ICO Warns of Student-Led Data Breaches in UK Schools – Infosecurity Magazine
Published on: 2025-09-12
Intelligence Report: ICO Warns of Student-Led Data Breaches in UK Schools – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that student-led data breaches in UK schools are primarily driven by curiosity and a lack of legitimate cybersecurity opportunities, rather than malicious intent. This conclusion is supported by the pattern of behavior and the lack of sophisticated techniques used. Confidence level: Moderate. Recommended action: Implement educational programs to channel students’ cyber skills into legitimate pathways and enhance cybersecurity measures in schools.
2. Competing Hypotheses
Hypothesis 1: Student-led data breaches are primarily driven by curiosity and a lack of legitimate opportunities in cybersecurity. Students engage in these activities to test their skills and explore cyber capabilities without malicious intent.
Hypothesis 2: Student-led data breaches are motivated by malicious intent, with students aiming to exploit personal data for financial gain or other nefarious purposes. This hypothesis suggests a more organized and potentially harmful intent behind the breaches.
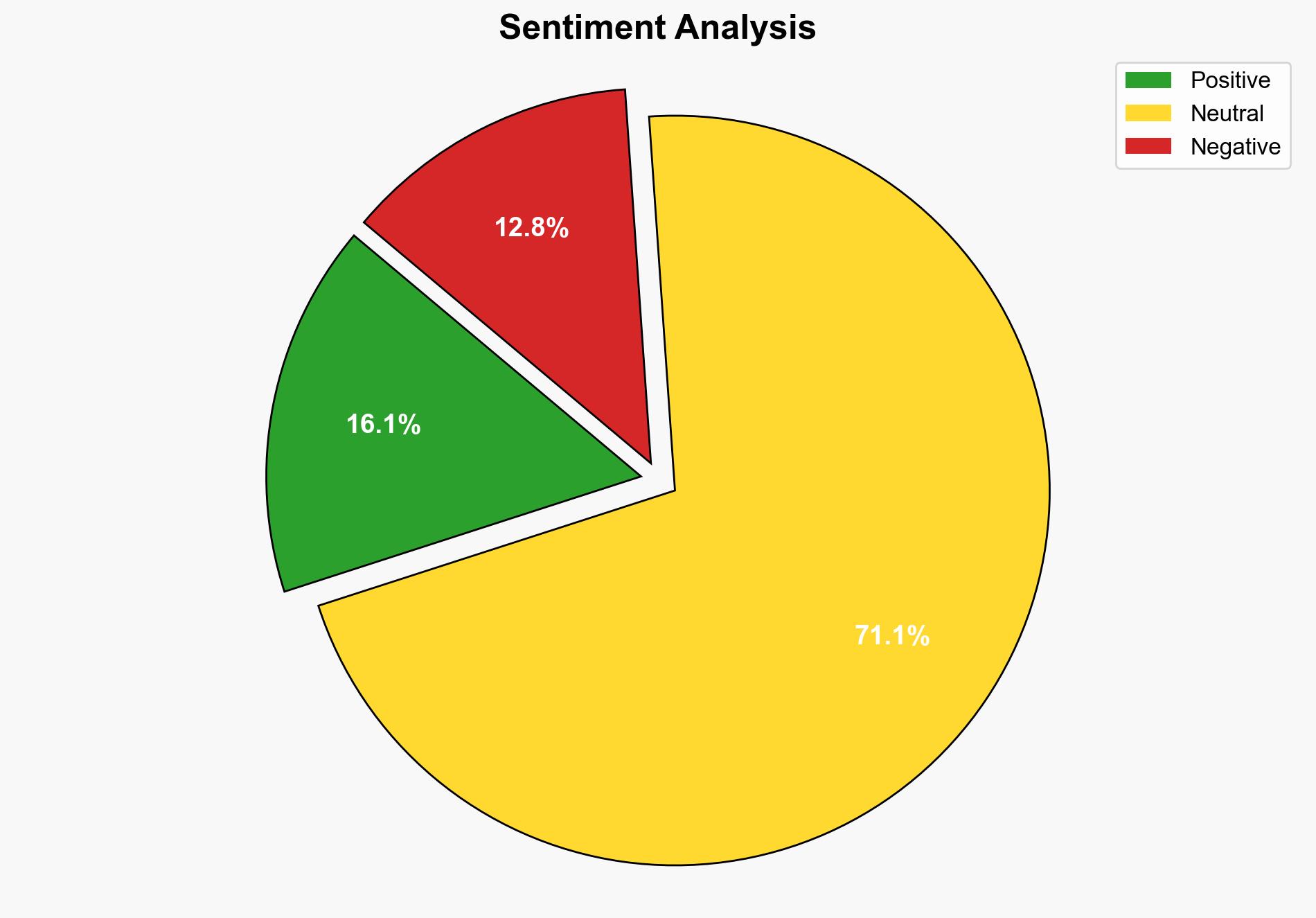
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the reported behaviors such as guessing weak passwords and accessing online hacker forums for skill development. The lack of sophisticated techniques and the emphasis on curiosity suggest a non-malicious intent.
3. Key Assumptions and Red Flags
Assumptions:
– Students lack access to legitimate cybersecurity training and opportunities.
– The breaches are primarily exploratory rather than exploitative.
Red Flags:
– Potential underestimation of students’ capabilities to conduct more sophisticated attacks.
– Insufficient data on the extent of financial or personal harm caused by these breaches.
4. Implications and Strategic Risks
The pattern of student-led breaches could escalate if not addressed, potentially leading to more sophisticated attacks as students’ skills develop. This poses a risk to personal data security and could lead to financial and reputational damage for educational institutions. The psychological impact on students, if labeled as criminals, could deter them from pursuing legitimate cybersecurity careers, exacerbating the skills shortage in this field.
5. Recommendations and Outlook
- Implement cybersecurity education programs in schools to channel students’ curiosity into legitimate career paths.
- Strengthen cybersecurity protocols in educational institutions to prevent unauthorized access.
- Best-case scenario: Students are guided into cybersecurity careers, reducing breaches and addressing workforce shortages.
- Worst-case scenario: Breaches become more sophisticated, leading to significant data losses and reputational damage.
- Most likely scenario: With proper intervention, the frequency and impact of breaches decrease over time.
6. Key Individuals and Entities
– Heather Toomey
– Chris Wysopal
– ICO (Information Commissioner’s Office)
– NCA (National Crime Agency)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus