Hackers Exploit WSUS Flaw to Spread Skuld Stealer Despite Microsoft Patch – HackRead
Published on: 2025-10-31
Intelligence Report: Hackers Exploit WSUS Flaw to Spread Skuld Stealer Despite Microsoft Patch – HackRead
1. BLUF (Bottom Line Up Front)
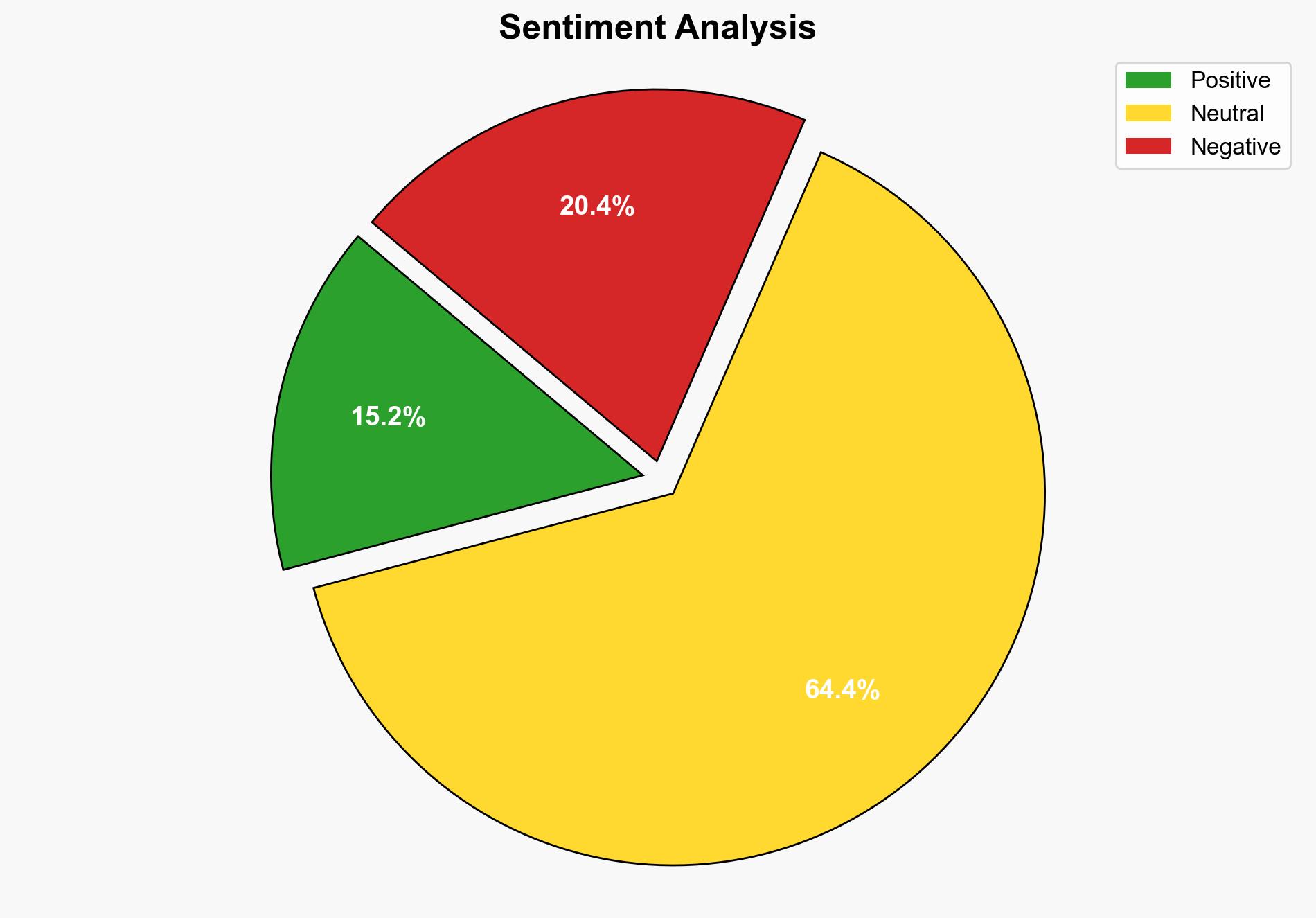
The exploitation of a WSUS vulnerability by cybercriminals to deploy the Skuld Stealer malware indicates a significant threat to corporate networks, despite Microsoft’s patch efforts. The most supported hypothesis is that cybercriminals are leveraging the WSUS flaw to bypass traditional security measures and maintain persistence within enterprise environments. Confidence level: High. Recommended action: Immediate review and reinforcement of WSUS configurations and network monitoring protocols.
2. Competing Hypotheses
1. **Hypothesis A**: Cybercriminals are exploiting the WSUS vulnerability to deploy Skuld Stealer malware, aiming to maintain persistence and extract sensitive data from corporate networks.
2. **Hypothesis B**: The WSUS vulnerability is being used as a decoy, with the primary objective being to test and refine cyberattack methodologies for future, more significant operations.
Structured Analytic Technique: Using Analysis of Competing Hypotheses (ACH), Hypothesis A is better supported due to direct evidence of malware deployment and data theft activities, as reported by Darktrace. Hypothesis B lacks substantial evidence and is speculative, relying on the assumption of future intentions without current indicators.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the WSUS vulnerability is the primary vector for the Skuld Stealer deployment. Another assumption is that the patch provided by Microsoft is insufficient, as indicated by continued exploitation.
– **Red Flags**: The rapid exploitation post-patch suggests potential insider knowledge or advanced reconnaissance capabilities. The lack of detailed information on the attackers raises concerns about attribution and intent.
– **Blind Spots**: The report does not address the potential for other vulnerabilities being exploited concurrently or the full scope of affected sectors beyond those mentioned.
4. Implications and Strategic Risks
The exploitation of WSUS vulnerabilities poses a significant risk to corporate and potentially governmental networks, given WSUS’s role in centralized update management. The persistence of such threats could lead to widespread data breaches, financial losses, and erosion of trust in cybersecurity measures. The potential for cascading threats exists if attackers leverage compromised systems to launch further attacks or exfiltrate sensitive data.
5. Recommendations and Outlook
- **Mitigation Actions**: Conduct a comprehensive audit of WSUS configurations and apply additional security measures, such as network segmentation and enhanced monitoring of outbound connections.
- **Scenario-Based Projections**:
– **Best Case**: Rapid identification and patching of vulnerabilities lead to minimal data loss and restored trust in cybersecurity protocols.
– **Worst Case**: Continued exploitation results in significant data breaches across multiple sectors, leading to economic and reputational damage.
– **Most Likely**: Ongoing exploitation with periodic data theft incidents, prompting gradual improvements in cybersecurity practices.
6. Key Individuals and Entities
– **Entities**: Darktrace, Microsoft, Cybersecurity and Infrastructure Security Agency (CISA).
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus