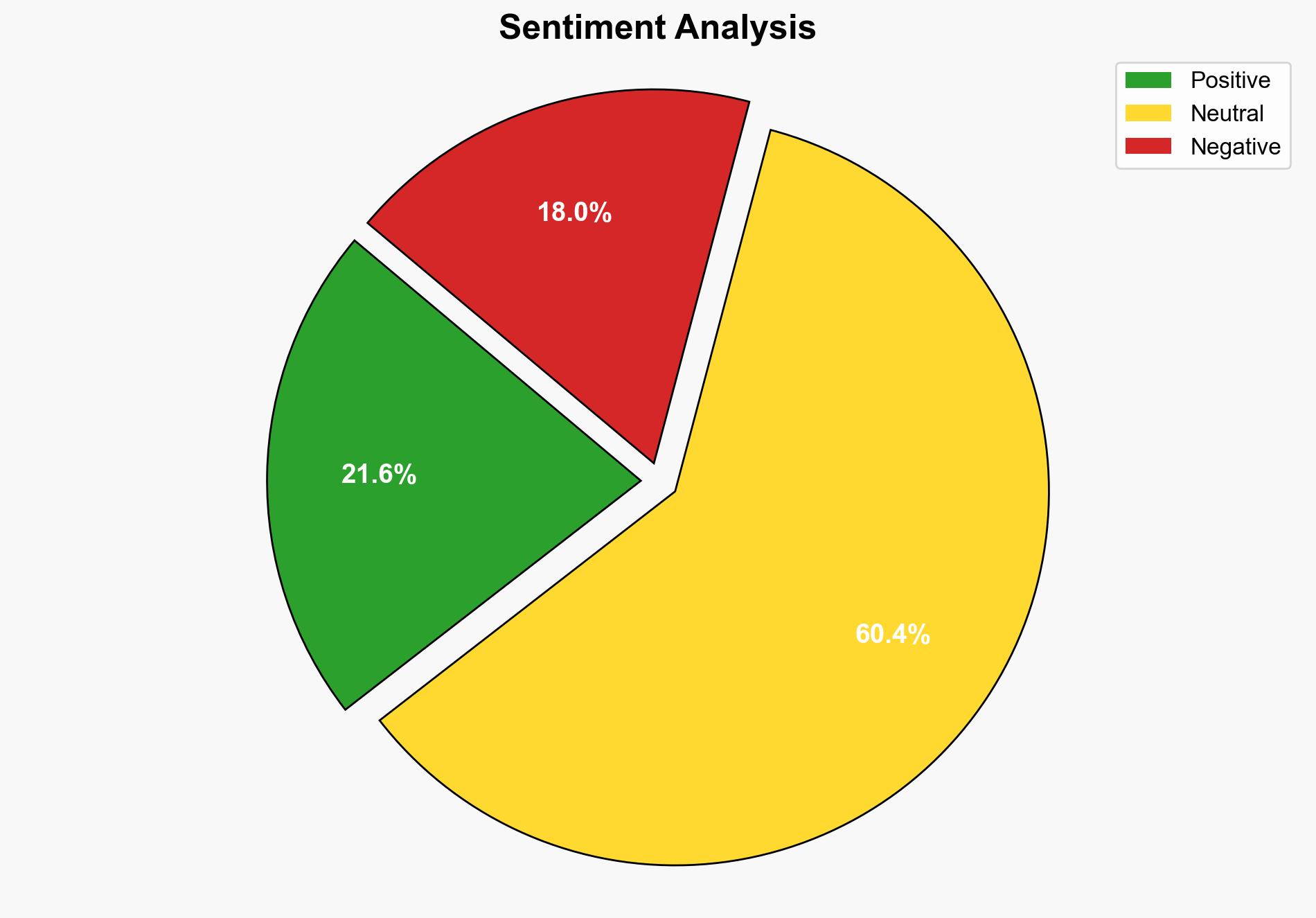
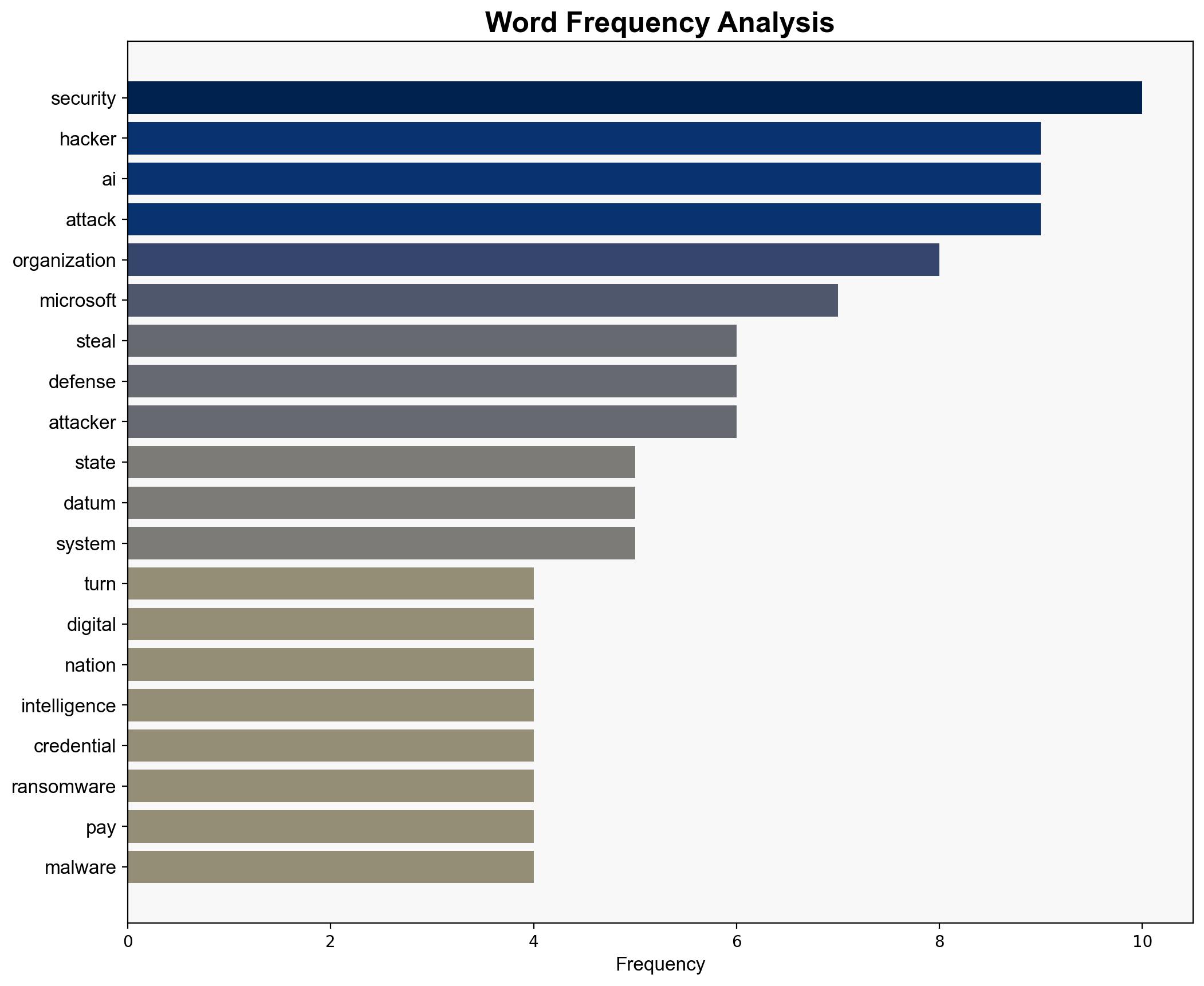
The strategic judgment is that the integration of AI into cyberattacks is significantly enhancing the capabilities of both financially motivated hackers and state-sponsored actors. The most supported hypothesis is that AI is being used to automate and scale phishing and malware attacks, making them more effective and harder to detect. Confidence level: High. Recommended action is to prioritize the development and deployment of AI-driven defensive measures and enhance intelligence sharing between governments and private organizations.
2. Competing Hypotheses
Hypothesis 1: AI is primarily being used by financially motivated hackers to automate phishing and ransomware attacks, increasing their success rate and financial gain.
Hypothesis 2: State-sponsored actors are leveraging AI to conduct sophisticated cyber-espionage and disruption campaigns, targeting critical infrastructure and geopolitical adversaries.
Using structured analytic techniques, such as Analysis of Competing Hypotheses (ACH), Hypothesis 1 is better supported due to the prevalence of financially motivated attacks and the widespread use of AI in automating phishing campaigns, as reported by Microsoft. However, Hypothesis 2 cannot be dismissed, given the documented activities of state actors like China, Iran, and Russia.
3. Key Assumptions and Red Flags
– Assumption: AI technology is equally accessible to both hackers and defenders, which may not be the case due to resource disparities.
– Red Flag: The report may underrepresent the role of insider threats and human error in facilitating cyber breaches.
– Blind Spot: Potential overreliance on AI for defense without addressing fundamental cybersecurity hygiene and training.
4. Implications and Strategic Risks
The integration of AI in cyberattacks poses significant risks, including the potential for large-scale data breaches, disruption of critical infrastructure, and escalation of geopolitical tensions. Economically, businesses face increased costs for cybersecurity measures and potential losses from ransomware. Psychologically, the threat of AI-driven attacks may erode public trust in digital systems.
5. Recommendations and Outlook
- Develop and deploy AI-driven cybersecurity tools to detect and mitigate AI-enhanced attacks.
- Enhance collaboration and intelligence sharing between governments and private sectors.
- Scenario-based projections:
- Best: Successful deployment of AI defenses reduces attack success rates.
- Worst: AI-driven attacks overwhelm current defenses, leading to significant economic and geopolitical damage.
- Most Likely: A continuous arms race between attackers and defenders, with incremental improvements in defense capabilities.
6. Key Individuals and Entities
– Microsoft (as the source of the report)
– China, Iran, Russia (as state actors involved in cyber activities)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus