Infosec2025 Majority of Compromises Caused by Stolen Credentials No MFA – Infosecurity Magazine
Published on: 2025-06-04
Intelligence Report: Infosec2025 Majority of Compromises Caused by Stolen Credentials No MFA – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
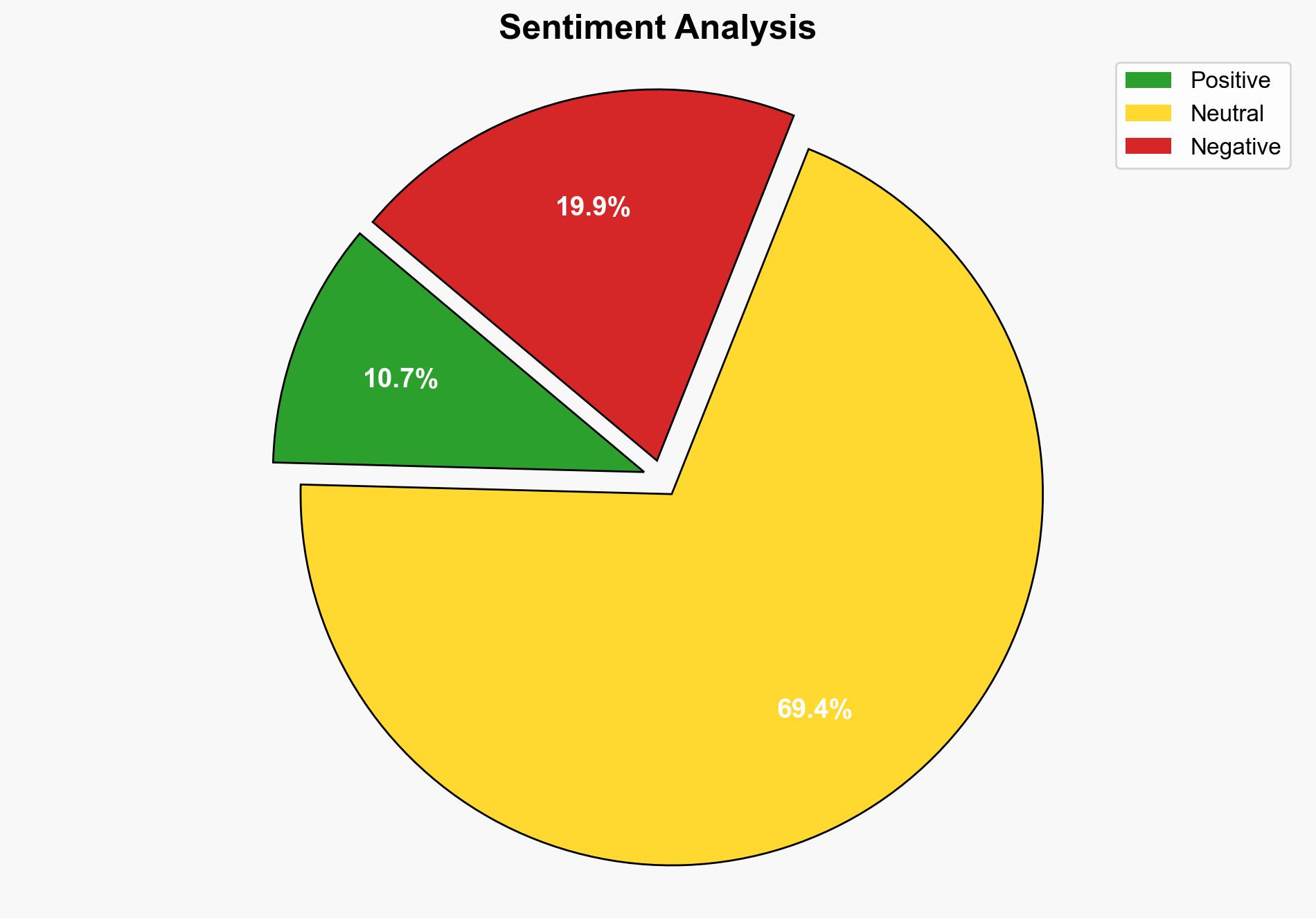
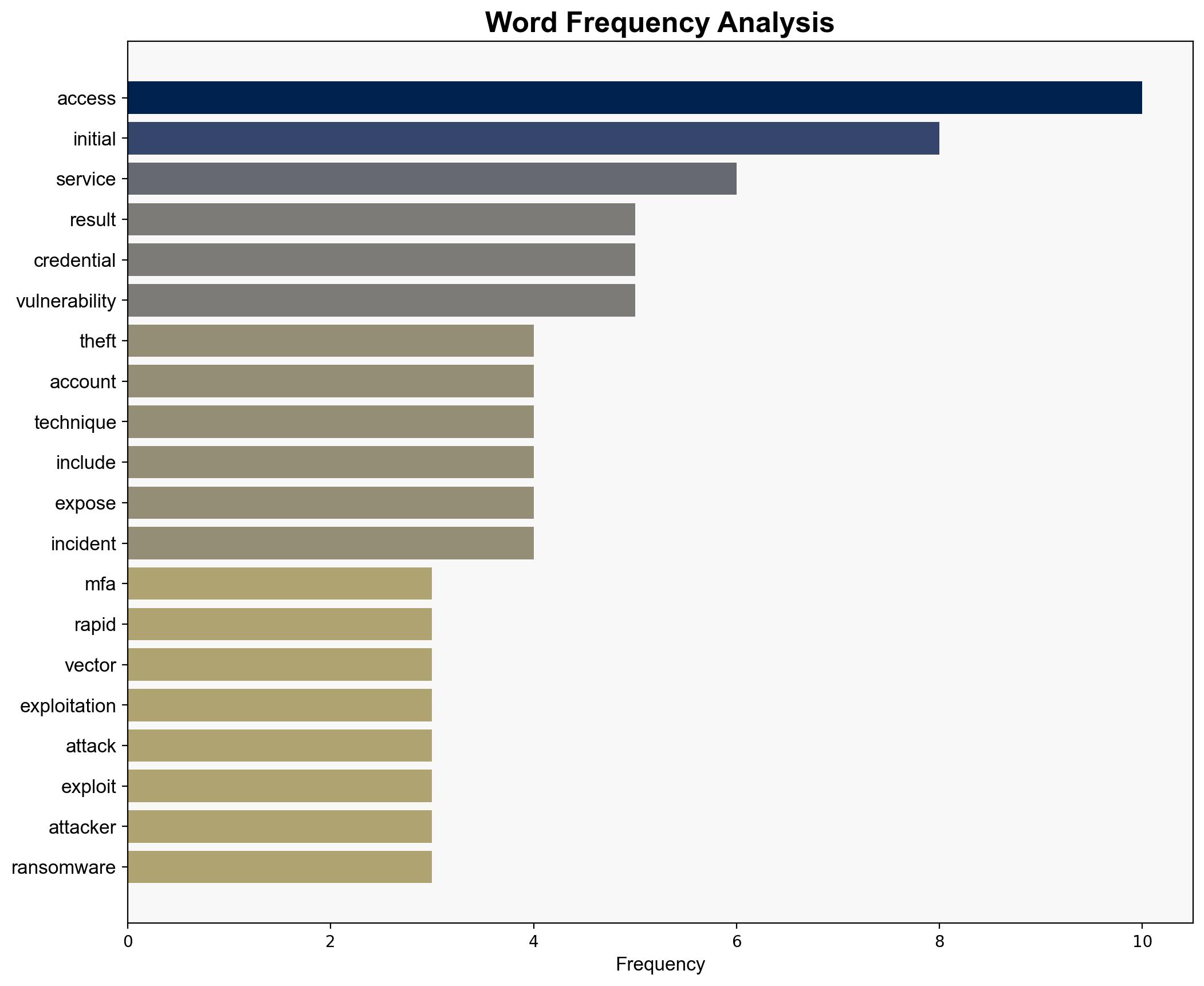
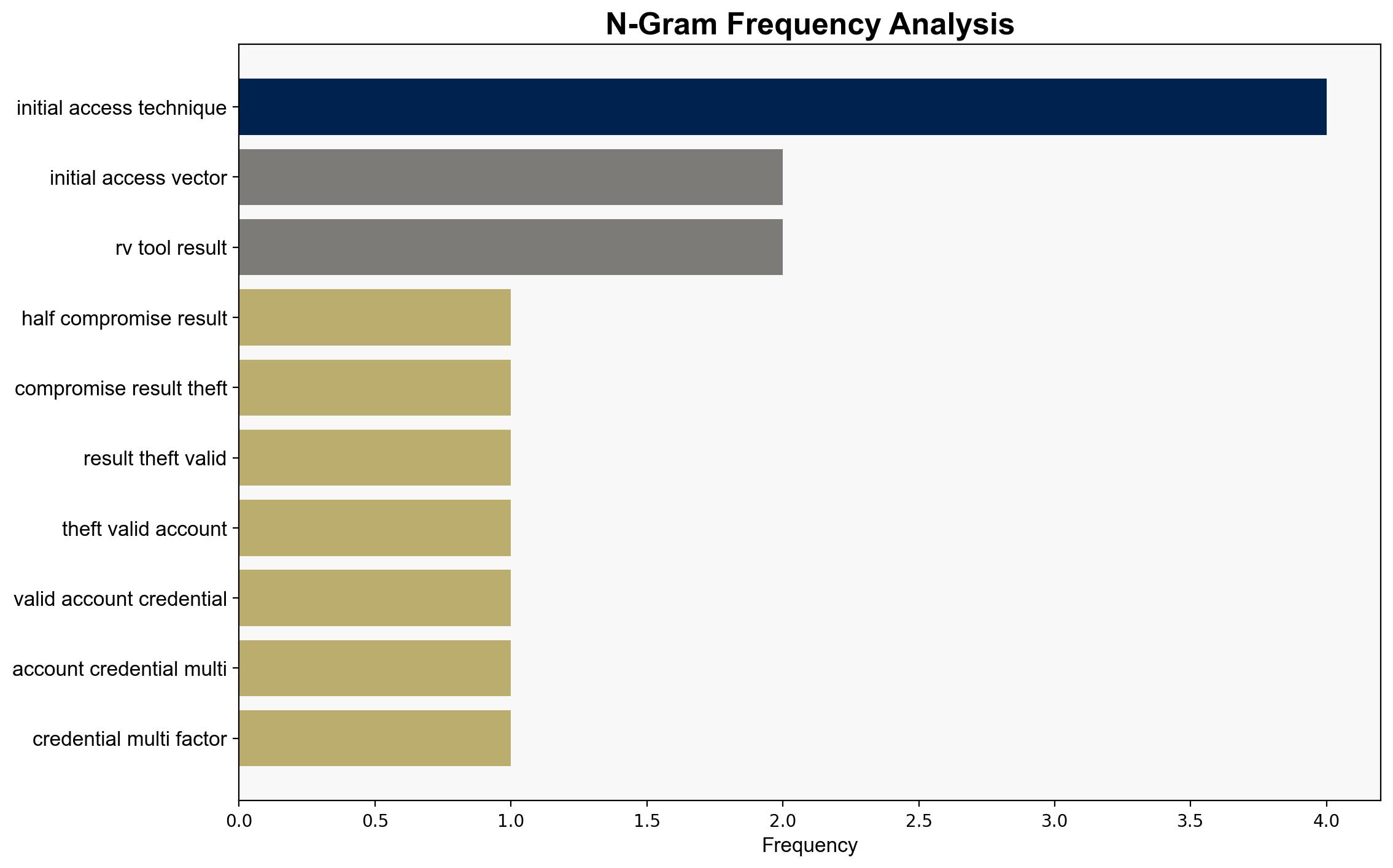
Recent research highlights that the majority of cybersecurity compromises are due to stolen credentials, exacerbated by the absence of multi-factor authentication (MFA). This trend is expected to continue as organizations fail to implement adequate protective measures. Key vulnerabilities include credential theft, exploitation of system weaknesses, and the misuse of remote access tools. Immediate action is required to enhance security protocols, particularly the adoption of MFA, to mitigate these risks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that cyber adversaries exploit credential theft and system vulnerabilities to gain unauthorized access. This highlights the need for robust defense mechanisms.
Indicators Development
Monitoring for anomalies such as unusual login patterns and unauthorized access attempts can provide early warnings of potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of continued credential-based attacks unless MFA is widely adopted.
Network Influence Mapping
Mapping relationships between network entities reveals potential pathways for adversarial influence and access.
3. Implications and Strategic Risks
The persistence of credential theft as a primary access vector poses significant risks to national security and economic stability. The exploitation of vulnerabilities in critical infrastructure could lead to cascading effects, disrupting essential services and undermining public trust. The increasing sophistication of social engineering attacks, such as SEO poisoning, further complicates the threat landscape.
4. Recommendations and Outlook
- Implement MFA across all systems to significantly reduce the risk of unauthorized access.
- Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses.
- Enhance employee training programs to recognize and respond to phishing and social engineering attempts.
- Scenario-based projections:
- Best case: Widespread adoption of MFA and improved security measures lead to a significant decrease in credential-based attacks.
- Worst case: Continued neglect of MFA implementation results in increased breaches and economic losses.
- Most likely: Incremental improvements in security practices reduce but do not eliminate the threat of credential theft.
5. Key Individuals and Entities
No specific individuals are mentioned in the source data. Focus remains on organizational practices and systemic vulnerabilities.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus