High-Severity Vulnerabilities Patched in VMware Aria Operations NSX vCenter – Securityweek.com
Published on: 2025-09-30
Intelligence Report: High-Severity Vulnerabilities Patched in VMware Aria Operations NSX vCenter – Securityweek.com
1. BLUF (Bottom Line Up Front)
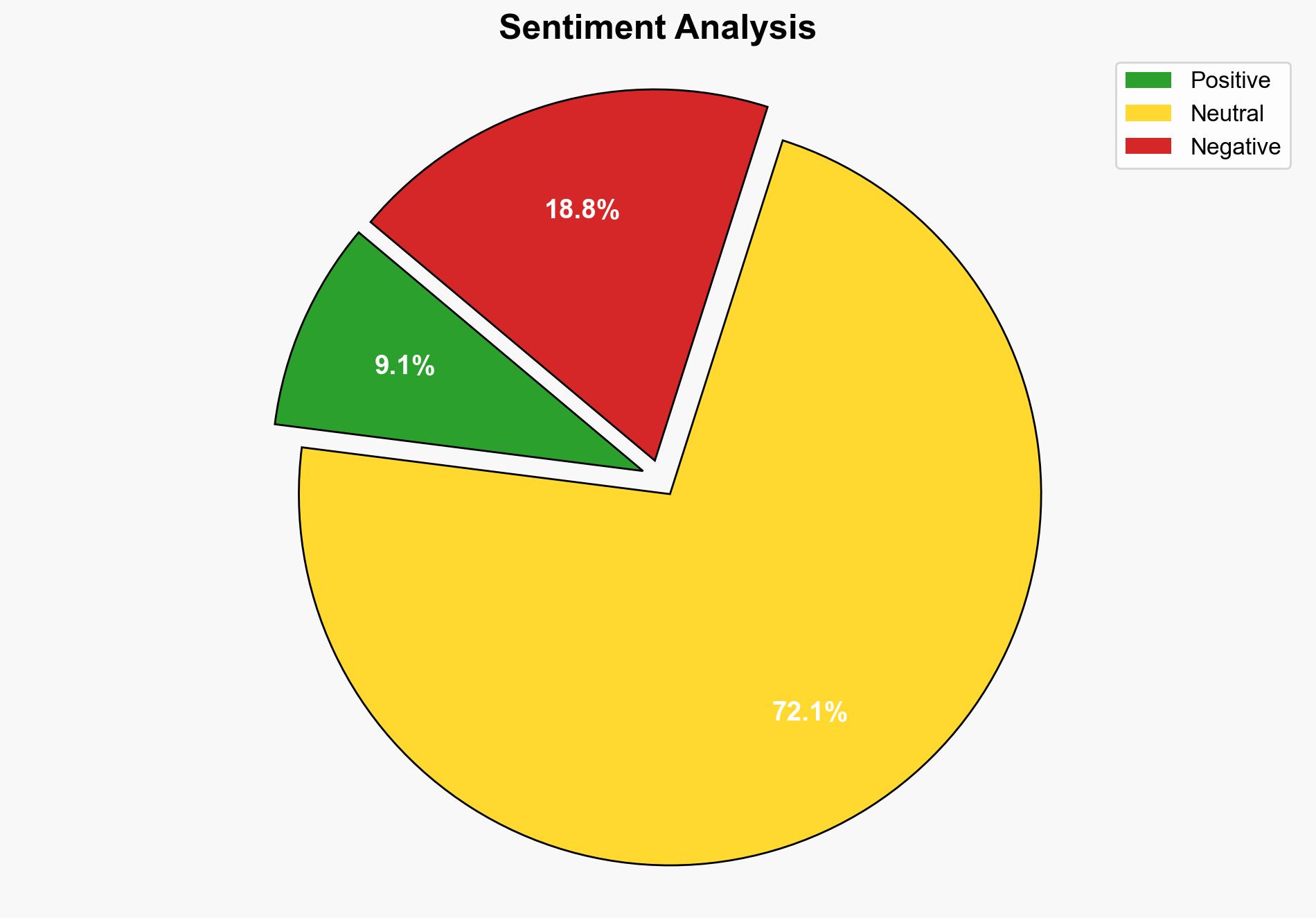
The most supported hypothesis is that the recent patching of high-severity vulnerabilities in VMware products is a proactive measure to mitigate potential cyber threats, rather than a response to known exploitation in the wild. Confidence level: Moderate. Recommended action: Organizations using VMware products should prioritize updating their systems to the latest patched versions to prevent exploitation.
2. Competing Hypotheses
– **Hypothesis 1**: The vulnerabilities were patched as a proactive measure by VMware to prevent potential exploitation, with no current evidence of these vulnerabilities being exploited in the wild.
– **Hypothesis 2**: The vulnerabilities were patched in response to detected exploitation attempts or credible intelligence suggesting imminent exploitation.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the lack of explicit evidence in the source text indicating active exploitation. The emphasis on advising users to update suggests a preventative approach.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that VMware’s disclosure and patching are timely and comprehensive. There is an assumption that users will promptly apply patches.
– **Red Flags**: The source does not provide evidence of exploitation in the wild, which could indicate either a lack of detection or a strategic omission. The absence of specific threat actor mentions may suggest incomplete threat intelligence.
4. Implications and Strategic Risks
Failure to patch these vulnerabilities could lead to significant cyber risks, including unauthorized access and data breaches. If Hypothesis 2 is true, there may be an immediate threat from actors already exploiting these vulnerabilities. The economic impact could be severe for organizations reliant on VMware infrastructure. Geopolitically, widespread exploitation could lead to increased tensions if state actors are involved.
5. Recommendations and Outlook
- Organizations should immediately apply the latest patches to all affected VMware products.
- Conduct a thorough security audit to ensure no prior exploitation has occurred.
- Monitor for any emerging threats or advisories related to these vulnerabilities.
- Scenario-based projections:
- Best Case: All organizations patch promptly, preventing any exploitation.
- Worst Case: Delayed patching leads to widespread exploitation and data breaches.
- Most Likely: Mixed response with some organizations patching promptly while others delay, leading to isolated incidents.
6. Key Individuals and Entities
– VMware
– Broadcom (as the announcing entity)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus