How to share files with sensitive content securely on Windows 11 – Windows Central
Published on: 2025-04-17
Intelligence Report: How to Share Files with Sensitive Content Securely on Windows 11 – Windows Central
1. BLUF (Bottom Line Up Front)
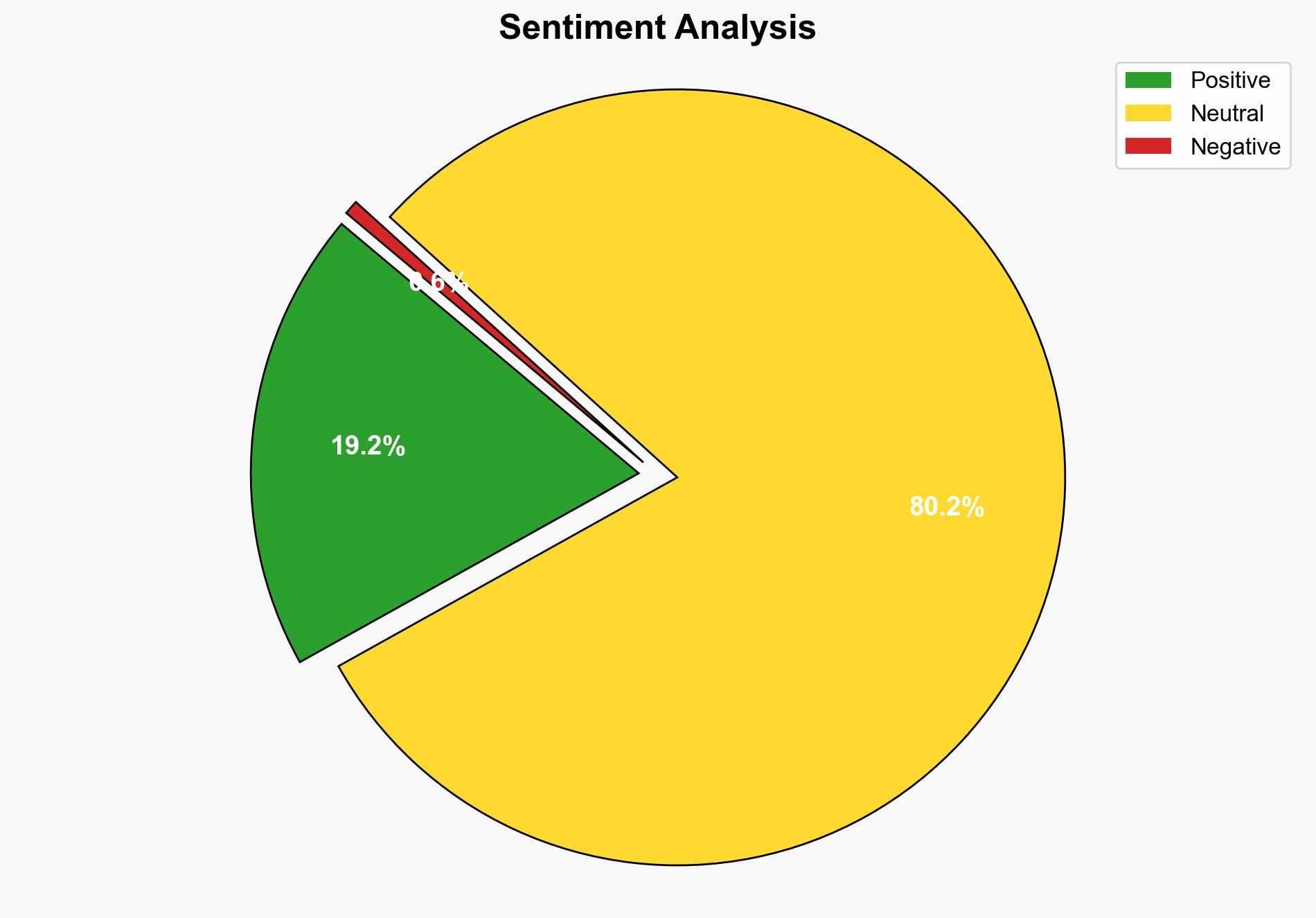
The report highlights effective methods for securely sharing sensitive files on Windows 11. Key recommendations include removing metadata, using encryption, and selecting secure transmission mediums. These steps significantly reduce the risk of unauthorized access and data breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
Potential causes for security breaches include inadequate encryption, improper handling of metadata, and insecure transmission channels. Motivations for attacks may range from financial gain to espionage.
SWOT Analysis
Strengths: Availability of third-party encryption tools like 7-Zip; Windows 11’s built-in security features.
Weaknesses: Lack of native file-level encryption in Windows 11; potential user error in following security protocols.
Opportunities: Increasing user awareness and education on cybersecurity practices; development of more integrated security solutions.
Threats: Evolving cyber threats targeting file-sharing vulnerabilities; potential exploitation of metadata.
Indicators Development
Warning signs of emerging cyber threats include increased phishing attempts, unauthorized access attempts, and unusual network activity. Monitoring these indicators can help preemptively address potential breaches.
3. Implications and Strategic Risks
The primary risks involve unauthorized data access and potential leaks of sensitive information, which could have significant political and economic repercussions. Ensuring secure file-sharing practices is crucial to maintaining data integrity and trust.
4. Recommendations and Outlook
- Implement mandatory training on secure file-sharing practices for all users.
- Encourage the use of third-party encryption tools and regularly update them to mitigate vulnerabilities.
- Develop a comprehensive cybersecurity strategy that includes regular audits and updates to security protocols.
- Scenario-based projection: If current practices are not improved, the likelihood of data breaches will increase, potentially leading to significant financial and reputational damage.
5. Key Individuals and Entities
Not applicable for this report as it focuses on general practices and tools rather than specific individuals or entities.