Healthcare sector faces ongoing ransomware threats despite decrease in average ransom amounts, report reveals.
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Ransomware pressure on healthcare remains high as ransom demands plunge report says
1. BLUF (Bottom Line Up Front)
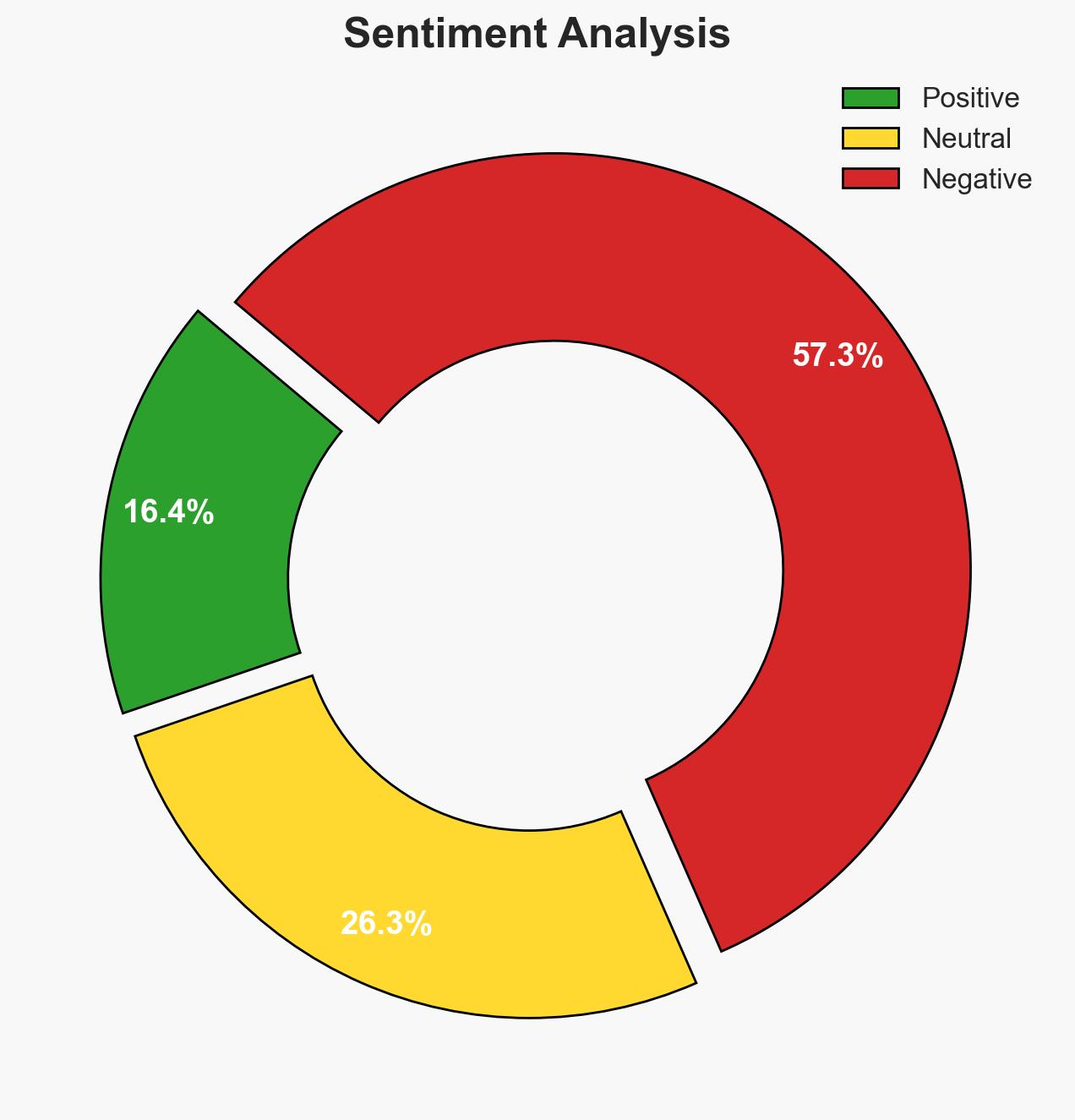
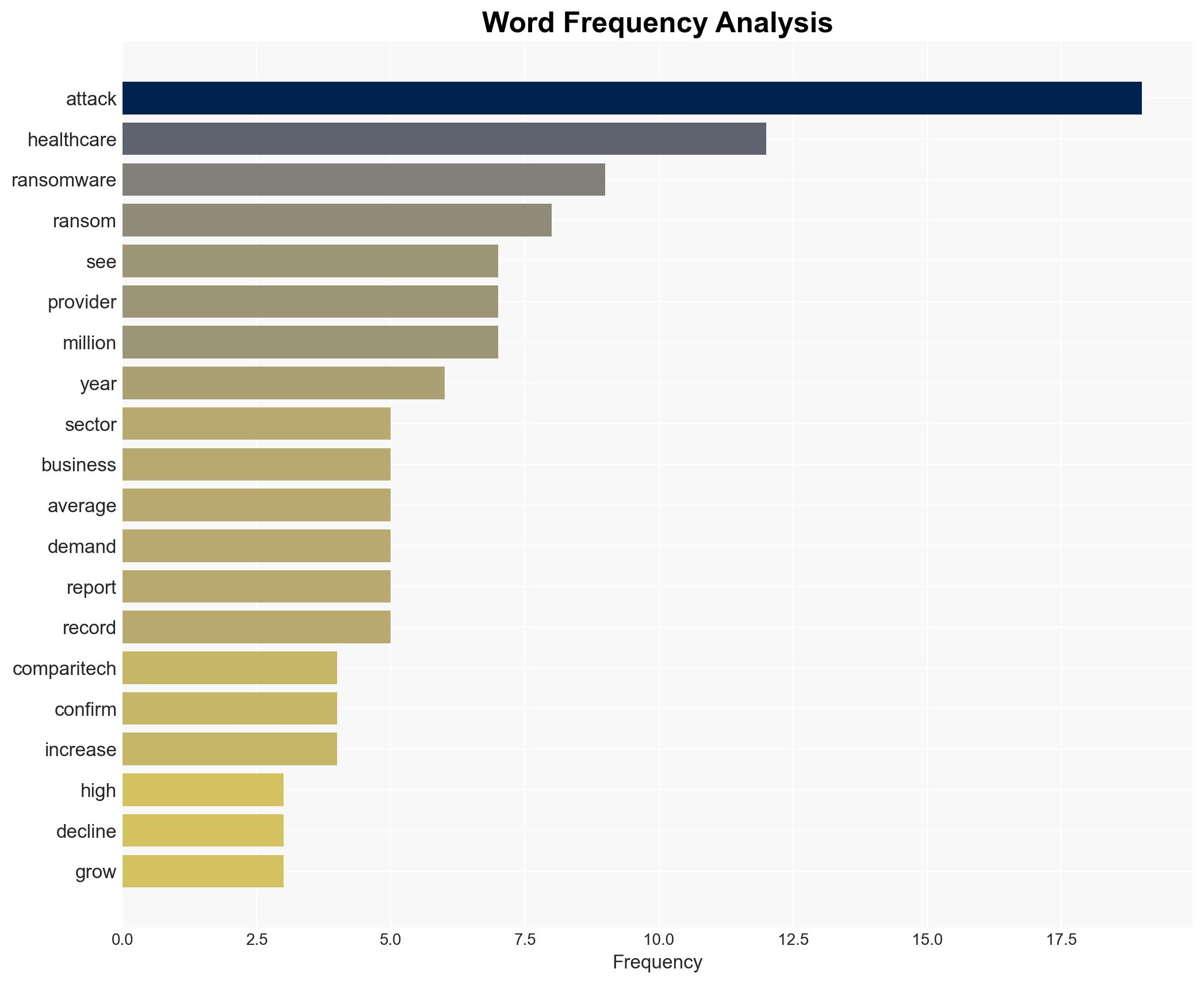
Ransomware attacks on the healthcare sector remain high despite a significant drop in ransom demands, indicating a shift in threat actor strategies. The U.S. and several other developed nations are most affected, with healthcare providers and related businesses experiencing substantial data breaches. The overall confidence level in this assessment is moderate due to potential underreporting and emerging disclosures.
2. Competing Hypotheses
- Hypothesis A: The decline in ransom demands is due to increased resistance from healthcare organizations to pay ransoms, leading threat actors to lower demands to increase the likelihood of payment. Supporting evidence includes the significant drop in average ransom demands and the low number of confirmed ransom payments. Key uncertainties include the actual number of undisclosed payments.
- Hypothesis B: The decrease in ransom demands is primarily driven by the rise of ransomware-as-a-service and AI-assisted attacks, which allow for more efficient operations and quicker, smaller payouts. Supporting evidence includes the report’s attribution of falling demands to these technological advancements. Contradicting evidence is limited but includes the possibility of strategic deception by threat actors.
- Assessment: Hypothesis B is currently better supported due to the technological trends observed and the scalability of operations enabled by ransomware-as-a-service. Indicators that could shift this judgment include a significant increase in reported ransom payments or new evidence of strategic shifts in threat actor behavior.
3. Key Assumptions and Red Flags
- Assumptions: Healthcare organizations are increasingly resistant to paying ransoms; ransomware-as-a-service is becoming more prevalent; data breach disclosures are incomplete.
- Information Gaps: Comprehensive data on unreported ransomware payments and the full extent of data breaches remain unknown.
- Bias & Deception Risks: Potential bias in reporting due to reliance on disclosed incidents; threat actors may be manipulating ransom demands to mislead analysts.
4. Implications and Strategic Risks
The sustained pressure from ransomware attacks on the healthcare sector could lead to increased regulatory scrutiny and investment in cybersecurity. The evolving threat landscape may drive further innovation in both offensive and defensive cyber capabilities.
- Political / Geopolitical: Increased international cooperation on cybersecurity could emerge, potentially leading to new treaties or agreements.
- Security / Counter-Terrorism: Enhanced security measures may be implemented, affecting the operational environment for healthcare providers.
- Cyber / Information Space: The rise of ransomware-as-a-service could lead to more sophisticated and frequent attacks, necessitating advanced defensive strategies.
- Economic / Social: Continued attacks could strain healthcare resources and erode public trust, impacting social cohesion and economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Strengthen monitoring of ransomware activity, enhance incident response protocols, and increase awareness among healthcare staff.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms, invest in advanced threat detection technologies, and conduct regular security audits.
- Scenario Outlook:
- Best: Ransomware threats decrease due to improved defenses and international cooperation.
- Worst: Attacks increase in sophistication and frequency, overwhelming healthcare systems.
- Most-Likely: Continued pressure with gradual improvements in defenses and threat actor adaptation.
6. Key Individuals and Entities
- Qilin ransomware group
- INC ransomware group
- SafePay ransomware group
- Sinobi ransomware group
- Medusa ransomware group
- Akira ransomware group
- KillSec ransomware group
- Clop ransomware group
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, ransomware, healthcare cybersecurity, data breaches, ransomware-as-a-service, cyber threats, artificial intelligence, international cooperation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us