How Your AI Chatbot Can Become a Backdoor – Trendmicro.com
Published on: 2025-10-08
Intelligence Report: How Your AI Chatbot Can Become a Backdoor – Trendmicro.com
1. BLUF (Bottom Line Up Front)
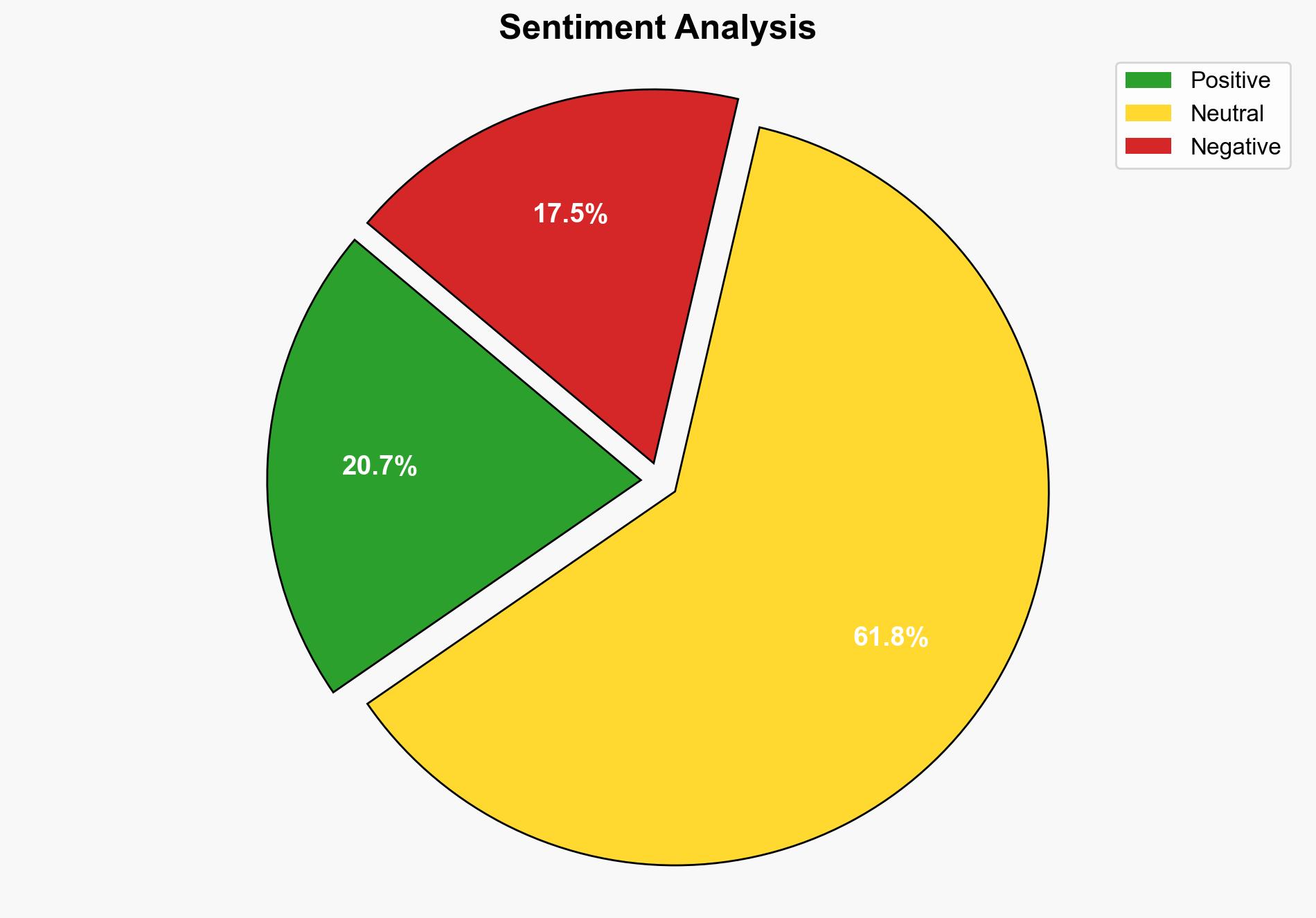
The most supported hypothesis is that AI chatbots, due to their complex and interconnected nature, present a significant cybersecurity risk as potential backdoors for attackers. This is supported by the detailed attack chain analysis provided. Confidence level is moderate due to the evolving nature of AI threats. Recommended action includes implementing a robust, multi-layered defense strategy to secure AI ecosystems and prevent exploitation.
2. Competing Hypotheses
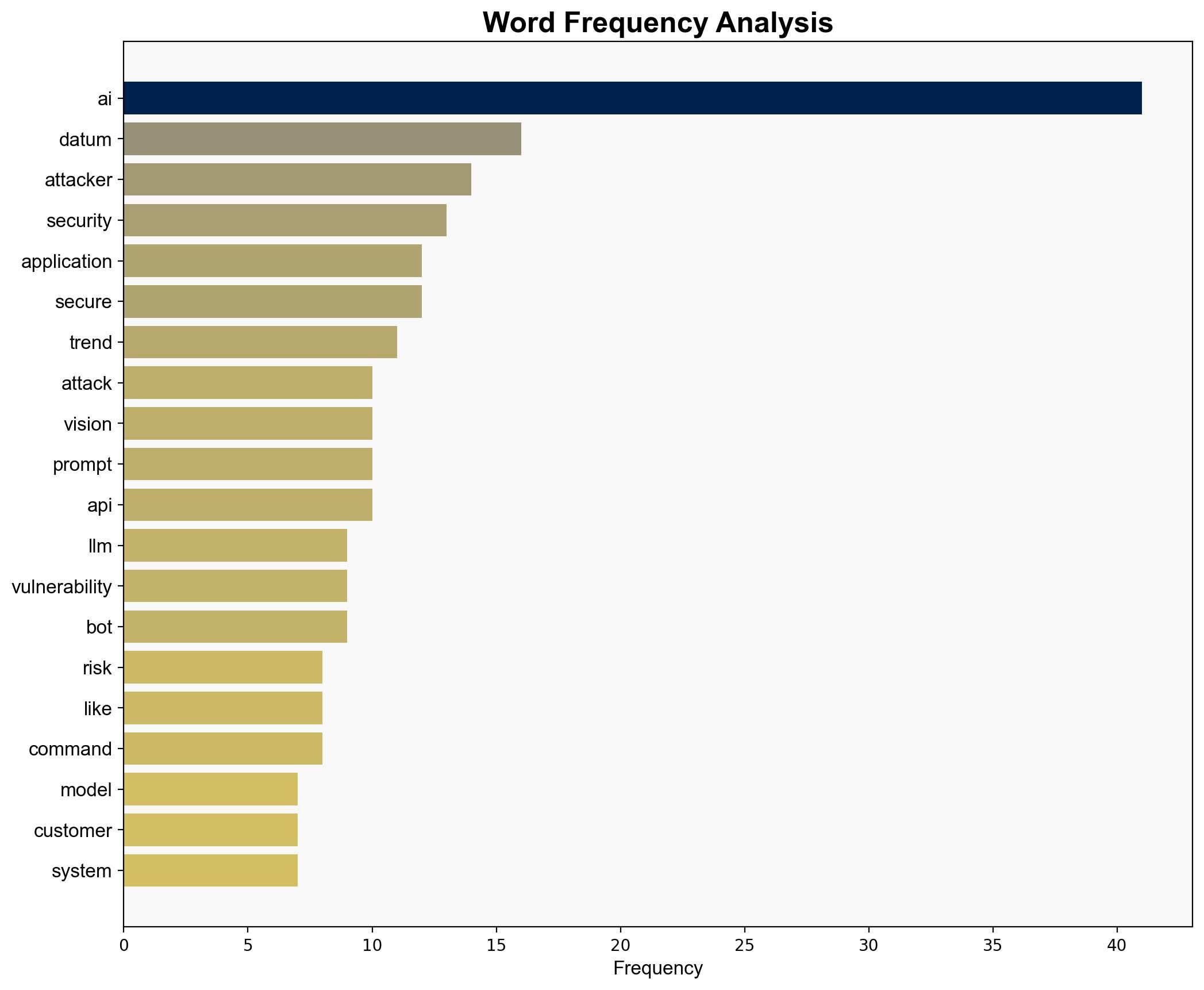
1. **Hypothesis A**: AI chatbots inherently increase cybersecurity risks due to their complexity and the potential for exploitation through indirect prompt injections and system prompt leakage.
2. **Hypothesis B**: The perceived risk of AI chatbots as backdoors is overstated and can be mitigated with existing cybersecurity measures and best practices.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the detailed attack scenarios and vulnerabilities identified, such as OWASP LLM vulnerabilities and indirect prompt injections, which are not fully addressed by current standard cybersecurity measures.
3. Key Assumptions and Red Flags
– **Assumptions**:
– AI systems will continue to be integrated into business operations without significant changes to current security protocols.
– Attackers have the capability to exploit identified vulnerabilities effectively.
– **Red Flags**:
– Lack of detailed mitigation strategies for specific vulnerabilities.
– Potential bias in the source towards emphasizing threats to promote security solutions.
4. Implications and Strategic Risks
The integration of AI chatbots into business operations could lead to significant cybersecurity threats if vulnerabilities are exploited, potentially resulting in data breaches and financial losses. The cascading effect of a compromised AI system could extend to broader IT infrastructure, impacting customer trust and operational integrity. Geopolitically, widespread exploitation could lead to regulatory scrutiny and international tensions over data privacy and security standards.
5. Recommendations and Outlook
- Implement a comprehensive, multi-layered security strategy focusing on securing the entire AI stack.
- Regularly update and patch AI systems to address known vulnerabilities.
- Conduct continuous threat assessments and simulations to identify potential weaknesses.
- Best-case scenario: AI systems are secured, leading to enhanced business operations with minimal risk.
- Worst-case scenario: Unaddressed vulnerabilities lead to significant breaches and loss of customer trust.
- Most likely scenario: Incremental improvements in AI security reduce but do not eliminate risk.
6. Key Individuals and Entities
Eva Chen, Trend Micro CEO and founder, is a key individual mentioned in the context of advocating for comprehensive AI security strategies.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus