Haryana DGP visits Al Falah varsity directs officials to probe how ‘vicious’ elements made it their hideout – The Times of India
Published on: 2025-11-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
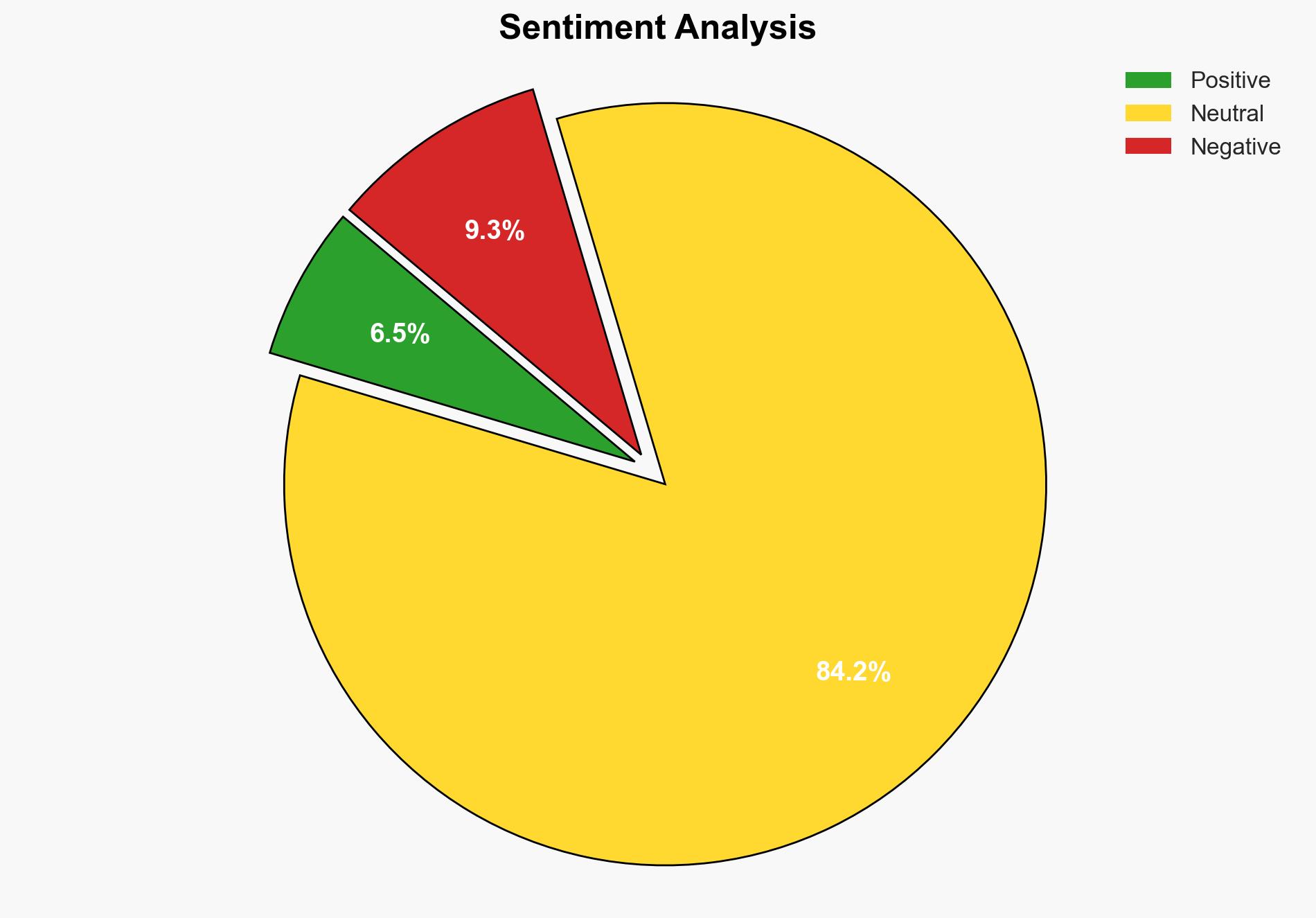
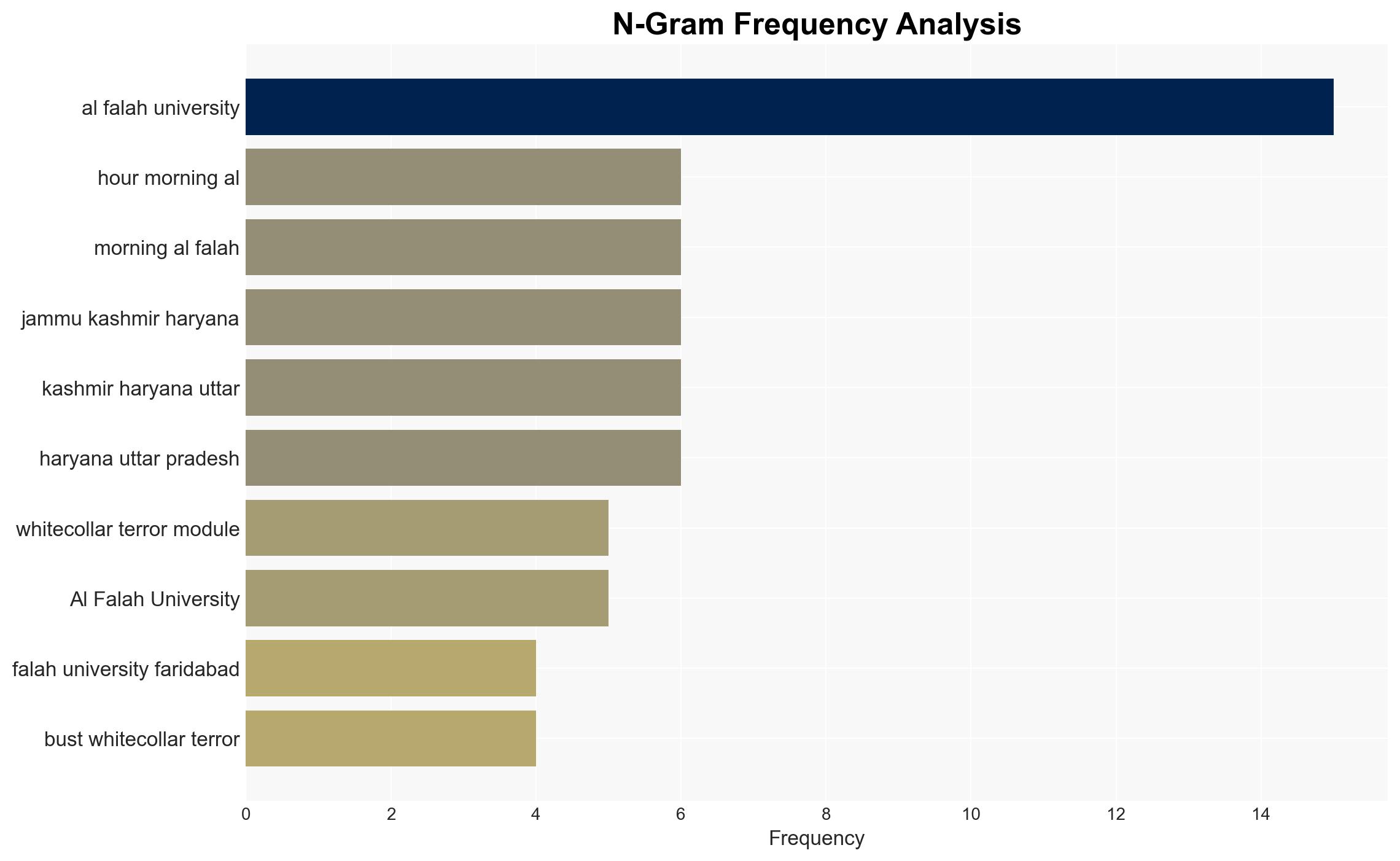
The investigation into Al Falah University as a potential hideout for a white-collar terror module suggests a significant security lapse. The most supported hypothesis is that the university was inadvertently used as a hideout by individuals linked to terror activities due to inadequate security protocols. Confidence level: Moderate. Recommended action includes enhancing security measures at educational institutions and increasing intelligence collaboration between local and central agencies.
2. Competing Hypotheses
Hypothesis 1: Al Falah University was deliberately chosen as a hideout by the terror module due to its strategic location and perceived vulnerabilities in security.
Hypothesis 2: The university was inadvertently used as a hideout by individuals linked to terror activities, exploiting existing security lapses without the institution’s knowledge.
Hypothesis 2 is more likely due to the lack of direct evidence suggesting institutional complicity and the common occurrence of security oversights in educational settings.
