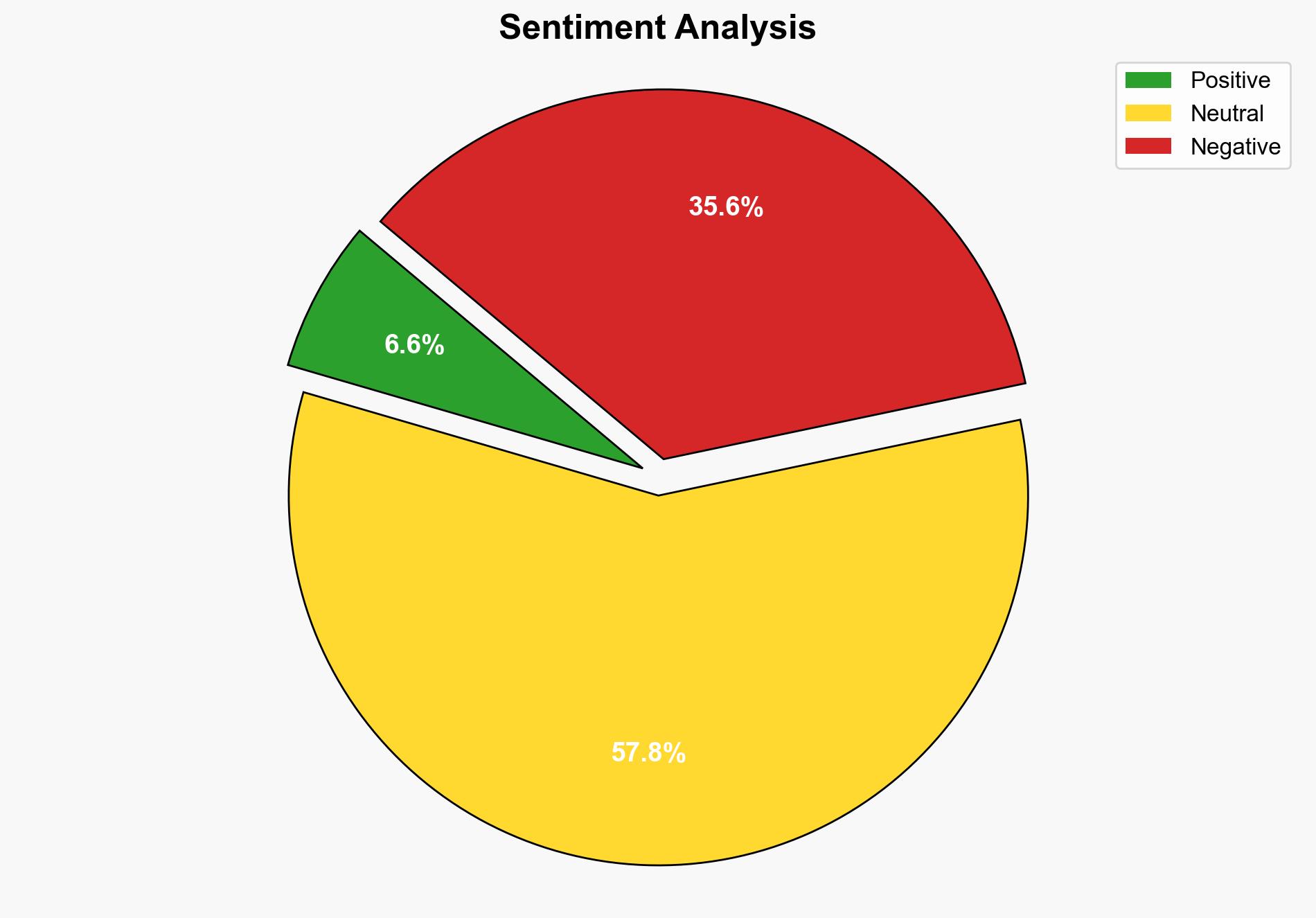
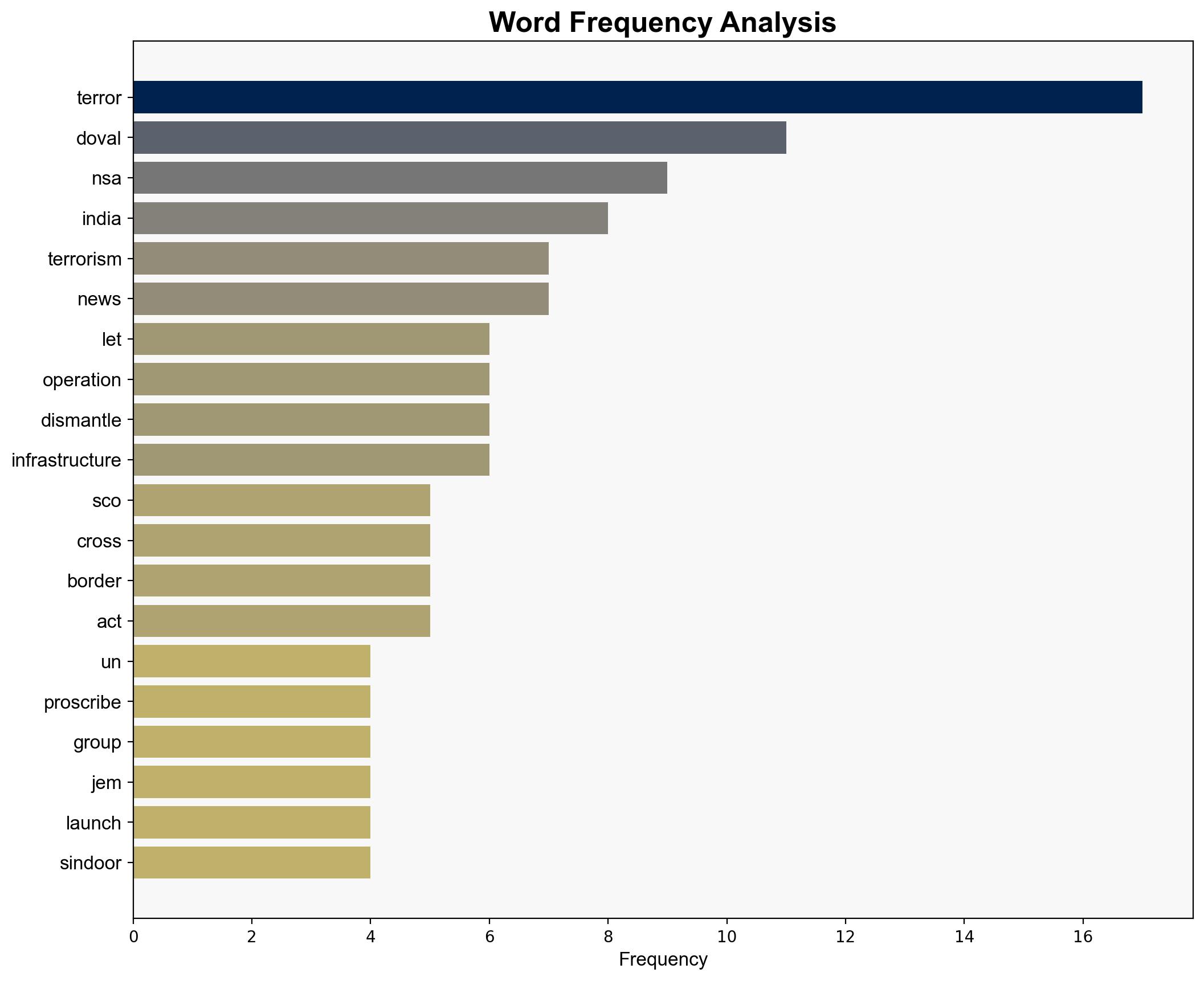
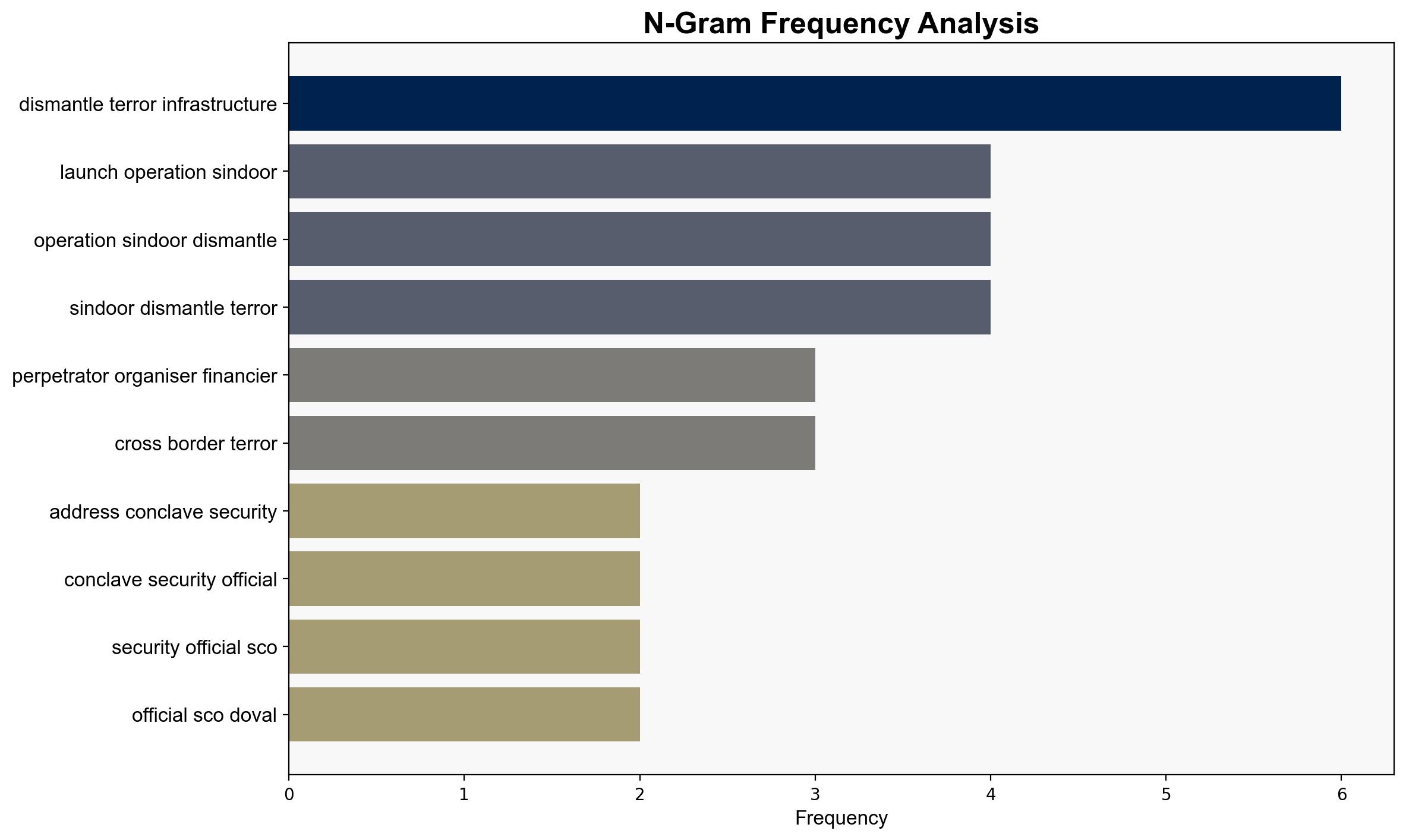
Hold perpetrators of cross-border terror to account NSA Doval at SCO meet in China – The Times of India
Published on: 2025-06-24
Intelligence Report: Hold perpetrators of cross-border terror to account NSA Doval at SCO meet in China – The Times of India
1. BLUF (Bottom Line Up Front)
Ajit Doval emphasized the need for accountability for those involved in cross-border terrorism during the Shanghai Cooperation Organisation (SCO) meeting. He called for decisive action against groups like Lashkar-e-Taiba and Jaish-e-Mohammed, highlighting India’s recent Operation Sindoor aimed at dismantling terror infrastructure. The report underscores the importance of joint operations among SCO members to combat terrorism, separatism, and extremism.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
ACH 2.0
Reconstruct likely threat actor intentions using machine-assisted hypothesis testing and structured refutation. This approach helps in understanding the strategic objectives of terror groups and their sponsors.
Indicators Development
Track digital radicalization, travel patterns, or online propaganda to anticipate operational planning. This includes monitoring online activities that could signal impending attacks.
Narrative Pattern Analysis
Analyze the spread and adaptation of ideological narratives for recruitment and incitement signals. This helps in identifying shifts in propaganda strategies and recruitment efforts.
3. Implications and Strategic Risks
The persistent threat from UN-proscribed groups poses significant risks to regional stability. The potential for increased cross-border attacks could strain diplomatic relations and escalate military tensions. Cyber threats linked to these groups may also target critical infrastructure, amplifying economic vulnerabilities.
4. Recommendations and Outlook
- Enhance intelligence-sharing mechanisms among SCO members to preemptively identify and disrupt terror plots.
- Strengthen cybersecurity frameworks to protect against potential cyber-attacks from affiliated groups.
- Scenario-based projections:
- Best Case: Successful dismantling of terror networks leads to reduced attacks and improved regional cooperation.
- Worst Case: Escalation of cross-border terrorism results in military conflict and economic instability.
- Most Likely: Continued low-intensity conflicts with sporadic successes in counter-terrorism efforts.
5. Key Individuals and Entities
Ajit Doval, Lashkar-e-Taiba, Jaish-e-Mohammed, Al-Qaeda, ISIS affiliates.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus