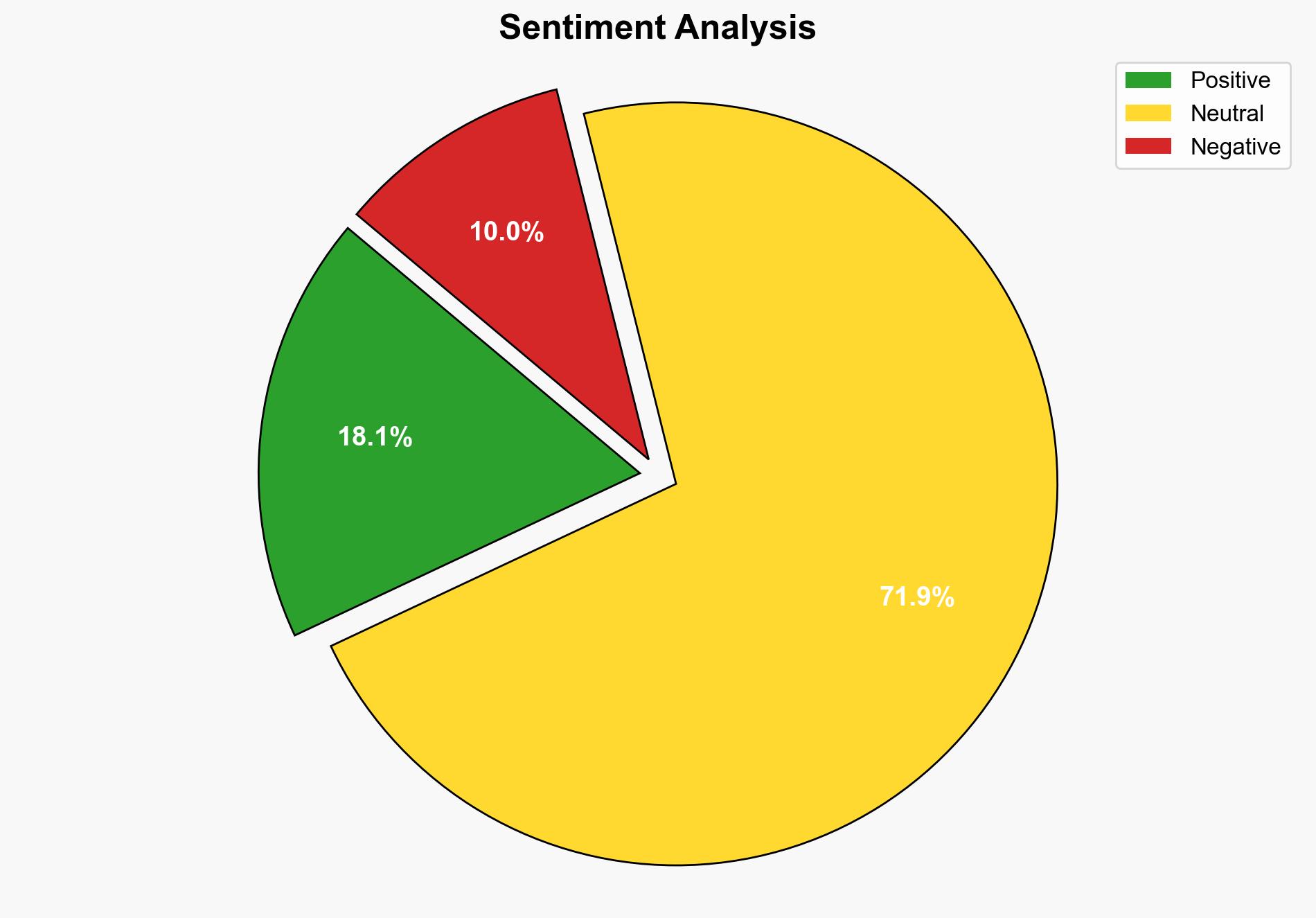
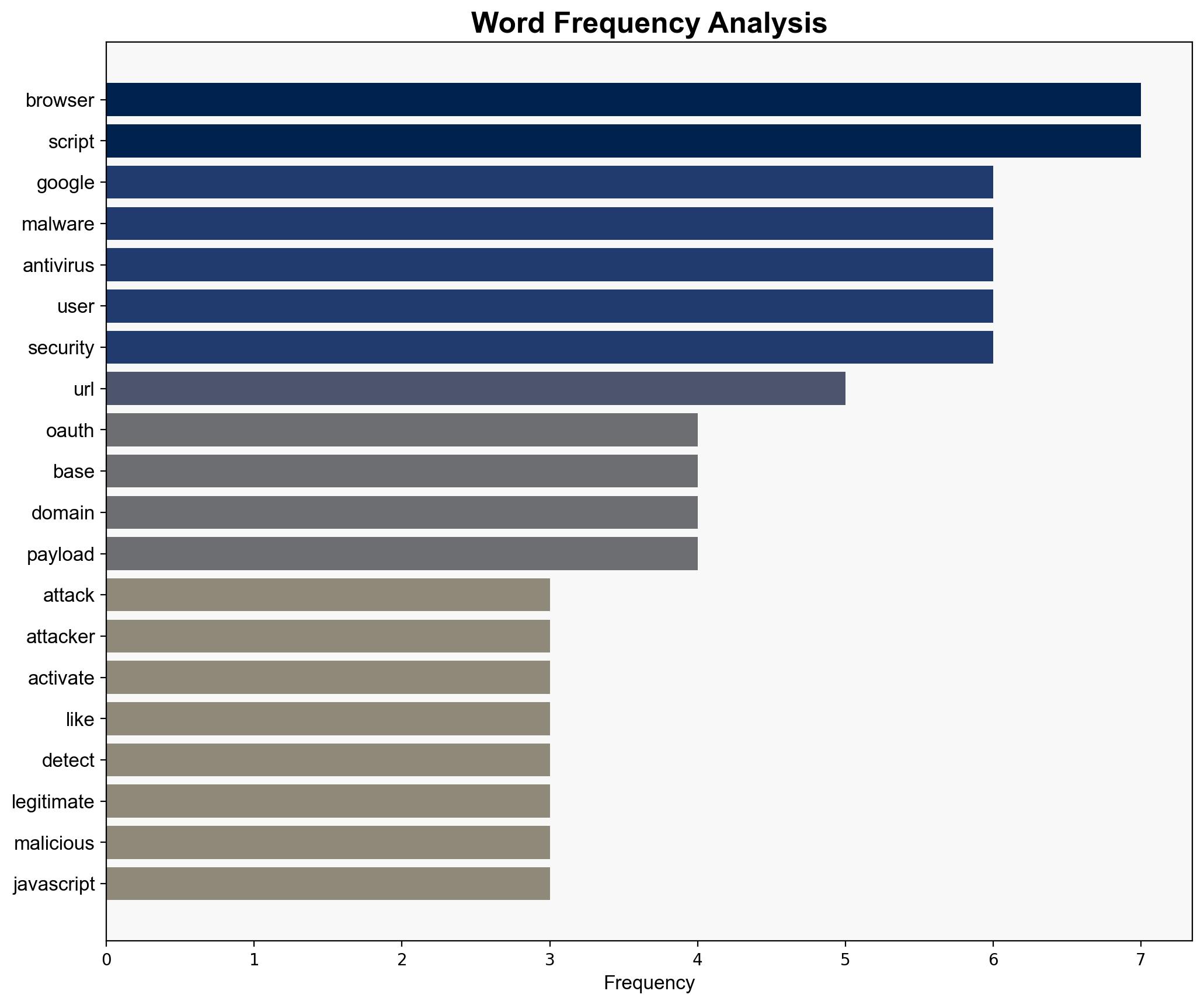
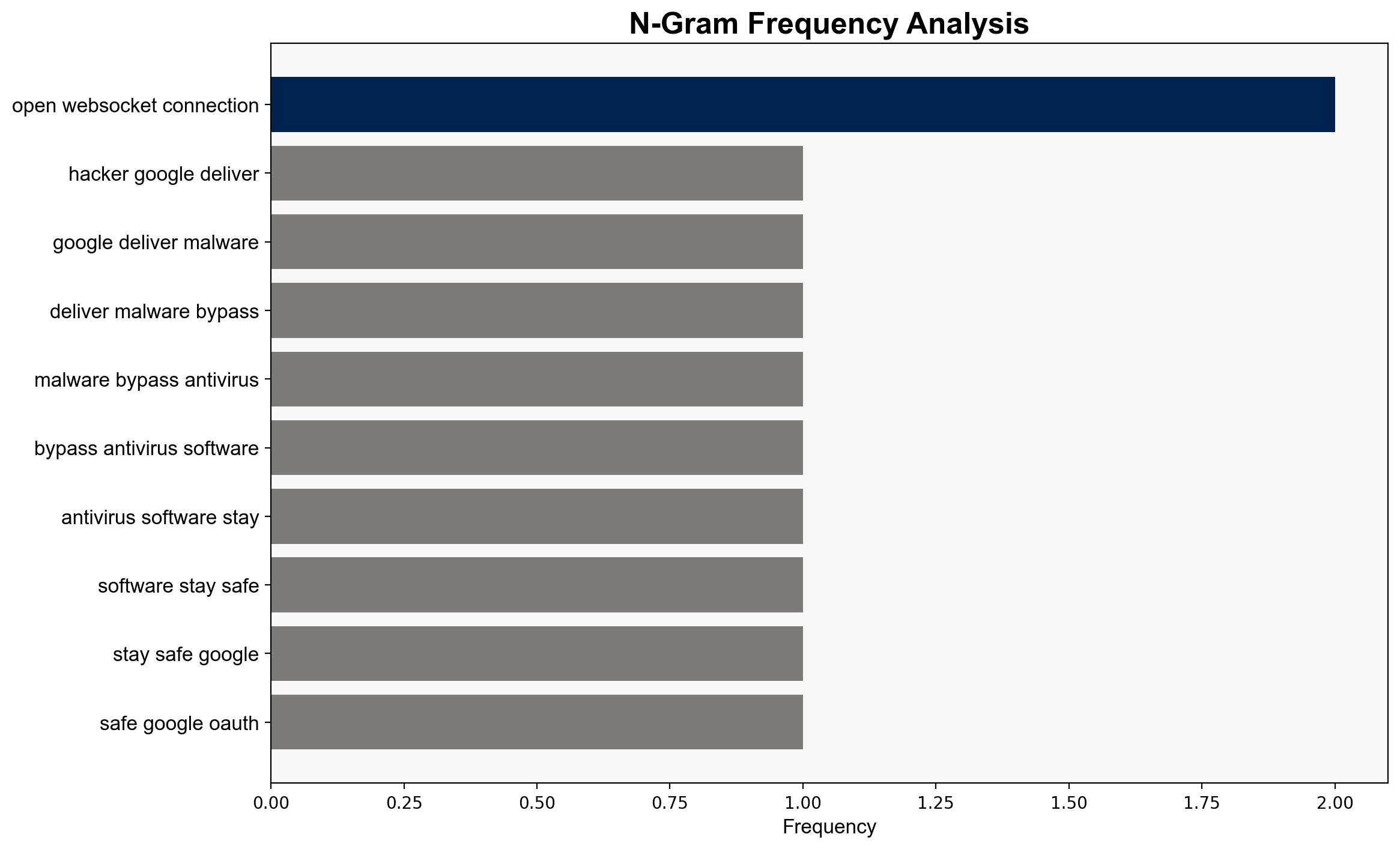
Hackers are using Googlecom to deliver malware by bypassing antivirus software Here’s how to stay safe – TechRadar
Published on: 2025-06-14
Intelligence Report: Hackers are using Googlecom to deliver malware by bypassing antivirus software Here’s how to stay safe – TechRadar
1. BLUF (Bottom Line Up Front)
Cyber adversaries are exploiting Google OAuth links to deliver malware, bypassing traditional antivirus defenses. This method leverages trusted domains to evade detection, posing significant risks to users and organizations. Immediate measures include enhancing browser security protocols and user awareness to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Cyber adversaries are using legitimate Google URLs to deliver malware, exploiting the trust in Google’s domain to bypass antivirus software. This technique involves embedding malicious scripts in compromised e-commerce sites, which are triggered under specific conditions.
Indicators Development
Key indicators include unusual browser behavior, unexpected site redirects, and the presence of obfuscated JavaScript payloads. Monitoring these can aid in early detection of such threats.
Bayesian Scenario Modeling
Probabilistic models suggest an increased likelihood of such attacks due to their high success rate in evading current security measures. The adaptability of these techniques poses a persistent threat.
Narrative Pattern Analysis
The narrative exploits the trust in well-known domains, making it challenging for users to discern malicious activity. This highlights the need for enhanced user education on cybersecurity threats.
3. Implications and Strategic Risks
The exploitation of trusted domains like Google for malware delivery presents systemic vulnerabilities across digital infrastructures. This could lead to widespread data breaches and financial losses, affecting both individual users and enterprises. The reliance on domain reputation for security measures is a critical weakness.
4. Recommendations and Outlook
- Enhance browser security settings and deploy advanced content inspection tools to detect and block malicious scripts.
- Increase user awareness and training on recognizing phishing attempts and suspicious online behaviors.
- Implement scenario-based planning to prepare for potential escalations in attack sophistication.
- Short-term: Strengthen endpoint protection with behavioral analysis capabilities.
- Long-term: Develop and integrate AI-driven threat detection systems to adapt to evolving cyber threats.
5. Key Individuals and Entities
Efosa Udinmwen
6. Thematic Tags
national security threats, cybersecurity, malware, phishing, digital trust exploitation