Half a Million Stolen FTSE 100 Credentials Found on Criminal Sites – Infosecurity Magazine
Published on: 2025-11-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
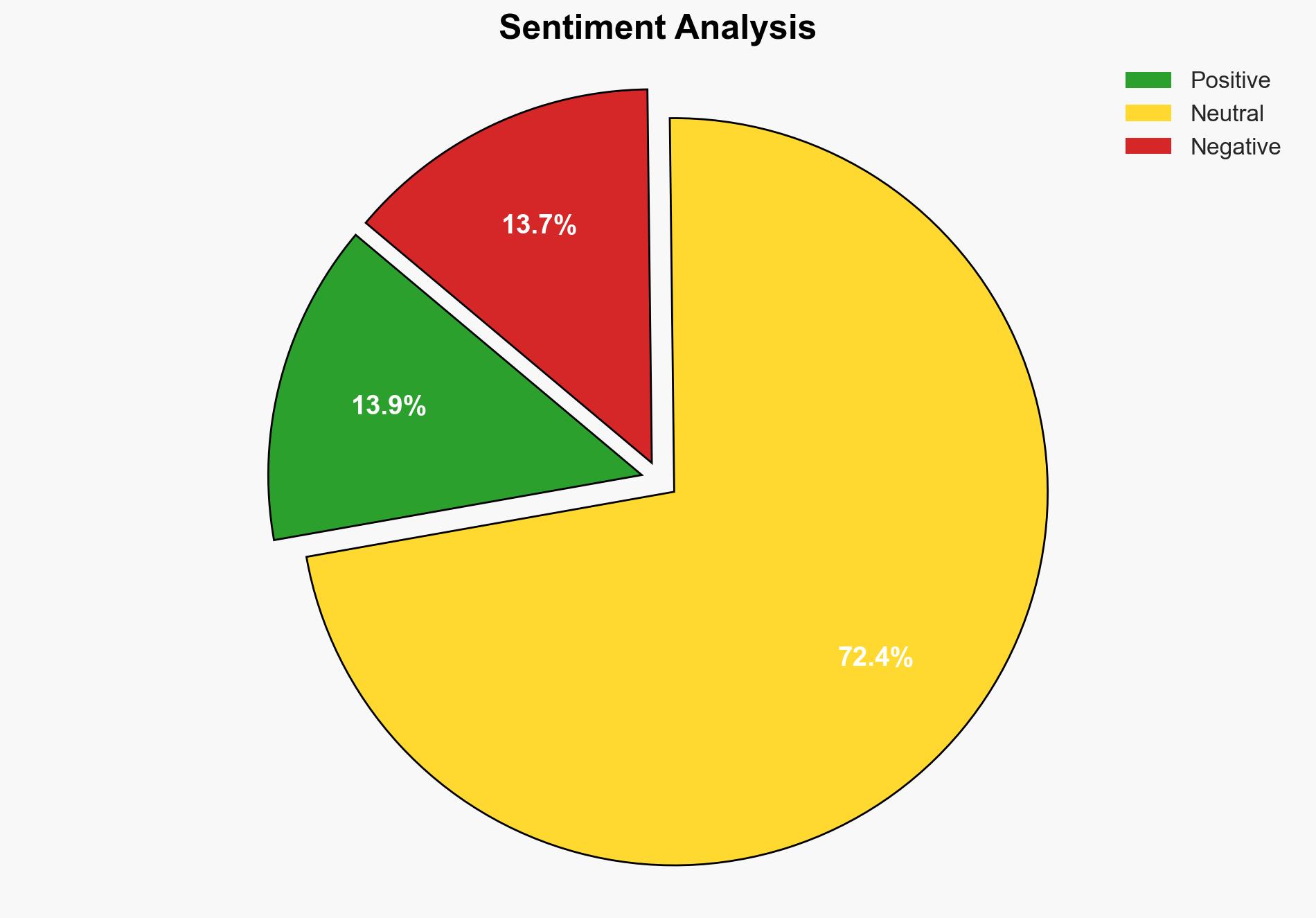
The most supported hypothesis is that the proliferation of stolen credentials from FTSE 100 companies on criminal sites is primarily due to poor password hygiene and inadequate cybersecurity practices among employees. This poses a significant risk of cyber breaches, necessitating immediate implementation of enhanced security measures such as Multi-Factor Authentication (MFA) and employee education. Confidence Level: Moderate.
2. Competing Hypotheses
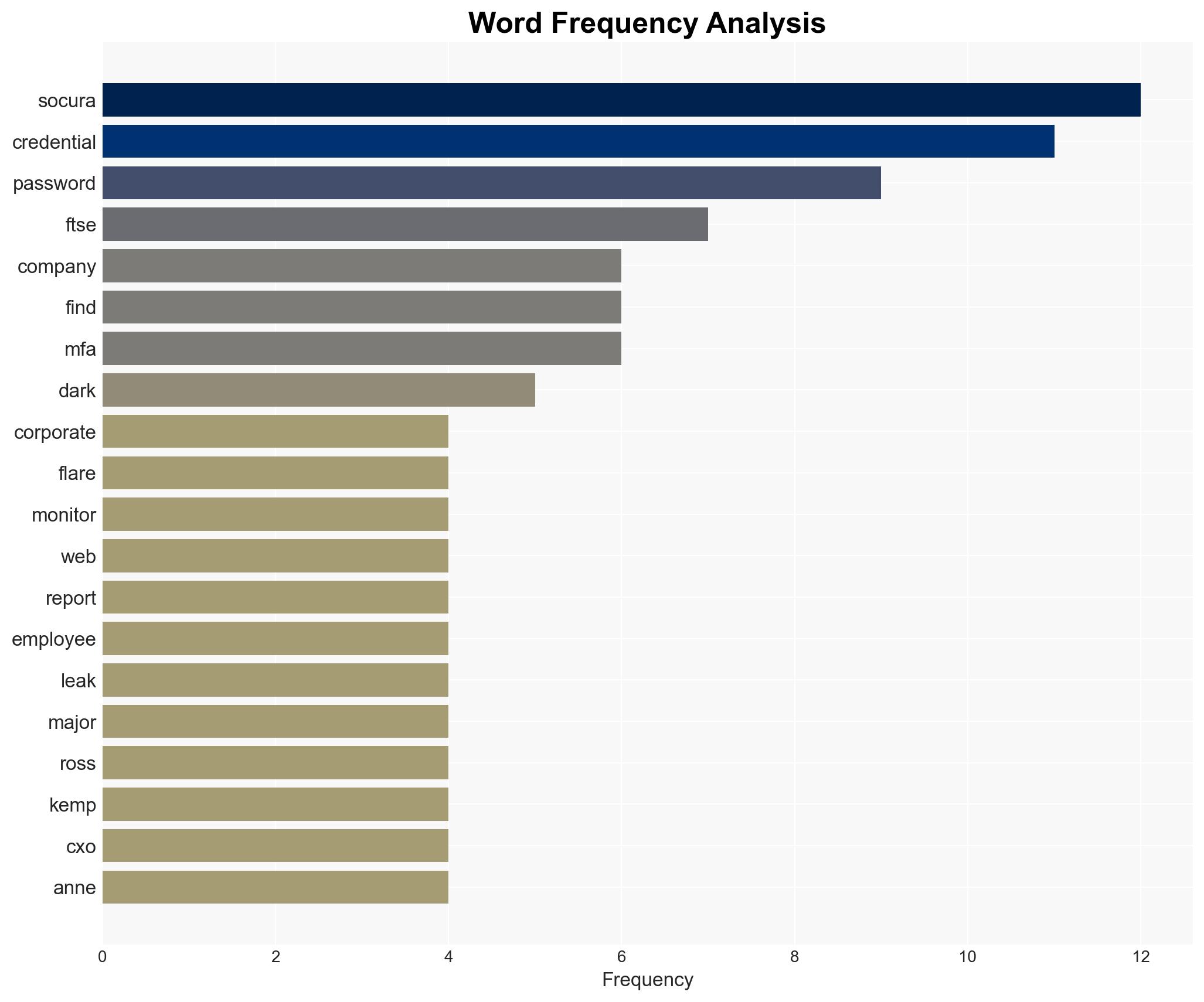
Hypothesis 1: The widespread availability of FTSE 100 credentials on criminal sites is primarily due to poor password hygiene and lack of robust cybersecurity practices among employees.
Hypothesis 2: The credentials were obtained through sophisticated cyber-attacks targeting FTSE 100 companies, indicating a coordinated effort by cybercriminals to exploit high-value targets.
Hypothesis 1 is more likely due to the evidence of poor password practices and the opportunistic nature of cybercriminals exploiting easily accessible credentials. Hypothesis 2 is less supported as there is no direct evidence of coordinated attacks specifically targeting these companies.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the credentials were leaked primarily due to employee negligence and not through direct breaches of company systems. It is also assumed that the reported figures accurately represent the scale of the issue.
Red Flags: The lack of specific details on how credentials were obtained raises questions about the completeness of the report. The potential for deception exists if the data was manipulated to exaggerate the threat.
4. Implications and Strategic Risks
The exposure of credentials could lead to significant cyber breaches, resulting in financial losses, reputational damage, and regulatory penalties for affected companies. There is also a risk of cascading effects, where compromised credentials are used to infiltrate supply chains or partner networks, amplifying the impact.
5. Recommendations and Outlook
- Implement Multi-Factor Authentication (MFA) across all systems to enhance security.
- Conduct regular cybersecurity training for employees to improve password hygiene and awareness.
- Establish a robust monitoring system to detect and respond to credential leaks promptly.
- Best Scenario: Companies swiftly adopt recommended security measures, significantly reducing the risk of breaches.
- Worst Scenario: Continued negligence leads to major breaches, causing severe financial and reputational damage.
- Most-likely Scenario: Incremental improvements in security practices reduce, but do not eliminate, the risk of breaches.
6. Key Individuals and Entities
Anne Heim – Socura Threat Intelligence Lead
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us