Hackers exploit revoked EnCase driver to create EDR killer targeting 59 security tools
Published on: 2026-02-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: EDR killer tool uses signed kernel driver from forensic software
1. BLUF (Bottom Line Up Front)
The exploitation of a revoked EnCase kernel driver in an EDR killer tool represents a significant cybersecurity threat, particularly to organizations using Windows systems. This attack vector leverages weaknesses in driver signature enforcement to disable security tools, potentially facilitating ransomware attacks. Moderate confidence is placed in the assessment that such techniques will continue to be exploited due to persistent vulnerabilities and inadequate defenses.
2. Competing Hypotheses
- Hypothesis A: The use of the EnCase kernel driver is primarily opportunistic, exploiting known vulnerabilities in Windows systems to facilitate ransomware attacks. Supporting evidence includes the use of compromised VPN credentials and lack of MFA, which are common tactics in ransomware operations. However, the specific targeting of forensic software drivers suggests a more sophisticated understanding of security tool bypass techniques.
- Hypothesis B: The attack is part of a broader campaign targeting forensic tools to undermine law enforcement capabilities. This hypothesis is less supported due to the lack of direct evidence linking the attack to broader anti-law enforcement activities. The primary focus appears to be on disabling security tools for ransomware deployment.
- Assessment: Hypothesis A is currently better supported due to the alignment with known ransomware tactics and the absence of specific indicators pointing to a targeted campaign against forensic tools. Indicators that could shift this judgment include evidence of similar attacks on other forensic tools or explicit anti-law enforcement motivations.
3. Key Assumptions and Red Flags
- Assumptions: The attack was primarily intended for ransomware deployment; Windows systems remain vulnerable to BYOVD techniques; the attackers have a high level of technical expertise.
- Information Gaps: The identity and motivations of the attackers; the extent of the network breach; whether similar techniques are being used in other attacks.
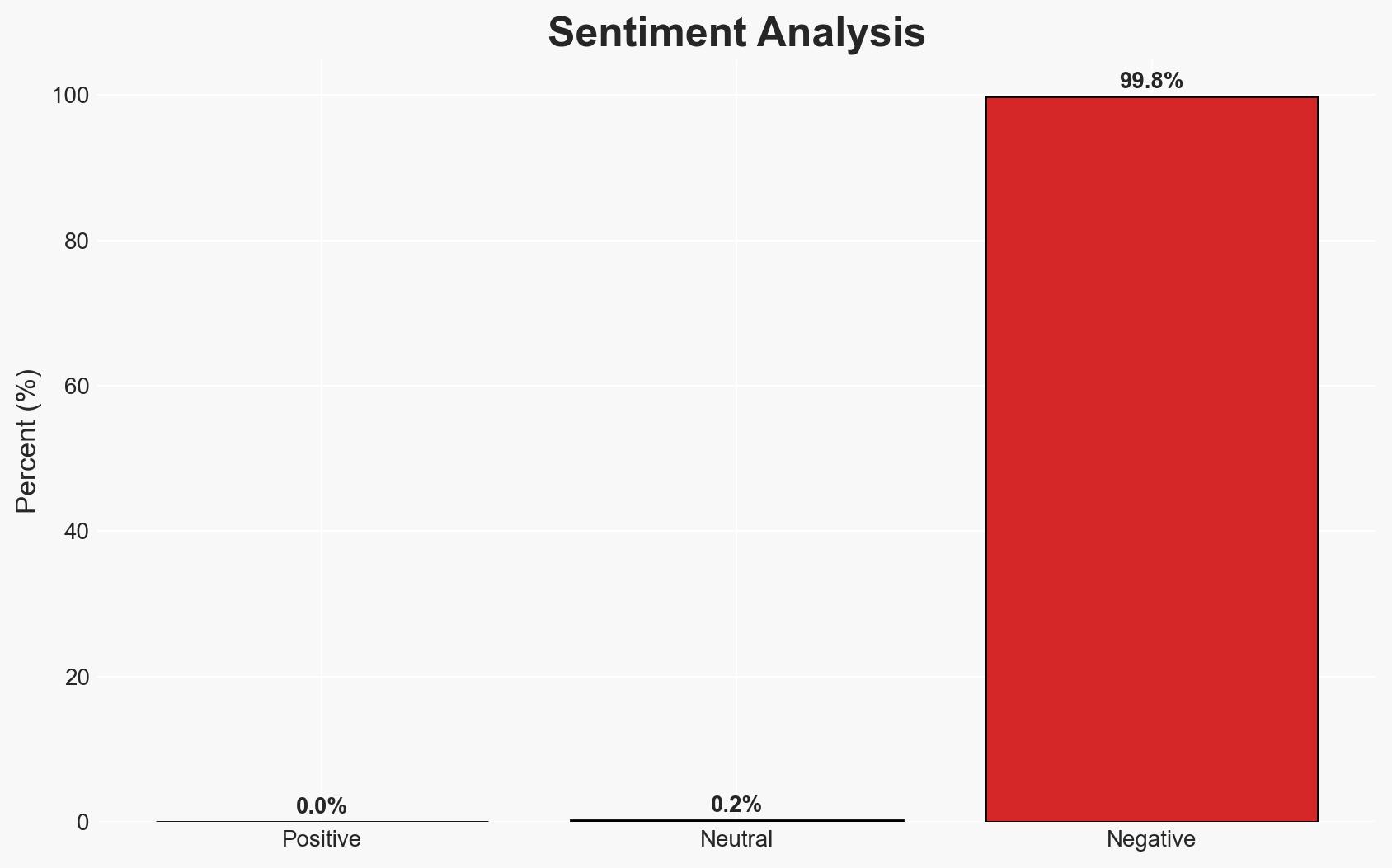
- Bias & Deception Risks: Confirmation bias towards ransomware as the primary motive; potential deception in the attackers’ use of legitimate tools to obscure intent.
4. Implications and Strategic Risks
The continued exploitation of vulnerable drivers poses a persistent threat to cybersecurity, potentially enabling widespread ransomware attacks and undermining trust in digital forensic tools.
- Political / Geopolitical: Escalation of cyber tensions if linked to state-sponsored actors or if critical infrastructure is targeted.
- Security / Counter-Terrorism: Increased operational challenges for law enforcement in digital investigations; potential for heightened ransomware activity.
- Cyber / Information Space: Reinforcement of the need for robust cybersecurity measures and the development of more effective driver signature enforcement mechanisms.
- Economic / Social: Potential economic impact from ransomware disruptions; increased costs for organizations to enhance cybersecurity defenses.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement MFA for all remote access points; conduct thorough network audits to identify and patch vulnerabilities; enhance monitoring for BYOVD techniques.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing; invest in advanced endpoint protection solutions; advocate for improved driver signature enforcement policies.
- Scenario Outlook:
- Best Case: Improved defenses reduce the effectiveness of BYOVD attacks, leading to a decline in ransomware incidents.
- Worst Case: Proliferation of similar attacks targeting critical infrastructure, resulting in significant economic and operational disruptions.
- Most Likely: Continued exploitation of vulnerable drivers with periodic high-profile ransomware incidents.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, BYOVD, digital forensics, Windows vulnerabilities, endpoint protection, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us