How to Fix a Hacked Website A Step-by-Step Recovery Guide – WordPress.com
Published on: 2025-07-17
Intelligence Report: How to Fix a Hacked Website A Step-by-Step Recovery Guide – WordPress.com
1. BLUF (Bottom Line Up Front)
The report provides a comprehensive guide to recovering a hacked WordPress website, emphasizing the importance of securing web hosts and maintaining updated software to prevent future breaches. Key recommendations include strengthening server configurations, using trusted plugins, and monitoring for unusual activity. These measures are crucial for mitigating risks associated with cyber threats targeting website vulnerabilities.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Cyber adversaries often exploit weak server configurations and outdated software. Simulating these attacks can help identify vulnerabilities and strengthen defenses.
Indicators Development
Monitoring for anomalies such as unexpected traffic patterns or unauthorized admin access can serve as early warnings of potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest that maintaining updated systems and secure configurations significantly reduce the likelihood of successful cyber attacks.
3. Implications and Strategic Risks
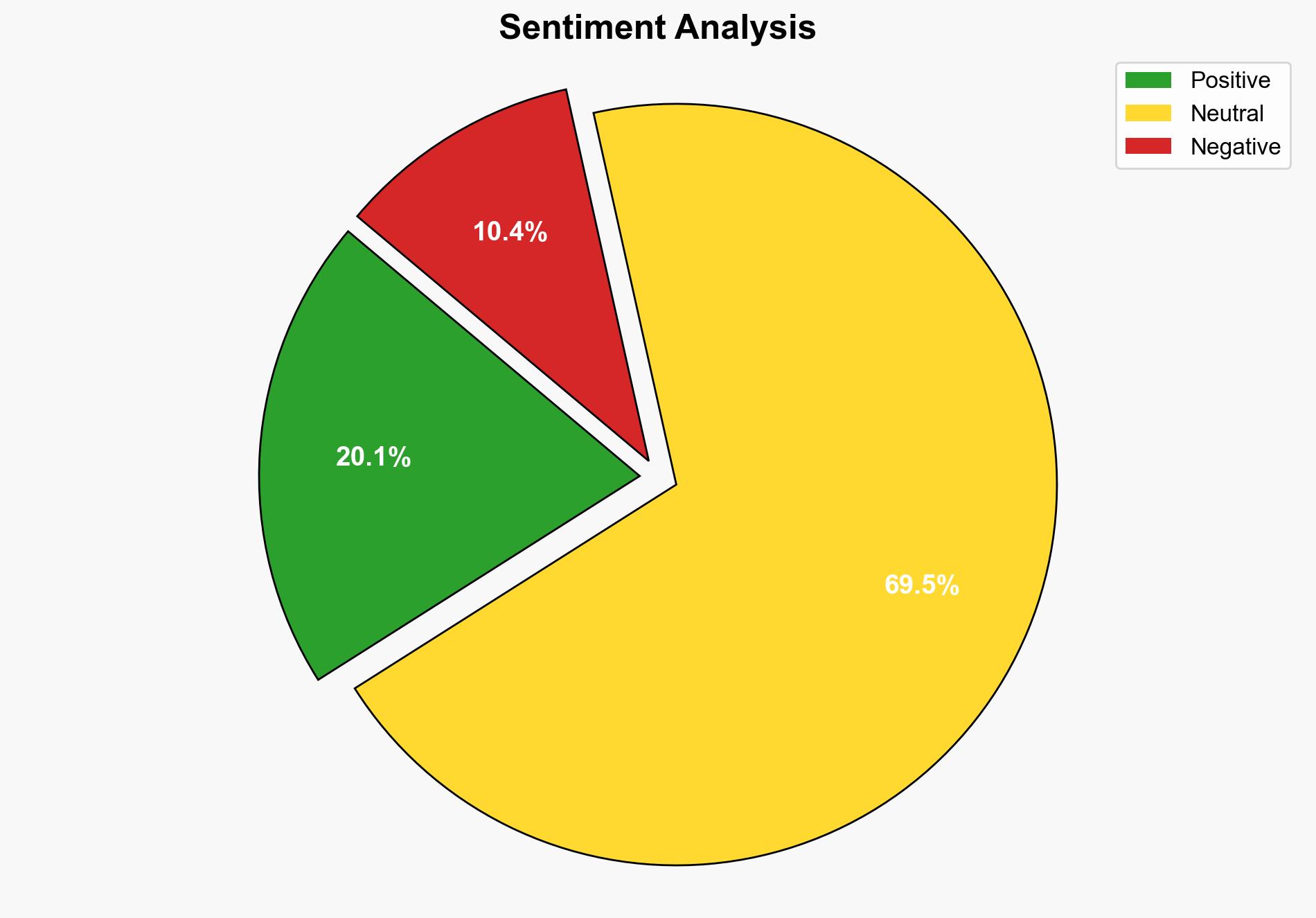
The persistence of outdated software and weak security practices poses systemic vulnerabilities across digital infrastructures. Such weaknesses can lead to data theft, malware distribution, and reputational damage. The cascading effects of a breach can impact economic stability and national security, especially if critical infrastructure is targeted.
4. Recommendations and Outlook
- Regularly update WordPress core, plugins, and themes to patch known vulnerabilities.
- Implement strong password policies and two-factor authentication to enhance security.
- Conduct regular security audits and penetration testing to identify and address vulnerabilities.
- Best Case: Enhanced security measures lead to reduced breach incidents and increased trust.
- Worst Case: Failure to address vulnerabilities results in significant data breaches and financial losses.
- Most Likely: Incremental improvements in security practices reduce but do not eliminate risks.
5. Key Individuals and Entities
No specific individuals are mentioned in the context of this report. The focus remains on general practices and strategies applicable to website administrators and cybersecurity professionals.
6. Thematic Tags
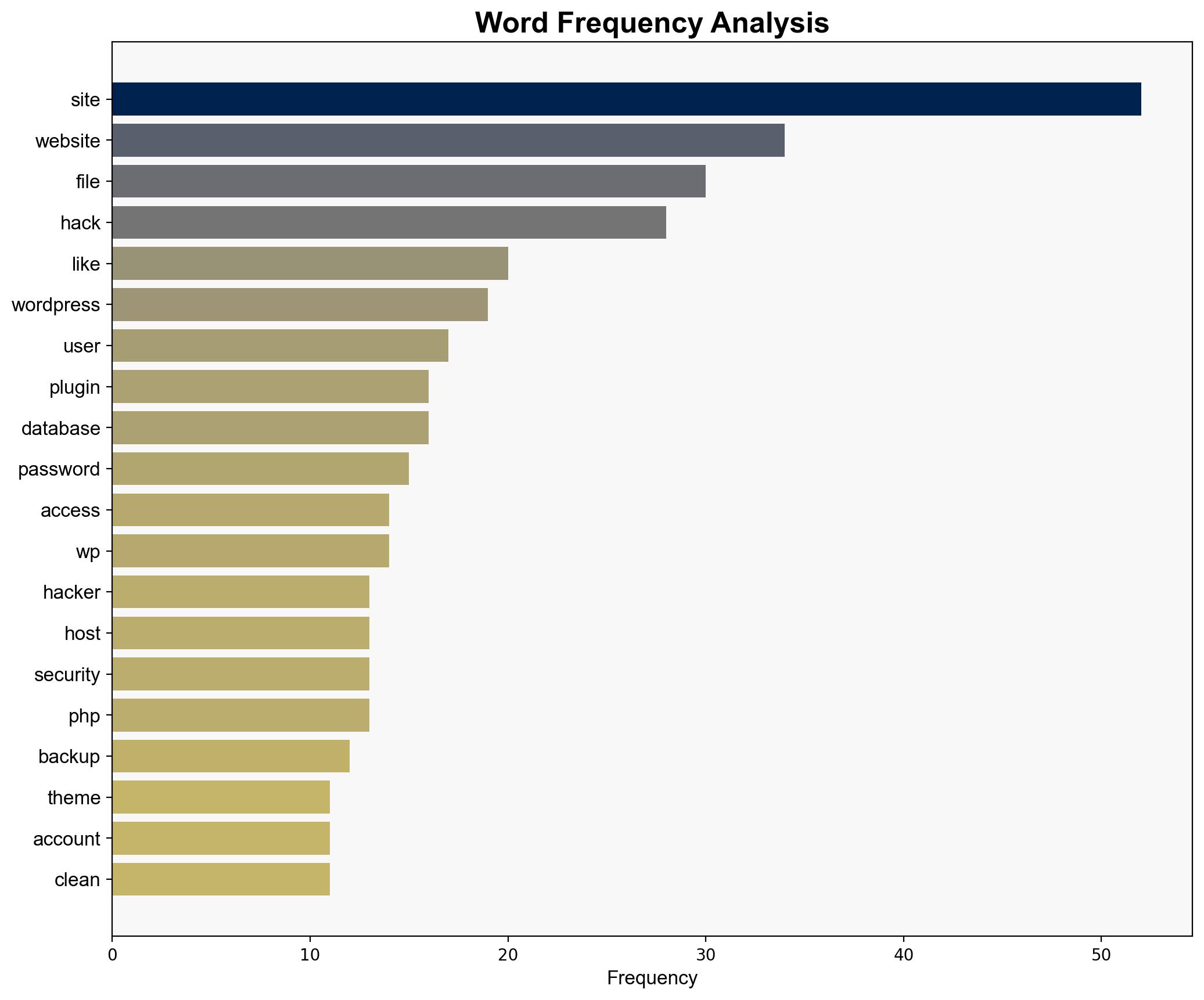
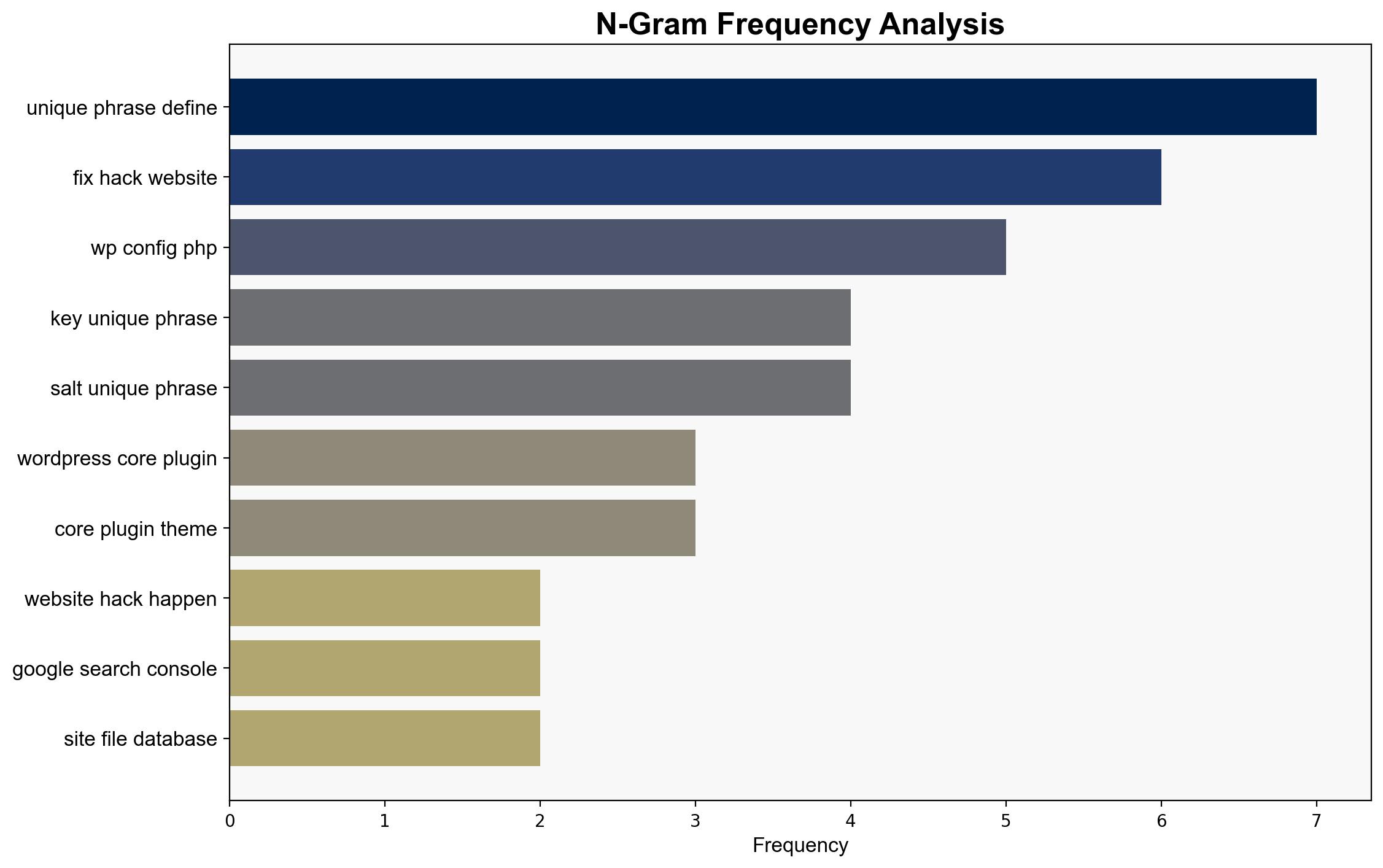
national security threats, cybersecurity, data protection, website security, risk management