Identity Risk Metrics Revolutionize Cyber Insurance Evaluations by 2026
Published on: 2026-02-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Identity Cyber Scores The New Metric Shaping Cyber Insurance in 2026
1. BLUF (Bottom Line Up Front)
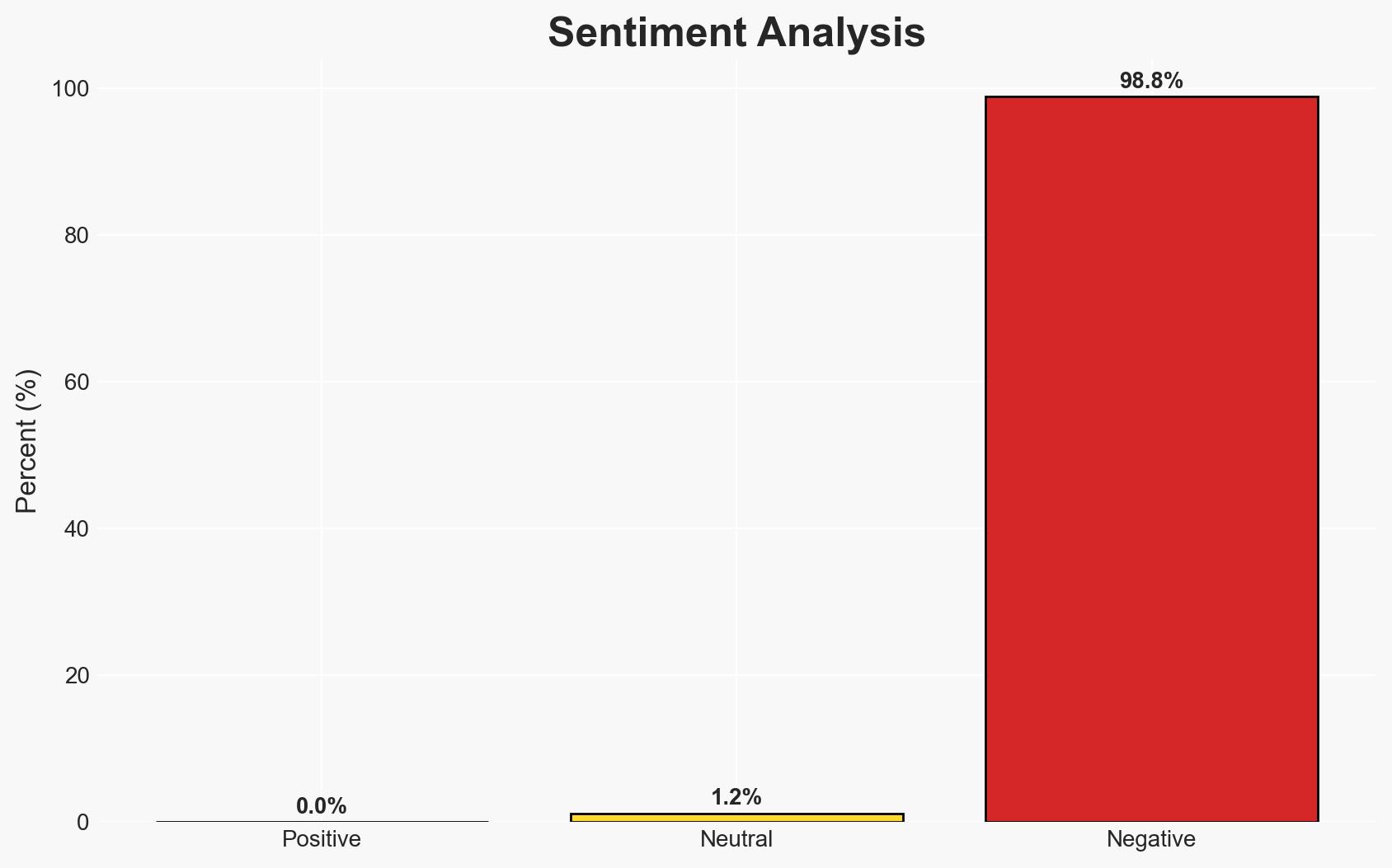
The increasing emphasis on identity posture in cyber insurance underwriting is reshaping how organizations manage cyber risks, with a particular focus on credential management and privileged access. This shift is driven by the rising cost of data breaches and the prevalence of credential compromise. The most likely hypothesis is that insurers will continue to tighten requirements, impacting organizations’ cyber risk management strategies. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Insurers are tightening identity posture requirements primarily due to the increasing frequency and cost of data breaches. Supporting evidence includes the rise in cyber insurance coverage and the emphasis on identity controls. However, there is uncertainty about the uniformity of these requirements across different insurers.
- Hypothesis B: The focus on identity posture is a temporary trend driven by current high-profile breaches and may not sustain long-term changes in underwriting practices. This is contradicted by the ongoing increase in claims and the persistent threat of credential compromise.
- Assessment: Hypothesis A is currently better supported due to the consistent increase in insurance coverage and the strategic emphasis on identity controls. Indicators that could shift this judgment include changes in breach costs or a significant reduction in credential-based attacks.
3. Key Assumptions and Red Flags
- Assumptions: Insurers will continue to prioritize identity posture in underwriting; credential compromise remains a primary attack vector; organizations will adapt to these new requirements.
- Information Gaps: Specific insurer criteria for identity posture; data on the effectiveness of identity controls in reducing breach costs.
- Bias & Deception Risks: Potential bias from insurers overstating the effectiveness of identity controls; possible manipulation of identity posture metrics by organizations seeking favorable terms.
4. Implications and Strategic Risks
The focus on identity posture in cyber insurance could lead to significant changes in organizational cybersecurity strategies and insurance markets. This development may influence broader regulatory and industry standards.
- Political / Geopolitical: Potential for increased regulatory oversight on identity management practices.
- Security / Counter-Terrorism: Enhanced identity controls could reduce the effectiveness of credential-based attacks, impacting threat actor strategies.
- Cyber / Information Space: Increased focus on identity security may drive innovation in authentication technologies and practices.
- Economic / Social: Organizations may face increased costs to comply with new insurance requirements, impacting financial stability and operational budgets.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive review of current identity management practices; engage with insurers to understand specific underwriting criteria.
- Medium-Term Posture (1–12 months): Develop and implement a robust identity management strategy; invest in technologies that enhance credential security and privileged access management.
- Scenario Outlook:
- Best: Organizations adapt effectively, reducing breach costs and securing favorable insurance terms.
- Worst: Identity posture requirements become overly burdensome, leading to increased operational costs and potential non-compliance.
- Most-Likely: Gradual adaptation to new requirements, with incremental improvements in identity security practices.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber insurance, identity management, credential security, data breaches, underwriting practices, cyber risk, privileged access management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us