Hundreds of Cisco Clients at Risk from New Chinese Cyber Attack, Researchers Warn
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hundreds of Cisco customers are vulnerable to new Chinese hacking campaign researchers say TechCrunch
1. BLUF (Bottom Line Up Front)
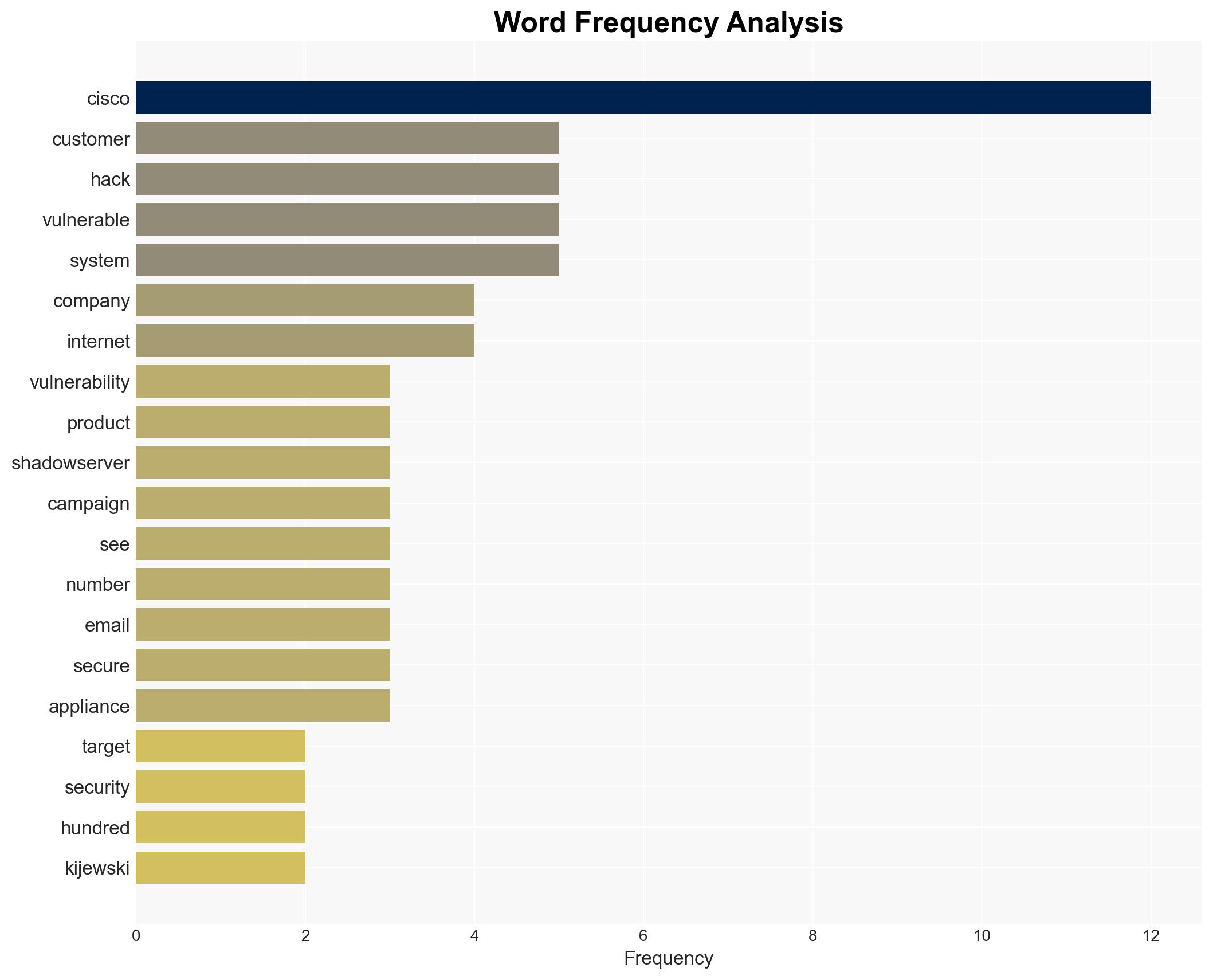
A Chinese government-backed hacking group is exploiting a zero-day vulnerability in Cisco products, potentially affecting hundreds of enterprise customers. The campaign appears targeted, with no patches currently available, necessitating system restoration for mitigation. This assessment is made with moderate confidence due to limited data on the full scope of affected systems.
2. Competing Hypotheses
- Hypothesis A: The hacking campaign is a targeted operation by a Chinese state-sponsored group aimed at specific high-value targets. This is supported by the limited number of affected systems and the targeted nature of the attacks. However, the exact criteria for target selection remain unclear.
- Hypothesis B: The campaign is a broader reconnaissance effort to identify vulnerabilities across a wide range of Cisco customers, potentially for future exploitation. This is contradicted by the current evidence of limited activity and the specific conditions required for vulnerability exploitation.
- Assessment: Hypothesis A is currently better supported due to the observed targeted nature of the attacks and the limited number of affected systems. Indicators such as an increase in the number of affected systems or broader targeting patterns could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is not widely known outside of the identified threat actors; Cisco’s remediation guidance is effective in preventing further compromise; the threat actors are indeed state-sponsored.
- Information Gaps: The total number of affected systems and the specific targets of the campaign; detailed attribution of the hacking group to Chinese state apparatus; the timeline for Cisco’s patch release.
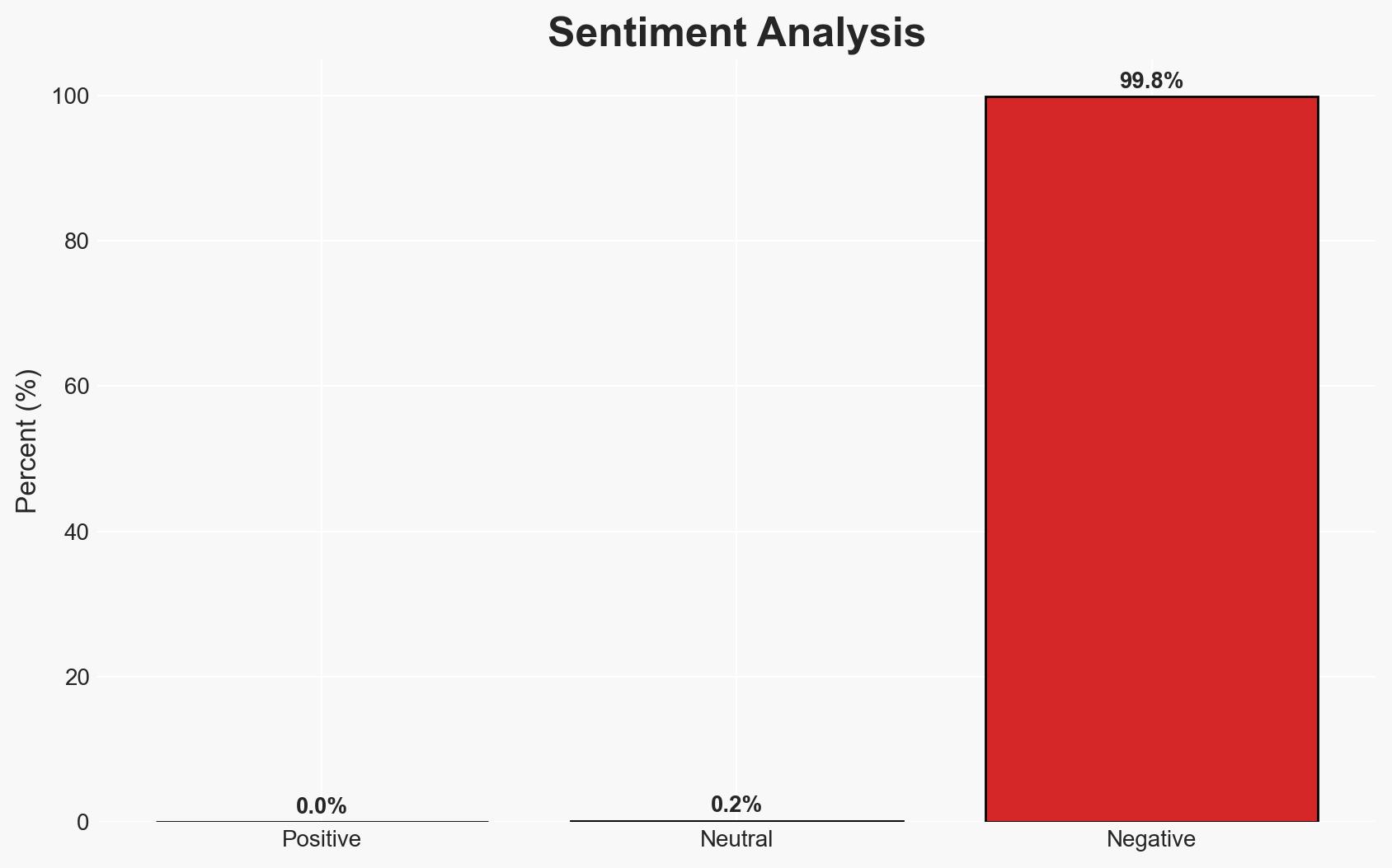
- Bias & Deception Risks: Potential bias in attributing the campaign to Chinese actors without conclusive evidence; reliance on third-party reports such as Shadowserver and Censys, which may have their own data limitations.
4. Implications and Strategic Risks
This development could lead to increased tensions in cyber relations between China and affected nations, particularly if the campaign is perceived as state-sponsored cyber-espionage.
- Political / Geopolitical: Potential diplomatic friction between China and affected countries, especially if the campaign escalates or targets critical infrastructure.
- Security / Counter-Terrorism: Increased vigilance required for potential follow-on attacks or data exfiltration activities.
- Cyber / Information Space: Heightened awareness and scrutiny of Cisco products, potential for increased cybersecurity measures and vendor accountability.
- Economic / Social: Potential financial impact on affected organizations due to system restoration costs and operational disruptions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage affected organizations to follow Cisco’s remediation guidance; enhance monitoring for signs of compromise; engage with Cisco for updates on patch development.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in resilience measures to mitigate future zero-day vulnerabilities.
- Scenario Outlook:
- Best: Rapid patch deployment by Cisco mitigates the threat with minimal disruption.
- Worst: Widespread exploitation leads to significant data breaches and geopolitical tensions.
- Most-Likely: Targeted attacks continue until patches are deployed, with limited broader impact.
6. Key Individuals and Entities
- Piotr Kijewski, Shadowserver Foundation
- Cisco Systems, Inc.
- Censys, Cybersecurity Firm
- Not clearly identifiable from open sources in this snippet for specific threat actors.
7. Thematic Tags
cybersecurity, zero-day vulnerability, Chinese state-sponsored hacking, Cisco, cyber-espionage, threat intelligence, enterprise security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us