How to use Hashcat to recover passwords – Techtarget.com
Published on: 2025-11-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
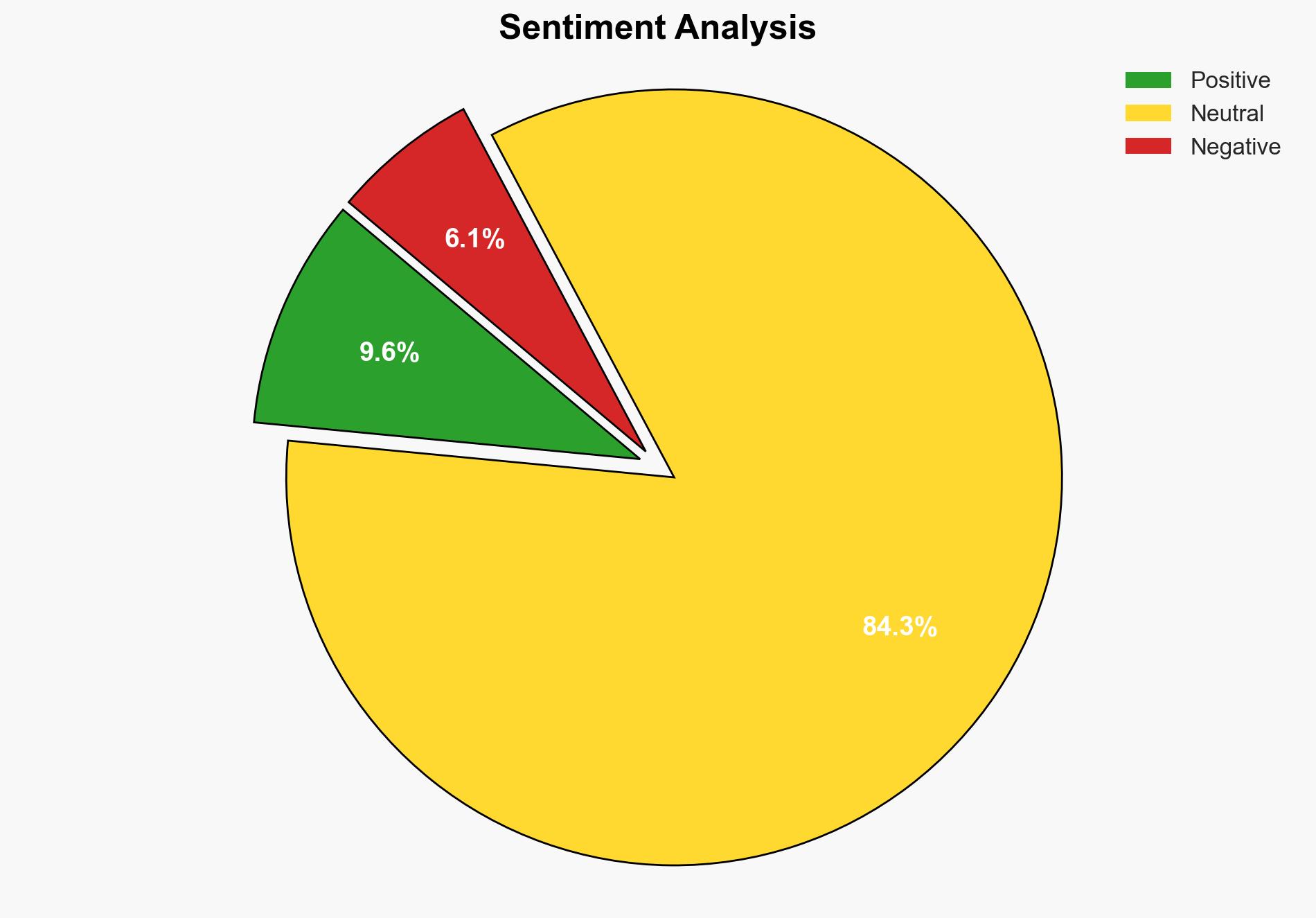
The strategic judgment is that the use of Hashcat for password recovery presents a dual-use technology risk, with a moderate confidence level that it is more likely to be exploited for unauthorized access than for ethical purposes. Recommended actions include enhancing cybersecurity training, implementing strict access controls, and monitoring for misuse.
2. Competing Hypotheses
Hypothesis 1: Hashcat is primarily used by cybersecurity professionals for ethical hacking and security testing, contributing positively to organizational security.
Hypothesis 2: Hashcat is predominantly exploited by malicious actors to gain unauthorized access to systems, posing a significant cybersecurity threat.
Hypothesis 2 is more likely given the tool’s powerful capabilities and the general difficulty in enforcing ethical use, especially considering the ease of access and potential for misuse by individuals with malicious intent.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that users of Hashcat have the technical expertise to use it responsibly and that organizations have adequate policies to govern its use.
Red Flags: The tutorial’s emphasis on the tool’s efficiency and power without sufficient emphasis on ethical guidelines could indicate a potential for misuse. The lack of robust verification mechanisms for ethical use is a significant concern.
4. Implications and Strategic Risks
The primary risk is the potential for widespread unauthorized access to sensitive systems, leading to data breaches and loss of sensitive information. This could escalate into significant economic and reputational damage for affected organizations. Politically, it could lead to increased regulatory scrutiny and potential sanctions for non-compliance with cybersecurity standards.
5. Recommendations and Outlook
- Enhance cybersecurity training programs to emphasize ethical use and legal implications of using tools like Hashcat.
- Implement strict access controls and monitoring systems to detect and prevent unauthorized use of password recovery tools.
- Develop and enforce comprehensive policies that clearly define the legal and ethical boundaries for using such tools.
- Best-case scenario: Organizations effectively use Hashcat to strengthen their cybersecurity posture without incidents of misuse.
- Worst-case scenario: Widespread misuse leads to significant data breaches and regulatory penalties.
- Most-likely scenario: Mixed use with some incidents of misuse, prompting increased regulatory focus and organizational policy adjustments.
6. Key Individuals and Entities
Rob Shapland, mentioned as an ethical hacker specializing in cloud security and social engineering, is a key individual in promoting ethical cybersecurity practices.
7. Thematic Tags
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us