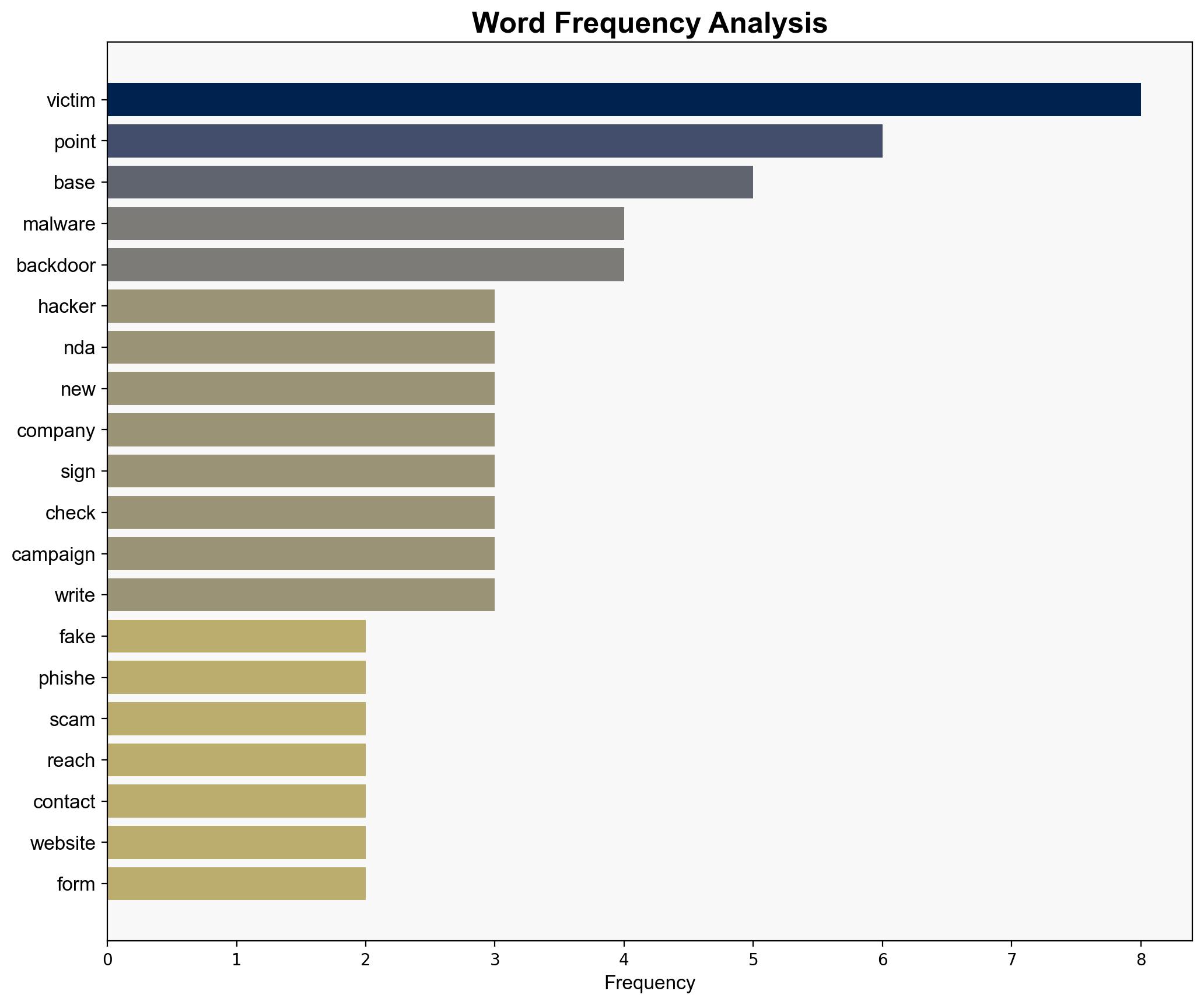
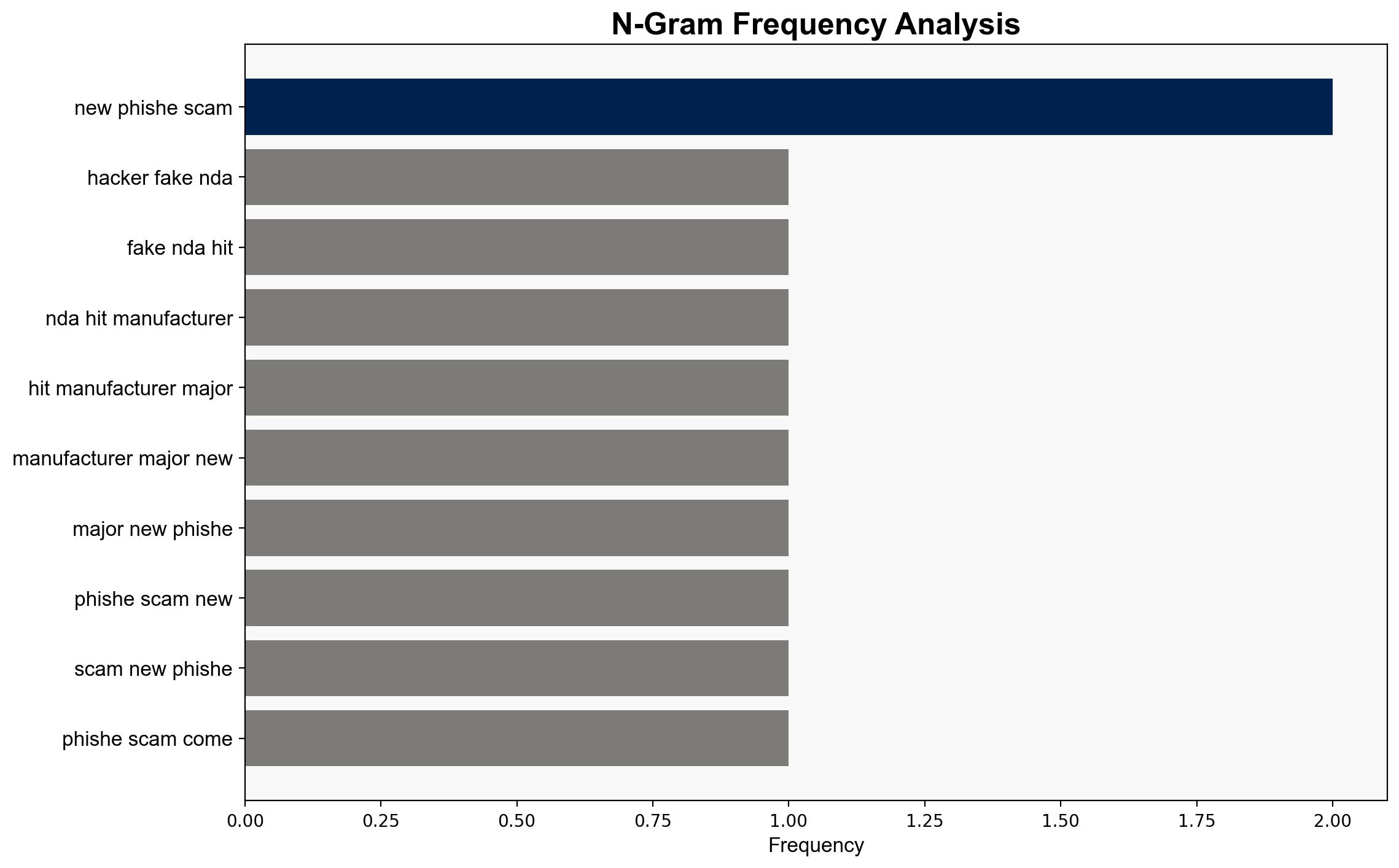
Hackers are using fake NDAs to hit US manufacturers in major new phishing scam – TechRadar
Published on: 2025-08-28
Intelligence Report: Hackers are using fake NDAs to hit US manufacturers in major new phishing scam – TechRadar
1. BLUF (Bottom Line Up Front)
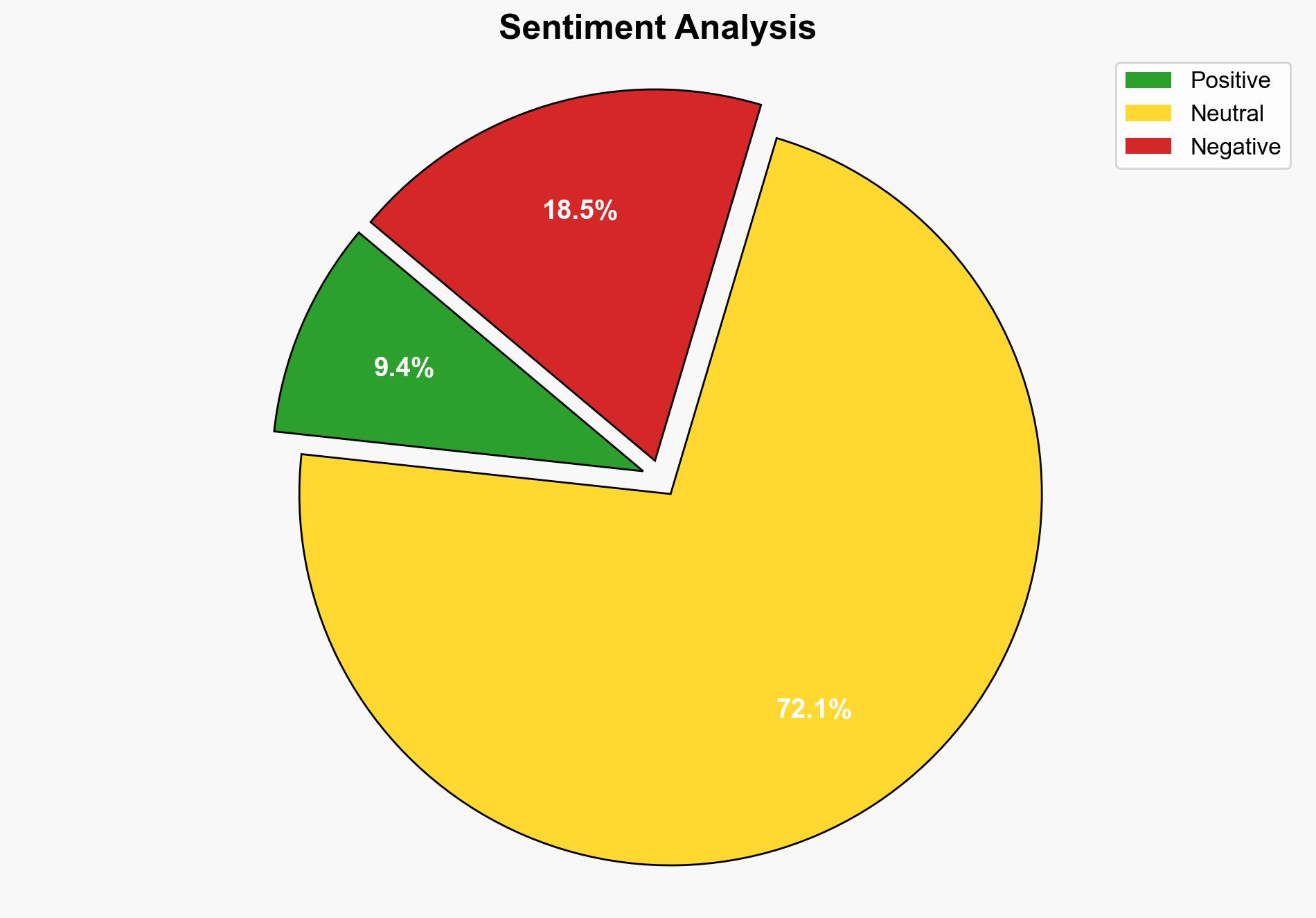
The most supported hypothesis is that a sophisticated cybercriminal group is targeting US manufacturers and other critical industries using fake NDAs to deploy custom malware, aiming to infiltrate supply chains. Confidence level: Moderate. Recommended action: Enhance cybersecurity awareness and training for employees, particularly regarding phishing tactics, and implement advanced email filtering and endpoint protection systems.
2. Competing Hypotheses
Hypothesis 1: A cybercriminal group is using fake NDAs as a novel phishing tactic to deploy malware and gain access to critical supply chains, primarily targeting US manufacturers and related industries.
Hypothesis 2: The phishing campaign is a state-sponsored operation disguised as a cybercriminal activity, aiming to gather intelligence and disrupt operations in critical industries.
3. Key Assumptions and Red Flags
Assumptions:
– The attackers have a high level of technical capability, as evidenced by the use of custom backdoor malware.
– The choice of targets suggests a focus on industries with significant economic and strategic value.
Red Flags:
– Lack of clear attribution to a known threat actor raises questions about the true origin of the campaign.
– The use of dormant domains with legitimate business histories could indicate insider knowledge or advanced reconnaissance.
4. Implications and Strategic Risks
The campaign poses a significant risk to the operational integrity of critical supply chains, potentially leading to economic disruptions. If state-sponsored, it could escalate geopolitical tensions, particularly if linked to strategic competitors. The psychological impact on targeted industries could lead to increased caution and investment in cybersecurity, but also potential overreaction and resource misallocation.
5. Recommendations and Outlook
- Conduct comprehensive cybersecurity audits and implement robust incident response plans.
- Increase collaboration with industry partners and government agencies to share threat intelligence.
- Best-case scenario: Enhanced defenses deter future attacks, and collaboration leads to the identification of the threat actor.
- Worst-case scenario: Successful breaches lead to significant data loss and operational disruptions.
- Most likely scenario: Continued attempts with varying success, prompting ongoing vigilance and adaptation of security measures.
6. Key Individuals and Entities
No specific individuals are mentioned. Entities involved include US manufacturers, cybersecurity firms like Check Point, and potential threat actors operating under the guise of legitimate businesses.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus