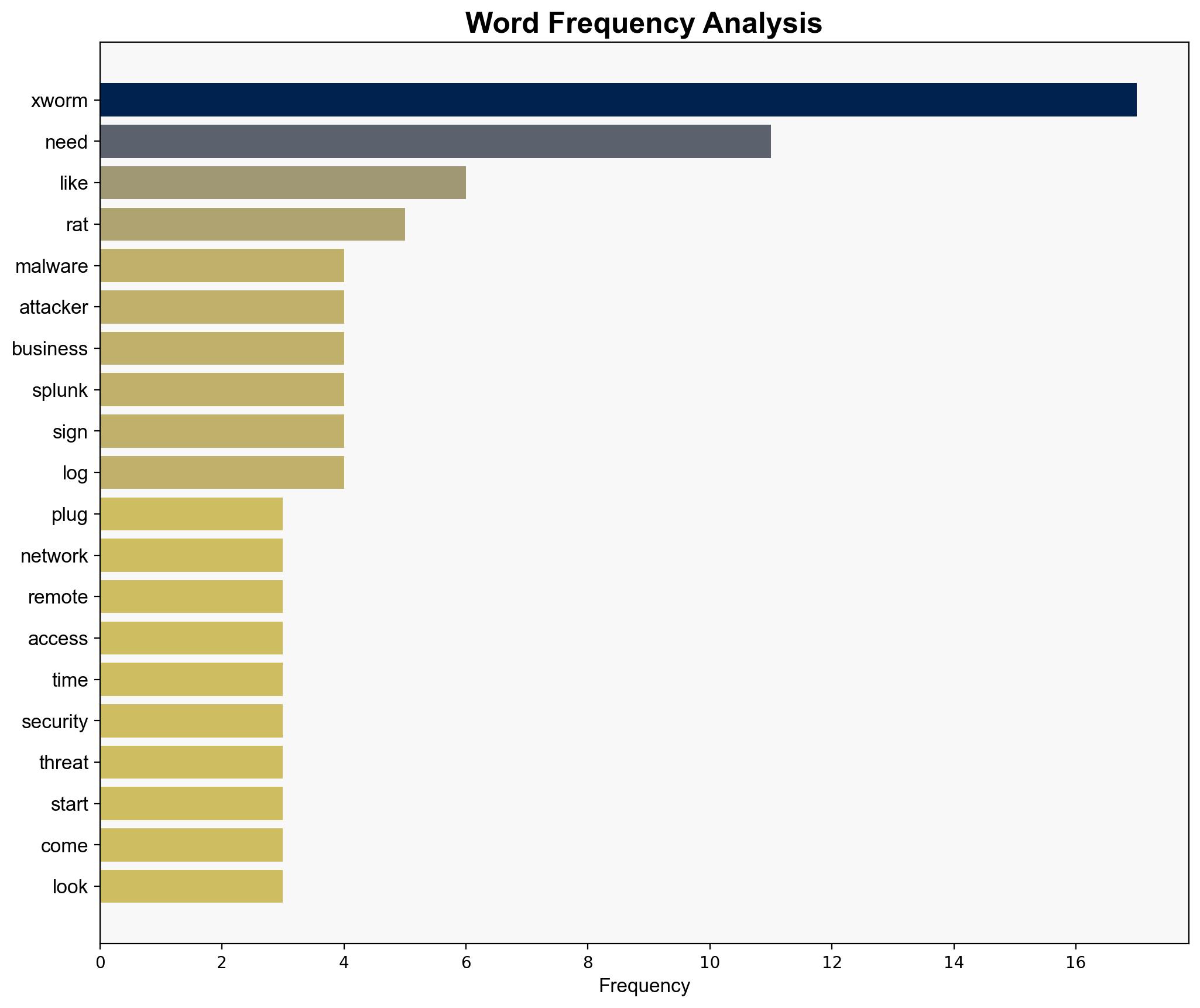
How XWorm is fueling the rise of plug-and-play malware – TechRadar
Published on: 2025-09-12
Intelligence Report: How XWorm is fueling the rise of plug-and-play malware – TechRadar
1. BLUF (Bottom Line Up Front)
XWorm is significantly contributing to the proliferation of plug-and-play malware due to its accessibility, ease of use, and effectiveness in evading detection. The most supported hypothesis is that XWorm’s rise is primarily due to its ability to exploit existing vulnerabilities in legacy systems and overworked security teams. Confidence level: High. Recommended action: Enhance detection capabilities and conduct regular security audits to mitigate risks.
2. Competing Hypotheses
1. **Hypothesis A**: XWorm’s rise is primarily due to its technical capabilities and modular design, making it an attractive option for cybercriminals seeking efficient and effective tools.
2. **Hypothesis B**: The increase in XWorm usage is largely driven by the vulnerabilities in legacy infrastructure and the inability of overworked security teams to detect and respond to threats in a timely manner.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis B is better supported due to the emphasis on XWorm’s ability to exploit existing weaknesses rather than its technical innovations.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that all organizations have legacy systems and overworked security teams, which may not be universally true.
– **Red Flags**: The open sale of XWorm on forums suggests potential underestimation of its distribution and impact.
– **Blind Spots**: Lack of detailed data on the specific sectors most affected by XWorm could hinder targeted defense strategies.
4. Implications and Strategic Risks
The widespread use of XWorm could lead to increased cyberattacks across critical sectors such as finance, healthcare, and government. This could result in significant economic losses and undermine public trust in digital infrastructure. The potential for cascading threats includes data breaches, financial theft, and operational disruptions.
5. Recommendations and Outlook
- Enhance network monitoring and anomaly detection to identify subtle indicators of XWorm activity.
- Conduct regular security audits and vulnerability assessments to identify and patch weaknesses.
- Implement scenario-based training exercises to improve response times and effectiveness.
- Best Case Scenario: Organizations rapidly adapt to the threat, reducing XWorm’s impact through improved defenses.
- Worst Case Scenario: XWorm’s proliferation overwhelms current security measures, leading to widespread data breaches and financial losses.
- Most Likely Scenario: Incremental improvements in security measures mitigate some risks, but XWorm continues to pose a significant threat.
6. Key Individuals and Entities
– Mick Baccio
– Teoderick Contreras
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus