Hackers hit SAP security bug to send out nasty Linux malware – TechRadar
Published on: 2025-07-30
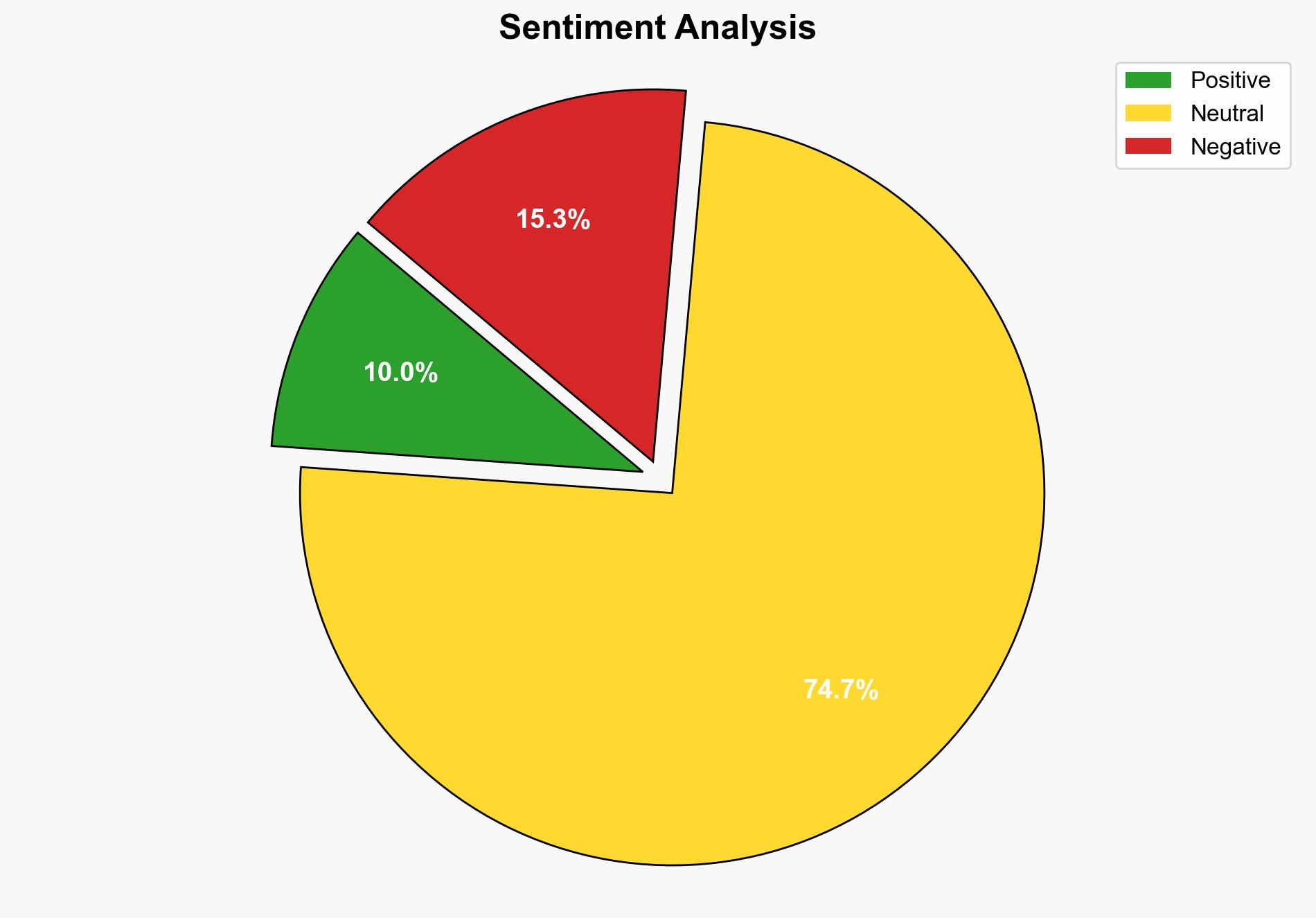
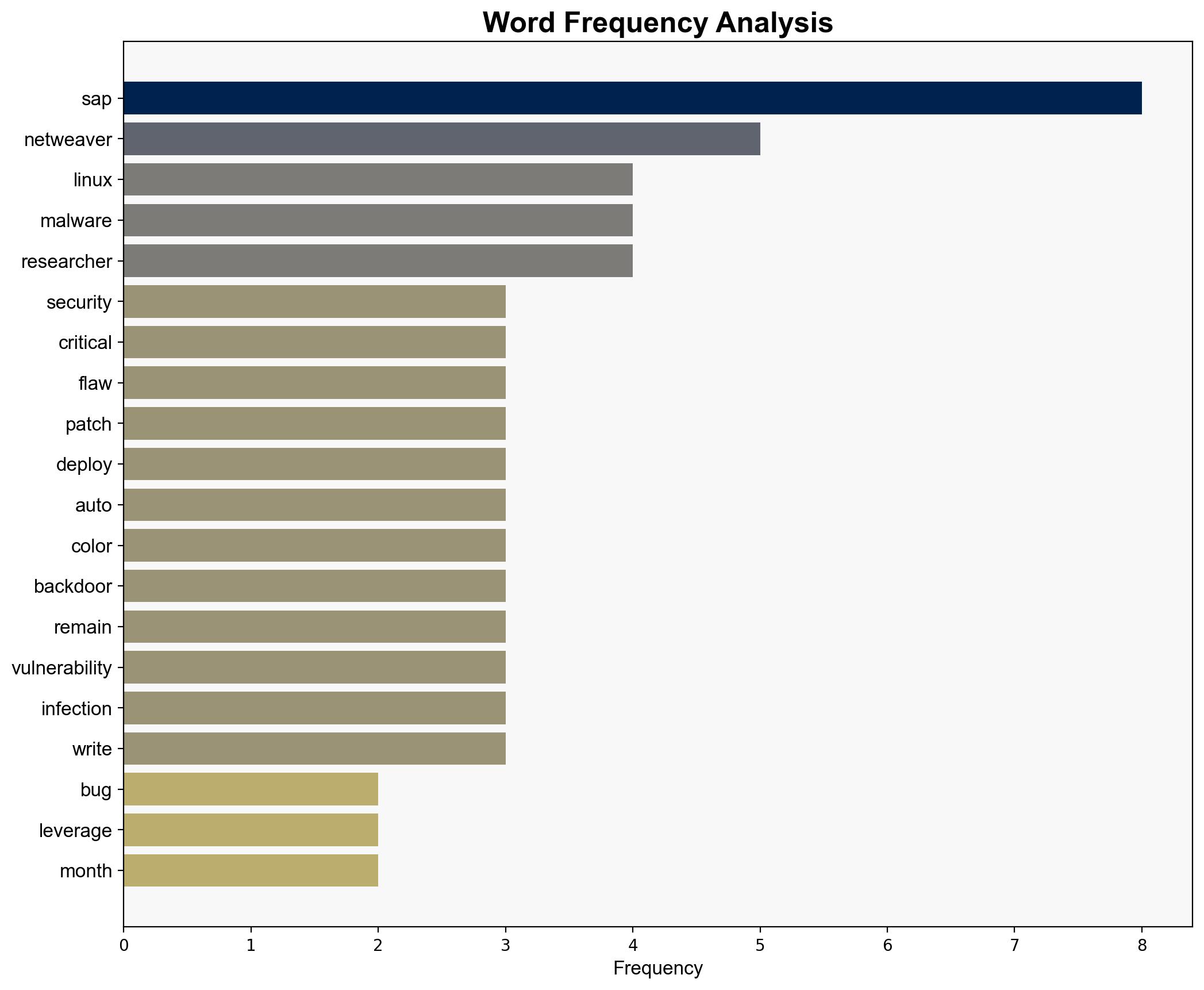
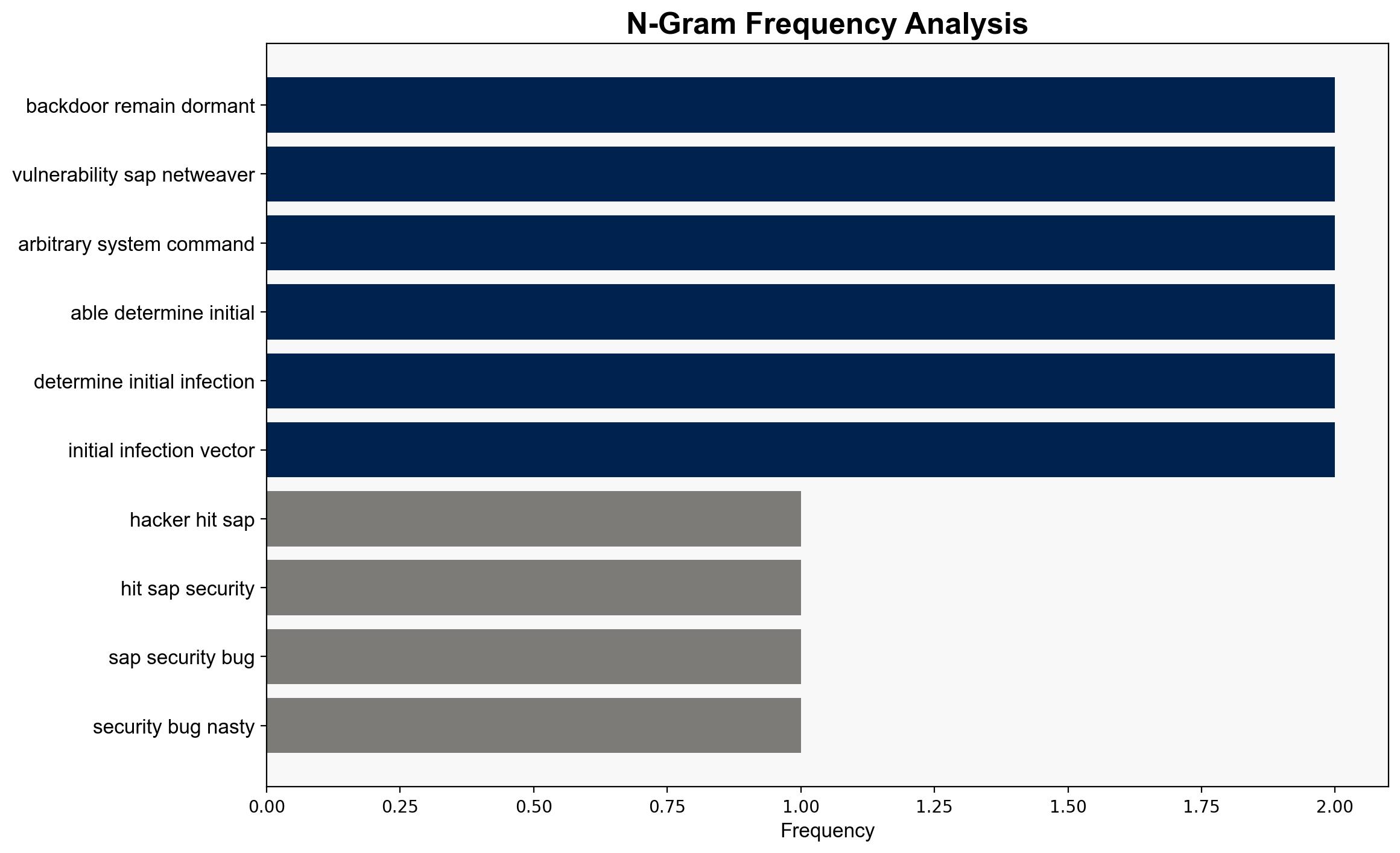
Intelligence Report: Hackers hit SAP security bug to send out nasty Linux malware – TechRadar
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that a state-sponsored group, potentially from China, is exploiting a critical vulnerability in SAP NetWeaver to deploy Linux malware for strategic cyber espionage. Confidence level: Moderate. Immediate action is recommended to patch vulnerabilities and enhance monitoring of SAP systems to mitigate potential threats.
2. Competing Hypotheses
1. **State-Sponsored Cyber Espionage**: The exploitation of the SAP NetWeaver vulnerability is part of a coordinated effort by a state-sponsored group, likely Chinese, to conduct cyber espionage against strategic industries.
2. **Criminal Cyber Exploitation for Financial Gain**: Independent cybercriminals are leveraging the SAP vulnerability to deploy malware aimed at financial theft or ransomware attacks.
