Illicit Stablecoin Transactions Reach $141 Billion in 2025, Marking a Five-Year Peak, Reports TRM Labs
Published on: 2026-02-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Illicit stablecoin activity hit 5-year high of 141B in 2025 TRM Labs
1. BLUF (Bottom Line Up Front)
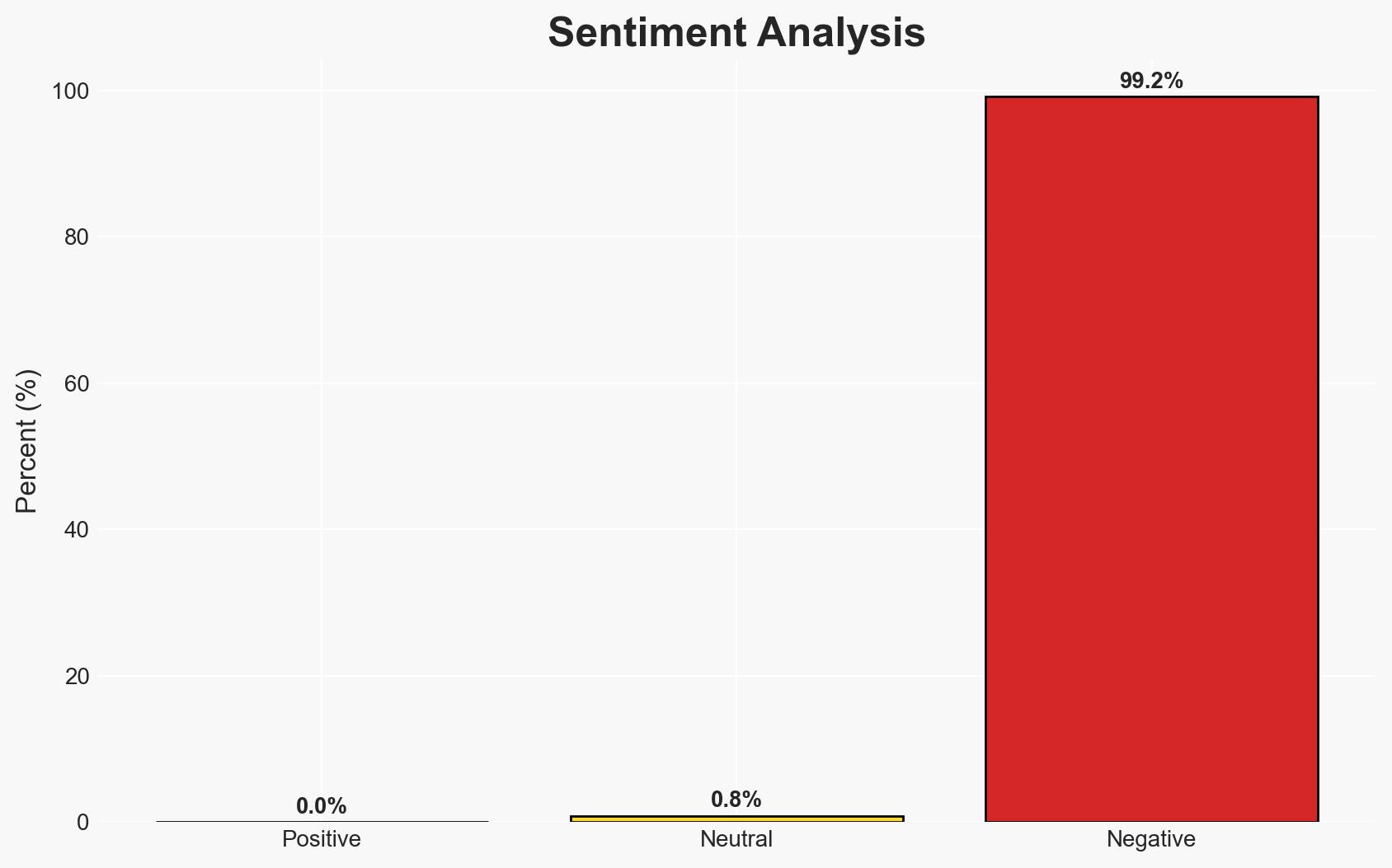
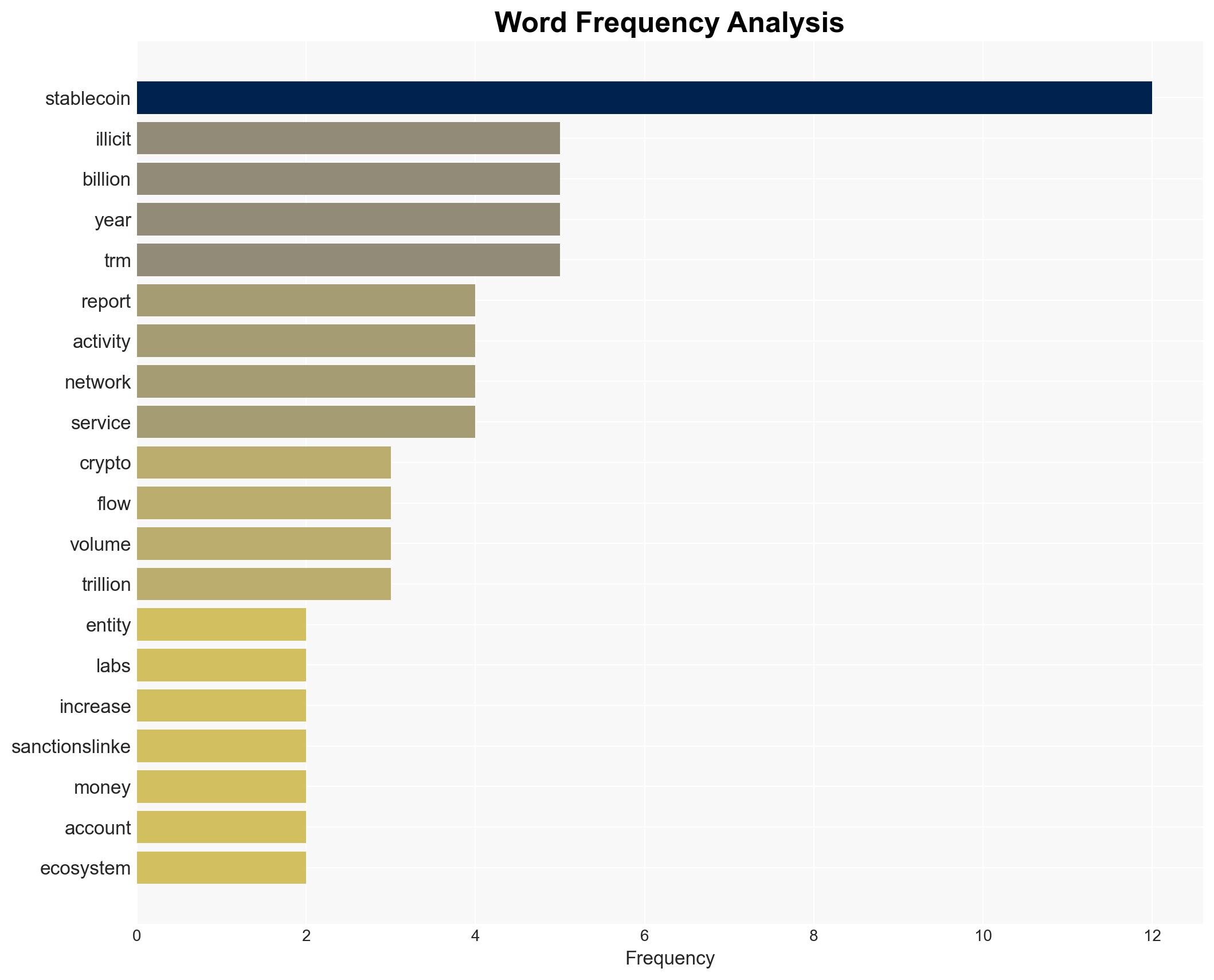
Illicit stablecoin activity reached a five-year high of $141 billion in 2025, primarily driven by sanctions-related transactions. The Russian ruble-pegged token A7A5 is heavily implicated, suggesting a strategic shift in how sanctioned entities bypass financial controls. This development poses significant geopolitical and security challenges, with moderate confidence in the assessment due to existing information gaps.
2. Competing Hypotheses
- Hypothesis A: The increase in illicit stablecoin activity is primarily due to sanctioned states and actors exploiting stablecoins to circumvent international financial restrictions. This is supported by the concentration of activity in sanctions-linked networks and the use of the Russian ruble-pegged token A7A5. Uncertainties include the full extent of state involvement and potential undisclosed networks.
- Hypothesis B: The rise in illicit stablecoin activity is a broader trend in the criminal underworld’s adoption of stablecoins for various illegal activities, not limited to sanctions evasion. While stablecoins are used in other illicit activities, the predominance of sanctions-related flows contradicts this hypothesis.
- Assessment: Hypothesis A is currently better supported due to the specific mention of sanctions-related flows and the significant role of the A7A5 token. Indicators that could shift this judgment include evidence of increased stablecoin use in non-sanction-related illicit activities.
3. Key Assumptions and Red Flags
- Assumptions: Stablecoins offer operational advantages for illicit transactions; sanctions-related actors are primary drivers of the observed increase; blockchain analytics accurately capture illicit flows.
- Information Gaps: Detailed breakdown of non-sanction-related illicit stablecoin activities; comprehensive data on the involvement of state actors beyond Russia.
- Bias & Deception Risks: Potential bias in data interpretation from TRM Labs; risk of deceptive practices by illicit actors to obfuscate transactions.
4. Implications and Strategic Risks
This development could lead to increased geopolitical tensions as states seek to enforce sanctions and control illicit financial flows. The reliance on stablecoins by sanctioned entities may drive regulatory and enforcement actions.
- Political / Geopolitical: Heightened tensions between sanctioning and sanctioned states; potential for diplomatic conflicts over enforcement measures.
- Security / Counter-Terrorism: Increased complexity in tracking and disrupting illicit financial networks; potential for enhanced collaboration among sanctioned states.
- Cyber / Information Space: Potential for cyber operations targeting blockchain infrastructure; increased use of digital currencies in information warfare.
- Economic / Social: Potential destabilization of financial markets due to increased scrutiny and regulation of stablecoins; social unrest in regions heavily reliant on illicit financial flows.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of stablecoin transactions; collaborate with international partners to share intelligence on illicit networks.
- Medium-Term Posture (1–12 months): Develop regulatory frameworks for stablecoins; strengthen public-private partnerships to improve blockchain analytics capabilities.
- Scenario Outlook:
- Best: Effective international cooperation reduces illicit stablecoin use.
- Worst: Escalation of geopolitical tensions and financial instability.
- Most-Likely: Incremental regulatory improvements and continued illicit use with moderate disruption.
6. Key Individuals and Entities
- Russian ruble-pegged token A7A5
- Network A7
- Entities linked to China, Iran, North Korea, Venezuela
- Huione marketplace
- TRM Labs
- Chainalysis
7. Thematic Tags
cybersecurity, sanctions, stablecoins, illicit finance, blockchain analytics, geopolitical tensions, cyber operations, regulatory frameworks
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us