3. Key Assumptions and Red Flags
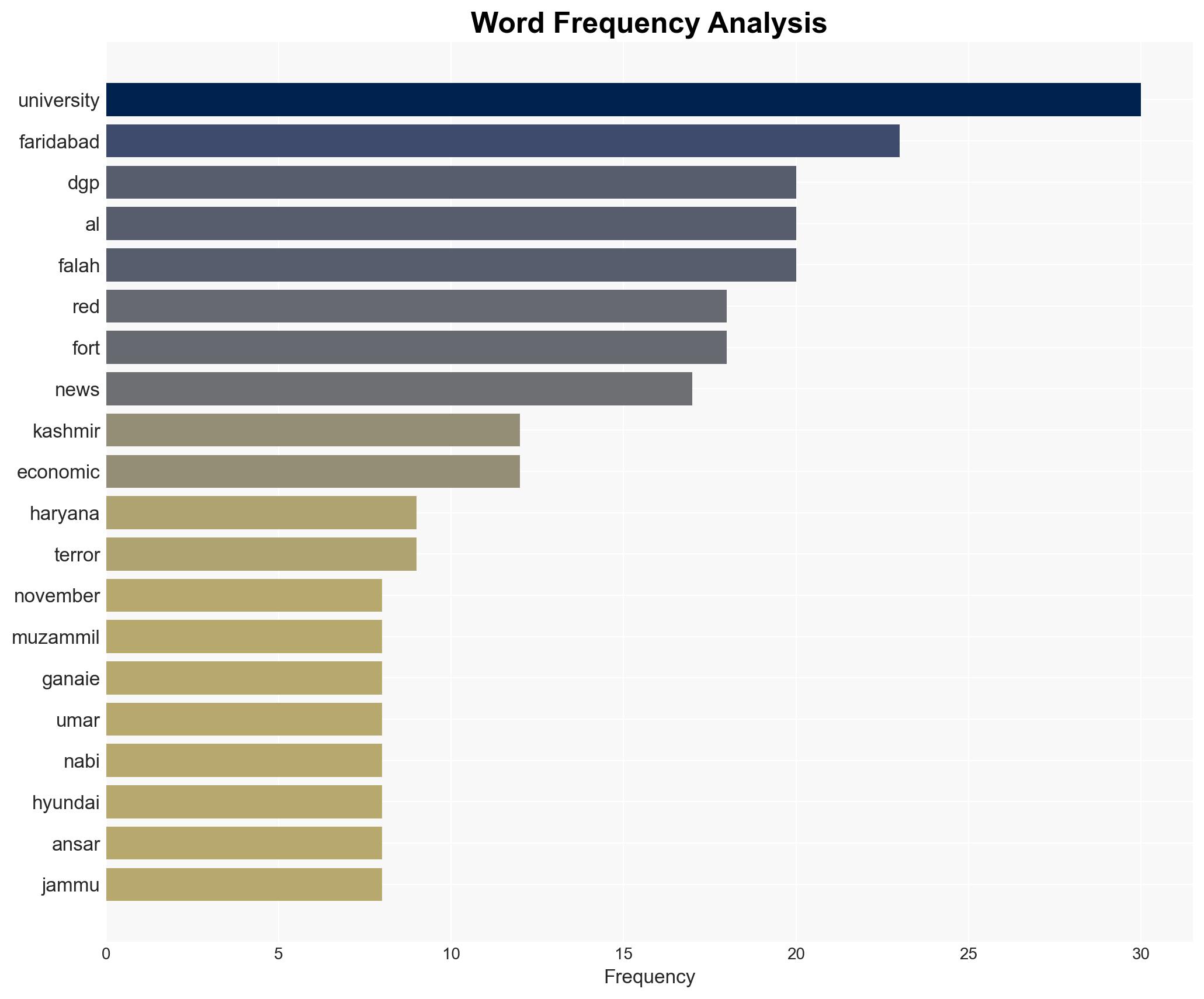
Assumptions include the belief that the university administration was unaware of the activities and that the security lapses were not intentional. Red flags include the presence of significant quantities of ammunition and the involvement of university-affiliated individuals, which could suggest deeper complicity or negligence.
4. Implications and Strategic Risks
Cascading threats include potential reputational damage to educational institutions, increased sectarian tensions, and the risk of similar institutions being exploited. Escalation scenarios involve political backlash, increased scrutiny on educational institutions, and potential retaliatory actions by terror groups.
5. Recommendations and Outlook
- Enhance security protocols at educational institutions, including regular audits and training for staff.
- Strengthen intelligence-sharing mechanisms between local and central agencies.
- Best scenario: Successful mitigation of security lapses and prevention of future incidents.
- Worst scenario: Further exploitation of educational institutions by terror modules, leading to increased attacks.
- Most-likely scenario: Incremental improvements in security with occasional lapses due to resource constraints.
6. Key Individuals and Entities
Dr. Muzammil Ganaie, Dr. Shaheen Sayeed, Dr. Umar Nabi, and the Haryana DGP Singh are central figures in the investigation. Their roles in the probe and potential connections to the terror module are critical to understanding the situation.
7. Thematic Tags
Cybersecurity, Counterterrorism, Educational Security, Intelligence Collaboration
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us