ICE Is Collecting More Data Aims to Outsource Judgment to Private Contractors – Truthout
Published on: 2025-11-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: ICE Data Collection and Outsourcing to Private Contractors
1. BLUF (Bottom Line Up Front)
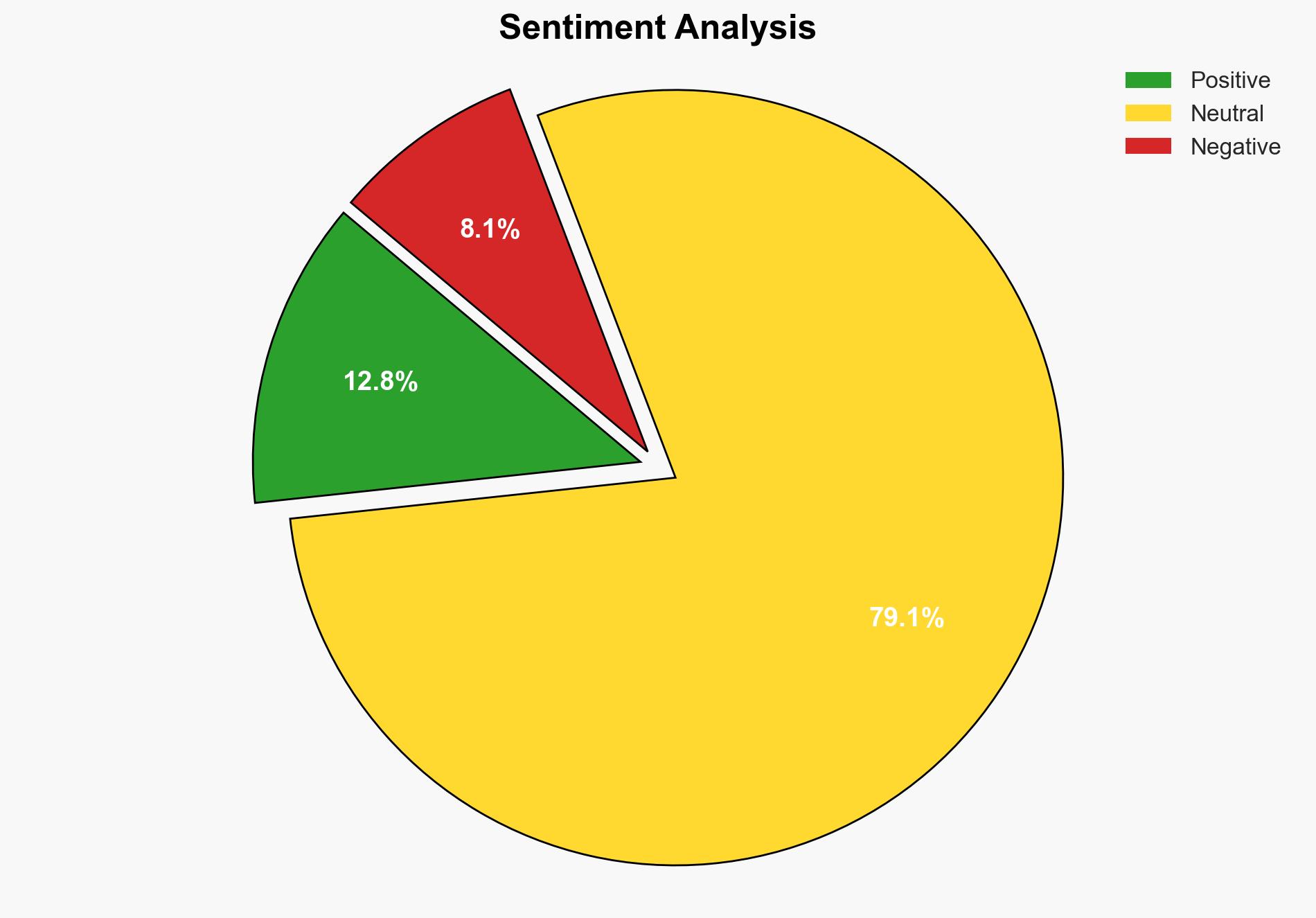
With a moderate confidence level, the most supported hypothesis is that ICE’s increased data collection and outsourcing to private contractors is primarily aimed at enhancing operational efficiency and effectiveness in immigration enforcement. However, this approach poses significant privacy and civil liberties concerns, potentially leading to public backlash and legal challenges. Recommended actions include increased oversight and transparency measures to mitigate risks and maintain public trust.
2. Competing Hypotheses
Hypothesis 1: ICE’s data collection and outsourcing strategy is primarily driven by the need to enhance operational efficiency and effectiveness in identifying and monitoring high-risk individuals.
Hypothesis 2: ICE’s strategy is primarily a means to expand surveillance capabilities, potentially leading to overreach and infringement on civil liberties.
Hypothesis 1 is more likely given the historical trend of government agencies leveraging technology to improve operational capabilities. However, the potential for overreach as suggested in Hypothesis 2 cannot be dismissed, especially given past instances of scope expansion and lack of oversight.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that ICE’s intentions are aligned with stated goals of improving enforcement efficiency. It is also assumed that private contractors will adhere to legal and ethical standards.
Red Flags: The lack of transparency in contractor operations and potential for data misuse are significant concerns. Historical instances of scope creep and informal data sharing raise red flags about potential overreach.
4. Implications and Strategic Risks
The primary implications include potential public backlash and erosion of trust in government institutions due to perceived privacy violations. There is also a risk of legal challenges that could disrupt ICE operations. Escalation scenarios include increased political pressure for legislative oversight and potential cyber vulnerabilities due to expanded data collection.
5. Recommendations and Outlook
- Implement robust oversight mechanisms to ensure contractor compliance with legal and ethical standards.
- Increase transparency in data collection and usage to build public trust.
- Best-case scenario: Enhanced operational efficiency with minimal public backlash.
- Worst-case scenario: Significant legal challenges and public outcry leading to operational disruptions.
- Most-likely scenario: Continued operational improvements with ongoing public and legal scrutiny.
6. Key Individuals and Entities
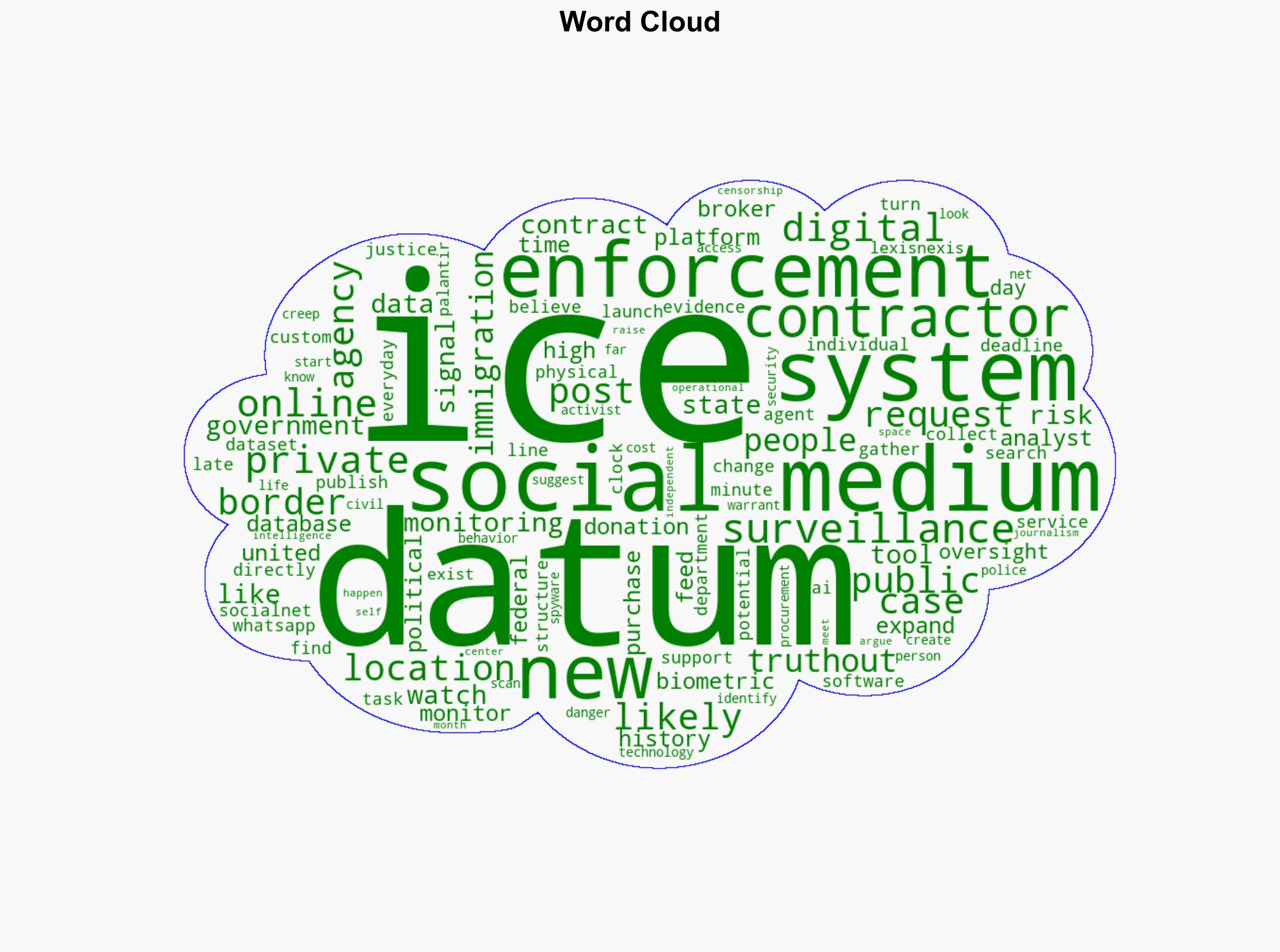
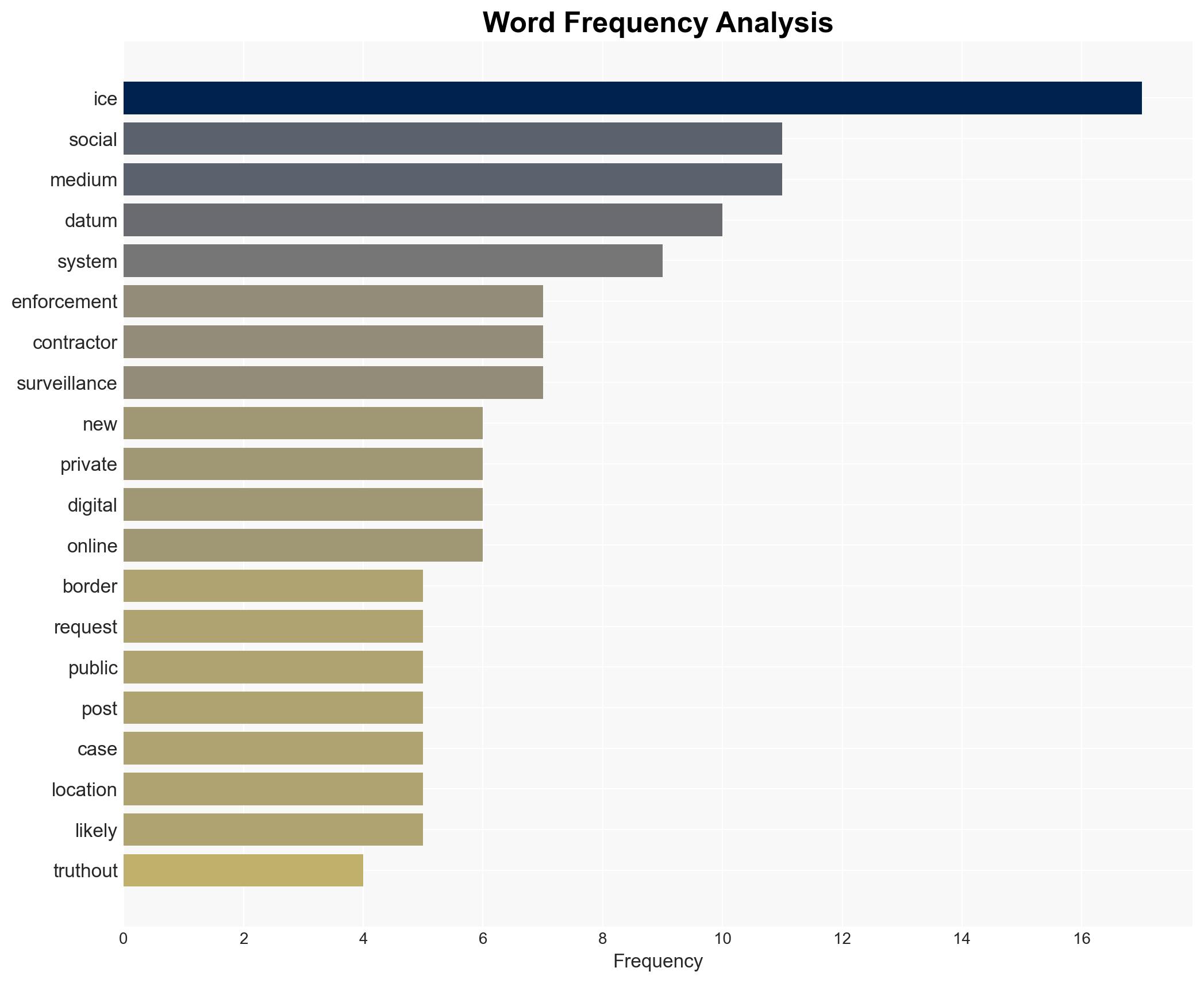
No specific individuals are mentioned in the source text. Key entities include ICE, private contractors (e.g., Zignal Labs), and data brokers (e.g., LexisNexis, Thomson Reuters).
7. Thematic Tags
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Structured challenge to expose and correct biases.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us
·