Structured Analytic Technique: Using Analysis of Competing Hypotheses (ACH), the state-sponsored hypothesis is better supported due to the involvement of sophisticated malware, the strategic nature of the targets, and the historical context of similar activities by state-sponsored actors.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the malware’s sophistication and target selection are indicative of state-sponsored activities. Another assumption is that the vulnerability was exploited soon after its discovery.
– **Red Flags**: The initial infection vector remains unidentified, raising questions about the completeness of the intelligence. The lack of direct attribution to a specific group introduces uncertainty.
– **Blind Spots**: There is limited information on the full scope of affected entities and the potential for undiscovered vulnerabilities.
4. Implications and Strategic Risks
The exploitation of SAP vulnerabilities poses significant risks to industries relying on SAP systems, potentially leading to data breaches, intellectual property theft, and operational disruptions. If state-sponsored, this could escalate geopolitical tensions, especially if linked to critical infrastructure or defense sectors. The economic impact could be substantial if industries face prolonged disruptions or data loss.
5. Recommendations and Outlook
- **Immediate Actions**: Urgently apply SAP patches and enhance system monitoring for unusual activities.
- **Long-term Strategy**: Develop a comprehensive cybersecurity framework focusing on critical software vulnerabilities and establish partnerships for intelligence sharing.
- **Scenario Projections**:
- **Best Case**: Vulnerabilities are patched promptly, and no further exploitation occurs.
- **Worst Case**: Widespread exploitation leads to significant economic and operational damage.
- **Most Likely**: Continued attempts to exploit similar vulnerabilities, with sporadic success.
6. Key Individuals and Entities
– Palo Alto Networks: Security researchers who discovered the malware.
– Darktrace: Cybersecurity experts investigating the incident.
– Sead: Journalist reporting on the incident.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus